VMSA-2025-0004 Critical VMware ESXi, Workstation, and Fusion Vulnerability Patch Now!
In case you haven’t heard as of yet, there is a new critical VMware ESXi, Workstation, and Fusion vulnerability that has been discovered and noted in the VMSA-2025-0004 security bulletin. These are tracked as CVE-2025-22224, CVE-2025-22225, CVE-2025-22226. Let’s look at the new vulnerability, what it entails, and how to remediate.
Table of contents
- Details about the new VMSA-2025-0004 security bulletin
- 1. VMCI heap-overflow vulnerability (CVS-2025-22224)
- 2. VMware ESXi arbitrary write vulnerability (CVE-2025-22225)
- 3. HGFS information-disclosure vulnerability (CVE-2025-22226)
- How do you fix these vulnerabilities?
- How to patch the new VMSA-2025-0004
- Resources
Details about the new VMSA-2025-0004 security bulletin
The vulnerabilities tracked in this VMSA are the following: CVE-2025-22224, CVE-2025-22225, CVE-2025-22226. So, this includes multiple vulnerabilities affecting multiple products, including VMware ESXi, VMware Workstation, VMware Cloud Foundation, VMware Fusion, and Telco Cloud Platform.
Let’s look at the three primary vulnerabilities as part of this VMSA security bulletin, what they affect and how they are remediated.
1. VMCI heap-overflow vulnerability (CVS-2025-22224)
This is the worst in terms of the CVSSv3 score, rated at a 9.3 critical vulnerability. It is a Time-of-Check Time-of-Use (TOCTOU) vulnerability that is found in VMware ESXi and Workstation that can lead to an out-of-bounds write by an attacker. If an attacker has local administrative privileges on a virtual machine, they can exploit this issue to execute code as the VMX process that is running on the host.
Being the critical nature of the vulnerability, VMware has assigned it a 9.3 critical vulnerability and noted there is also evidence this is being actively exploited in the wild.
2. VMware ESXi arbitrary write vulnerability (CVE-2025-22225)
This vulnerability as part of the VMSA-2025-0004 bulletin is a vulnerability that enables an attacker with privileges within the VMX process to trigger a kernel write. This can lead to a sandbox escape. This part of the vulnerability affects VMware ESXi and has been given a CVSSv3 score of 8.2, which is an important vulnerability range. Again, with this vulnerability there is evidence that there may be active exploitation of this in the wild.
3. HGFS information-disclosure vulnerability (CVE-2025-22226)
This vulnerability is present in VMware ESXi, Workstation, and Fusion, It is an out-of-bounds read vulnerability in HGFS that can potentially be exploited by an attacker with administrative privileges to a virtual machine. If so, they can potentially leak memory contents from the VMX process. The CVSSv3 base score for this one is 7.1 and is also categorized in the important range. There is also evidence with this portion of the vulnerability of active exploitation in the wild.
How do you fix these vulnerabilities?
There is no workaround that is noted in the VMSA for the three vulnerabilities. Only patching can remediate the threat associated with these.
