Install CyberArk Conjur Open Source Secrets Management

Managing secrets is an extremely important part of DevOps and keeping things secure, whether you are housing secrets for your infrastructure as code, or other tasks. I have been a fan for quite a while of Hashicorp Vault. There are other solutions available however. CyberArk Conjur is an open-source solution that you can freely download to manage secrets.
Table of contents
What is CyberArk Conjur?
CyberArk Conjur is a free and open-source tool that you can download here: Secrets Management | Conjur. With it, you can manage secrets across tools, apps, and clouds. It can authenticate containers, isolate secrets from applications, and can be used for privileged access management to control access for non-human identities. It allows securely storing and retrieval of credentials, API keys, and other secrets.
CyberArk Conjur features
Note the following features of Conjur:
- Secure Storage: Storage in Conjur is secure and makes sure only users and non-human identities can access them if these are authorized and entitled
- Access: It enables access control to manage who can fetch specific secrets.
- Auditing: It can track all access to secrets and keep up with accountability for comprehensive audit purposes for sensitive data.
Integration with DevOps Tools
Like other secrets management tools, Conjur integrates well with DevOps tools, including CI/CD pipelines. This DevOps integration makes sure your secrets are secured through the development and deployment pipelines and tasks.
Support for Non-Human Identities
This is a big one. Non-human identities are often neglected when it comes to proper security. These non-human identities include things like service accounts and applications, or also machine identity. Conjur is a good tool in this area. You can use it to provide secure secrets management for non-human identities like service accounts and other non human identities.
It supports cloud
Conjur supports all the major cloud environments and cloud providers, including AWS, Azure, and Google Cloud. It securely stores secrets for cloud environments and makes these only accessible to authorized cloud services and users configured.
It can also complement cloud secrets services like AWS Secrets Manager. You can use it with AWS Secrets Manager to provide an additional layer of security and management capabilities when you fetch secrets.
Helps secure Containerized Environments
In containerized environments, managing secrets can be difficult. CyberArk Conjur provides a solution that integrates well with container orchestration tools like Kubernetes.
Conjur allows containers to securely authenticate and read secrets without exposing them. Even in dynamic containerized environments it helps to make sure these are secured properly.
Install CyberArk Conjur Open Source
CyberArk provides a Quickstart guide to show you how to get up and running with CyberArk Conjur and start storing secrets. You can look at that documentation here: Install Conjur OpenSource Using Docker | Open Source OSS Environment. Below, we will follow these steps to setup the demo environment.
First we need to clone down the repo for Conjur to our Docker host:
git clone https://github.com/cyberark/conjur-quickstart.gitAfter cloning down the repository you will see the conjur-quickstart folder. Here I have changed into the directory and listing out the contents.
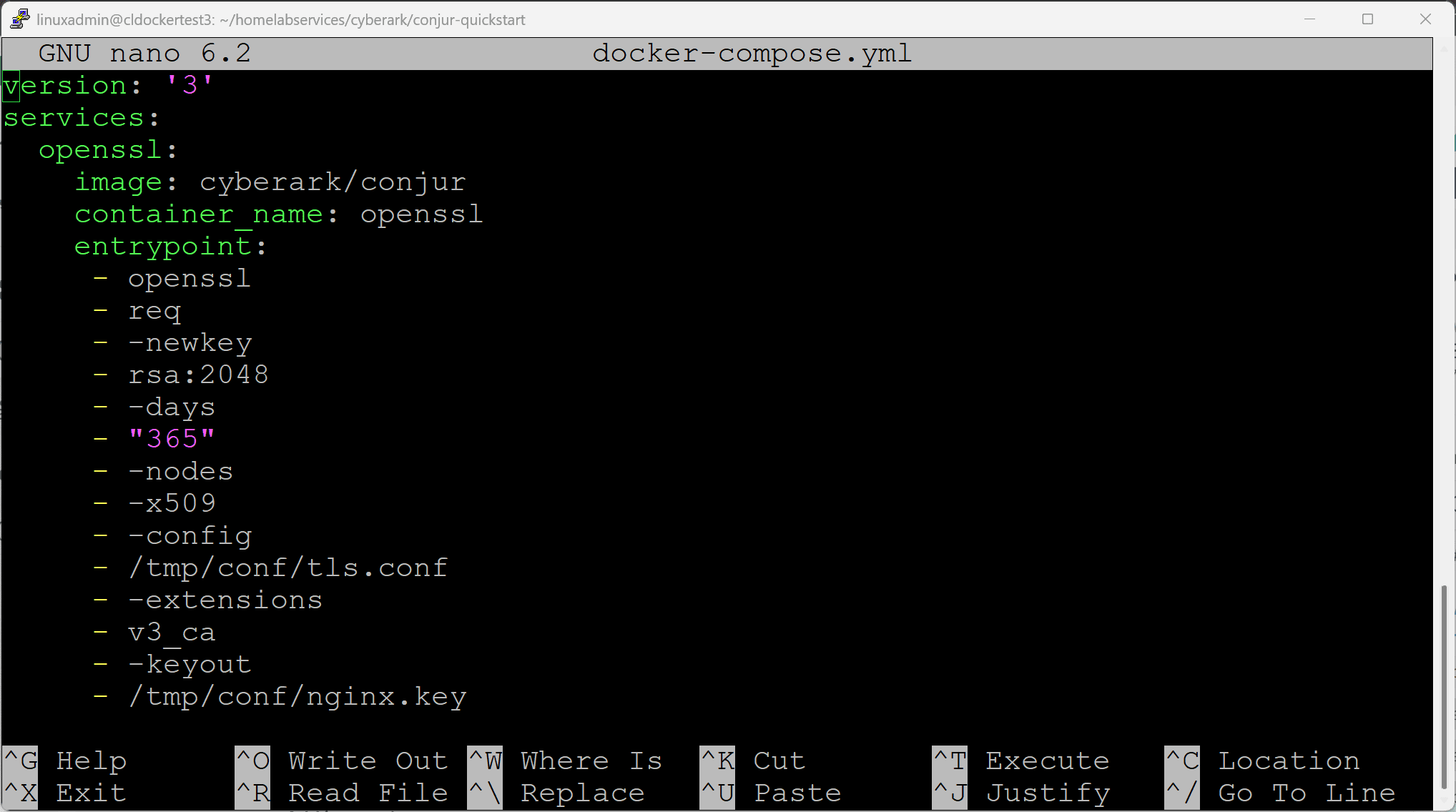
Just a quick look at the Docker-compose file, you will see the services defined.
