-
Computers
Best Budget GPU for AI in Your Home Server 2025
The heart of running AI workloads at home is the GPU installed in your AI workstation or AI server. If you are running local LLMs like LLaMA or looking to generate images with something like…
Read More » -
-
-
-
Latest articles
-
vSphere 6.5
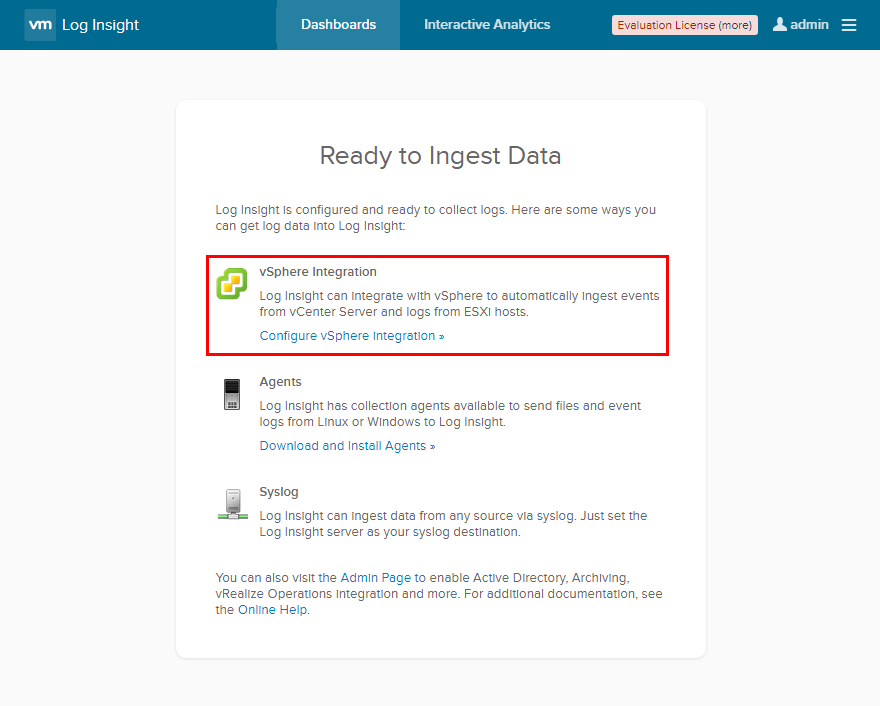
What is VMware vRealize Log Insight for vCenter Server
Let’s face it, syslog collection is not as exciting as other things we would like to be doing as administrators,…
-
vSphere 6.5
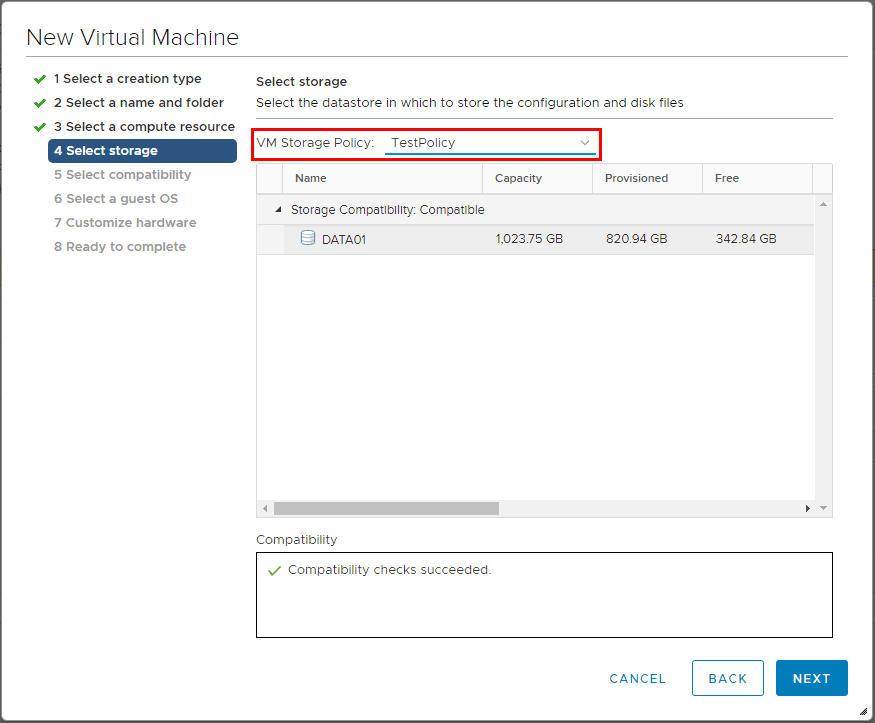
Using VMware VM Storage Policies
VMware Virtual Machine Storage Policies fall under the realm of Storage Policy Based Management that assists with virtual machine provisioning.…
-
vSphere 6.5
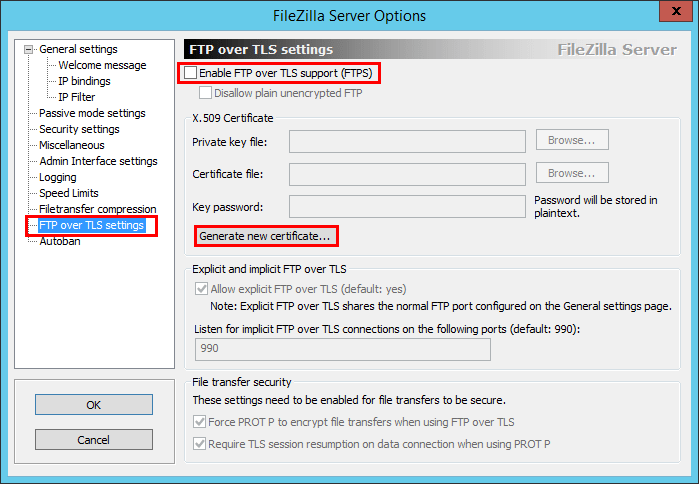
