If you are working with having your CI CD pipeline build Docker images automatically when you check in code to your repository, it is a good idea to have the Docker image checked for vulnerabilities. There are solutions like Docker Scout, but also, there is a free solution called Trivy that allows scanning your Docker container image for known vulnerabilities. Let’s learn more about Trivy and how you can use it.
Table of contents
What is Trivy Scanner?
Trivy is a free and open source vulnerability scanner that can find vulnerabilities in container images, including those stored in remote Git repositories and local container image locations. It scans your Docker container image for vulnerabilities from a vulnerability database that is updated regularly.
As more organizations migrate towards containerized workloads, scanning your Docker images for vulnerabilities is a great idea as there can be severe security issues with containers like there can be with other infrastructure.
Containers do shrink the attack surface, but they are still able to be compromised. Trivy not only scans container images, but Trivy scans IaC and OS packages as well. You can scan Terraform, CloudFormation, Docker, Kubernetes, and many other IaC configuration files with Trivy. You can also scan VM images (experimental) making it a comprehensive vulnerability scanner.
Learn more about Trivy here from the official site: Trivy Home – Trivy.
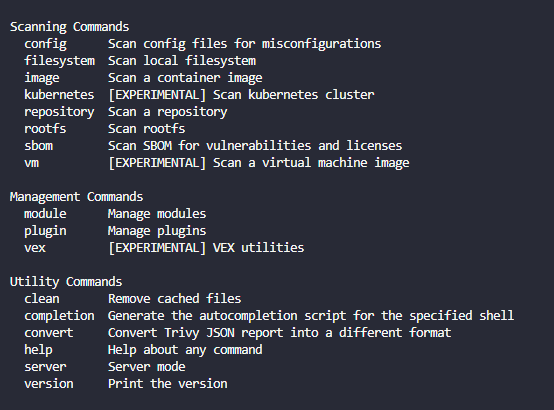
You can get an idea of what Trivy can do if you run the command without any parameters. It will output the available commands. As you can see below:
- config – Scan config files for misconfigurations
- filesystem – scan local filesystem
- image – scan a container image
- kubernetes – scan kubernetes cluster
- repository – scan a repository
- rootfs – scan rootfs
- sbom – scan SBOM for vulnerabilities and licenses
- VM – scan a virtual machine image
Misconfigurations and sensitive information detection
It can also do more than simple vulnerability detection. Trivy can help identify misconfigurations and sensitive information that may be found in your container images. This helps with an extra layer of security for your container images. It makes sure your container environments are safe from vulnerabilities but also configuration issues that could expose sensitive data.
Below, we are scanning a local folder with Terraform code for misconfiguration, etc:
Advantages of Using Trivy
Note the following advantages and pros of using Trivy for vulnerability scanning container images
- Easy to install and use
- Comprehensive vulnerability scanning and detection
- You can scan local and remote container images
- You can identify misconfigurations and sensitive information in configuration files, etc
- It can be used with CI/CD pipelines
Importance of Scanning Container Images
It is quite necessary to scan your container images. Severe vulnerabilities can creep into your images that are used in production, posing a large security risk. Scanning these images for known vulnerabilities is extremely important to maintaining a secure infrastructure. The Trivy scanner helps identify security issues within container images. This makes sure that security vulnerabilities are detected and remediated.
Setting Up Trivy
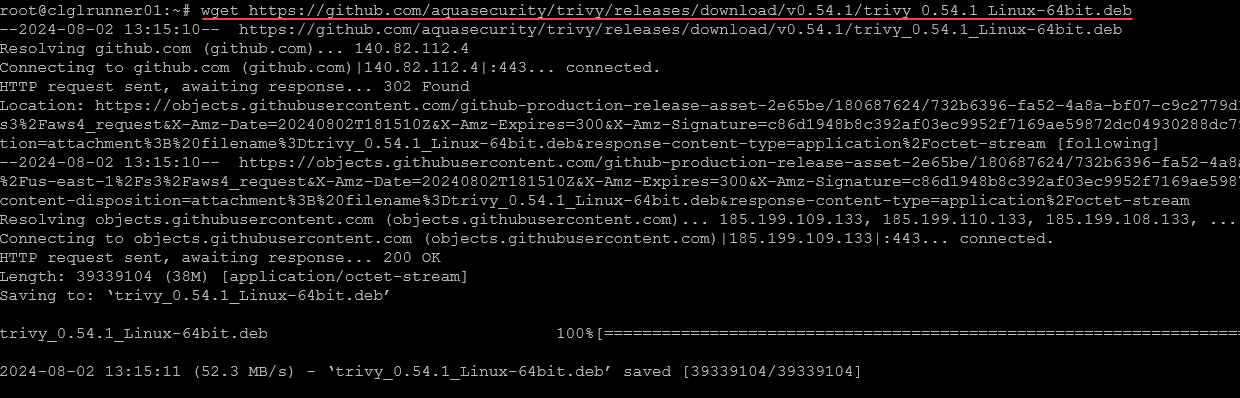
Below, we will see how you can easily install this in your Linux environment. You can find the latest of the release by browsing out to: Releases · aquasecurity/trivy (github.com).
