Well, it seems like the vulnerabilities for vCenter Server and other vSphere components never end. There is a new security advisory that actually helps to continue to close off a vulnerability showcased at a Chinese hacking contest. While VMware released a patch for the heap overflow in September 2024 this year, this vCenter Server critical patch continues to address this issue, as we will see below.
Table of contents
1. CVE-2024-38812: Heap-Overflow Vulnerability
This is a vulnerability that affects the DCERPC protocol which can allow an attacker that has only network access to be able to trigger remote code deployment by sending a packet that is specially crafted to your vCenter Server. This is the vulnerability of the security advisory that has a base score of CVSSv3 9.8 and is critical to get patched.
You can read more about this latest vCenter Server security issue on VMware’s Security Advisory Page.
Attack Vectors
If an attacker is able to have line-of-sight network access to your vCenter Server, they can attack the server using the specially crafted network payload that exploits the vulnerability. If your vCenter Server is exposed to less secure networks in the environment, this can definitely be an easy target for an attacker that already has a foothold in the environment on a compromised workstation, etc.
Resolution
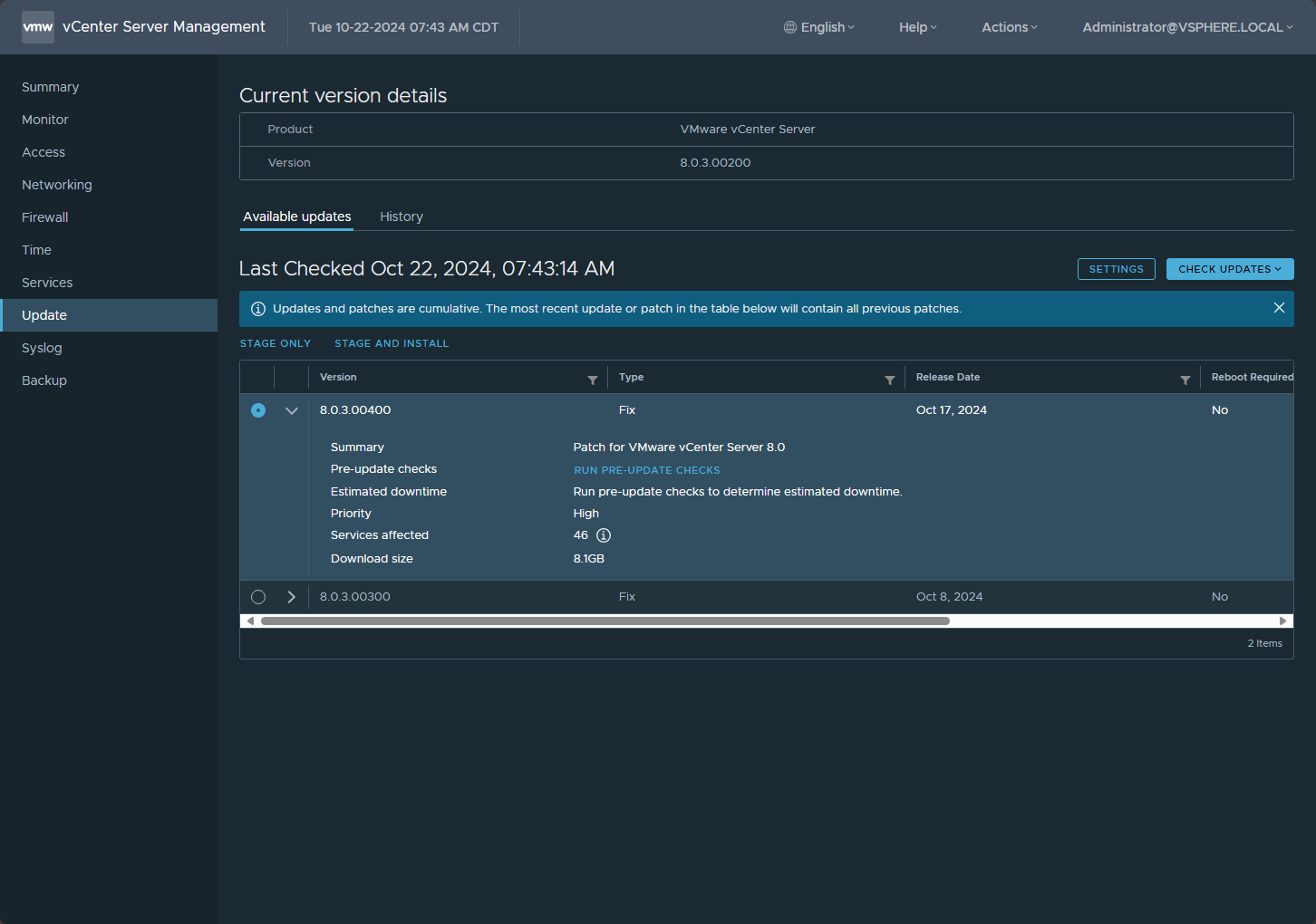
There are new patched versions of vCenter Server as a result of remediating this vulnerability. Even though there was an initial patch to address this issue released on September 17, 2024, VMware has since discovered the issue was not fully addressed. They said the following:
“VMware by Broadcom has determined that the vCenter patches released on September 17, 2024, did not fully address CVE-2024-38812“
As a result, it has released the updated patches as part of the new security advisory. These include:
- vCenter Server 8.0 U3d
- vCenter Server 8.0 U2e
- vCenter Server 7.0 U3t
Workarounds?
There are no workarounds, according to VMware, as these were explored but not viable to really protect your vCenter Server. So, you need to patch.
2. CVE-2024-38813: Privilege Escalation Vulnerability
There is another vulnerability contained in the CVE-2024-38813 security vulnerability that allows attackers to escalate privileges on your vCenter Server using specially crafted network packets. This one is an important level advisory with a CVSSv3 score of 7.5
Attack Vectors