Create Secure FTPS server for VMware VCSA 6.5 Backups
We have covered in detail how to in general provision an FTP server using FileZilla for the purposes of targeting…
-
VMware
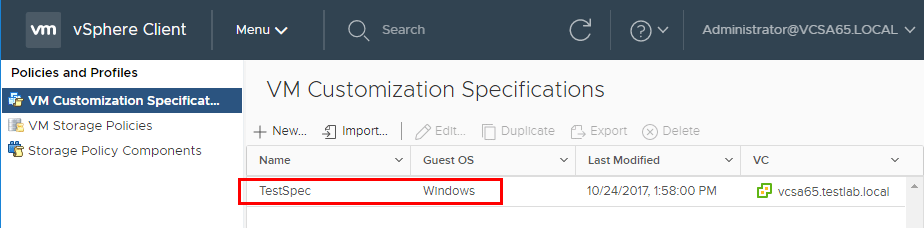
Using VMware vSphere VM Customization Specification
Deploying virtual machines is a basic part of VMware vSphere administration. Virtual machines are deployed, cloned, etc. Customizing the guest…
-
vSphere 6.5
New VMware vSphere 6.5 HTML5 Web Client Features with Fling
VMware is showing great commitment to the development of the new HTML5 web client and are quickly releasing new features…
-
VMware
What is VMware Changed Block Tracking
Most of today’s backup solutions that interact with VMware vSphere environments are able to use a technology called Changed Block…
