New Local Administrator Protection in Windows 11: Just In Time Security to Admin Accounts!

As IT admins we all know the challenge that is the local administrator accounts on a Windows PC or endpoint. These are really a double-edged sword as they are needed in some cases. However, they are definitely teh target of attackers when compromising a Windows PC. Microsoft has announced a new Administrator Protection feature that will help to make local administrator accounts more secure, compared to the way we have been doing things with traditional UAC, etc. Let’s see how.
Table of contents
What is Administrator Protection?
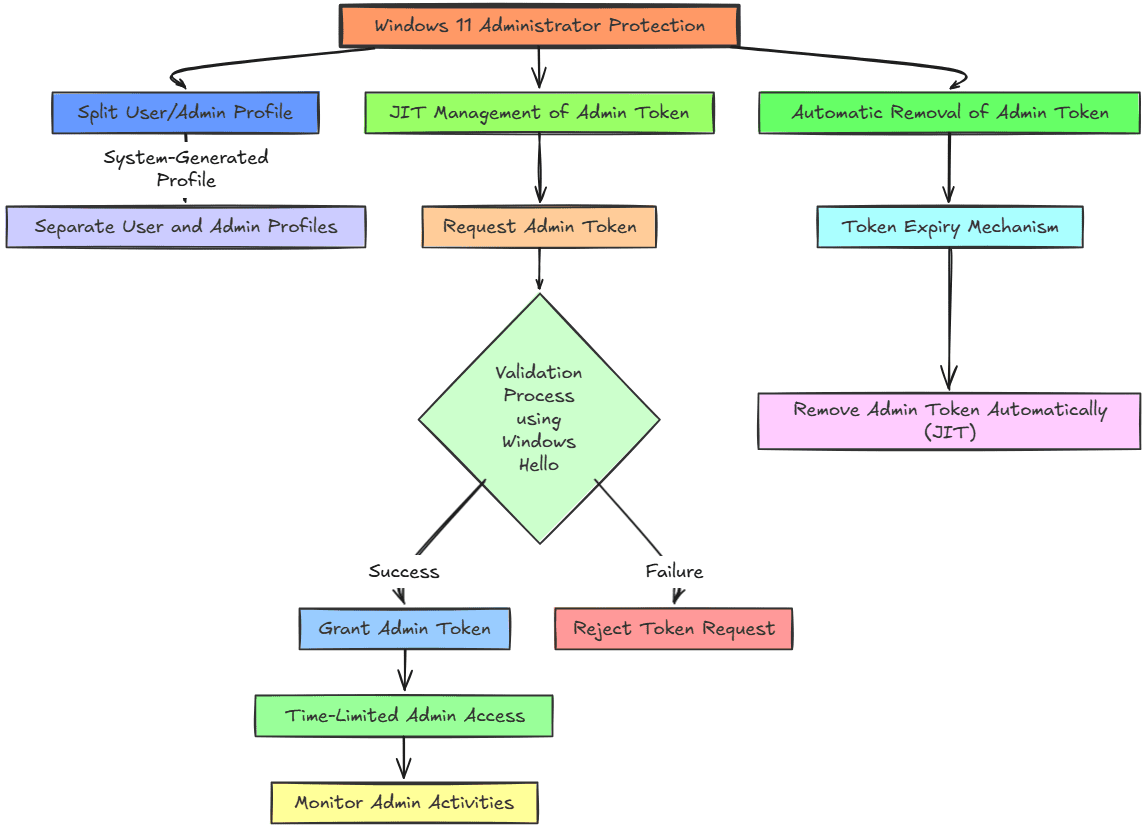
The new Administrator Protection feature is a complete overhaul of how administrator privileges are granted and managed in Windows. It introduces just-in-time (JIT) elevation and the principle of lease privilege. This helps to make it where admin rights are only available when they are absolutely needed and they are tightly controlled instead of wide open.
What are some of the features of the new Administrator Protection solution?
- Just-in-time (JIT) elevation – Just-in-time means that you are only granted elevated permissions for the exact amount of time you need to perform a specific task. With this model it limits the window of time an attacker would have to compromise an environment compared to traditional models where admin tokens stick around until the session is logged off.
