There has been a lot of back and forth on Active Directory integration security with VMware lately and a really great article by Bob Plankers on Active Directory integration and IdP in general. You can read that here, definitely a good one: Thoughts on CVE-2024-37085 and ESXi (plankers.com).
Table of contents
Why are settings being changed?
In the VMSA for the specific CVE of VMware ESXi Active Directory Integration Authentication Bypass (CVE-2024-37085) and the linked KB article, it was noted that several ESXi advanced settings had default values that are not secure by default. As an example, the ESX Admins is automatically given a role when an ESXi host is joined by the VI Admin to the Active Directory Domain. That role is the VIM Admin.
VMware also makes this note regarding the ESX Admins group:
Note: The ESX Admins group will be added to the host with Admin privileges once the host is added to Active Directory. It is recommended to change these settings before joining the domain. These settings take effect within a minute. A reboot is not required.
What is changing?
There are just a few advanced settings that are changing in regards to what VMware is now recommending for settings on your ESXi hosts. They are now recommending the following advanced settings changes:
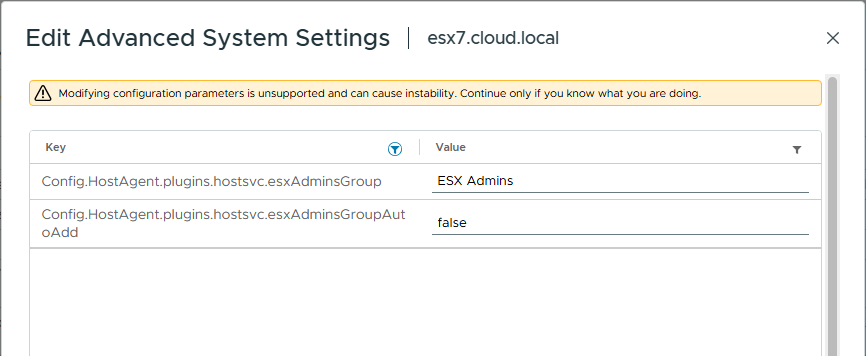
Config.HostAgent.plugins.hostsvc.esxAdminsGroupAutoAdd from true to false
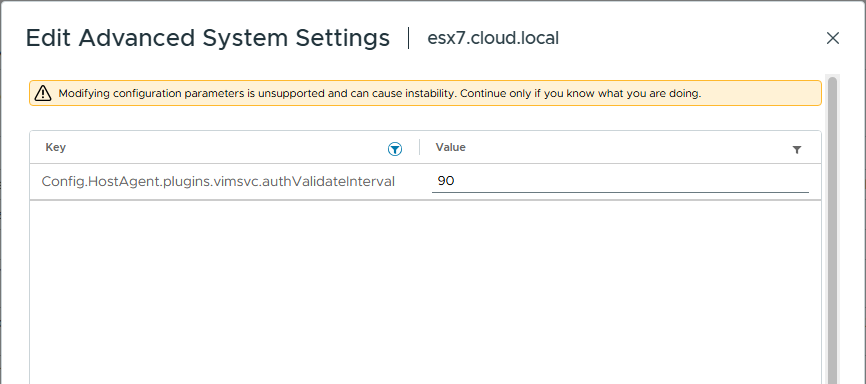
Config.HostAgent.plugins.vimsvc.authValidateInterval from 1440 to 90
Config.HostAgent.plugins.hostsvc.esxAdminsGroup from "ESX Admins" to "" 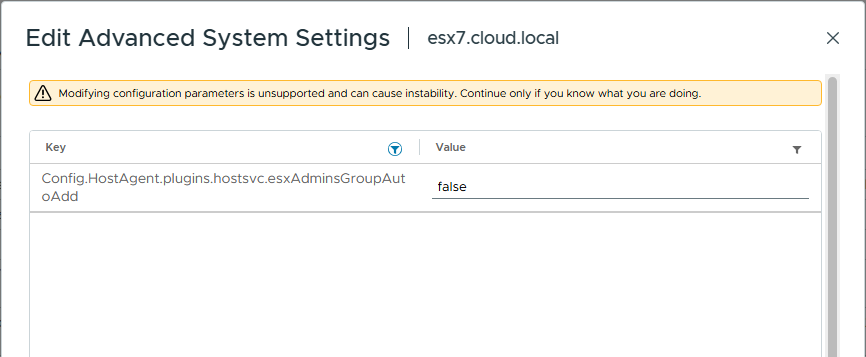
Also, if you have already joined ESXi hosts to Active Directory before the workaround is put in place, the new direction is to remove the Admin permissions for the AD group ESX Admins. There is a command you can run to do this:
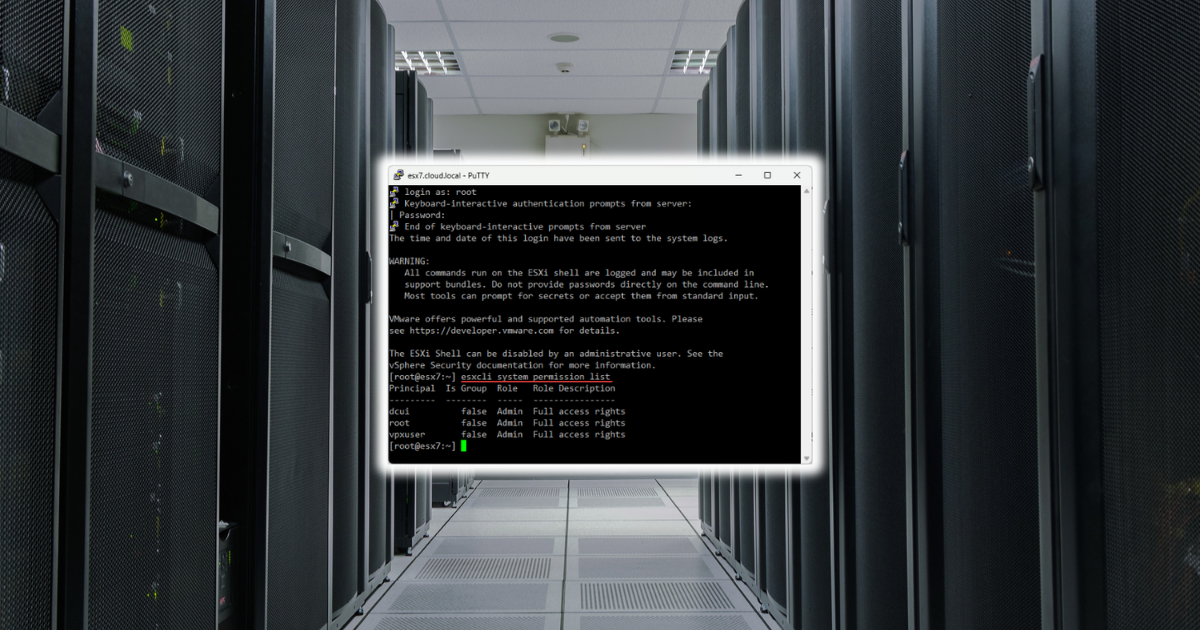
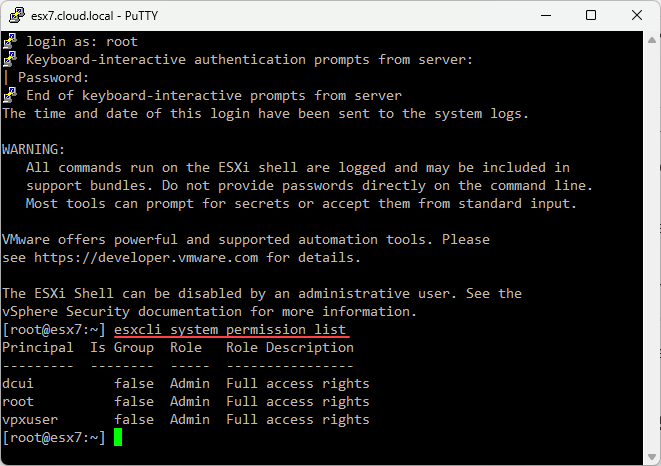
esxcli system permission unset -i 'DOMAIN\esx^admins' --groupTo make sure of what permissions are set for VIM permissions you can use the command:
esxcli system permission listBelow is VMware’s response Matrix for the VMware ESXi Active Directory Integration Authentication Bypass (CVE-2024-37085) for those that would like to look at the following table:
| VMware Product | Version | Running On | CVE | CVSSv3 | Severity | Fixed Version | Workarounds | Additional Documentation |
| ESXi | 8.0 | Any | CVE-2024-37085 | 6.8 | Moderate | ESXi80U3-24022510 | KB369707 | None |
| ESXi | 7.0 | Any | CVE-2024-37085 | 6.8 | Moderate | No Patch Planned | KB369707 | None |
| VMware Cloud Foundation | 5.x | Any | CVE-2024-37085 | 6.8 | Moderate | 5.2 | KB369707 | None |
| VMware Cloud Foundation | 4.x | Any | CVE-2024-37085 | 6.8 | Moderate | No Patch Planned | KB369707 | None |
The response matrix for the VMware ESXi out-of-bounds read vulnerability (CVE-2024-37086):
| VMware Product | Version | Running On | CVE | CVSSv3 | Severity | Fixed Version | Workarounds | Additional Documentation |
| ESXi | 8.0 | Any | CVE-2024-37086 | 6.8 | Moderate | ESXi80U3-24022510 | None | None |
| ESXi | 7.0 | Any | CVE-2024-37086 | 6.8 | Moderate | ESXi70U3sq-23794019 | None | None |
| VMware Cloud Foundation | 5.x | Any | CVE-2024-37086 | 6.8 | Moderate | 5.2 | None | None |
| VMware Cloud Foundation | 4.x | Any | CVE-2024-37086 | 6.8 | Moderate | Async patch to ESXi 7.0 U3q | None | Async Patching Guide: KB88287 |
The response matrix for the VMware vCenter denial-of-service vulnerability (CVE-2024-37087):
| VMware Product | Version | Running On | CVE | CVSSv3 | Severity | Fixed Version | Workarounds | Additional Documentation |
| vCenter Server | 8.0 | Any | CVE-2024-37087 | 5.3 | Moderate | 8.0 U3 | None | None |
| vCenter Server | 7.0 | Any | CVE-2024-37087 | 5.3 | Moderate | 7.0 U3q [1] | None | None |
| VMware Cloud Foundation | 5.x | Any | CVE-2024-37087 | 5.3 | Moderate | 5.2 | None | None |
| VMware Cloud Foundation | 4.x | Any | CVE-2024-37087 | 5.3 | Moderate | Async patch to 7.0 U3q [1] | None | Async Patching Guide: KB88287 |
Wrapping up
If you read the latest VMware Security best practices, VMware no longer recommends joining your ESXi hosts to an Active Directory Domain Services environment. There are just too many risks to doing this. A lot of the ransomware gangs are compromising vCenter Server using domain credentials. Not joining your vSphere environment to Active Directory just helps to eliminate this as a risk to the environment.
Google is updating how articles are shown. Don’t miss our leading home lab and tech content, written by humans, by setting Virtualization Howto as a preferred source.