How to patch the new VMSA-2025-0004
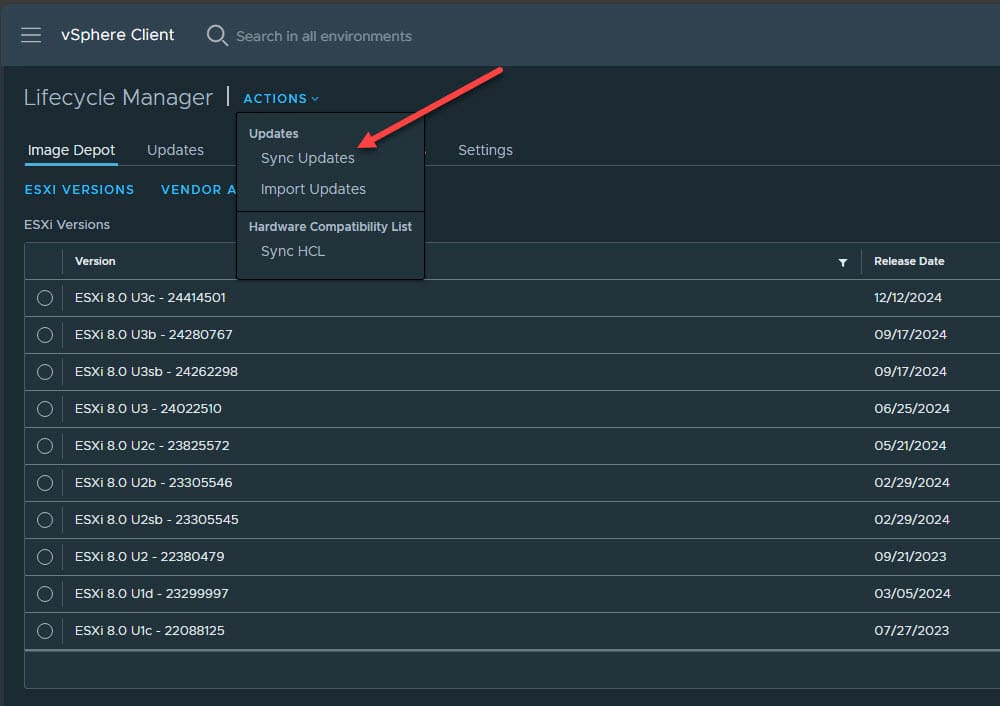
Below, we will show how to patch the vulnerabilities found in the VMSA-2025-0004 bulletin using the vSphere Lifecycle Management tool that provides image-based remediation for your cluster. Click the “hamburger” menu on the upper left-hand side of the vSphere Client. Then select Image Depot > Actions > Sync Updates.
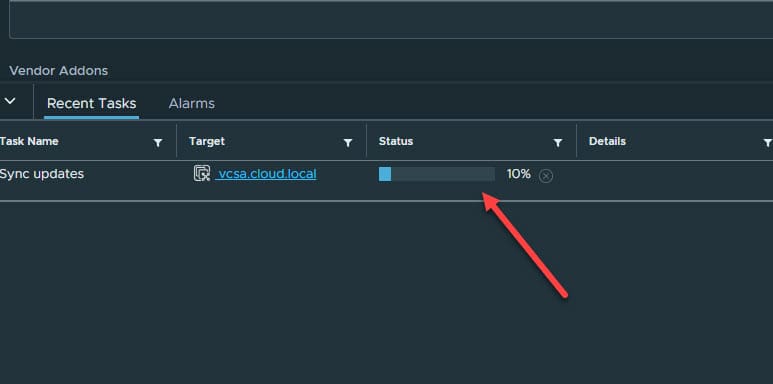
This will queue the sync updates task in vCenter Server. This step will take a couple of minutes to run.
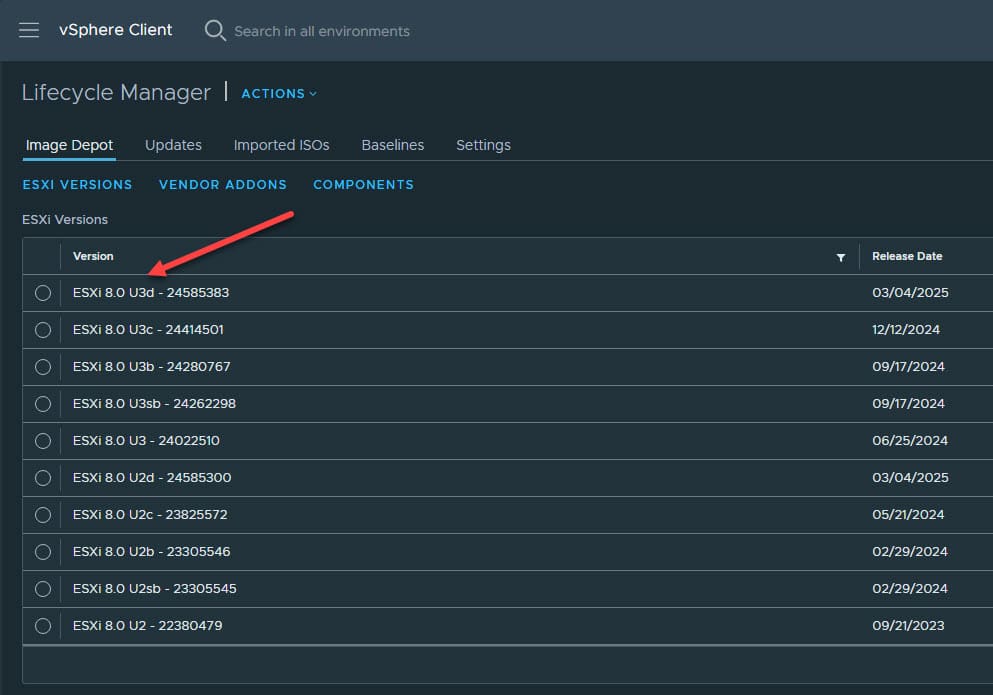
After the task completes, you should see a new version appear that shows the release date of 03/04/2025. The new version is ESXi 8.0 U3d – 24585383.
