VMware Tools Vulnerability VMSA-2025-0005: What You Need to Know

In case you didn’t know, VMware released a new VMware security advisory noted in the VMSA-2025-0005 bulletin and notes the flaw: CVE-2025-22230. This allows a user with limited privileges on a guest VM to perform privileged operations which means it can be a pretty major security concern in production environments. Let’s break down the VMware Tools Vulnerability VMSA-2025-0005 and see what it is and how you can remediate it.
Table of contents
What is VMware Tools?
Just as a brief overview of VMware Tools, what are they? VMware Tools is a set of utilities that you install inside the guest operationg system of a VMware virtual machine running inside VMware vSphere infrastructure. It enables much improved interaction between the guest operating system and the VMware ESXi host.
It allows for the following:
- Better graphics performance and mouse smoothness
- Time synchronization between host and guest
- Quiescing for backups
- Heartbeat and guest monitoring
- Clipboard sharing and drag-and-drop capabilities for copying and pasting, etc
Without VMware Tools, you will find your interaction with the guest operating system from the console will be very poor performance or basically unusable. So, it is an important part of managing VMware vSphere infrastructure.
VMSA-2025-0005 and CVE-2025-22230
Let’s look at the details of this new vulnerability found in VMware Tools. Note the following:
- CVE ID: CVE-2025-22230
- CVSSv3 Score: 7.8 (categorized as Important)
- Impact: Authentication bypass due
- Affected Product: VMware Tools for Windows (Versions 11.x.x and 12.x.x)
- Unaffected: VMware Tools for Linux and macOS
You can read the official details of the vulnerability here: Vulnerability details.
Exploitation
Exploitation of this vulnerability can happen with a non-administrative user on a Windows guest virtual machine. A non-admin user can potentially escalate privileges and carry out privileged operations using this flaw. This includes things like unauthorized access to functions inside the VM that should be restricted.
Products Affected
- VMware Tools 11.x.x and 12.x.x for Windows
- Linux and macOS variants are not affected
Resolution
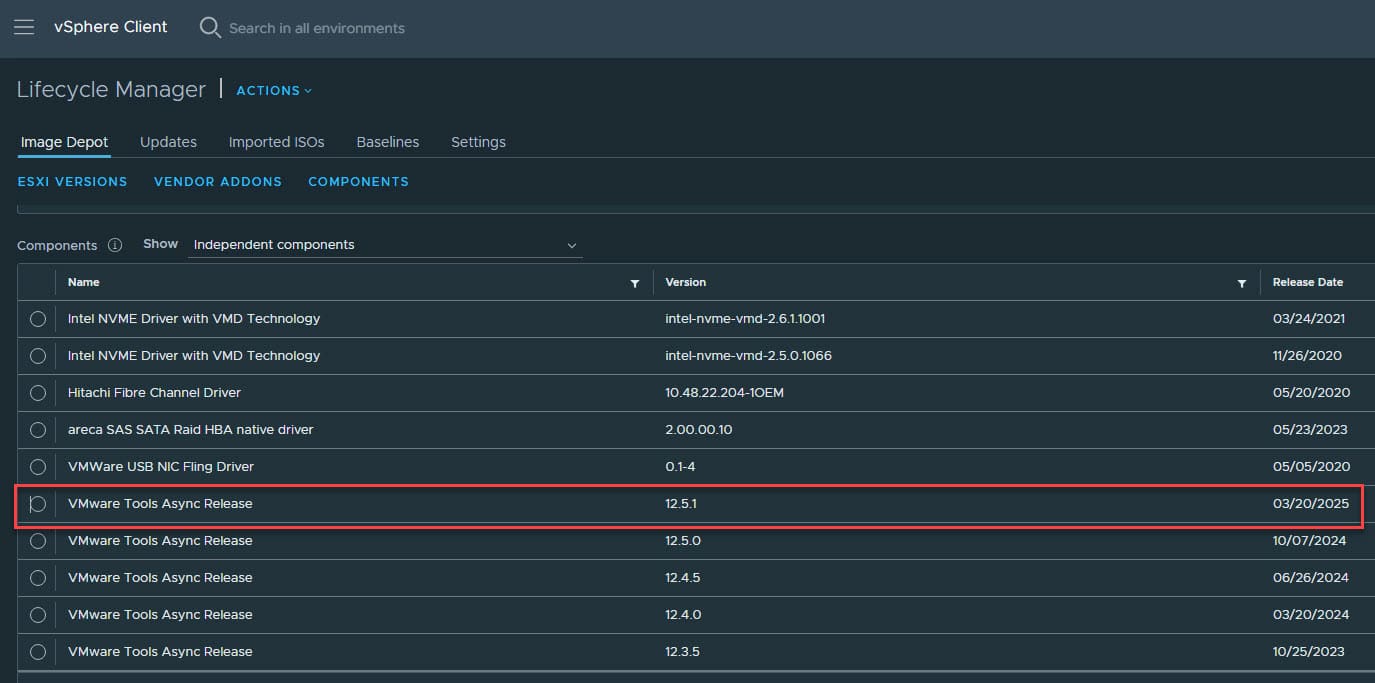
VMware has released VMware Tools 12.5.1, which addresses the vulnerability across both 64-bit and 32-bit Windows guest operating systems. Specifically:
- VMware Tools 12.5.1 for 64-bit Windows
- VMware Tools 12.4.6 (included in 12.5.1 package) for 32-bit Windows
If you’re running any of the impacted versions, upgrade immediately to stay protected.
