There are many different components with a working Kubernetes installation. However, one of the most important when it comes to getting traffic into your Kubernetes and serving out application is the Kubernetes ingress. However, if you have implemented the Kubernetes ingress in your cluster using something like Traefik, let’s look at hot to check if Kubernetes ingress worked. We can look at logs and other indicators to know, specifically if the resource is reachable.
Table of contents
What is a Kubernetes ingress?
When you look at what the Kubernetes ingress really is, it is an API object that is created that allows Kubernetes to manage external access to services in a cluster. Usually this is referring to HTTP or HTTPs routes to resources located in the cluster. It also allows you to expose multiple apps inside your cluster on the same IP address much like you would do with host headers in a traditional web server. It also performs things like load balancing, SSL termination, and routing based on path.
Below are some of the features that we can say are served by a Kubernetes ingress:
- HTTP and HTTPS Routing: HTTP(S) requests are directed to the right backend services based on which rules you have defined
- Path-based Routing: Requests are routed to different services based on the URL path. For instance,
/app1to Service A,/app2to Service B. - Host-based Routing: You can route traffic based on the hostname in the request (much like host headers). If the name is app1.mydomain.com it will go to service A, and if it is app2.mydomain.com it will route to service B.
- Load Balancing: The ingress can also distribute traffic coming in across multiple service endpoints (Pods) for better performance and also improves reliability.
- SSL/TLS Termination: This is one of the most important features. It can allow SSL/TLS encryption and termination for your applications.
- Customizable Rules: It supports things called annotations that allow configurations for advanced traffic management.
What is Traefik?
One of the most popular ingress controllers is Traefik. It is an open-source proxy and load balancer that allows you to manage your apps running inside your Kubernetes cluster. It helps to orchestrate environments including Kubernetes, but also Docker and Docker Swarm, Consul, and others.
You can do SSL termination with Traefik as well as path-based and host-based routing. It also does something called middleware that allows you to transform requests coming in. Used as an ingress controller it can dynamically handle HTTP and HTTPS requests coming in based on the ingress resources you configure and define.
Learn more about Traefik and download it here: Traefik Labs.
What does a Traefik ingress look like?
Take a look at the following ingress I have defined in my home lab for ArgoCD. Just a few things to call out in the code below:
- You see the certresolver is configured as letsencrypt
- The host in the annotations is defined as argocd.mydomain.cloud
- The spec rules defined are for host routing for the host argocd.mydomain.cloud
So, with this configuration, we are using Let’s Encrypt and we are routing based on the host name.
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: argocd-ingress-1
namespace: argocd
uid: 3beecab8-67b6-45e0-b598-933d64349f33
resourceVersion: '725389'
generation: 3
creationTimestamp: '2024-11-25T03:47:12Z'
labels:
app: argocd
k8slens-edit-resource-version: v1
annotations:
kubectl.kubernetes.io/last-applied-configuration: >
{"apiVersion":"networking.k8s.io/v1","kind":"Ingress","metadata":{"annotations":{"traefik.ingress.kubernetes.io/router.entrypoints":"websecure","traefik.ingress.kubernetes.io/router.tls":"true","traefik.ingress.kubernetes.io/router.tls.certresolver":"letsencrypt","traefik.ingress.kubernetes.io/service.serversscheme":"http"},"labels":{"app":"argocd"},"name":"argocd-ingress-1","namespace":"argocd"},"spec":{"ingressClassName":"traefik","rules":[{"host":"argocd.mydomain.cloud","http":{"paths":[{"backend":{"service":{"name":"argocd-server","port":{"number":80}}},"path":"/","pathType":"Prefix"}]}}]}}
traefik.ingress.kubernetes.io/router.entrypoints: websecure
traefik.ingress.kubernetes.io/router.tls: 'true'
traefik.ingress.kubernetes.io/router.tls.certresolver: letsencrypt
traefik.ingress.kubernetes.io/service.serversscheme: http
selfLink: /apis/networking.k8s.io/v1/namespaces/argocd/ingresses/argocd-ingress-1
status:
loadBalancer: {}
spec:
ingressClassName: traefik
rules:
- host: argocd.mydomain.cloud
http:
paths:
- path: /
pathType: Prefix
backend:
service:
name: argocd-server
port:
number: 80How to see if a configured ingress worked
How do you know if a configured ingress worked? Well, it may seem obvious, but one of the first things to do is simply open a web browser and see if you can get to the intended service that you have configured the ingress for.