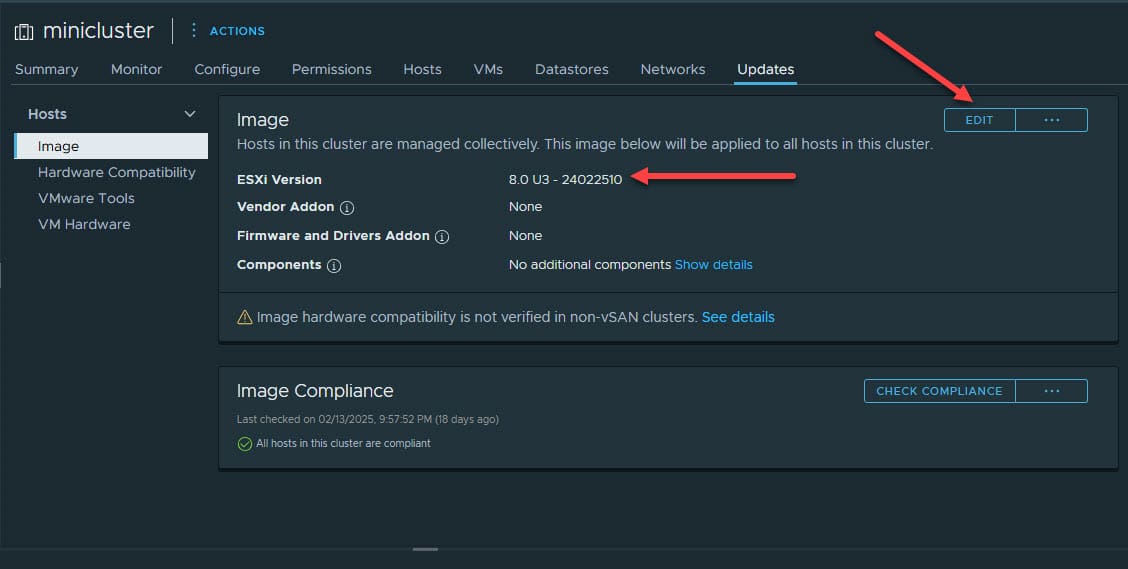
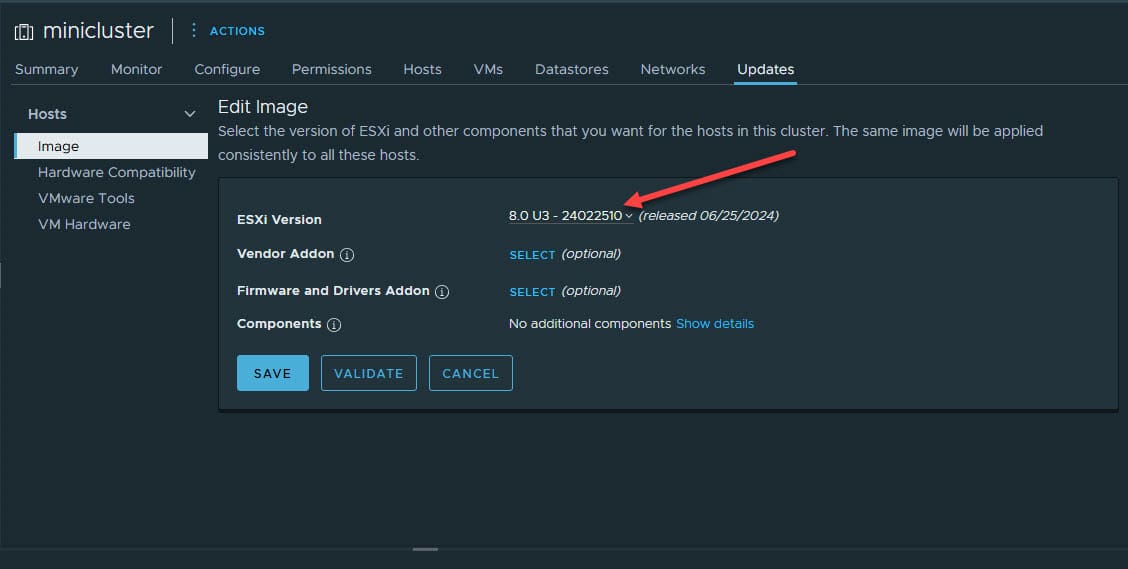
Click your cluster in the vSphere Client. Then click the Updates tab. You will see the old version listed for your current image for your cluster. Click the Edit button.
