Security
-
Top 20 Open Source Cyber Security Monitoring Tools in 2023
Let’s consider the top 25 open-source cyber security monitoring tools that are a great choice in 2023. Table of contents1. Wireshark2. Snort3. OSSEC4. Security Onion5. Nmap6. Kismet7. Suricata8. Zeek (formerly Bro)9. OpenVAS10. ClamAV: Open-Source Antivirus Engine11. Fail2Ban12. AlienVault OSSIM13. Cuckoo…
-
How to Send an Encrypted Email in Outlook
This post will consider how to send an encrypted email in Outlook, different types of encryption, and how this can be implemented. Table of contentsWhat is encryption?What is email encryption?Email Encryption OptionsSending secure in OutlookHow to set up your e-mail…
-
Airmon-ng VMware Kali Linux Hacking Wireless
external USB network adapter for monitor mode
-
pfSense vs OPNsense – Best Open Source Firewall
In the home lab and open source community, there are two firewall solutions that seem to get everyone’s attention when it comes to running an enterprise-grade firewall that is free. That is pfSense and OPNsense. Both of these solutions are…
-
Pialert Docker Setup – Detecting Rogue Devices connected to the network
If you are like me, you are constantly looking at new solutions for network security and better visibility to devices connected to your network, including unknown devices. I have been using arpwatch for a few years now, and it has…
-
Commvault Metallic ThreatWise Early Threat Detection with Deception Technology
There is no question that cybersecurity is at the top of the minds of businesses in 2022 and beyond. High-profile ransomware attacks and data breach events continue to plague businesses worldwide with no end in sight. Threat actors continue to…
-
I created ESXi ransomware its scary easy and why you need proper security
As I am sure you have been reading about a lot lately, ESXi ransomware is gaining momentum and is becoming widespread. It means we, as VI admins, must stay sharp and fully understand the risks of ESXi ransomware and just…
-
Remote Desktop Multi-factor Authentication with ThinMan Smart Identity
Modern security is based around verifying and only granting access to critical systems once identity has been verified. Attackers realize that compromising a user’s identity provides easy access to sensitive systems. Therefore, businesses must do their due diligence to protect…
-
RDP vs SSH – Which should you choose?
Remote access is one of the most powerful tools in the toolbelt of an IT admin or helpdesk technician as it allows an IT worker to remotely access, configure, and administrate systems, regardless of whether they are physically near the…
-
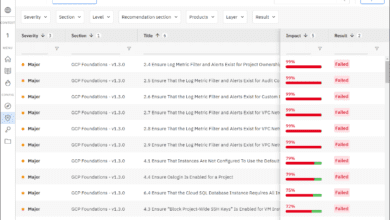
Runecast 6.2 Released New Features with Container Image Scanning and GCP support
I have written many times about the Runecast Analyzer solution that years ago started as a vSphere-only tool. However, now Runecast is a multi-faceted cybersecurity and compliance tool in addition to providing best practices recommendations and remediations across multiple environments,…