In looking at Windows Server 2025 and security configuration settings, there is a new tool that Microsoft has introduced called OSConfig. In case you haven’t heard of it, this blog post is for you! We will take a look at this new OSConfig PowerShell security tool in Windows Server 2025 what OSConfig is exactly, how you install it, and how you use it.
Table of contents
What is the OSConfig utility?
The OSConfig utility is a command line utility for managing OS system settings on Windows devices in enterprise environment. With it, admins can automate and control various things, like system configurations, updates, security settings, and other policy settings like compliance.
You can use it to manage things in cloud environments, Azure, as well as integrate with other management tools. This is a great way to set up configs at scale, system updates, and monitor compliance with policies.
Install OSConfig
There are a few commands that we need to run to get OSConfig installed. I am running this on a Windows Server 2025 preview build in the lab environment.
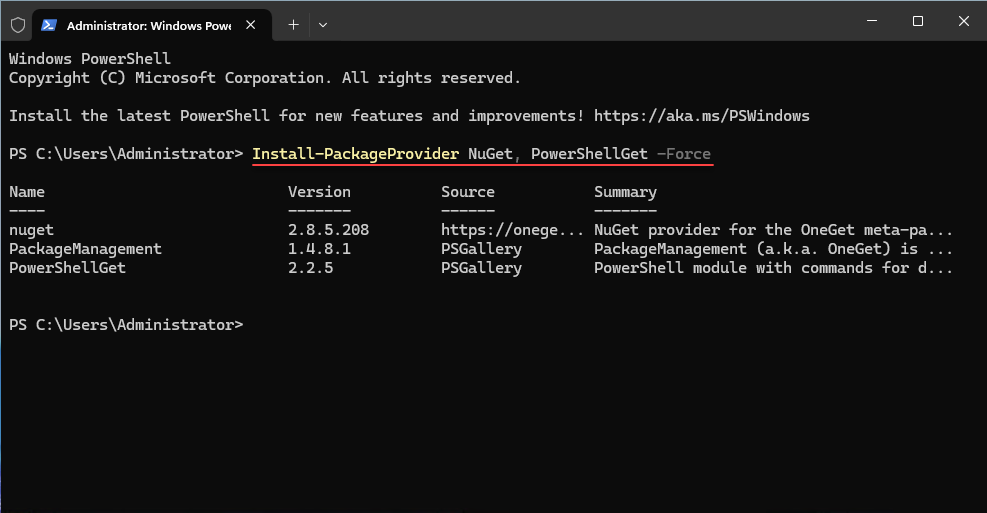
Install-PackageProvider NuGet, PowerShellGet -ForceThen run:
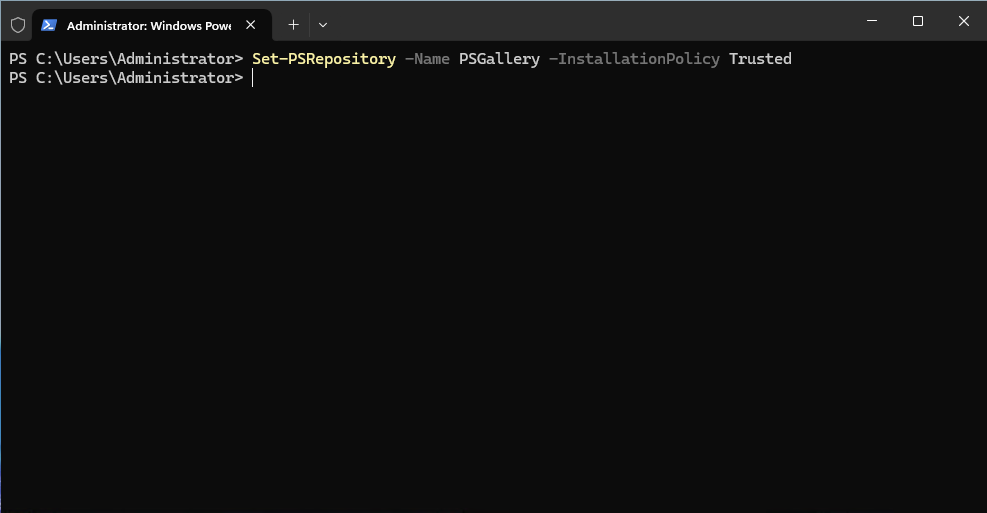
Set-PSRepository -Name PSGallery -InstallationPolicy TrustedTo install it:
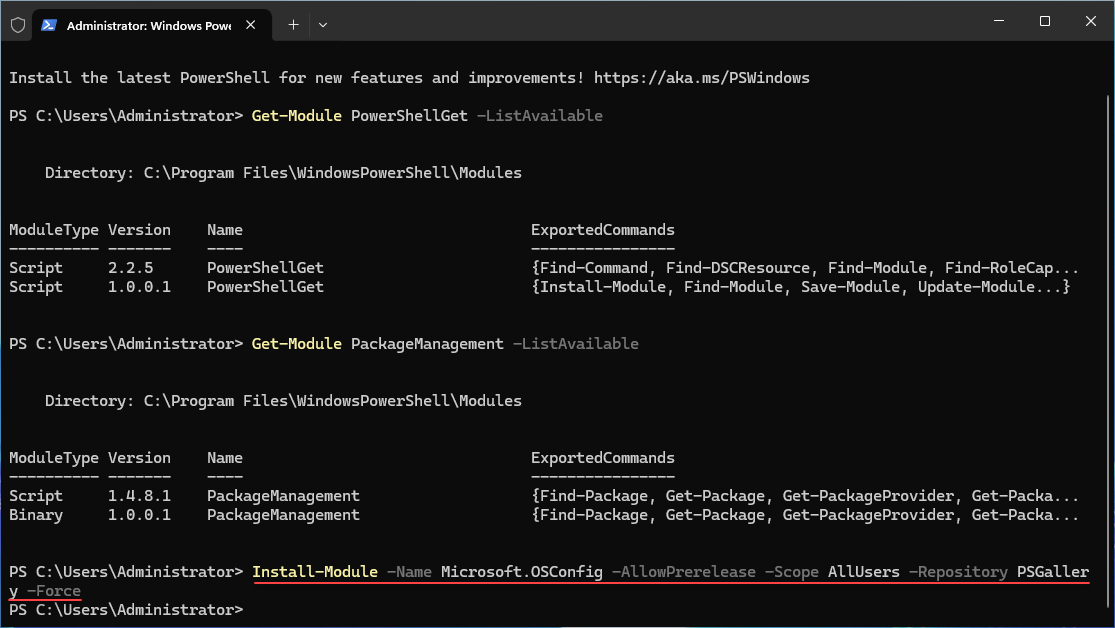
Install-Module -Name Microsoft.OSConfig -AllowPrerelease -Scope AllUsers -Repository PSGallery -ForceYou can verify it was installed with:
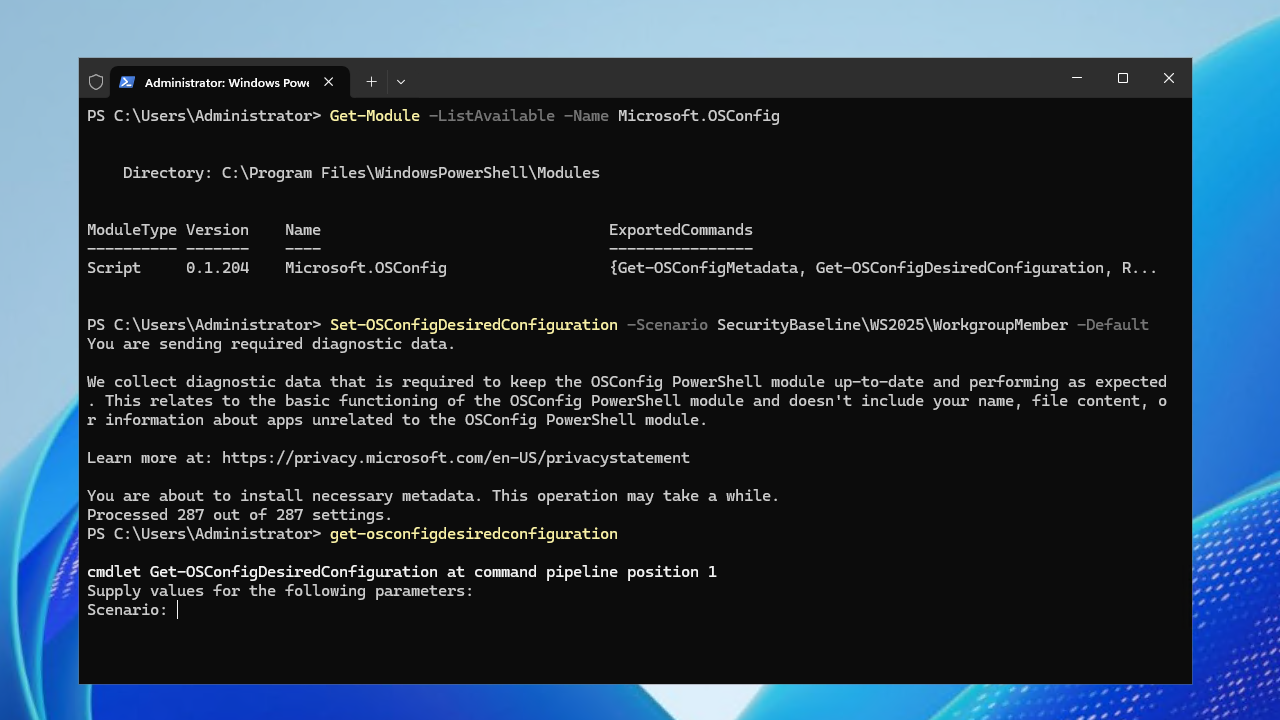
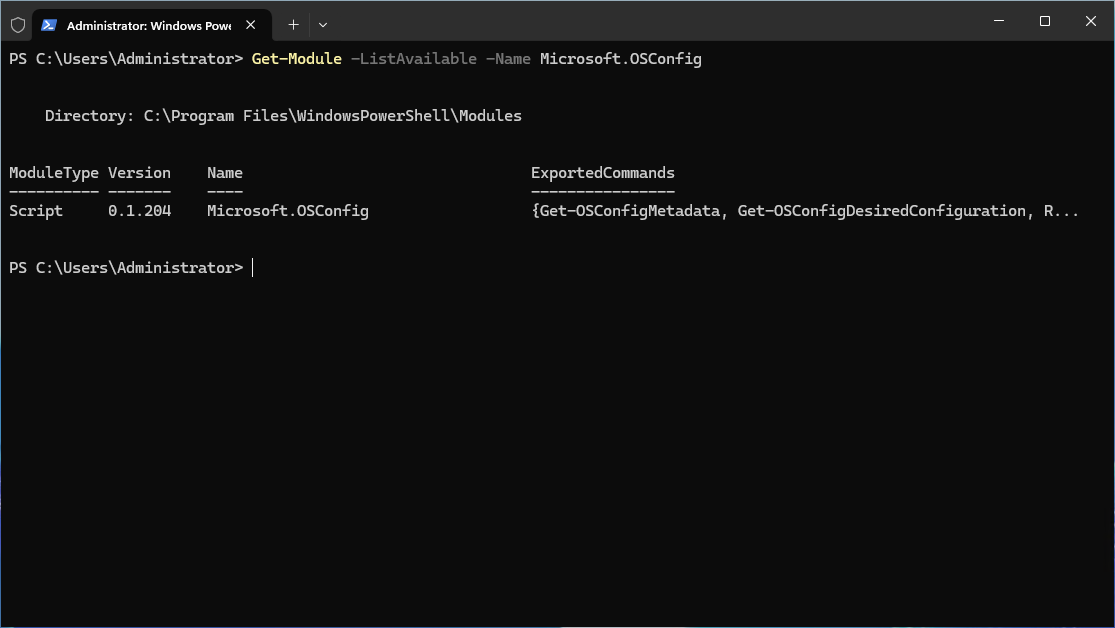
Get-Module -ListAvailable -Name Microsoft.OSConfigUsing it to apply security baselines
One of the really neat things we can do with the OSConfig utility is apply security baselines using the PowerShell cmdlets. Take a look at the example commands:
For a domain-joined device
Set-OSConfigDesiredConfiguration -Scenario SecurityBaseline\WS2025\MemberServer -DefaultFor a workgroup device:
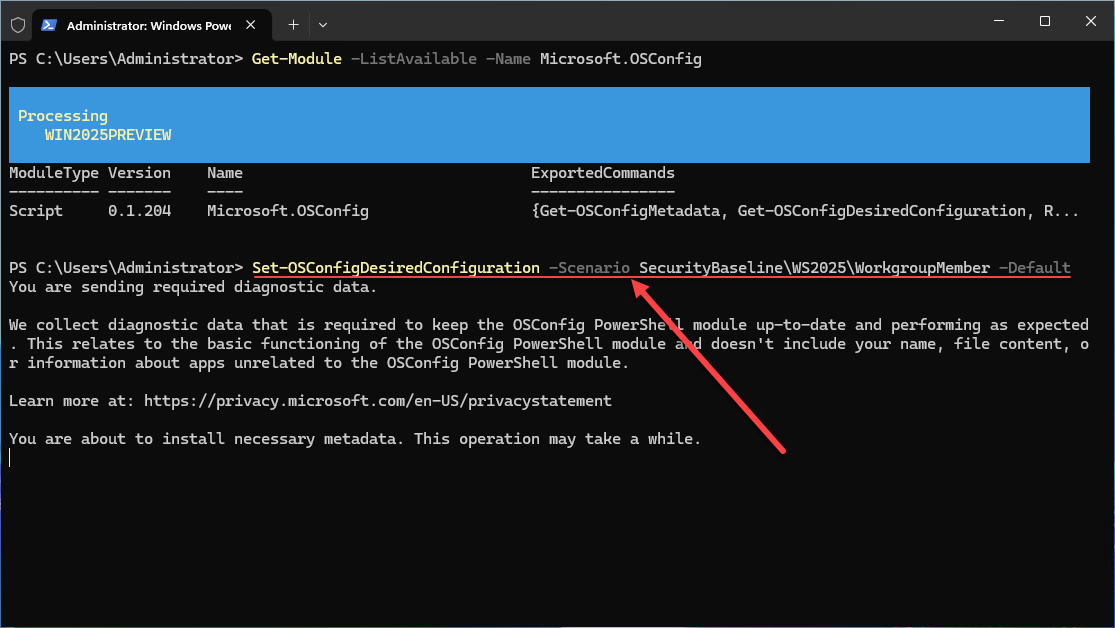
Set-OSConfigDesiredConfiguration -Scenario SecurityBaseline\WS2025\WorkgroupMember -Default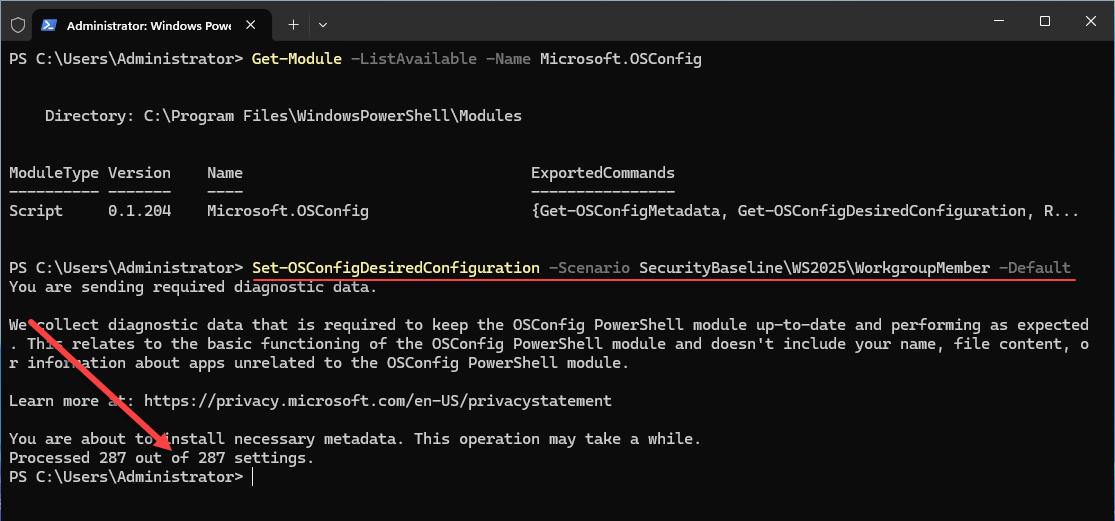
A domain controller:
Set-OSConfigDesiredConfiguration -Scenario SecurityBaseline/WS2025/DomainController -DefaultFor secured-core:
Set-OSConfigDesiredConfiguration -Scenario SecuredCore -DefaultFor Defender Antivirus:
Set-OSConfigDesiredConfiguration -Scenario Defender\Antivirus -DefaultCustomizing security baseline settings
One of the useful things you can do with the OSConfig utility is customize security baselines using PowerShell cmdlets. Here’s how you can customize and check compliance for specific settings:
For customizing AuditDetailedFileShare on a Member Server (where the default value is 2):
Set-OSConfigDesiredConfiguration -Scenario SecurityBaseline\WS2025\MemberServer -Name AuditDetailedFileShare -Value 3To verify the change:
Get-OSConfigDesiredConfiguration -Scenario SecurityBaseline\WS2025\MemberServer -Name AuditDetailedFileShareCheck that the value has now been set to 3.
For viewing the compliance status of the Security Baseline via PowerShell cmdlets, run the following commands:
Get-OSConfigDesiredConfiguration -Scenario SecuredCoreStateTo get a more detailed compliance report for a Member Server:
Get-OSConfigDesiredConfiguration -Scenario SecurityBaseline\WS2025\MemberServer | ft NameOSConfig Drift Control
OSConfig helps to maintain a desired state by continuously monitoring and then remediating settings that may have changed or drifted compared to the settings in the baseline.
- Set Desired Configuration: You first need to apply the desired configuration for a specific scenario using the
Set-OSConfigDesiredConfigurationcmdlet.Set-OSConfigDesiredConfiguration -Scenario SecurityBaseline\WS2025\MemberServer -Name <SettingName> -Value <DesiredValue> - Continuous Monitoring: OSConfig automatically enables drift control for scenarios where it is configured. The OSConfig tool checks whether the current configuration matches the desired configuration you have applied. If it detects drift, OSConfig will try to bring the configuration back to the intended state.
- Check Compliance/Drift Status: You can view the current compliance stance (whether drift has occurred), you can use the
Get-OSConfigDesiredConfigurationcmdlet, which will show you the compliance status and any reasons for non-compliance (drift).Get-OSConfigDesiredConfiguration -Scenario SecurityBaseline\WS2025\MemberServer | ft Name, @{ Name = "Status"; Expression={$_.Compliance.Status} }, @{ Name = "Reason"; Expression={$_.Compliance.Reason} } -AutoSize -Wrap - Remediation: If drift happens, OSConfig will attempt to automatically remediate it by reapplying the desired configuration. However, in some cases where this may not be possible, you may need to manually enforce the configuration by running the
Set-OSConfigDesiredConfigurationcommand again.
Just so you know, drift control is implicitly enabled once a desired configuration is applied. You can monitor drift by regularly checking compliance, and OSConfig ensures that any deviations from the baseline are detected and corrected to maintain the intended security posture.
Common Tasks Impacted and Known Issues After Applying the Baseline
- Password Requirements: Local user accounts must have a minimum of 14 characters with password complexity enforced. For domain accounts, domain-specific password policies will apply.
- TLS Connections: Only TLS/DTLS 1.2 or higher is supported, which may block connections to older systems that do not support these protocols.
- Copy/Paste in RDP Sessions: Copy/paste functionality in Remote Desktop Protocol (RDP) sessions is disabled by default. You can turn this back on, run the following command in an elevated PowerShell session: code
Set-OSConfigDesiredConfiguration -Scenario SecurityBaseline\WS2025\[role being applied] -Name RemoteDesktopServicesDoNotAllowDriveRedirection -Value 0After running the command, you will need to reboot. - SMB Connections: SMB 3.0 or higher is required for connections (available since Windows Server 2012). If connecting to non-Windows systems like Linux SAMBA, you will need to make sure they support SMB 3.0, or adjust the baseline settings accordingly.
- User Rights Errors: You may run into user rights assignment errors based on your domain configuration. These do not have an impact on the overall security baseline and they can be safely ignored.
- Configuration Conflicts: If you’re configuring the same settings with multiple tools (including OSConfig), conflicts may occur. So you will need to keep this in mind, especially with drift control enabled.
If you have issues after using OSConfig and applying a security baseline:
- Test the security baseline only on non-production systems. While there is a ‘Remove’ command, not all settings can be reverted.
- To remove the applied baseline, open an elevated PowerShell window and run:
Remove-OSConfigDesiredConfiguration -Scenario SecurityBaseline\WS2025\MemberServerThen, reboot the system.
Wrapping up
The new OSConfig PowerShell security tool in Windows Server 2025 is a great way to have desired state on your servers and have them automatically conform to a specific compliance stance. It will automatically detect drift and attempt to remediate the drift that is detected which is a great way to keep servers secure and in compliance. This is also a great way to have security and compliance at scale if you need to roll out these settings to many Windows Servers.
Google is updating how articles are shown. Don’t miss our leading home lab and tech content, written by humans, by setting Virtualization Howto as a preferred source.