OPNsense Port Forwarding Tutorial Step-by-Step
Port forwarding is a feature that allows you to answer outside traffic requests for a certain service even though the server lives on the internal network. OPNsense is a great open-source firewall that has many features like port forwarding to control traffic and user requests. I will take you through the steps to port forward in OPNsense.
Table of contents
What is port forwarding and how does it work?
Before we look at setting up port forwarding rules in OPNsense, let’s first learn about port forwarding in general.
Port forwarding is a feature that takes a connection request from the outside that is destined for an external IP address and then forwards it to another IP and port (configurable) to a client/server on the inside network using their local IP address.
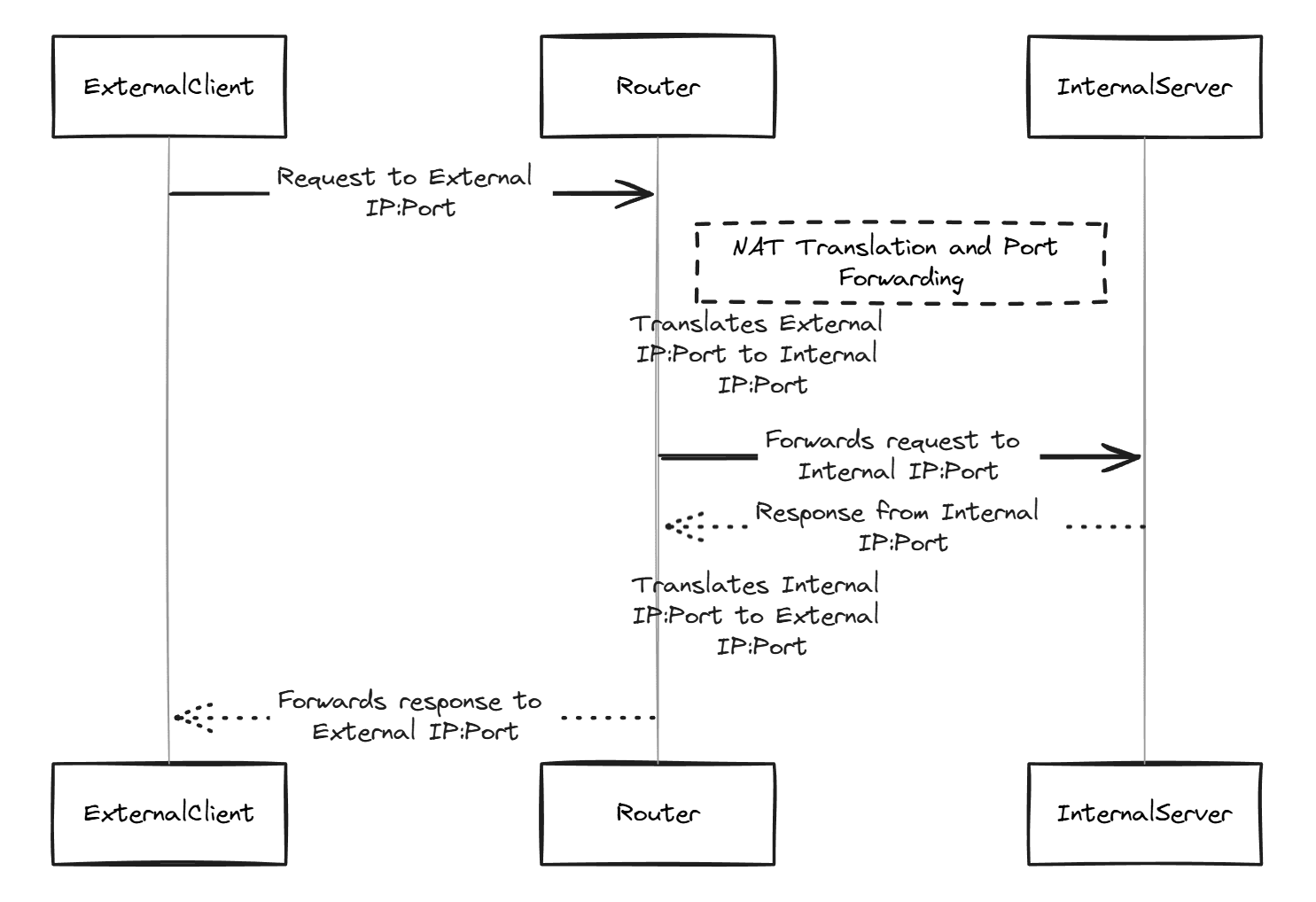
Usually, you set up port forwarding when you host services like a web server, email server, gaming server, etc., that you want others to be able to connect to outside your network.
