Security
-
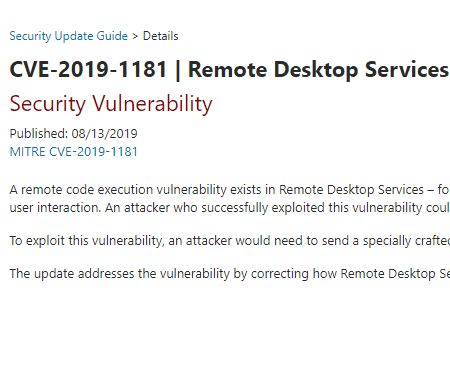
Automated Patching of Microsoft Wormable RDP Vulnerabilities
Patching is a huge part of managing IT infrastructure. It can consume a large part of IT operation’s time and energy. However, this is one area where automation and automated processes can really shine when it comes to keeping patches…
-
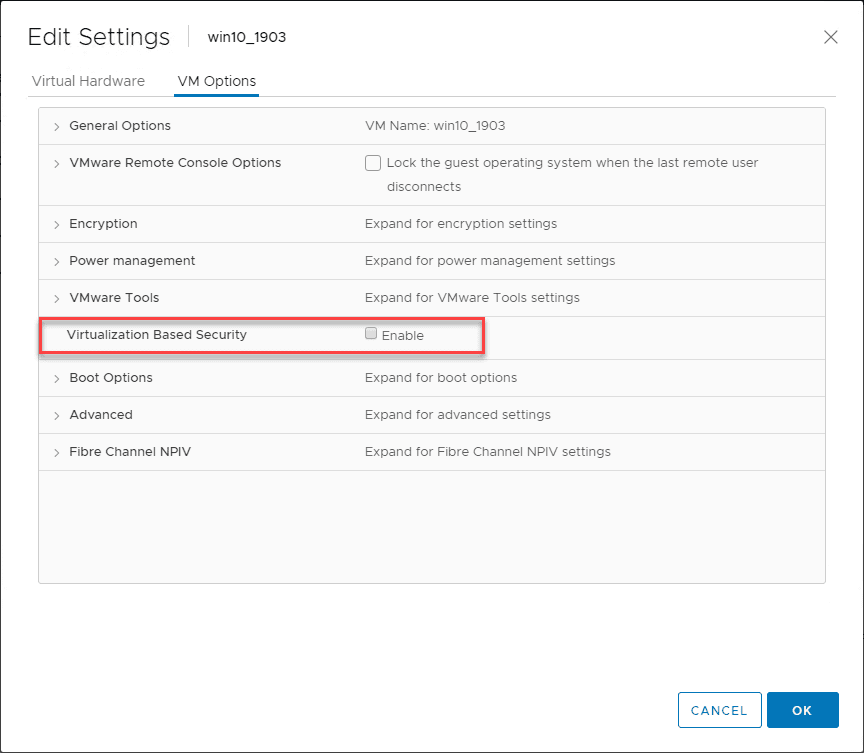
5 Ways to Improve Virtualization Security
Security is a top priority among businesses today and no doubt as a virtualization administrator you are tasked with ensuring securing in your environment is what it needs to be. Whether you manage VMware or Hyper-V environments, security is a…
-
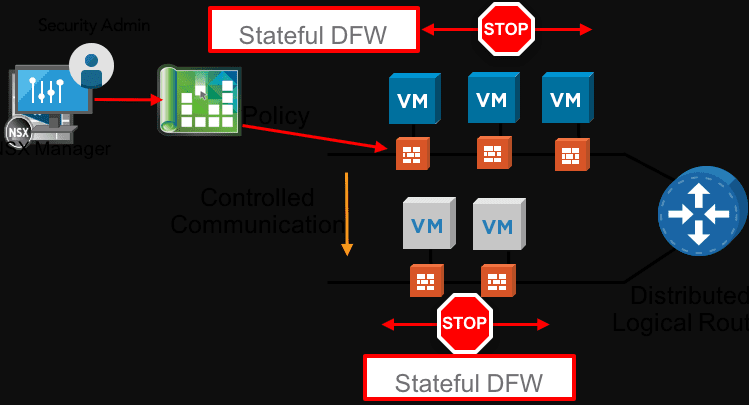
Five Ways to Improve Network Security
Network security is at the heart of designing a good security posture in an enterprise data center. Often, when threat actors are able to move easily in a lateral way across a network, it is due to poorly designed network…
-
Three Free SSL Certificates and Tools
There are various means that can be used to create free self-signed certificates that can be used for various means. This can include lab environments or POCs of products, testing, or other means. All of us know the headache at…
-
How to Create a Self-Signed Certificate for Nginx in Ubuntu 18.04
