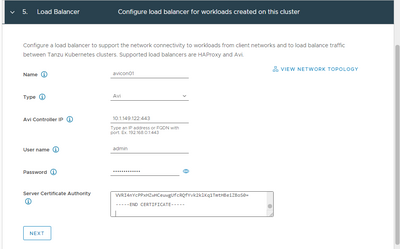
If you are running the Broadcom/VMware Avi Load Balancer, which is commonly used with the VMware Tanzu solution for Kubernetes. As you can see below, you can select the Avi load balancer when enabling VMware Tanzu workload cluster in VMware vSphere:
You need to take note of a serious vulnerability tracked by the CVE-2025-22217. The CVSS score is 8.6. It is described as:
- Unauthenticated blind SQL injection
What can an attacker do?
- An attacker with network access can use a specially crafted SQL query to gain database access to your AVI Load Balancer
You can read more specifics of the attack here directly from the Broadcom security advisory: Support Content Notification.
What do users need to do to remediate the SQL injection vulnerability? Apply the patches listed in the below response matrix. This information comes directly from the Broadcom security advisory page.
Response Matrix:
| Product | Version | Running On | CVE | CVSSv3 | Severity | Fixed Version | Workarounds | Additional Documents |
| VMware Avi Load Balancer | 30.1.1 | Any | CVE-2025-22217 | 8.6 | Important | 30.1.2-2p2 | None | None |
| VMware Avi Load Balancer | 30.1.2 | Any | CVE-2025-22217 | 8.6 | Important | 30.1.2-2p2 | None | None |
| VMware Avi Load Balancer | 30.2.1 | Any | CVE-2025-22217 | 8.6 | Important | 30.2.1-2p5 | None | None |
| VMware Avi Load Balancer | 30.2.2 | Any | CVE-2025-22217 | 8.6 | Important | 30.2.2-2p2 | None | None |