How Port Forwarding Works
When a user on the outside requests a certain resource on a server that exists in your network, the traffic first comes to the external address that is hosted on the firewall. Without a port forward, firewalls like OPNsense will block these requests since they have to be allowed to get through.
Here are the steps in the process:
- The firewall (OPNsense) receives the traffic request for a certain service port
- When a port forwarding rule is set up, it forwards the traffic to the internal IP address and port configured in the port forward
- The device inside the network then answers the request, and the communication follows the reverse path to get back to the client on the outside
Why Use Port Forwarding?
Port forwarding is crucial for running any server that needs to interact with users or devices outside its local network. It enables:
- Improved security by allowing only specific ports to be opened and directing them to specific devices.
- Reliable and direct communication access to services hosted internally, such as gaming servers, file servers, or communication platforms.
Common Applications of Port Forwarding
- Gaming: Allowing clients outside the local network to access game servers
- Web Servers: This allows clients on the Internet to access a website hosted on a web server on the internal network
- Remote Access Applications: Allowing services like VPNs and remote desktop applications (RDP) to connect to your network and clients that have RDP enabled
Setting Up OPNsense for Port Forwarding
Below are the steps to set up OPNsense for effective port forwarding.
Step 1: Accessing the OPNsense Web Interface
You first need to log into your OPNsense web admin interface. You do this by browsing out to the LAN IP address of your OPNsense firewall in the browser’s address bar. If you kept the defaults, the default LAN address web interface is found at https://192.168.1.1. Make sure you are connected to the same network as the OPNsense device.
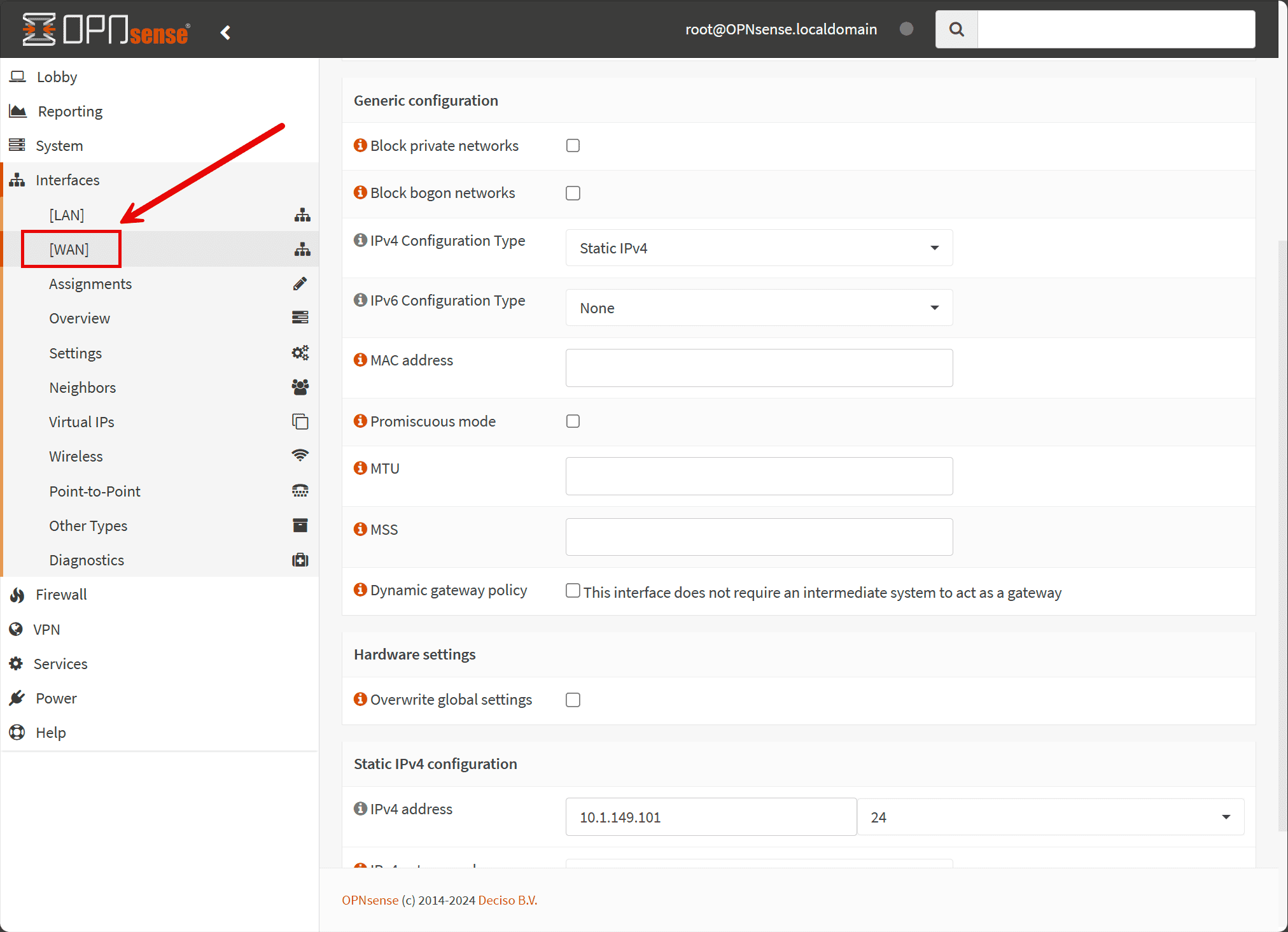
Step 2: Configuring the WAN Interface
Navigate to Interfaces > [WAN] to configure your WAN interface:
- Ensure that the interface is correctly assigned and enabled.
- Verify your WAN settings, such as the IP address assignment method (static, DHCP, or PPPoE depending on your ISP).
Step 3: Establishing Firewall and NAT Rules
Set up the necessary firewall and NAT (Network Address Translation) rules:
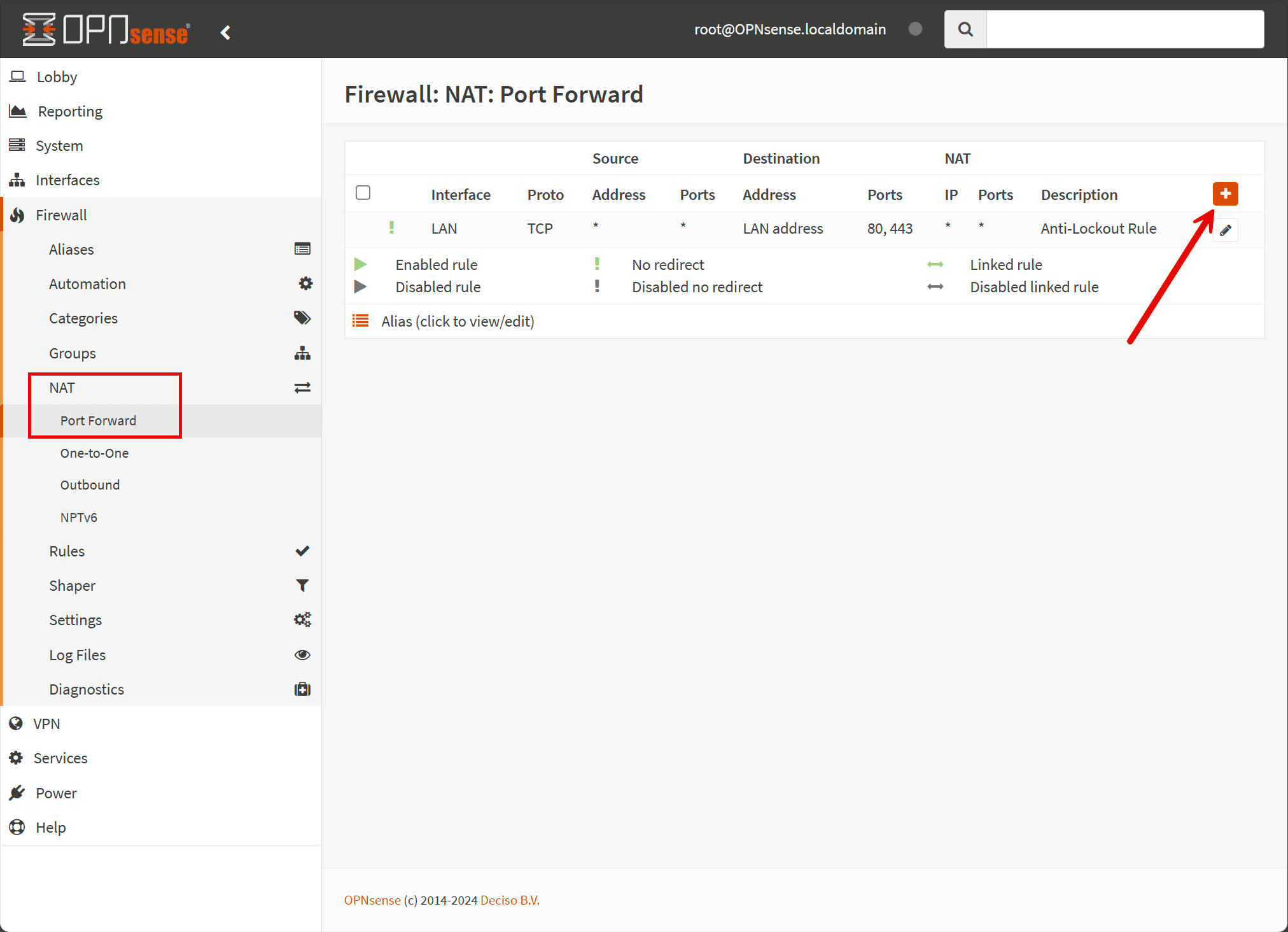
- Go to Firewall > NAT > Port Forward.
- Click on + sign to add a new rule.
Configuring NAT Port Forward Rules
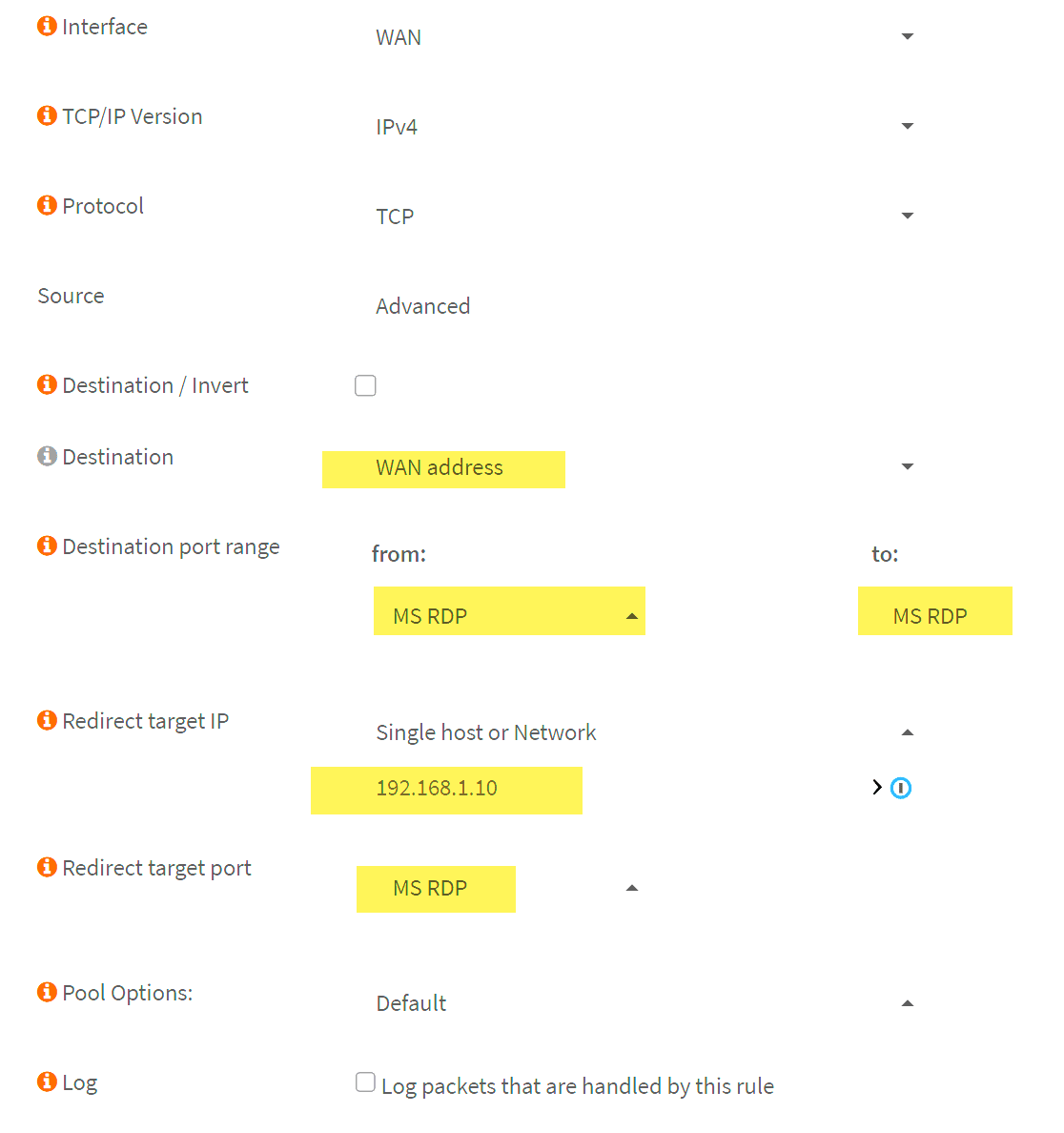
- Interface: Typically, this will be your WAN interface.
- Protocol: Choose TCP, UDP, or TCP/UDP, depending on the application requirements.
- Source: If you click the Advanced button next to source, you will be able to set things like the source port range if you need to.
- Destination: Set this to WAN address.
- Destination Port Range Service: Enter the port or range of ports that you want to forward.
- Redirect Target IP: Input the internal IP address of the device that will receive the traffic.
- Redirect Target Port: Specify the port on the internal device, if different from the external port.