##Download the trivy installer
wget https://github.com/aquasecurity/trivy/releases/download/v0.54.1/trivy_0.54.1_Linux-64bit.deb
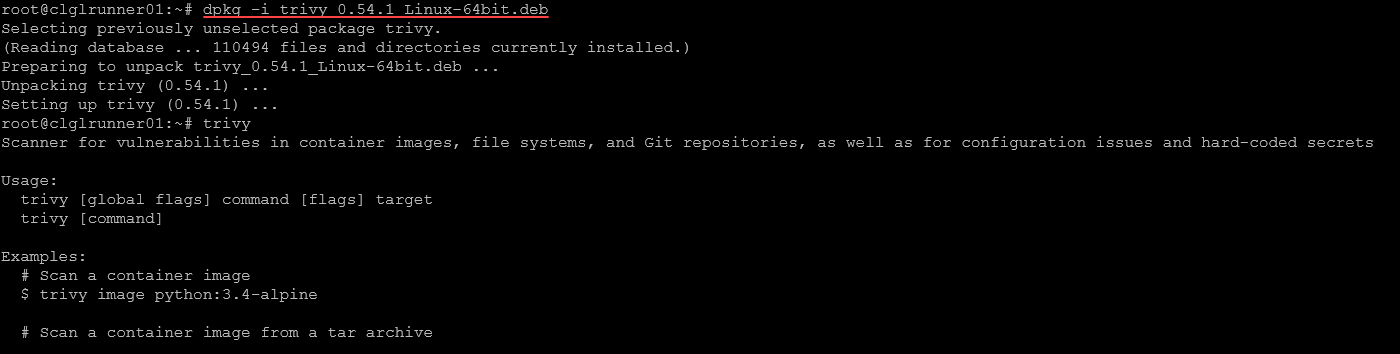
##Install Trivy
dpkg -i trivy_0.54.1_Linux-64bit.debRunning the installer.
Scanning Docker Images with Trivy
Once installed, you can scan Docker images for vulnerabilities using a simple command where you pass in only an image name:
trivy.exe image <your image>Replace <your image> with the name of your Docker image. This command initiates the scanning process to find vulnerabilities in the image.
Example of Scanning a Docker Image
For example, to scan an nginx Docker image:
trivy image nginx:latestThis command scans the latest version of the Nginx image for vulnerabilities. The output provides detailed information on any security issues found, allowing you to take necessary actions.
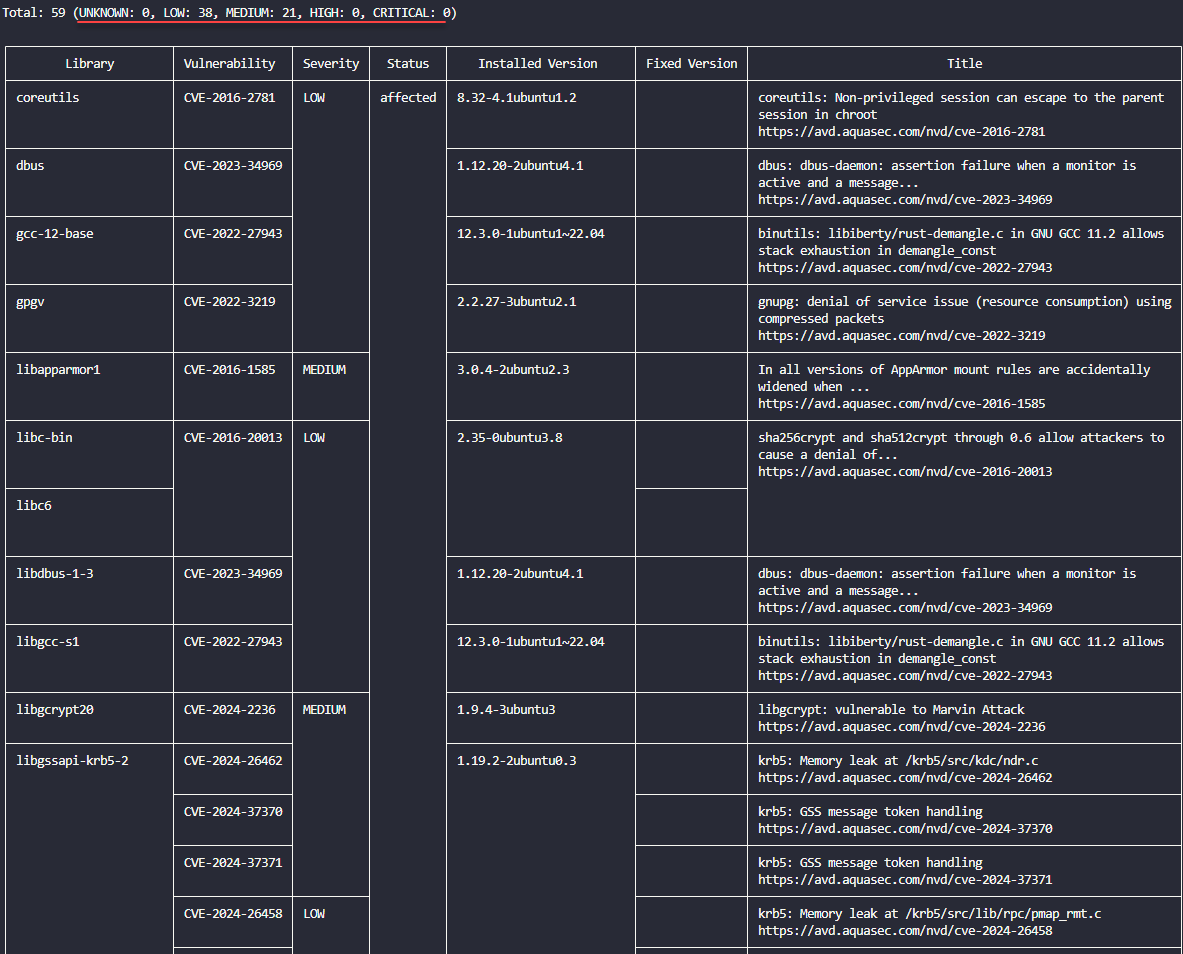
Output of the command
Trivy will give you an output table of vulnerabilities found. It will show you at the top the severities of the vulnerabilities found in the container image. The table will show you the details of each vulnerability, including the CVE number, status, fixed version, and Title. As you can see, it provides a comprehensive vulnerabilities matrix to look at to determine if there are vulnerabilities you need to address with your container images.
Scanning Local and Remote Container Images
You can also use Trivy to scan images found in a remote container registry. It means you can secure your container images no matter where these are located, local or remote. For remote scans, you can use commands like:
trivy image <remote_image_name>This command allows you to scan images directly from remote repositories.
Integrating Trivy with CI/CD Pipelines
Trivy can be integrated into CI/CD pipelines to automate the scanning process. This is a great way to automate security for your docker container images. You can setup your pipeline with a “stage” in the pipeline to scan. Also, you can set the pipeline so that it fails the pipeline if a certain severity of vulnerability is found in the container image, such as high or critical.
If the scan stage passes, you can have your CI CD pipeline go ahead and run the push stage so the image is pushed to your registry. This is just an example though and can be configured however you need to meet your security objectives.