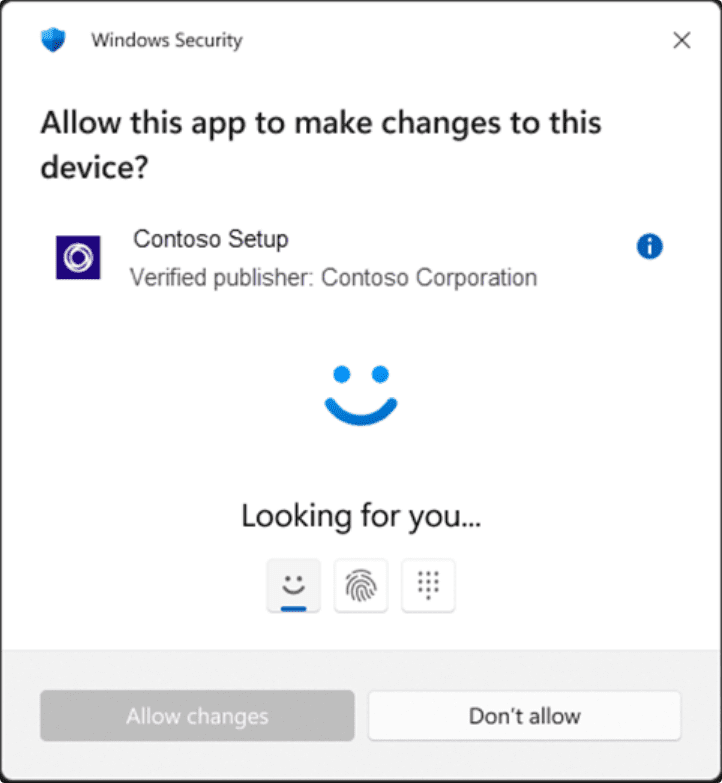
- Windows Hello authentication – When a user attempts to do something that requires admin-level privileges, they need to authenticate using Windows Hello. What this means is that it enforces identity along the way with the lifecycle of the admin task. Even if a device is compromised, authentication is still needed for elevated privileges.
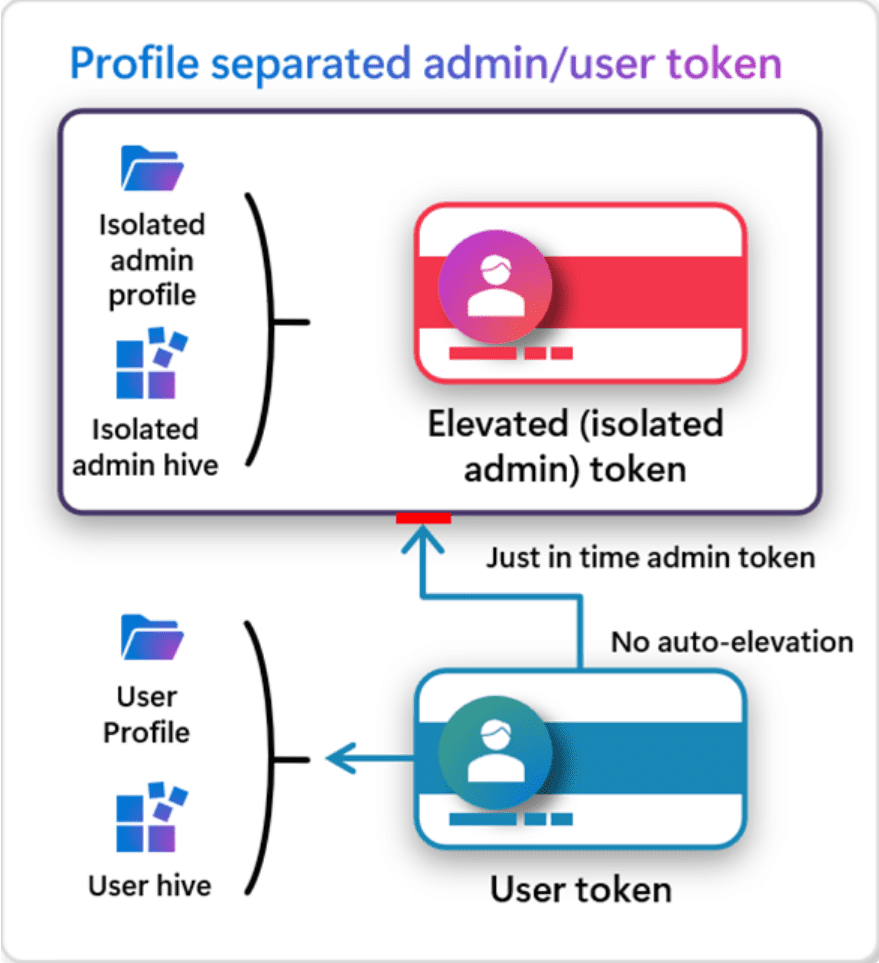
- Session isolation with Profile separation – With the new Administrator Protection feature, the system creates a new hidden and system-generated profile-separated user accounts. This means that malware that has access to the standard user session cannot compromise the elevated session.
