Best Home Lab Networking Architecture in 2025

One of the core aspects of any IT infrastructure is the network. The network is the center of how everything communicates, works, and it also forms the core of your security posture and how well your apps perform. This is no different in a home network or home lab environment. We are going to explore the best home lab networking architecture in 2025 and take a look at beginner, intermediate, and advanced networking architecture that can help you take your home lab to the next level.
Table of contents
What is the goal of your home lab?
One of the first things that you need to settle on is the goal of your home lab. You can build a home lab for so many different things. For learning, self-hosting, experimentation, or something else. Your lab may be a combination of all the above.
Note the following list of activities or goals you might have for your home lab, including:
- Virtualization and container networking: Built and configured for running VMware, Proxmox, Docker Swarm, or Kubernetes.
- Segmentation and security: This goal interwines with others, but is key in isolating lab services from personal/home devices or even studying for security certifications
- High availability (HA): Making sure your self-hosted apps have high availability and resilience against failure
- Remote access and VPNs: Be able to remotely connect, access, and administer your home lab environment.
- Performance: Your goal may be to have ultra-fast performance between your servers and any attached storage.
To make things easier, let’s look at the best home lab networking architecture from the standpoint of Beginner, Intermediate, and Advanced configurations. This will help users at different levels find a design that fits their needs.
Beginner home lab network architecture
The first level or network architecture design for home lab usually includes designs that many beginners start with. However, there isn’t anything fundamentally wrong with starting with the beginner concepts and network configuration. The beginner designs will focus on being simple, inexpensive, and give a solid network foundation on which you can build on or leave as is and be able to have the functionality needed.
1. Basic Flat Network (Beginner)
This is the simplest network setup for a home lab. Usually this is what everyone starts with if they don’t have much experience with network architecture or design. However, even experienced users may still opt for this, just for simplicity. In the basic flat network. It is designed to get started with minimal configuration. It can use just basic off the shelf networking equipment that most homes may already have. This includes things like a consumer router that may be a wireless/router all -in-one. Then, this device will connect everything else to the network that you have running in your home.
Below is just a simple overview diagram. Everything is connected on the same network and there are no VLANs in play.
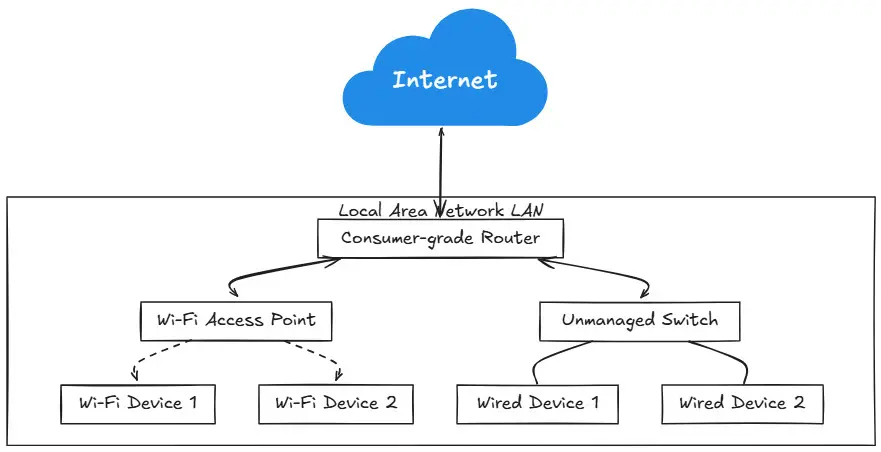
Hardware Requirements:
- Just a consumer-grade router (e.g., ASUS, Netgear, or TP-Link) or something you would find at your local retail store
- Unmanaged switch (if additional ports are needed)
- Wi-Fi access point (this is already built into most consumer routers)
Configuration:
- All devices share the same local network (LAN)
- Devices use DHCP for IP address assignment (automated IP address management)
- Local network and Internet traffic share the same bandwidth in and out of the network
Pros:
- Extremely easy to set up
- No other costs beyond the existing router
- Works well for starting out small with networking and experimentation
Cons:
- No network segmentation.