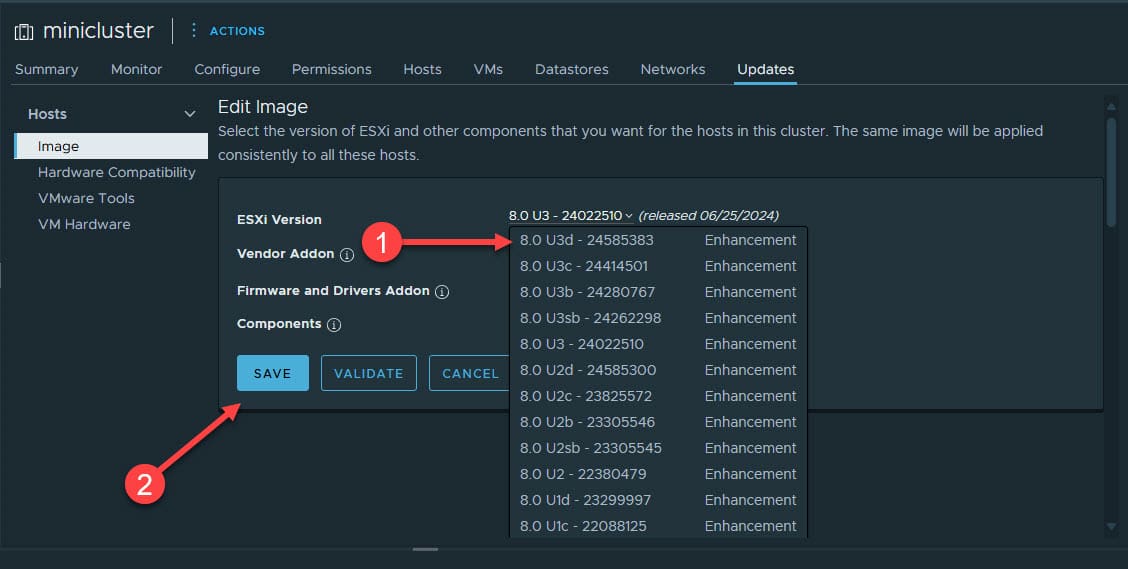
This will pop down a drop down menu. Select the new version, 8.0 U3d – 24585383. Then, click Save.
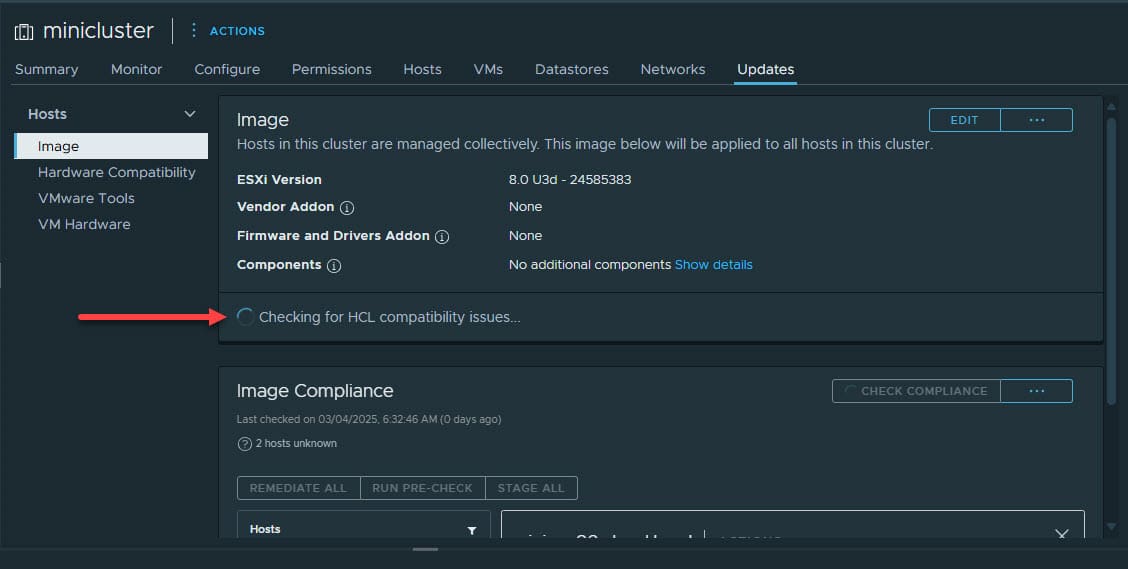
Once you save the image, it will begin checking for HCL compatibility issues.