- Interactive authorization – It eliminates the need for automatic elevations for things like processes or scripts. Each action that is an administrative action requires user approval. This helps to reinforce security by having the user in control of what runs and what doesn’t.
- Token expiration – Also the administrative tokens are automatically destroyed when the task is completed. This goes back to the JIT provisioning where the privilege is only available for the exact amount of time it is needed. This helps to make sure that the session is not elevated for longer than it is really needed.
Below is an overview of the workflow of the new local Administrator Protection feature in Windows 11:
You can read the official blog post from Microsoft on the new feature here: Administrator protection on Windows 11.
How is the new Local Administrator Protection a game changer for security?
Today, the way we have been doing things for years now, local admin rights on a Windows device are always active. It means that attackers can target a machine with active local administrative privileges and comrpromise those rights to gain control over an endpoint system.
With UAC implemented, a user operates under the standard token (standard user rights) until the admin prompt allows them to elevate their permissions to the admin context. However, once this is done, the admin privileges are there for the long-haul and don’t go away until the session ends.
This is why the Local Administrator Protection feature is really a game changer for IT admins since it will make sure that admin privileges are removed as soon as they are no longer needed.
Where and when is this available?
This will be a future GA build of Windows 11 where we will be able to get hands on with the feature. However, if you want to start playing around with it, you can install the following build:
- Windows Canary Build 27718
- A future Windows 11 release
How is Administrative Protection configured?
Let’s now talk about how this new feature will be introduced and configured in Microsoft Windows. There are three ways this can be configured currently:
- Windows Security settings
- Group Policy
- Microsoft Intune
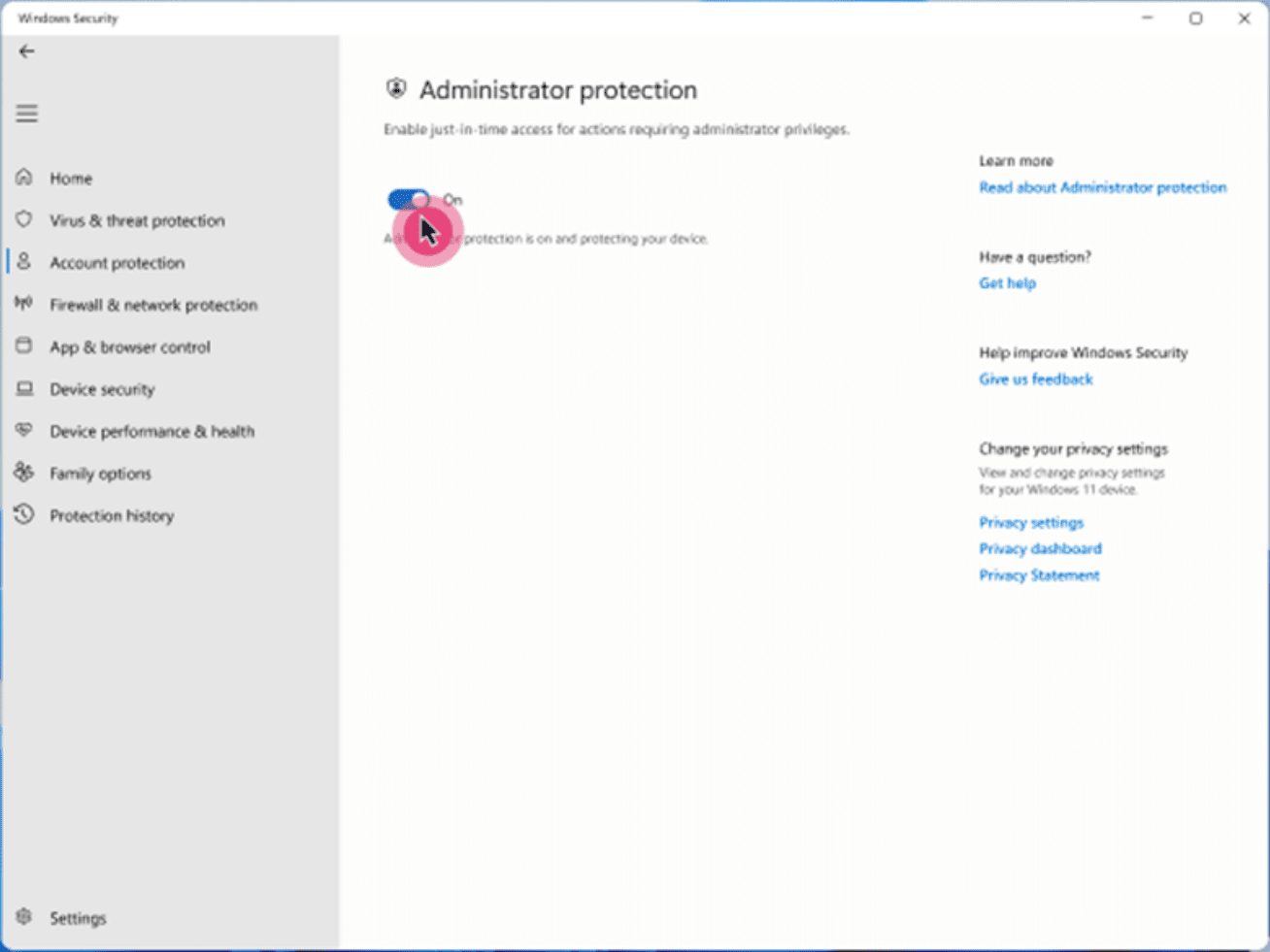
1. Windows Security settings
The first and expected way to configure the Local Administrator Protection feature is using the traditional Windows Security settings screen. This is a screenshot provided by Microsoft showing the forthcoming setting in a future Windows 11 build allowing a simple toggle of Administrator Protection.
2. Group Policy
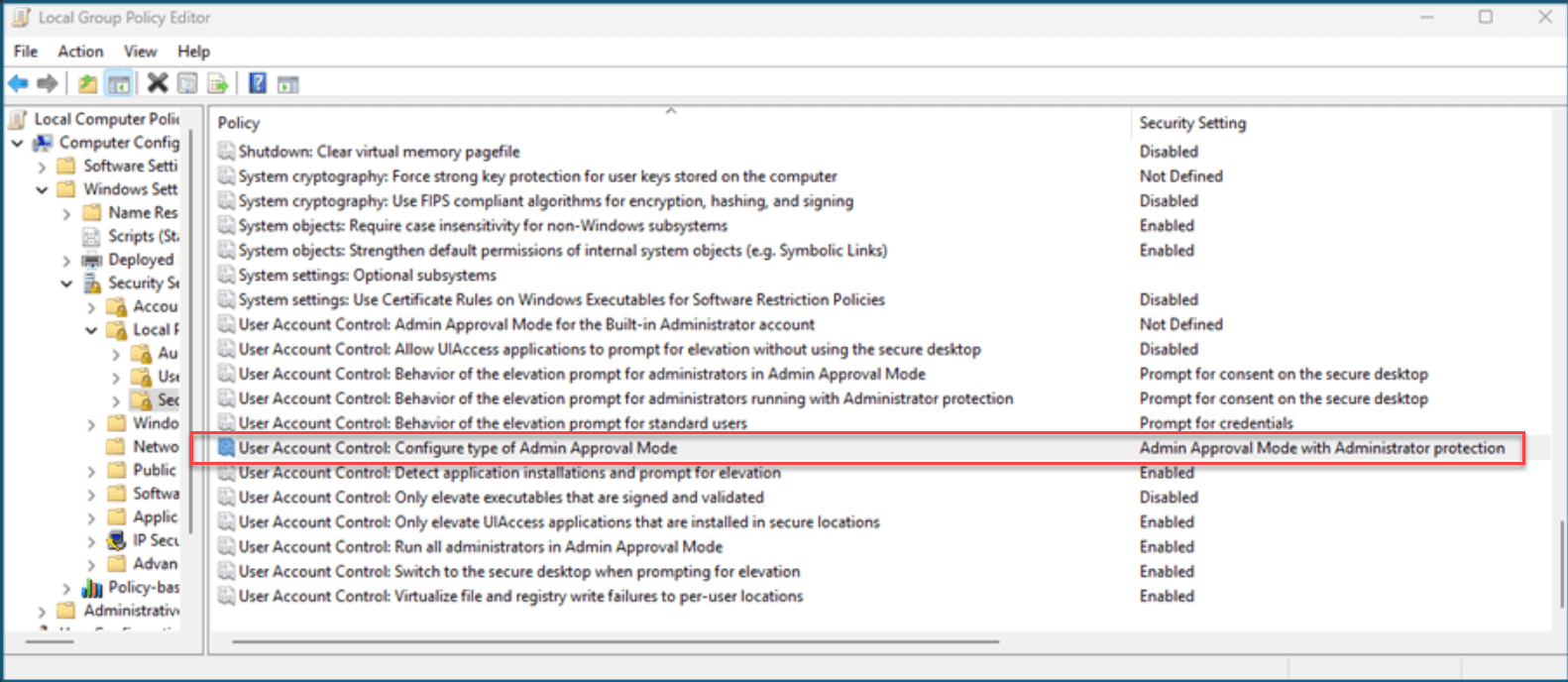
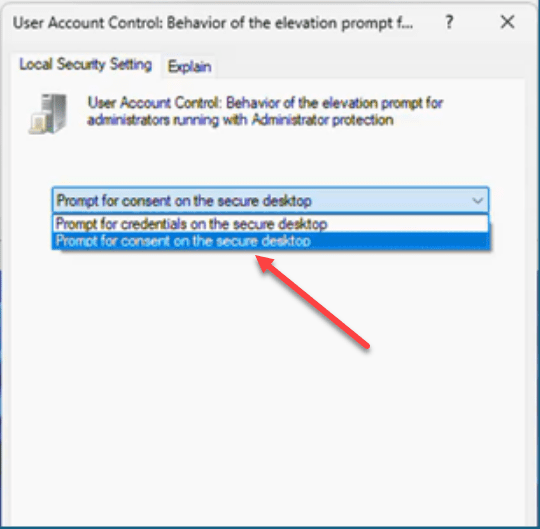
The next way this can be configured is by using Group Policy. Below we can see the following setting:
- Computer Configuration -> Windows Settings -> Security Settings -> Local Policies -> Security Options
- User Account Control: Configure Type of Admin Approval Mode > Admin Approval Mode With Administrator Protection
Below, you can see one of the configuration settings for changing the prompt behavior. You can set this to Prompt for consent on the secure desktop.