- Not as secure; all devices are on the same network
- Performance can suffer as all types of traffic share the same network
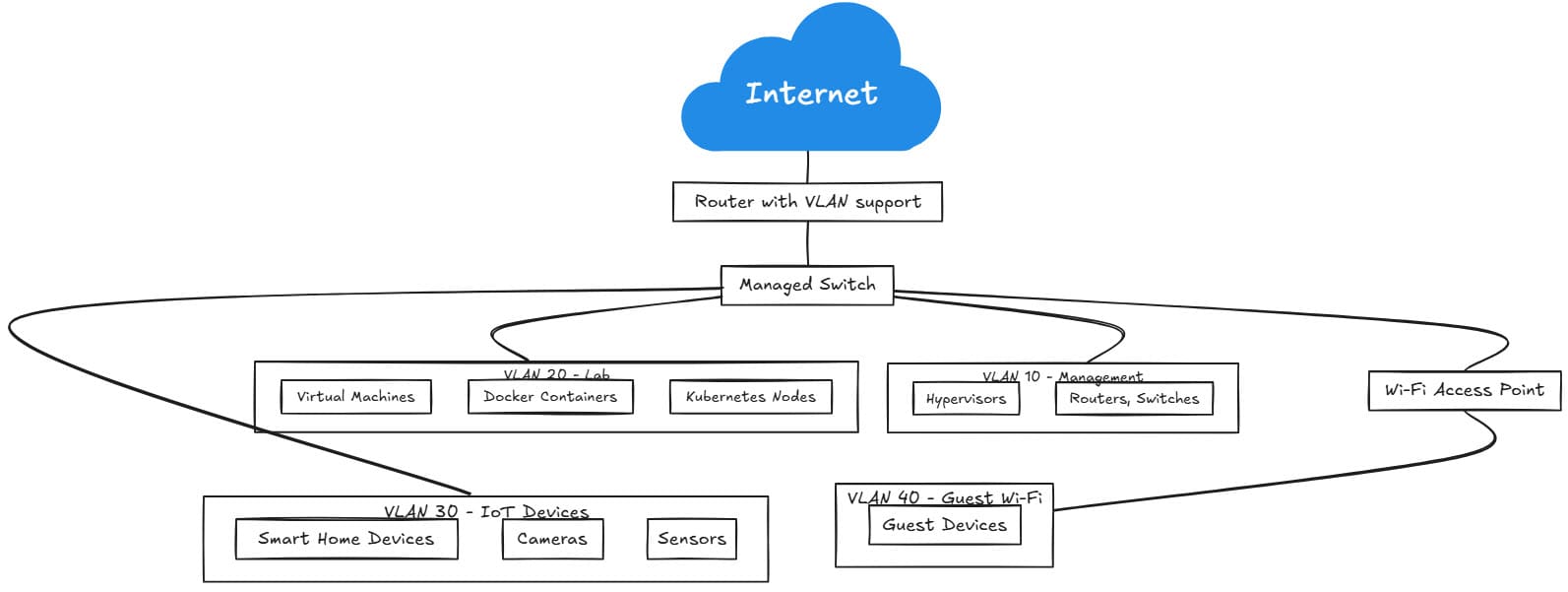
2. Beginner Segmented Network with VLANs
Taking things a step further, the beginner segmented network introduces VLANs. VLANs allow separating traffic on a network into individual logical networks that run across the “same wire” essentially. You can think of it as a means to do the same thing logically that would normally require multiple physical switches to carry different types of traffic.
Instead of multiple physical switches, the VLAN “tag” is added to different networks logically separating these as they flow across the wire.
Simple Example of Cisco VLAN syntax
Cisco devices and command syntax are usually universally accepted as the standard for command syntax. Below are a few examples of how to create VLANs and configure them along with ports:
# Creating VLANs
enable
configure terminal
vlan 10
name Management
exit
vlan 20
name Servers
exit
vlan 30
name IoT
exit
# Access VLAN
interface GigabitEthernet0/1
switchport mode access
switchport access vlan 10
exit
# Trunk port configuration
interface GigabitEthernet0/2
switchport mode trunk
switchport trunk allowed vlan 10,20,30
exit
# Setting untagged traffic on a port
interface GigabitEthernet0/2
switchport trunk native vlan 99
exitHardware Requirements:
The hardware requirements become a bit more expensive in this configuration and more complexity is added since all the network components in this design need to be VLAN aware. Many consumer grade devices that you buy at your local Wal-mart, for example, usually are not VLAN aware. You will often need to upgrade to more expensive “managed” switches that allow this type of configuration. Although, I have seen some cheap switches like TPLink and others that allow a very simplistic web interface and allow you to create and manage VLANs that way.