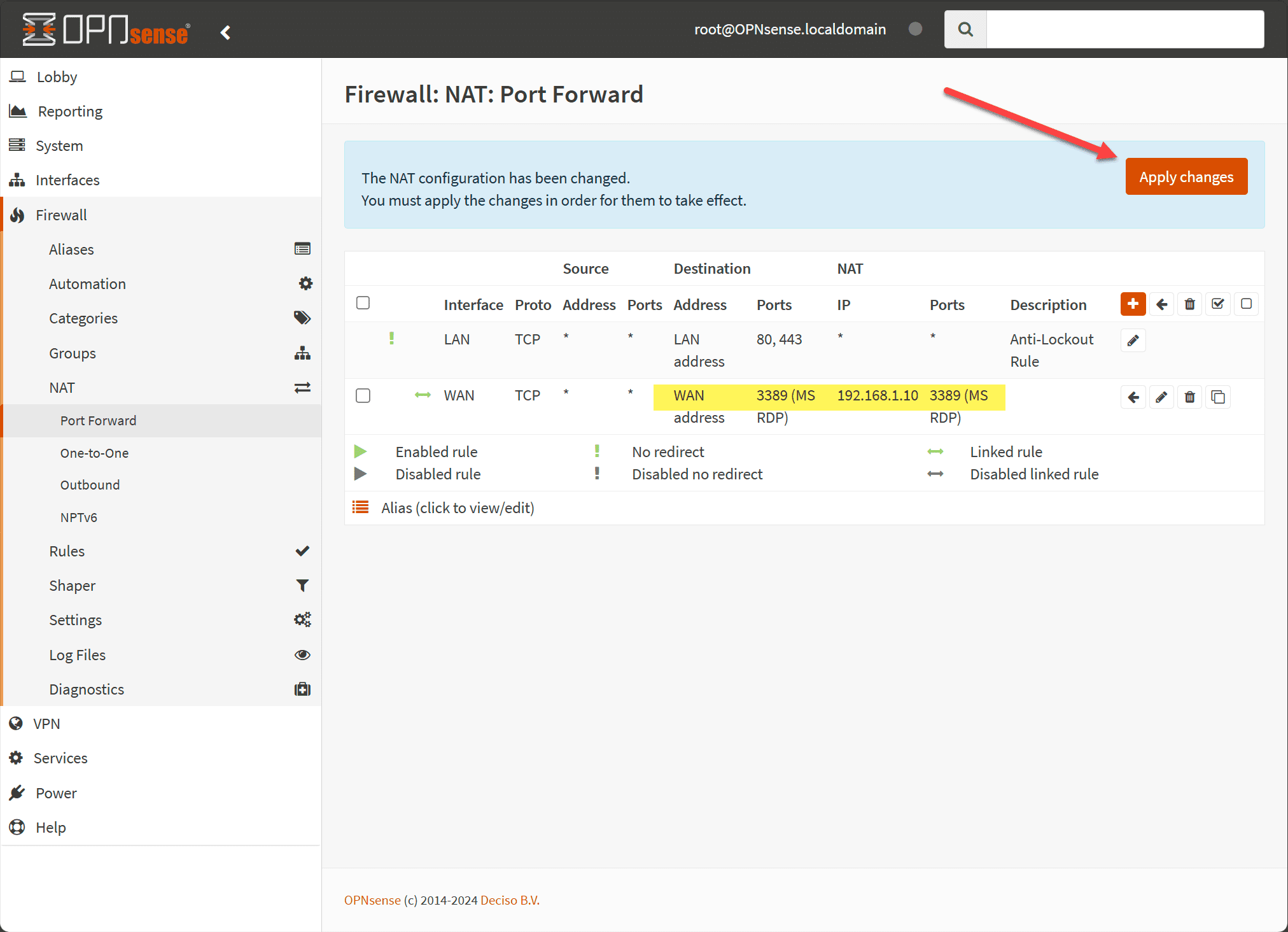
Step 4: Applying Changes
After entering all the necessary information for your port forward rule:
Click Save to store the configuration. Then you will see that you need to Apply the configuration. This will actually commit the changes.
