-
Computers

Best Budget GPU for AI in Your Home Server 2025
The heart of running AI workloads at home is the GPU installed in your AI workstation or AI server. If you are running local LLMs like LLaMA or looking to generate images with something like…
Read More » -

-

-

-

Latest articles
-
Self hosted
How to Install Pi-Hole on ProxMox
Pi-Hold DNS sinkholing
-
Windows
RDP An Internal Error Has Occurred Fix and workarounds
Microsoft Remote Desktop Protocol RDP makes it easy to remotely control and administer servers and clients. However, sometimes there are…
-
Automation
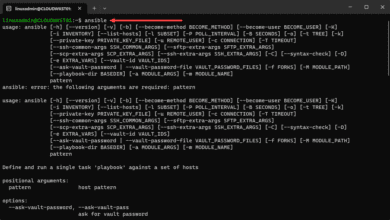
Ansible Docker Container Management Playbooks
Ansible can be used to manage your Docker container environment and other infrastructure. Let’s see how that can be done.…
-
Security
pfSense vs OPNsense – Best Open Source Firewall
In the home lab and open source community, there are two firewall solutions that seem to get everyone’s attention when…
-
Windows 11
Windows 11 Debloater with Tiny11 OS
Windows 11 has brought many new features and improvements to operating systems. While these advancements are welcomed, several pre-installed apps…
-
Microsoft 365
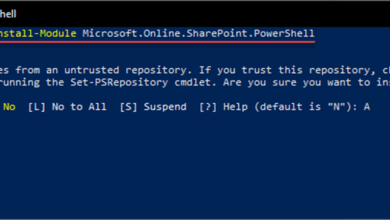
Connect to Azure AD PowerShell – Step-by-step guide
Using install-module to install the AzureAD PowerShell module
-
Storage
TrueNAS Docker Compose with Scale Apps and Truecharts
TrueNAS can truly be a LAN in a CAN solution as it can run virtual machines and even Docker containers…
-
Storage
Truenas Core vs. Scale – A detailed comparison
TrueNAS has made a name for itself as a great all around solution for not only storage but also running…
-
Cloud
Cloud Infrastructure Management for Beginners
There have been a lot of changes over the past several years in how organizations are rolling out their infrastructure.…
-
Kubernetes
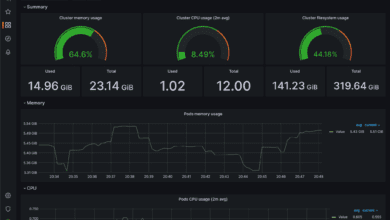
Kubernetes Monitoring Tools with Prometheus and Grafana
Kubernetes monitoring and effective monitoring at that can be done with effective free and open source solutions like Prometheus and…