Note the following hardware needed:
- Router with VLAN support such as pfSense, OPNsense, or UniFi Dream Machine Pro
- A managed switch that is VLAN-aware, such as UniFi, TP-Link Omada, MikroTik
- Wi-Fi Access Point with VLAN tagging capability
Configuration:
- VLANs must be created and then assigned to specific internfaces and also tagged from the device traffic. Untagged VLAN configurations allow setting the VLAN tag at the switch side if a network client can’t tag VLAN traffic. You might split up traffic to look like the following as an example:
- VLAN 10 – Management, hypervisors, routers, switches
- VLAN 20 – Lab VMs, Docker containers, Kubernetes nodes
- VLAN 30 – IoT Devices like smart home, cameras, sensors, etc
- VLAN 40 – Guest Wi-Fi that is isolated from lab and home network
- You can also use firewall rules to control access between your VLANs
Pros:
- When you separate network traffic as introduced with VLANs this greatly improves security
- Prevents devices from being able to communicate if they don’t need to
- This allows networks to perform better as it helps to control congestion with too many devices on the same network
Cons:
- VLANs can be a bit of a “mind bender” to get your head wrapped around. However, once it clicks, it is a fundamental skill that you will never forget and will help you in ever step of the way in your home lab journey
- Most consumer-grade hardware does not support VLANs and VLAN tagging