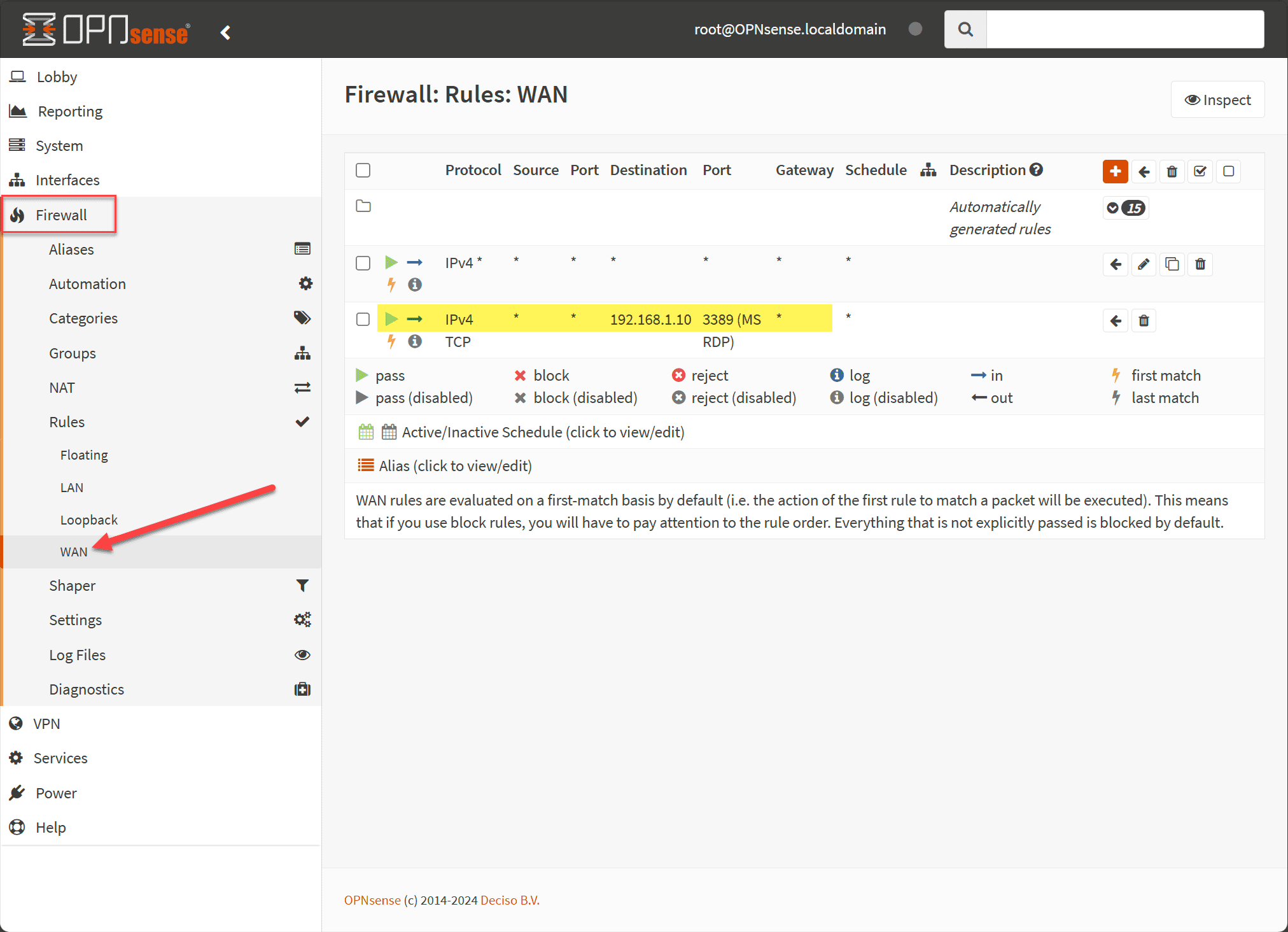
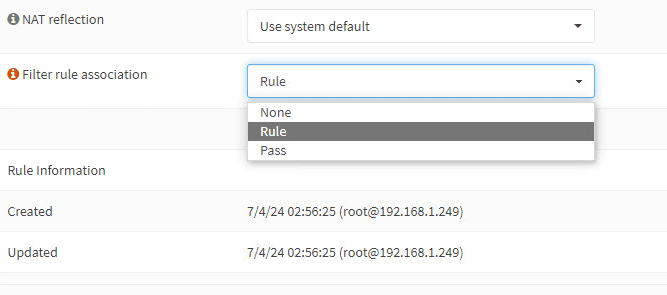
Navigate to Firewall > Rules > WAN and you will see the automatically created filter rule association allowing traffic to the forwarded ports. Make sure the associated filter rule matches your security requirements.