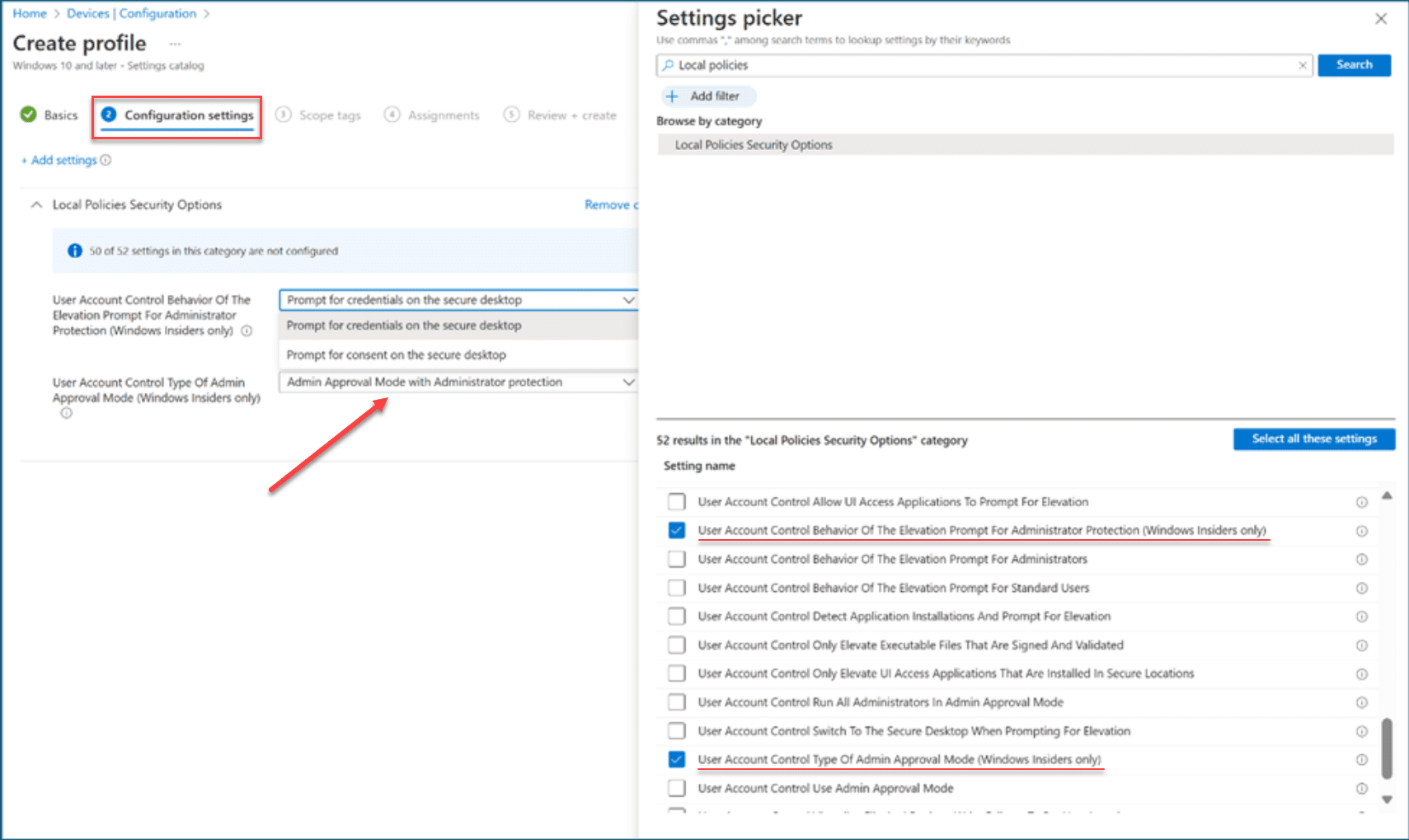
3. Microsoft Intune and LocalPoliciesSecurityOptions CSP
To turn on Administrator protection using Microsoft Intune, note the following overview of steps:
- Create a security group and enroll your users in that group
- Set up the Administrator protection policy using the settings catalog.
- Add the security group to the policy
- Intune will sync at its regular intervals to apply the policy to a device
- Restart the devices
To enable this in LocalPoliciesSecurityOptions CSP configure UserAccountControl_TypeOfAdminApprovalMode. To select between consent and credential, you can use the setting UserAccountControl_BehaviorOfTheElevationPromptForAdministratorProtection node.
Wrapping up
This is a great new feature that I think will help take Windows security to the next level. We all have seen that identity is arguably the number one target of attackers. By helping to secure the lcoal administrator credential security in Windows endpoints running Windows 11, this will drastically reduce the attack surface with the JIT security and truely separated standard user/admin accounts and profiles. Microsoft is definitely making strides to help secure the local administrator provilege with this new configuration of local administrator protection.
Also, what is nice is that it isn’t some long and complicated configuration process. It is a simple toggle in Windows Security and a couple of settings in Group Policy and Microsoft Intune. However, the implications and benefits of those simple settings will be major on the security front.