Intermediate Home Lab Networking Designs
Moving into the intermediate home lab networking design, this design helps users with growing home labs to achieve better performance, security, and also reliability at this stage usually comes front and center. Generally at the intermediate stage, virtualization is introduced and ones are experimenting with running virtual machines and containers if they didn’t already in the beginning stages.
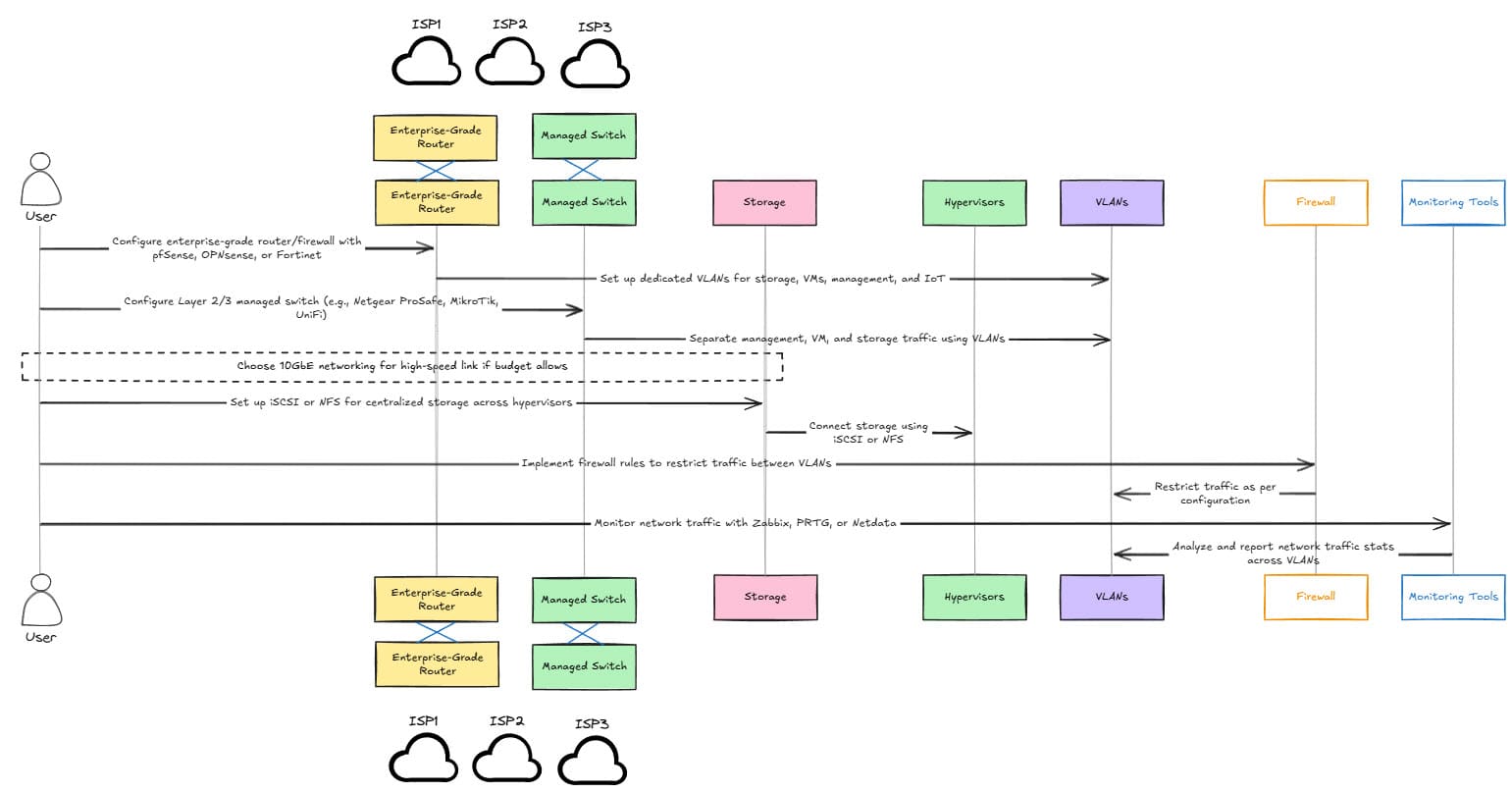
3. High-Performance virtualized network
In this configuration, the network is more optimized for running things like virtual machines, Docker containers, or Kubernetes clusters with high-speed networking.
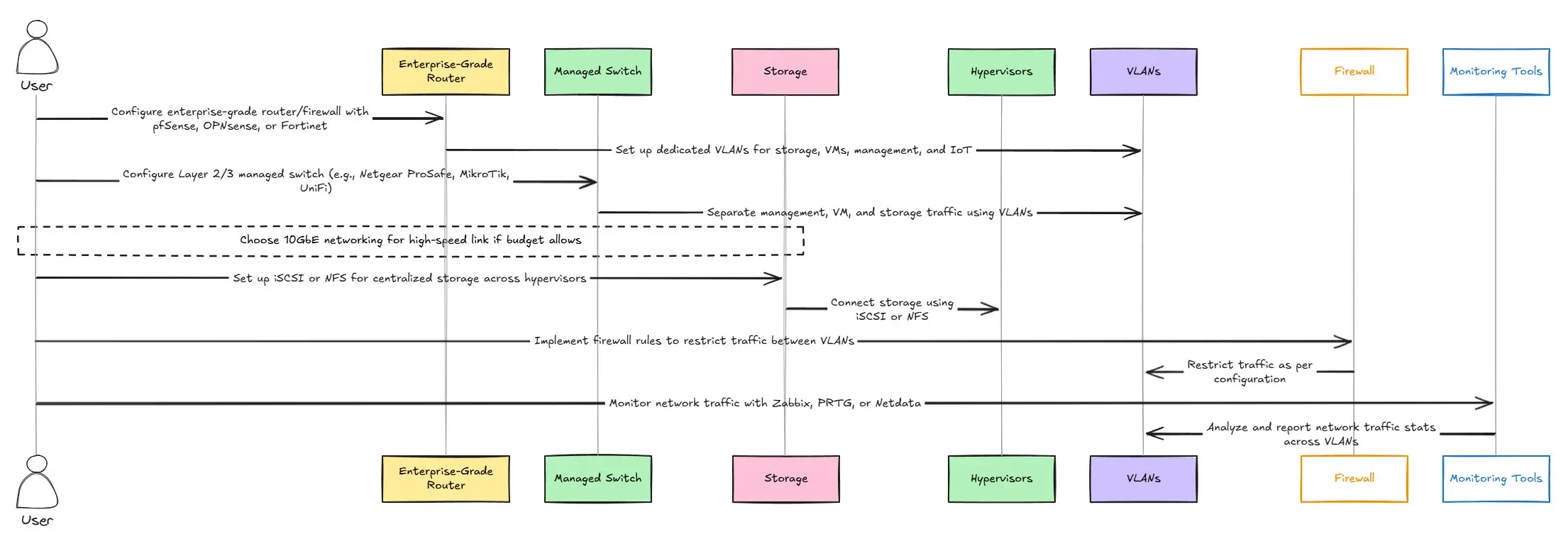
Hardware Requirements:
In this network design, you are looking at more enterprise-level gear that can keep pace with configurations you may want to implement with a virtual networking focus. You may need the following:
- Enterprise-grade router/firewall running something like pfSense, OPNsense, Unifi, etc
- Layer 2/3 managed switch is generally required like something similar to a Mikrotik, Ubiquiti, Cisco, etc
- You will want to have dedicated VLANs for storage, VMs, containers, management, wireless, and IoT to name a few
- 10GbE networking between storage and hypervisors is where you will start likely feeling pleased with the performance you are getting with running multiple virtual machines on shared storage.