-
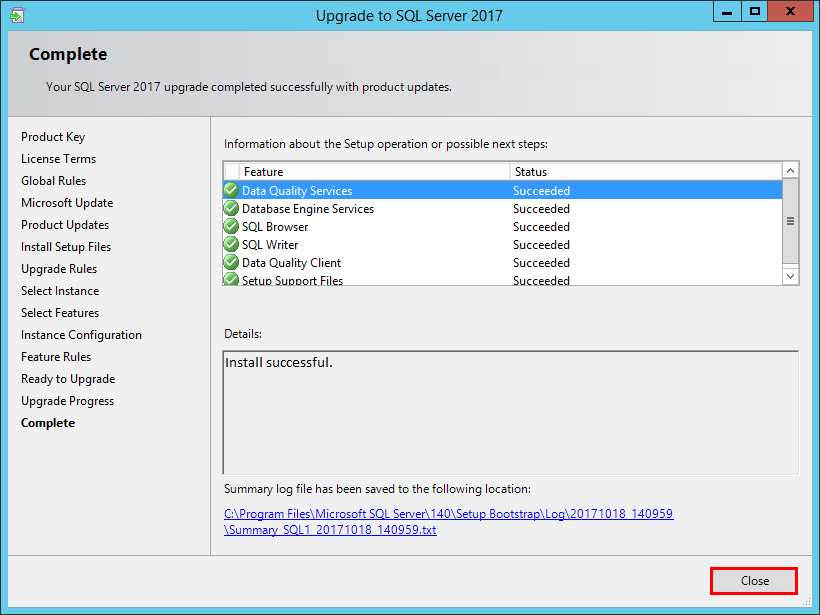
SQL
Upgrade SQL Server 2016 to 2017
Recently, SQL Server 2017 was released as GA to the masses. This represents the latest and greatest SQL server technology…
-
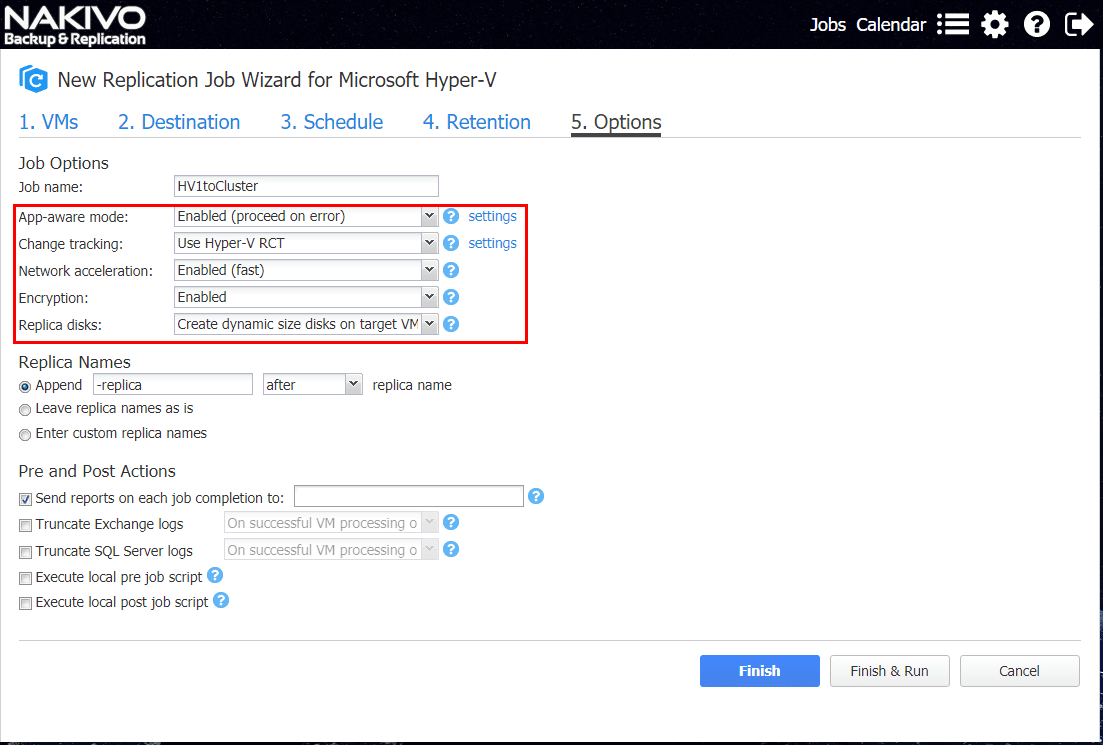
Hyper-V
Backup Hyper-V clusters with Nakivo
Nakivo Backup & Replication provides a powerful means to backup multiple hypervisors including VMware, AWS instances, and also Microsoft Hyper-V…
-
Backup Software
Veeam SQL Transaction Log Backups
Veeam Backup & Replication provides powerful features for backing up virtual environments. One of these features is the ability to…
-
NSX
What is VMware NSX SpoofGuard
VMware NSX includes many great features that help to bolster an organization’s security posture at a network level. It allows…