No Known Workarounds
There are currently no known workarounds for VMware Tools Vulnerability VMSA-2025-0005 meaning that patching is the only effective mitigation.
Acknowledgment
Broadcom credits Sergey Bliznyuk of Positive Technologies for responsibly disclosing this vulnerability.
How to Update VMware Tools at Scale
Keeping VMware Tools updated across a large environment can be challenging. VMware offers multiple supported workflows for patching VMware Tools to streamline this process. The official blog Updating VMware Tools at Scale gives the recommended ways to keep your VMware Tools updated. Let’s consider those here and see how they can be used.
1. Using vSphere Lifecycle Manager (vLCM)
Baseline Method
- Create a custom baseline for your cluster that includes the VMware Tools version
- Attach it to your cluster
- Remediate your hosts and VMs
Single Image Method
- If you are using the image-based management, add the VMware Tools component in the single image
- This helps with uniformity and also simplifies remediation across your hosts
2. Centralized VMware Tools Repository
This method is also a good way to centrally manage the new VMware Tools package and patch VMware Tools Vulnerability VMSA-2025-0005.
- You can host VMware Tools installers on a shared datastore
- Update
UserVars.ProductLockerLocationon your ESXi hosts to point to this shared path - This helps with centralized versioning and makes update management much easier
3. Automating Updates with PowerCLI
Once you have a shared location for updates, you can automate the process for getting the updates applied to your virtual machines using VMware PowerCLI.
VMware PowerCLI has the Update-Tools cmdlet for in-guest upgrades using an automated approach. Take a note of the example code below that connects to your vCenter Server, gets the VMs located on a cluster and then loops through and performs a VMware Tools upgrade on the affected VMs. As you note below, it does not perform a reboot. The RunAsync parameter helps with script performance as well.
Connect-VIServer -Server "your-vcenter-server.domain.local"
$VMs = Get-Cluster -Name "YourClusterName" | Get-VM
foreach ($vm in $VMs) {
if ($vm.ExtensionData.Guest.ToolsStatus -ne 'toolsOk') {
Write-Host "Updating VMware Tools on $($vm.Name)..."
Update-Tools -VM $vm -NoReboot -RunAsync
}
}
Disconnect-VIServer -Confirm:$false4. Guest OS-Level update tools
There are other approaches to updating your VMware Tools installation, using the following methods:
- Use Microsoft System Center Configuration Manager (SCCM) or other RMM tools
- You can push the VMware Tools installer as a managed package
- If your organization already has a process in place for managing guest-level software updates and packages, this is a good option to use
5. Set to upgrade at next reboot
Another method you can use is to set the ToolsUpgradePolicy to UpgradeAtPowerCycle which means the VM will upgrade its installation of VMware Tools at the next reboot. The PowerCLI code example below shows how you can use this approach to upgrade your VMware Tools using this policy.
Connect-VIServer -Server "your-vcenter-server.domain.local"
$VMs = Get-Cluster -Name "YourClusterName" | Get-VM
foreach ($vm in $VMs) {
$spec = New-Object VMware.Vim.VirtualMachineConfigSpec
$spec.Tools = New-Object VMware.Vim.ToolsConfigInfo
$spec.Tools.ToolsUpgradePolicy = "UpgradeAtPowerCycle"
$vm.ExtensionData.ReconfigVM_Task($spec)
}
Disconnect-VIServer -Confirm:$falseWhy update as soon as possible?
Generally speaking, once vulnerabilities become known and patches are made available, attackers and other threat actors will try to capitalize on the vulnerability sooner rather than later to hopefully catch environments in a vulnerable state before updates have been applied. By updating as soon as you can, you can mitigate this risk of possible security issues and get the vulnerability closed off from attack.
If organizations fail to patch or are slow to patch, this can lead to the following:
- Compromised compliance objectives (HIPAA, PCI-DSS, etc.)
- Lateral movement within the network by a threat actor
- Unauthorized data access or modification
The potential risks outweigh any hassle to upgrading VMware Tools in the environment.
Wrapping up
VMware Tools Vulnerability VMSA-2025-0005 is a serious vulnerability that VIAdmins need to take seriously and get patched as soon as possible. Thankfully, there are multiple methods to use for patching the environment, including manually patching the environment or using automation with VMware PowerCLI and vLCM images to have a more streamlined and consistent approach. Let me know in the comments what your thoughts are on this vulnerability and what method you use to patch your VMware environments.