If an attacker has access over the network to your vCenter Server, they can escalate privileges to root, giving them the ability to do anything they want with vCenter and compromising your entire environment.
Patch Availability and Versions
The following patches are available in the VMware Response Matrix:
- VMware vCenter Server 8.0 U3d
- VMware vCenter Server 8.0 U2e
- VMware vCenter Server 7.0 U3t
- VMware Cloud Foundation 5.x (Async patches to vCenter Server 8.0 U3d and 8.0 U2e)
These updates have been released and fully address the vulnerabilities. VMware Cloud Foundation admins also need to follow the Async Patching Guide (KB88287) for detailed instructions.
No Workarounds Available
VMware has confirmed that no in-product workarounds are effective for these critical vulnerabilities. The only way to make sure you are protected from the vulnerabilities is to get your vCenter Server patched.
Impact and Recommendations
The combination of a heap-overflow and privilege escalation vulnerability poses a serious threat to any infrastructure running vulnerable versions of vCenter Server. The critical nature of CVE-2024-38812, with its potential for remote code execution, makes patching an urgent priority for all affected organizations. Additionally, the privilege escalation vulnerability CVE-2024-38813 could enable attackers to gain root-level access, further increasing the risks associated with delayed patching.
Key Recommendations:
- Apply patches immediately: Given the critical severity of these vulnerabilities, organizations should prioritize updating their vCenter Server installations to the patched versions listed in the Response Matrix.
- Review network exposure: Ensure that vCenter Server is not exposed unnecessarily to insecure networks or the public internet, which could minimize the risk of external exploitation.
- Monitor VMware security advisories: Stay informed on future updates, as this is not the first time a patch has required a re-issue to address incomplete fixes.
Wrapping up
It seems like it has been a rough year of VMware vulnerabilities. However, when you are the leader of the pack, you can expect to be a target. Ransomware gangs, especially, are now targeting environments at the hypervisor level as they know this is the worst-case scenario for businesses. So, it is extremely important to stay on top of your environment with patches to make sure you are protected from ransomware and other types of security vulnerabilities.
Google is updating how articles are shown. Don’t miss our leading home lab and tech content, written by humans, by setting Virtualization Howto as a preferred source.