Configuration:
- You will use VLANs to separate management, VM, and storage traffic and keep these on their own space for security and performance reasons
- Set up iSCSI or NFS shared storage for shared storage across hypervisors
- Use firewall rules to restrict traffic between VLANs
- Monitor network traffic with Zabbix, PRTG, or Netdata – Monitoring will help once your network becomes more complex with more moving parts and segments
Pros:
- Much better performance and efficiency
- High-speed networking for virtualized environments, including VMs and containers
- Much better security with VLAN isolation and firewall rules
Cons:
- If you are looking for cheap, the intermediate home lab networking architecture design is where you will start to see your networking costs increase. This is due to the higher cost for managed switches and 10GbE networking
- Again, you will need network expertise to configure VLANs, firewall rules, and monitoring
4. Redundant and Highly Available Setup
This design takes what we have already stated above about the intermediate network design and introduces redundancy to prevent downtime due to network failures. In this configuration, you will add things like multiple firewalls/routers, switches, and multiple ISPs to prevent downtime due to a failure of network hardware or single ISP.
Hardware Requirements:
- Dual WAN setup with failover is required in this configuration so will depend on the vendor and implementation on how this is achieved
- High-availability firewall such as CARP with pfSense, HA with OPNsense
- You will need a managed Layer 3 switch for VLAN routing if you are doing intervlan routing on your switches. Even if your routing takes place on your firewall, your switch will still need to be VLAN aware
- Multiple APs for being able to roam from different areas of the home lab to others
Configuration:
- Use Link Aggregation Control Protocol (LACP) can be used for redundant links
- You can configure things like VRRP or CARP for failover between firewalls
- If you have at least dual ISP connections, you can setup WAN failover for high availability.
Pros:
- continuous network uptime, despite failures
- Improved fault tolerance with redundant links
- Better performance and uptime for self-hosted applications
Cons:
- More expensive setup
- Advanced configuration will be required and troubleshooting
Advanced home lab networking designs