Step 5: Testing the Configuration
Test the port forwarding setup by accessing your service from outside your network (e.g., using a mobile network):
- Use a port scanning tool or an external service like canYouSeeMe.org to check if the ports are open and correctly forwarding to the internal device.
Outbound NAT Rule Generation in OPNsense
Another concept to understand that goes along with port forwards in OPNsense is outbound NAT. OPNsense can handle outbound NAT rules for you or you can create manual outbound NAT rule configurations to have complete control over how NAT’ed traffic regresses out of the firewall.
With the automatic NAT rule generation, the configuration is created automatically by creating NAT rules based on your network config and firewall rules. This is a great setting that can be handy if you are new to firewalls for one (you don’t have to understand or configure it manually, the firewall does the work for you) and in dynamic environments where manual configuration of every NAT rule would be a lot of work or impractical to set up by hand.
How does this relate to Port Forwarding?
When it comes to port forwarding, automatic NAT rules make sure that any server or service configured to accept inbound connections can communicate back out effectively without manually configuring each new service or server.
Advanced Port Forwarding Features in OPNsense
OPNsense offers several advanced settings that can optimize your port forwarding setup, including NAT reflection, filter rule associations, and the creation of manual outbound NAT rules.
Using NAT Reflection
In OPNsense, you can enable NAT reflection on port forwards. What this does is allow devices in the LAN side of the network to access your public-facing servers using the public IP addresses. It helps with uniform access and DNS entries so you don’t have to have different URLs for internal clients vs external clients.
OPNsense allows you to fine-tune this feature and enable it on a per-rule basis. This helps by not universally applying NAT reflection across all services. There may be times when you don’t want to enable NAT reflection for internal clients, so you have the ability to do this granularly.
Troubleshooting
You may need to troubleshoot NAT rules and port forwarding in OPNsense:
- Why isn’t my port forwarding working?
- Check if the WAN IP address is correct and publicly accessible
- Make sure your destination port and redirect target IP in the port forwarding rule are correctly set
- Make sure the port is not blocked by your ISP
- How do I confirm if a port is open?
- Use external tools like canYouSeeMe.org to test if the specific port is open and reachable from outside your network.
- Check firewall logs in OPNsense to see if incoming connections are being blocked or allowed.
- Why are my internal clients not able to access the port-forwarded service using the external IP?
- Make sure NAT reflection is enabled for the specific port forwarding rule
- Check for conflicting NAT or firewall rules
- What should I do if the port shows as closed externally?
- Review firewall rules to make sure they allow traffic on the port from the WAN to the redirected internal IP
- Double-check the NAT rules and make sure they match the port forwarding settings
- How can I troubleshoot intermittent connectivity issues with port-forwarded services?
- Look at the firewall and system logs in OPNsense
- You may want to configure the TCP/UDP timeout settings in OPNsense if sessions are dropping unexpectedly
- Why does my service respond correctly locally but not externally?
- Verify that the outbound NAT rules are configured to translate the source IP from the internal network to the WAN IP
- Check for IP address conflicts or incorrect subnet mask settings that might affect routing
Wrapping up
OPNsense has many great features that allow you to host services that exist internally and allow these to be accessed from the Internet. OPNsense port forwarding is one of those capabilities that provides an easy way to do this.
It is easy to configure and setup a port forward to an internal network server. It will also automatically generate the needed firewall rules for you so you don’t have to do this.







If I use port forwarding and a HTTP request from an internet user is forwarded to my target server, does the target server then receive the IP address of the internet user or is this replaced by the IP of the OPNsense?
Andreas,
Thank you for the comment! When using port forwarding like with an OPNsense firewall, the HTTP request (as an example) from an internet user will still contain the original IP address of the internet user in the HTTP headers. This is because port forwarding operates at the network level (Layer 3 of the OSI model). It just reroutes the traffic without altering the packet headers that contain the IP address information.
Brandon