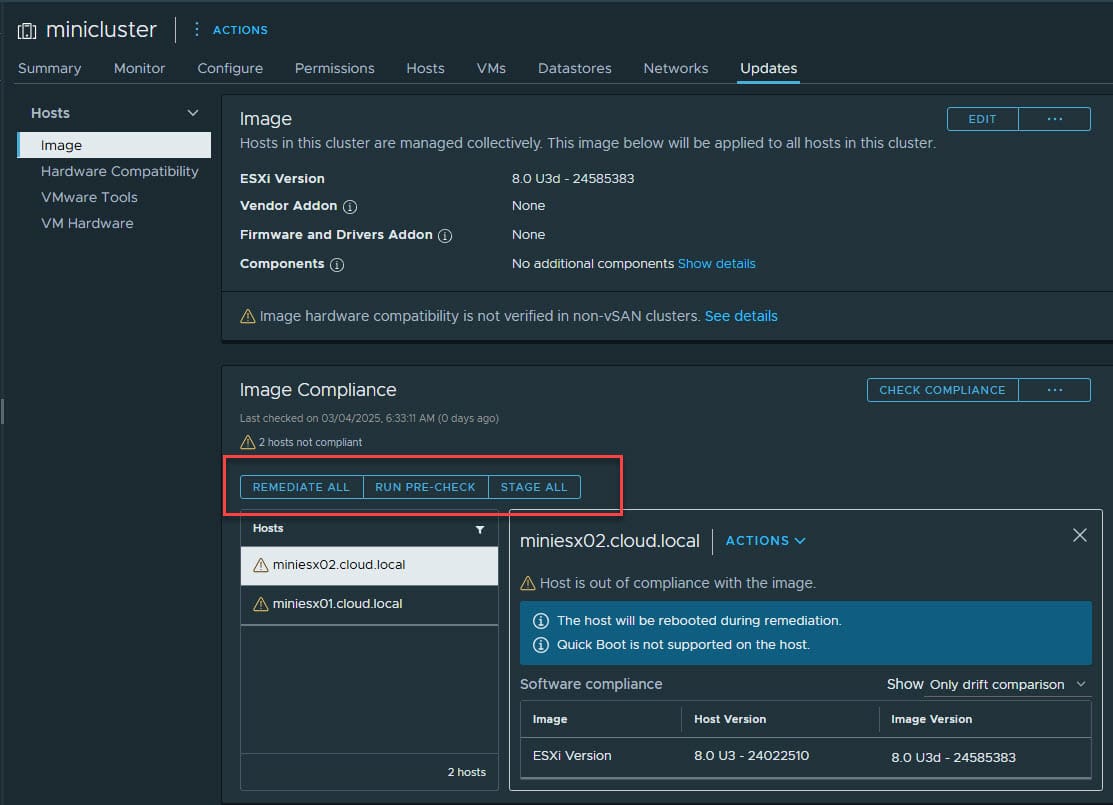
This should finish successfully. You will then see that your cluster is out of compliance with the new image which is expected. This means vSphere has correctly detected the change in the image for the cluster and knows your hosts need to be remediated.
Resources
You can read the official VMSA security bulletin here: Support Content Notification – Support Portal – Broadcom support portal.
If you need a primer on how to remediate your hosts with the vSphere Lifecycle Manager, watch my YouTube video here that shows the process: