Critical VMware vCenter Server Patch VMSA-2024-0019 – Upgrade Now!

In case you haven’t seen as of yet today, VMware has released a critical patch for VMware vCenter Server, noted in VMSA-2024-0019 for vulnerabilities: CVE-2024-38812, CVE-2024-38813. Let’s look at the vulnerabilities, the severity, any workarounds, and the process to get your VMware vCenter Server patched.
Table of contents
CVE-2024-38812 – Heap-overflow vulnerability
This is the worse of the two vulnerabilities fixed in this new patch release. Using a specially crafted network packet, an attacker can send this to your vCenter Server and take advantage of a heap-overflow vulnerability in the DCERPC protocol. The criticality of this vulnerability is critical, carrying a CVSSv3 score of 9.8 which is about as bad as it gets.
There are no workarounds for this vulnerability that are listed in the official VMSA KB article for this vulnerability. The only resolution is to get your vCenter Server patched to the latest version in the fixed versions for your particular vCenter Server.
CVE-2024-38813 – Privilege escalation vulnerability
VMware vCenter Server also contains a privilege escalation vulnerability to be aware of. This particular vulnerability has a CVSSv3 score of 7.5. With this vulnerability, the attacker also just has to be the network to “see” the vCenter Server. They can then snd a specially crafted network packet to the server and escalate privileges to root.
Again, with this vulnerability, there is no workaround. You will want to apply the known fix for the vulnerability as soon as possible.
Below is the relevant patching matrix from VMware on the vulnerabilities:
| VMware Product | Version | Running On | CVE | CVSSv3 | Severity | Fixed Version | Workarounds | Additional Documentation |
| vCenter Server | 8.0 | Any | CVE-2024-38812, CVE-2024-38813 | 9.8, 7.5 | Critical | 8.0 U3b | None | FAQ |
| vCenter Server | 7.0 | Any | CVE-2024-38812, CVE-2024-38813 | 9.8, 7.5 | Critical | 7.0 U3s | None | FAQ |
| VMware Cloud Foundation | 5.x | Any | CVE-2024-38812, CVE-2024-38813 | 9.8, 7.5 | Critical | Async patch to 8.0 U3b | None | Async Patching Guide: KB88287 |
| VMware Cloud Foundation | 4.x | Any | CVE-2024-38812, CVE-2024-38813 | 9.8, 7.5 | Critical | Async patch to 7.0 U3s | None | Async Patching Guide: KB88287 |
Before updating
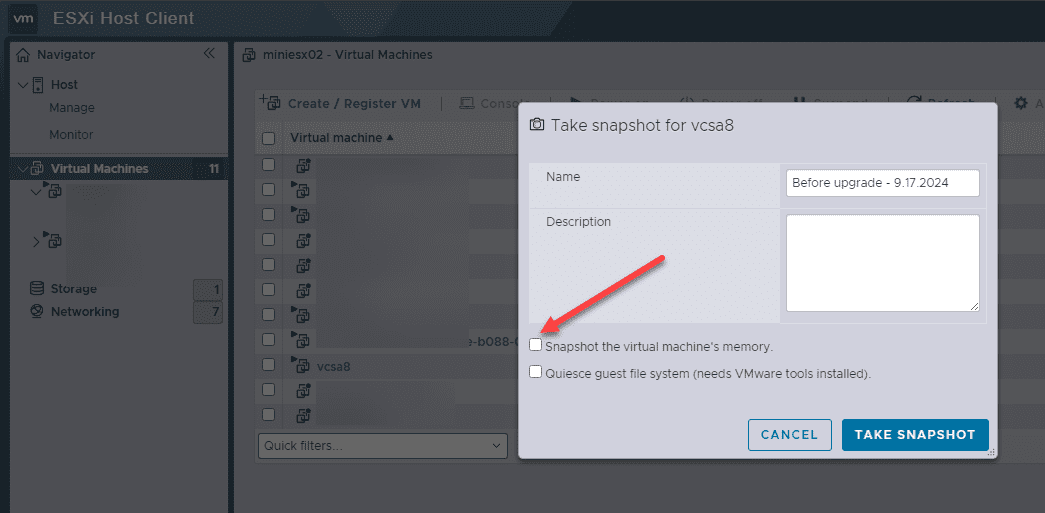
Before you update your VMware vCenter Server appliance for the critical vulnerability, you can take a non-memory snapshot of the appliance to have a fail-safe in case something happens during the upgrade process.
Log in to the ESXi host that “owns” vCenter and then create a non-memory snapshot on the VCSA appliance VM.
Now, we can proceed to actually pulling, staging, and applying the update for the critical vulnerability.
Patching vCenter Server
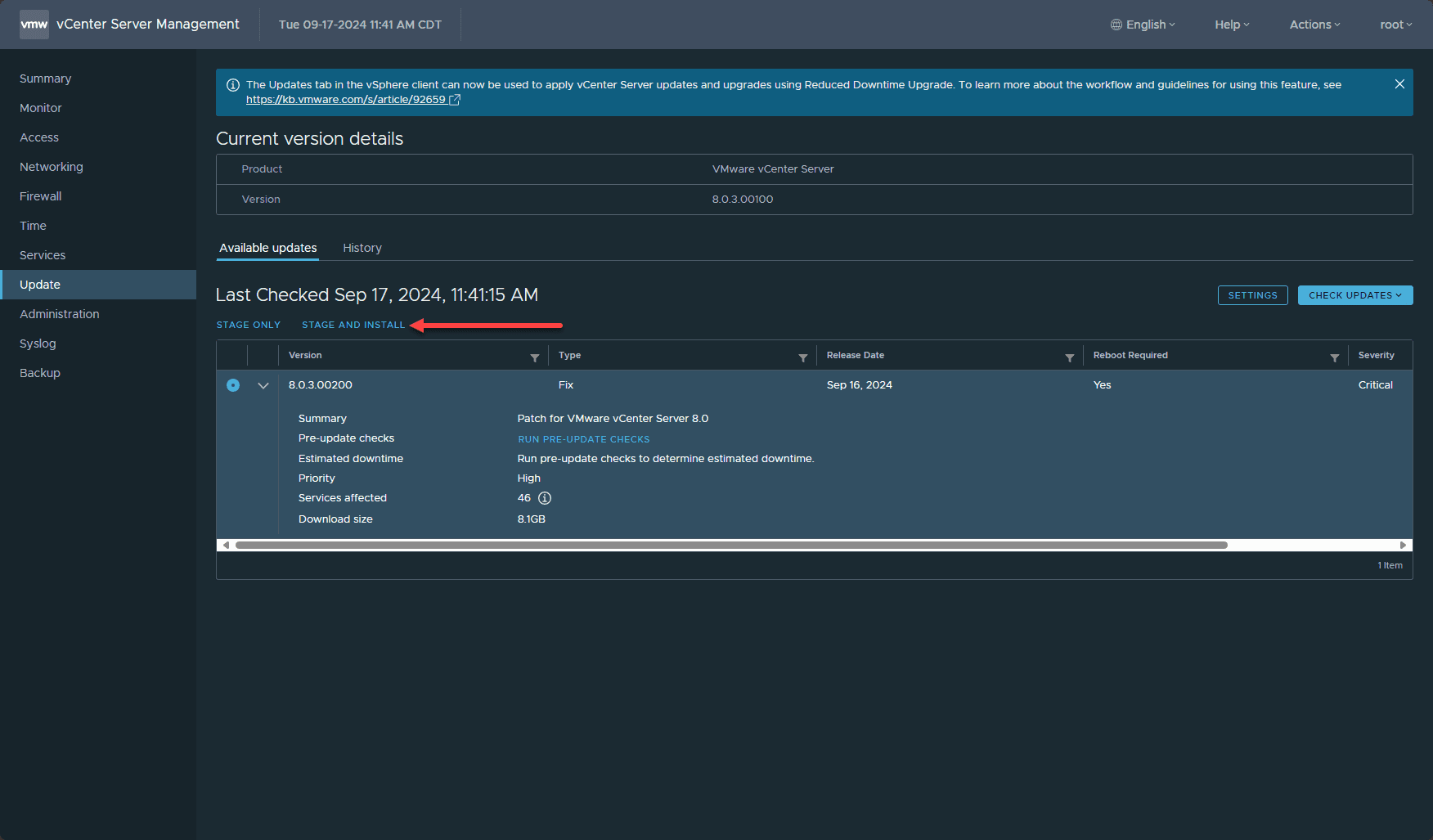
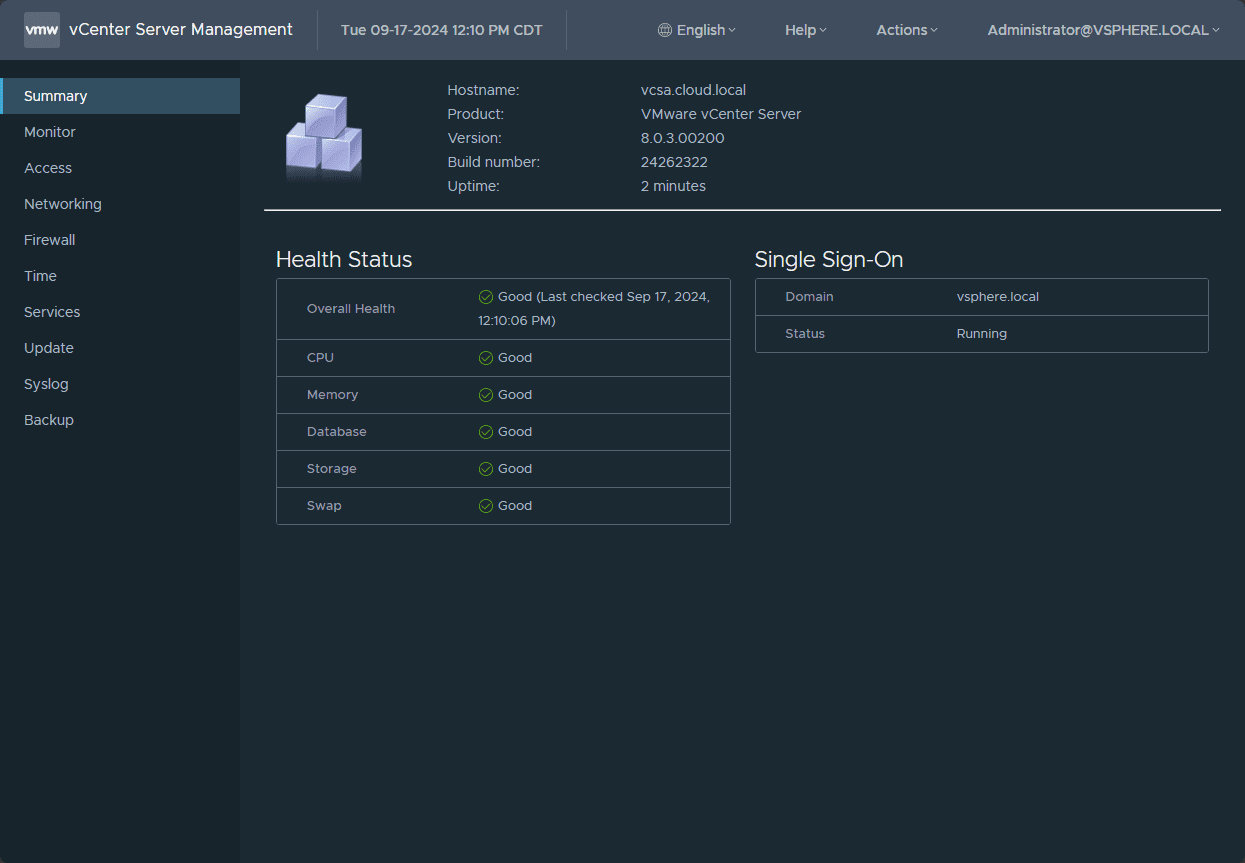
Now, let’s step through the process to get vCenter Server patched. First click the Check Updates button over on the right hand side. Then you should see the latest patch pulled that is dated today. For vCenter Server 8.0 Update 3b, the new version is 8.0.3.00200.
Then we just need to click Stage and Install.
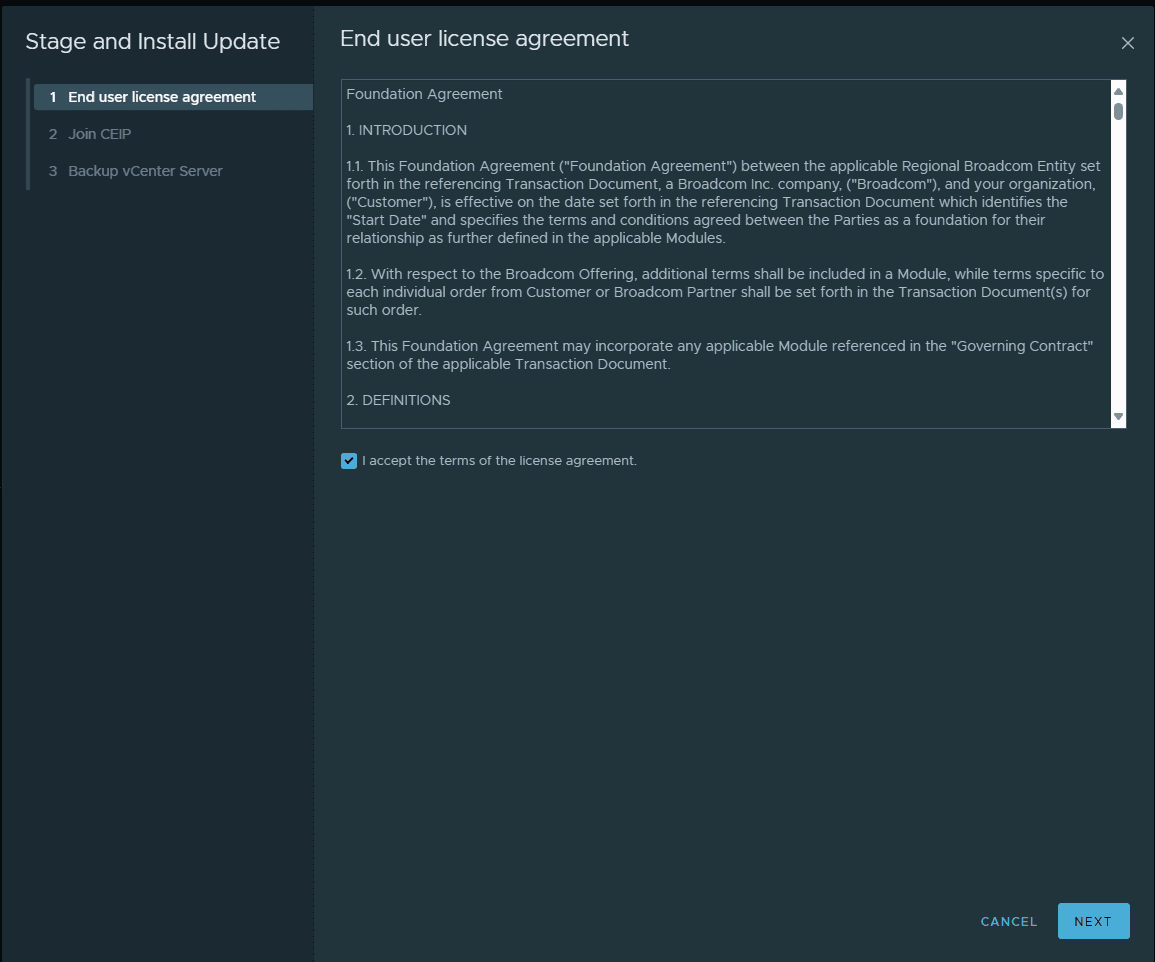
This will launch the Stage and Install Update wizard. First, we need to check the box to accept the EULA.
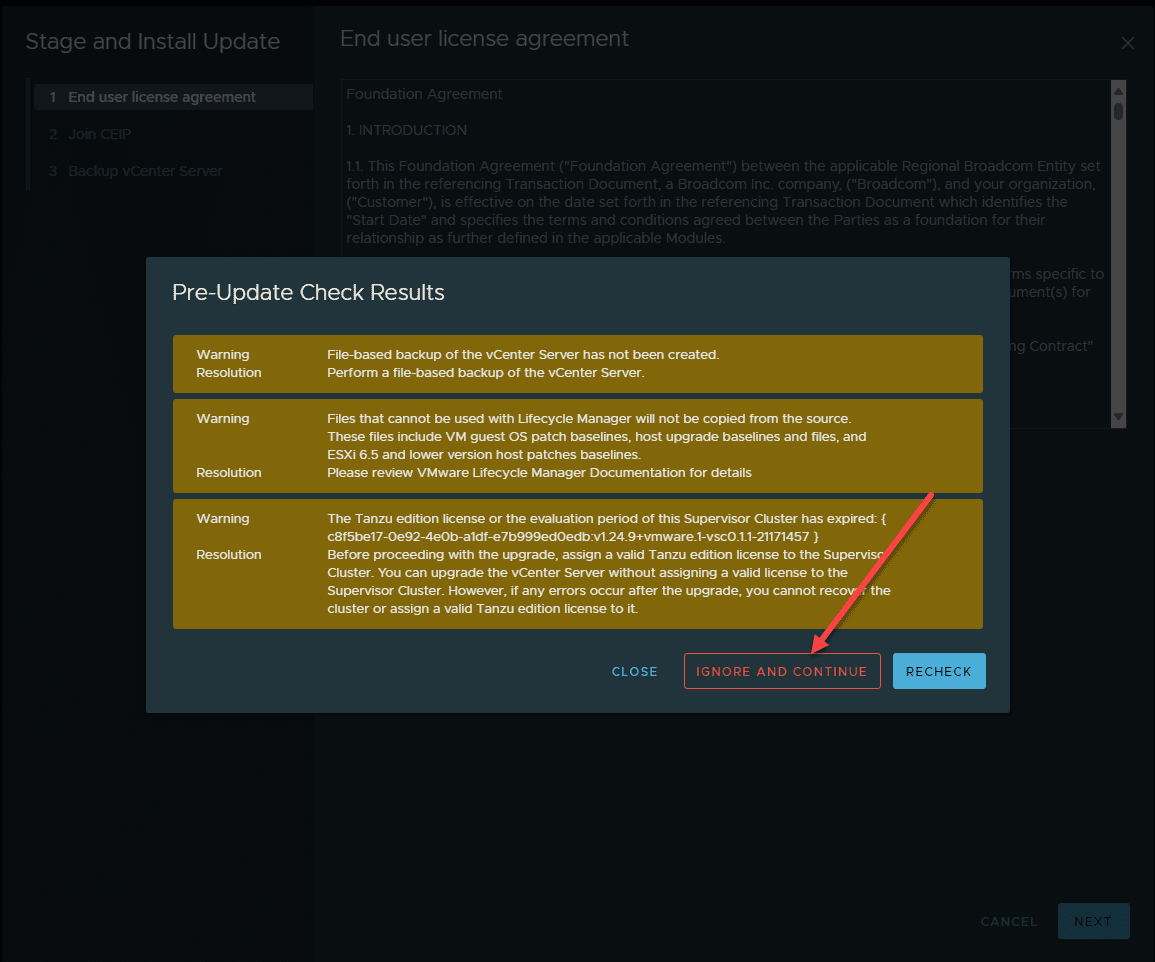
It will run a pre-update check on your vCenter Server. Note the findings and choose to proceed if applicable in your environment.
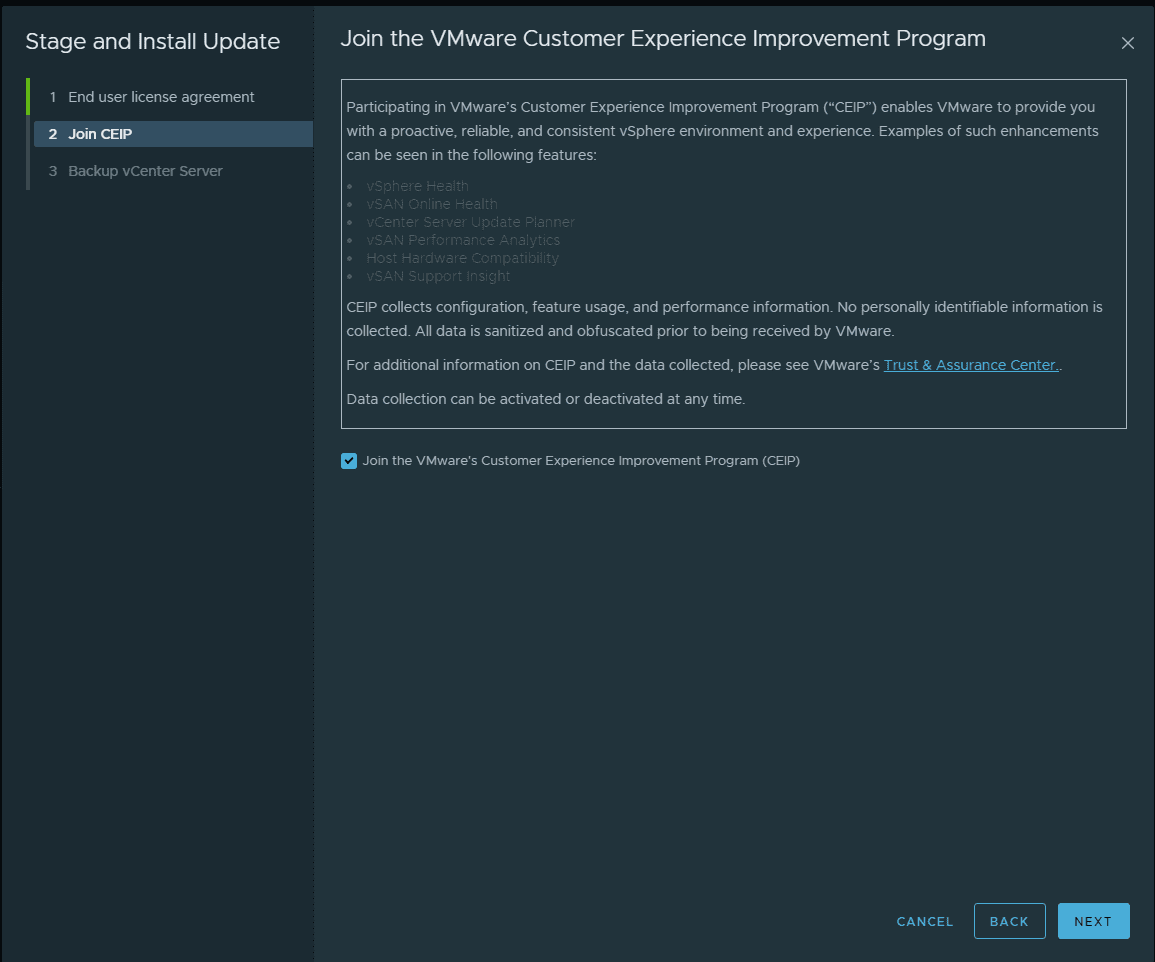
Next, you can choose to join the CEIP or uncheck the box.
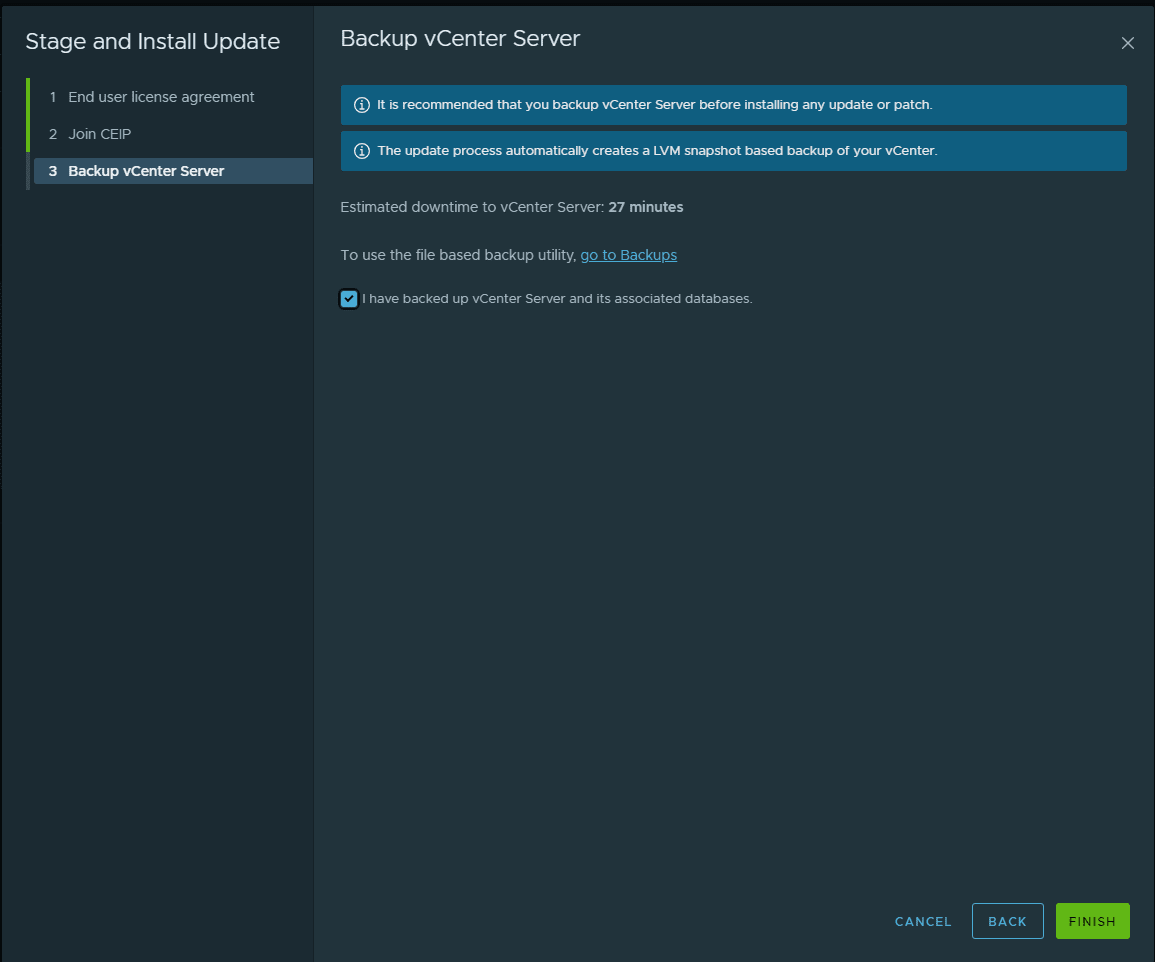
To proceed, you will have to check the box I have backed up vCenter Server and its associated databases. Then click Finish.
This will begin the update process.
After a few minutes, in my home lab, I saw the process converting the data as part of the post install process.
Then another 5 minutes or so, the installation succeeded.
Be sure to check the version of vCenter in the VAMI interface after the update to make sure it shows the new 8.0.3.00200 version.
Wrapping up
This is definitely a vulnerability that you will want to get patched in production as soon as possible to close off this vulnerability, which at its worst, is a 9.8 on the CVSSv3 scale. As always, the process to update vCenter VCSA appliance is not difficult. Just make sure to take the quick snapshot of your appliance beforehand to have a quick rollback.