In the last post, we looked at how to configure and setup a Netbox installation to model and document your network. Netbox serves as the “source of truth” for network information in an environment. It is easily deployed following a…
-
Install LogRhythm NetMon in VMware vSphere VM
In the previous post, Free Network Threat Detection Monitoring and Forensics Tool, we tool a look at a great free network threat detection, monitoring solution, and forensics tool in the LogRhythm NetMon tool. It is a great way to stand…
-
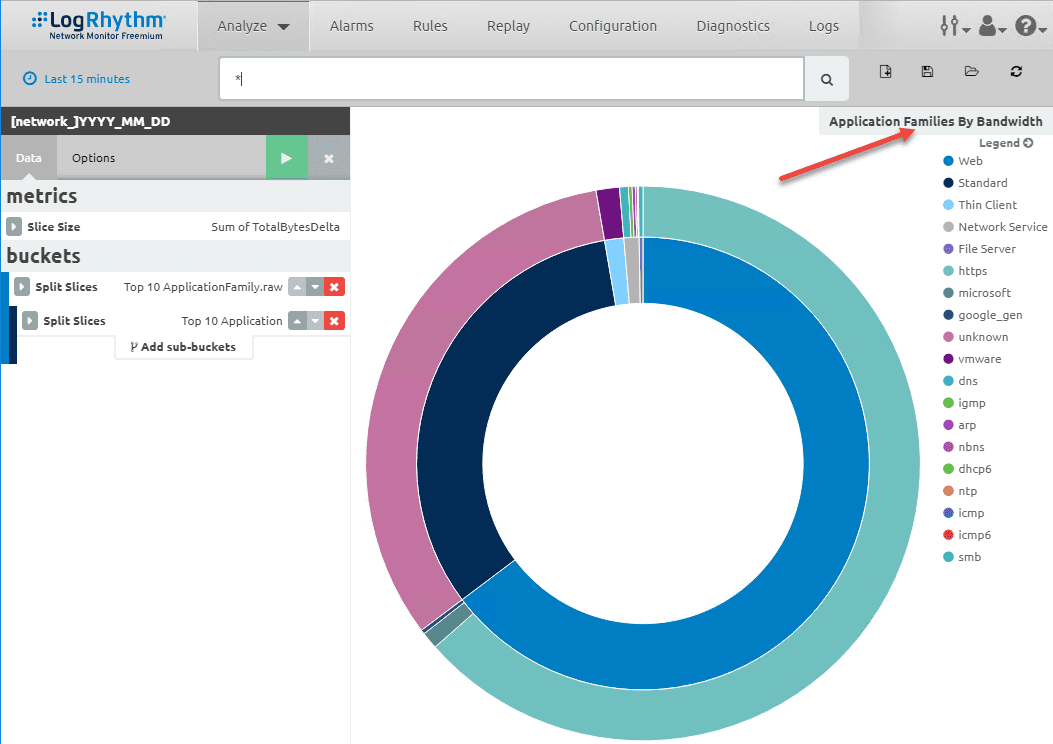
Free Network Threat Detection Monitoring and Forensics Tool
Today’s networks are becoming increasingly complex and full of many different kinds of traffic traversing them. Capable tools are needed to be able to detect threats in real time and perform network monitoring and forensics. Often organizations combine many different…
-
Top Security Threats and Responses in 2019 and Ahead
There is no shortage of security concerns in the world of technology today. It seems like there are news headlines almost every week of data breaches, ransomware infections, and other security-related events. As we look ahead in 2019 and where…
-
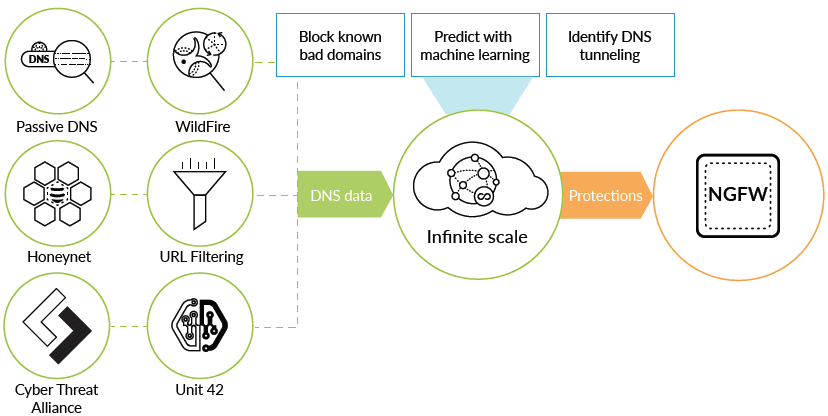
Create DNS Sinkhole to Block Malware Domains with PAN-OS 9.0
This week Palo Alto released PAN-OS 9.0. There are over 60 new capabilities in this release of the new firmware and many great new features. There is a new security functionality introduced as part of PAN-OS 9.0 that is an…