If you get a page cannot be displayed or the any of the following:
- Error 404
- Error 500 (Internal Server Error)
- or other…
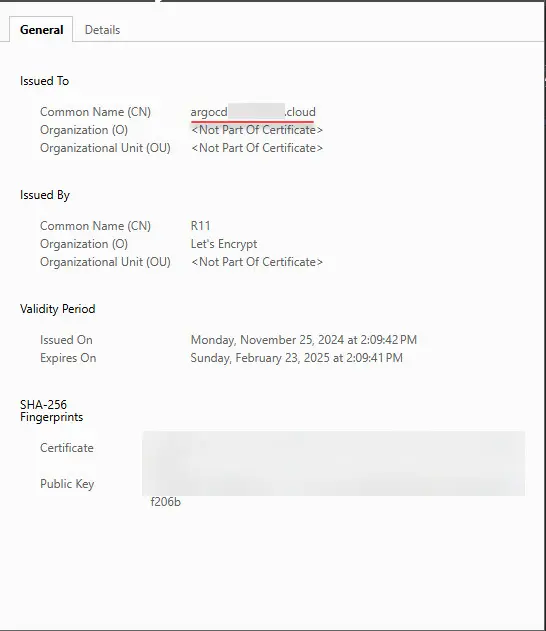
If you do get to your service, check the security tab in the browser tools to see the security information presented on the cert. If you have configured Let’s Encrypt, you will want to make sure the correct certificate has been pulled and you are not getting a cert error:
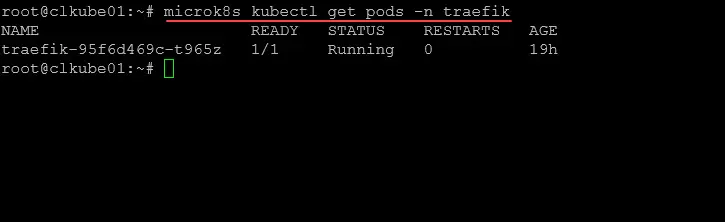
OK, so you did get an error. Where do you look? Logs are your best friend. The first place to take a look is in your Traefik logs. You can see your Traefik pod name by running the following command if you
kubectl get pod -n traefikOnce you get the traefik pod name, you can view the logs with the following command:
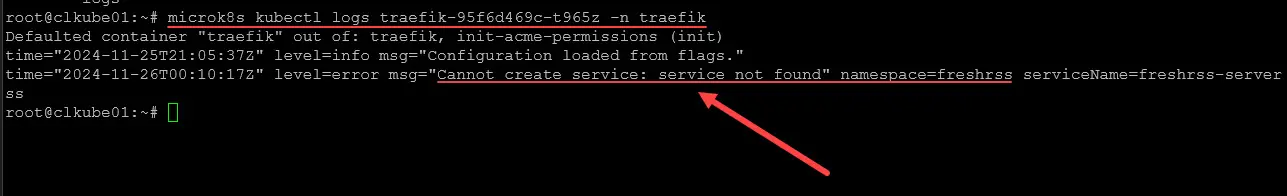
kubectl logs <your traefik pod name> -n traefikBelow, we see in the logs an error routing traffic to a freshrss service in Kubernetes. It is saying the service is not found. So, we have an issue with the service configuration.
Getting, editing, and deleting ingresses
You can easily get your configured ingresses with the command:
kubectl get ingress -n <namespace>Once you have found your ingress, you can edit it or delete it if needed. To edit your ingress:
kubectl edit ingress -n <namespace>To delete your ingress:
kubectl delete ingress -n <namespace>To add an ingress, you need to create your YAML code and apply it using the apply command:
kubectl apply -f ingress.ymlA blueprint of generic code for a minimal ingress looks like the following:
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: minimal-ingress
annotations:
nginx.ingress.kubernetes.io/rewrite-target: /
spec:
rules:
- http:
paths:
- path: /testpath
pathType: Prefix
backend:
service:
name: test
port:
number: 80Wrapping up
Kubernetes ingress configurations are vital to be able to be able to get traffic into your Kubernetes cluster efficiently and do things like load balancing, SSL termination, and app or host-based routing. Traefik is one of the most popular ingress controllers and is open-source, free to use. It lends itself very well to GitOps operations and tasks. Hopefully the above few steps will help you on how to check if Kubernetes ingress worked with your ingress controller, such as Traefik.
Google is updating how articles are shown. Don’t miss our leading home lab and tech content, written by humans, by setting Virtualization Howto as a preferred source.