For users who want or need enterprise-grade networking at home, the advanced home lab networking designs focus on the performance of your network, redundancy, and scalability. With this configuration, you will have the advantages of the intermediate network design with the HA configuration, adding in the spine-leaf switching architecture in the mix and adding redundant switches for your core. Your WAN connection should load balance connections and failover when needed.
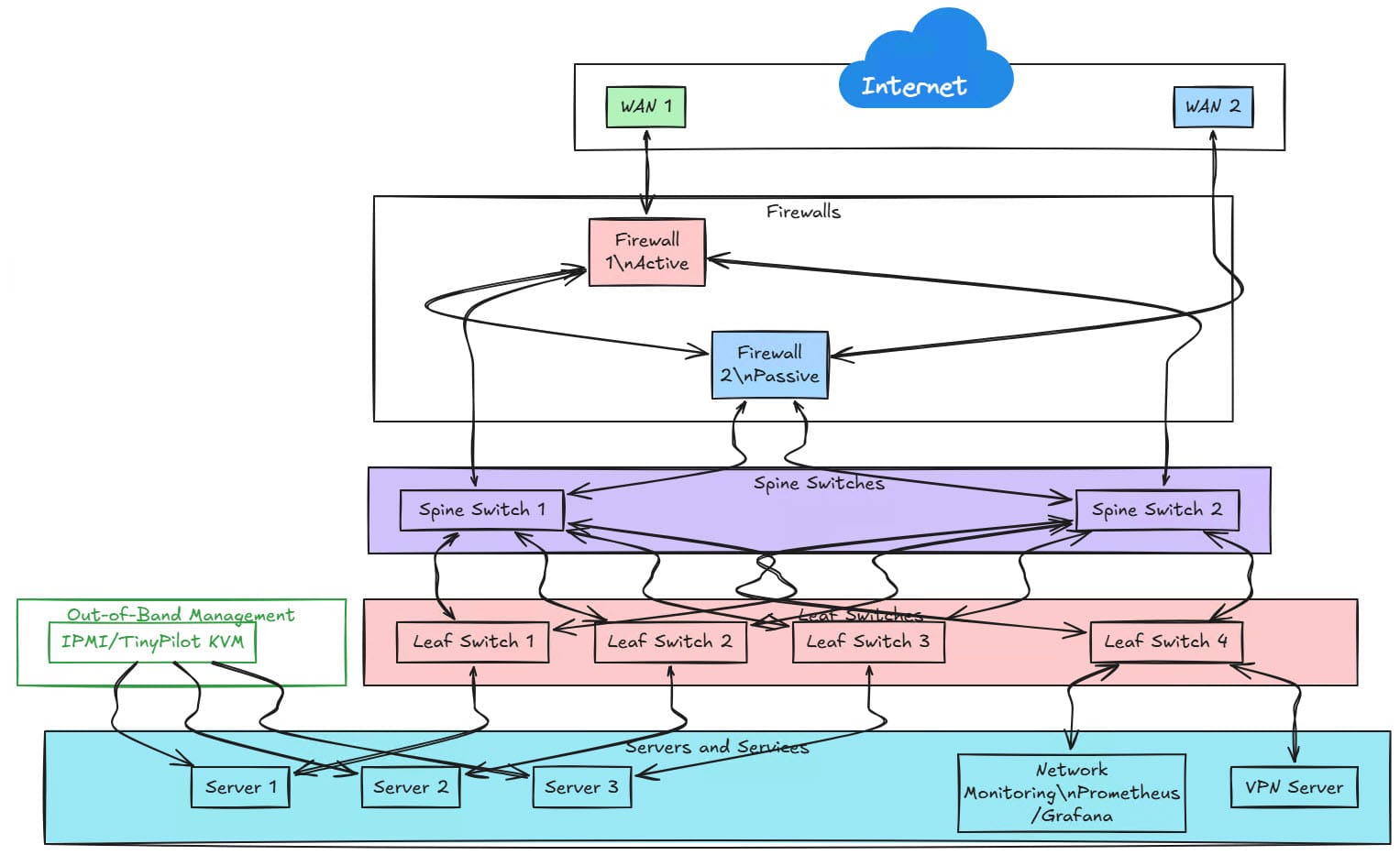
5. Fully Redundant Data Center-Grade Home Lab
This design mimics an enterprise-grade data center setup, ideal for users running production-grade workloads in a home lab.
Hardware Requirements:
- Dual firewalls (Active/Passive) with pfSense, Fortinet, Palo Alto, or another enterprise vendor
- Spine-leaf switching architecture with redundant core switches
- 10GbE or 25GbE backbone for ultra-fast networking
- Dual WAN with load balancing and failover
- Out-of-band management with IPMI or TinyPilot KVM
- Make use of advanced routing protocols like BGP
Configuration:
- Implement network monitoring tools like Prometheus, Grafana, or LibreNMS.
- Utilize multi-site VPNs for remote access.
- Deploy BGP routing for advanced network control
Pros:
- You will make the most of your uptime and redundancy with the WAN Maximum uptime with full redundancy.
- If you want to scale your home network even further, this configuration will allow you to do that
- With a 10 or 25 GbE backbone, you will have high speed and low latency connections
Cons:
- Very expensive network hardware with hardware that potentially won’t be used very often (active/passive)
- More heat generated and more power consumption
- At this stage, you have to understand advanced networking concepts, configuration, and troubleshooting
Video showing concepts
Wrapping up
Designing your home lab network can be extremely fun. It teaches you all the same skills that you will need to know when designing out a real network in the SMB or enterprise space. Many start out with the simple, flat network that is shown in the beginner home lab networking architecture, but as you get comfortable with networking in general, you can move into the more advanced beginner configuration with VLANs and into the intermediate design of networking architecture.
For a home lab, many may have no need to go with the advanced networking architecture configuration, especially due to the cost, heat, and power consumption. However, if you are studying for high-level networking certs or just want to have the same type of advanced networking that you would have in the enterprise, the advanced networking architecture will not disappoint.
Let me know what design you are rocking in your home lab. If you get stuck with a networking design or issue, create a topic on the VHT forums and we can help work through it.