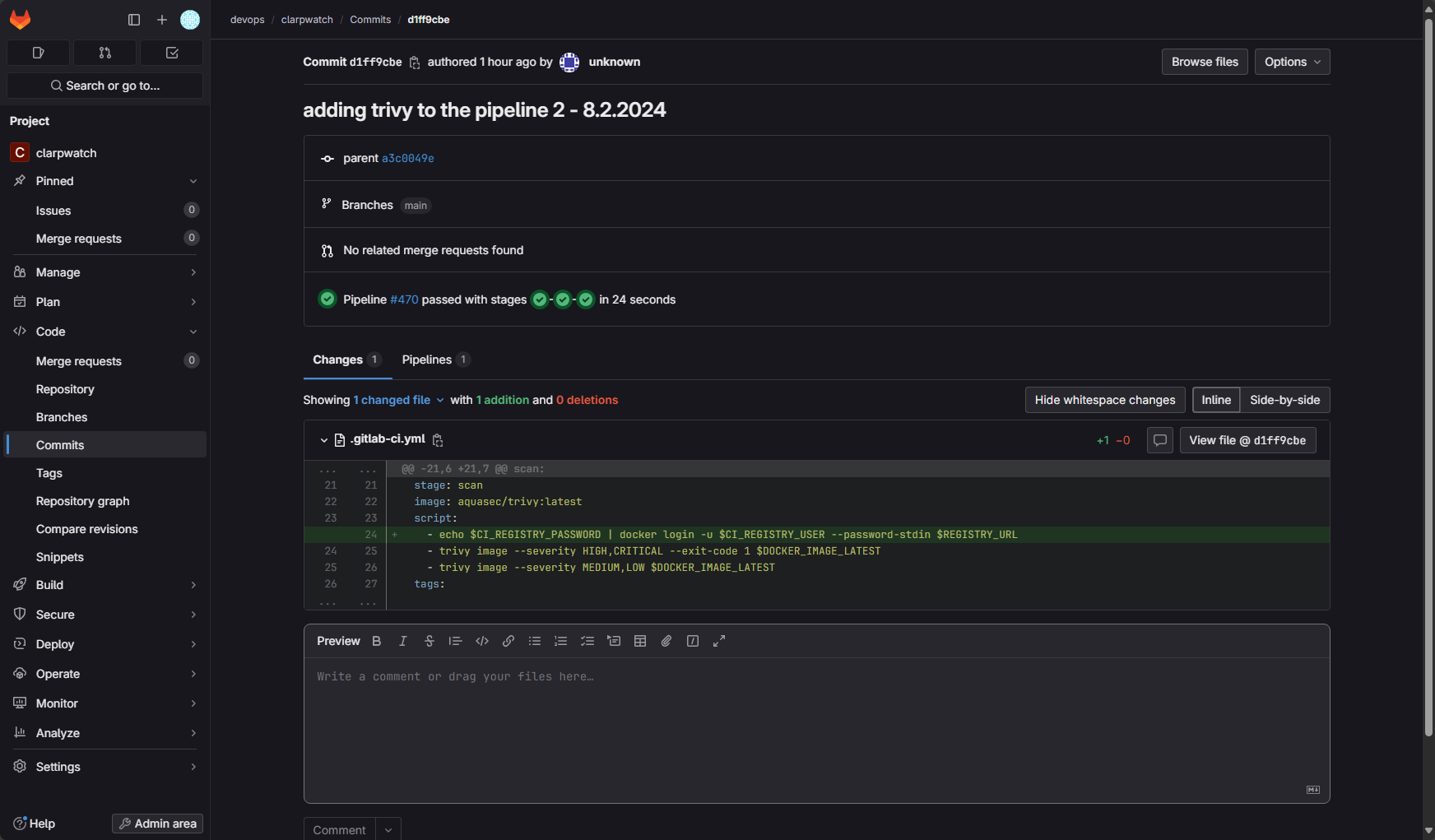
For example, in GitLab your pipeline file might look like this:
stages:
- build
- scan
- push
variables:
REGISTRY_URL: <your registry URL>
DOCKER_IMAGE_LATEST: $REGISTRY_URL/$CI_PROJECT_NAMESPACE/$CI_PROJECT_NAME:latest
before_script:
- echo $CI_REGISTRY_PASSWORD | docker login -u $CI_REGISTRY_USER --password-stdin $REGISTRY_URL
build:
stage: build
script:
- docker build -t $DOCKER_IMAGE_LATEST .
tags:
- shell
scan:
stage: scan
image: aquasec/trivy:latest
script:
- echo $CI_REGISTRY_PASSWORD | docker login -u $CI_REGISTRY_USER --password-stdin $REGISTRY_URL
- trivy image --severity HIGH,CRITICAL --exit-code 1 $DOCKER_IMAGE_LATEST
- trivy image --severity MEDIUM,LOW $DOCKER_IMAGE_LATEST
tags:
- shell
push:
stage: push
script:
- docker push $DOCKER_IMAGE_LATEST
tags:
- shell
when: on_successWrapping up
Trivy scanner is a great utility. It is a free and open-source vulnerability scanner that can be installed in minutes and even integrated into your CI CD pipeline in a few minutes with just a couple of line changes to your pipeline file.
There is an installer for your operating system, including Windows, Linux, macOS, and even a container image you can use that is easy to integrate into pipelines. It can easily find common vulnerabilities, misconfigurations sensitive information, software dependencies, and pulls vulnerability information from a vulnerability database that is constantly updated.
Google is updating how articles are shown. Don’t miss our leading home lab and tech content, written by humans, by setting Virtualization Howto as a preferred source.