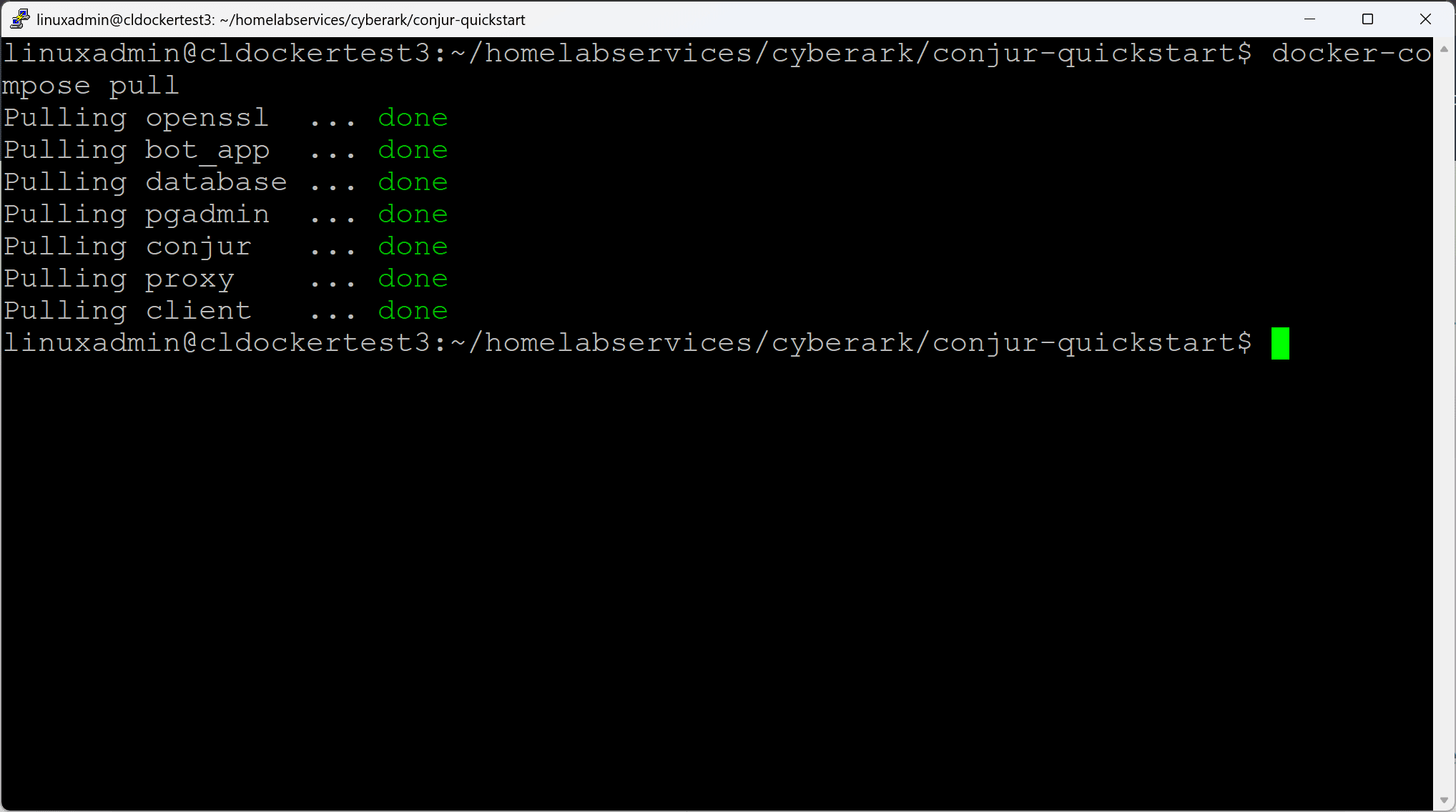
Next, we will pull the container images of services defined in the Docker Compose file:
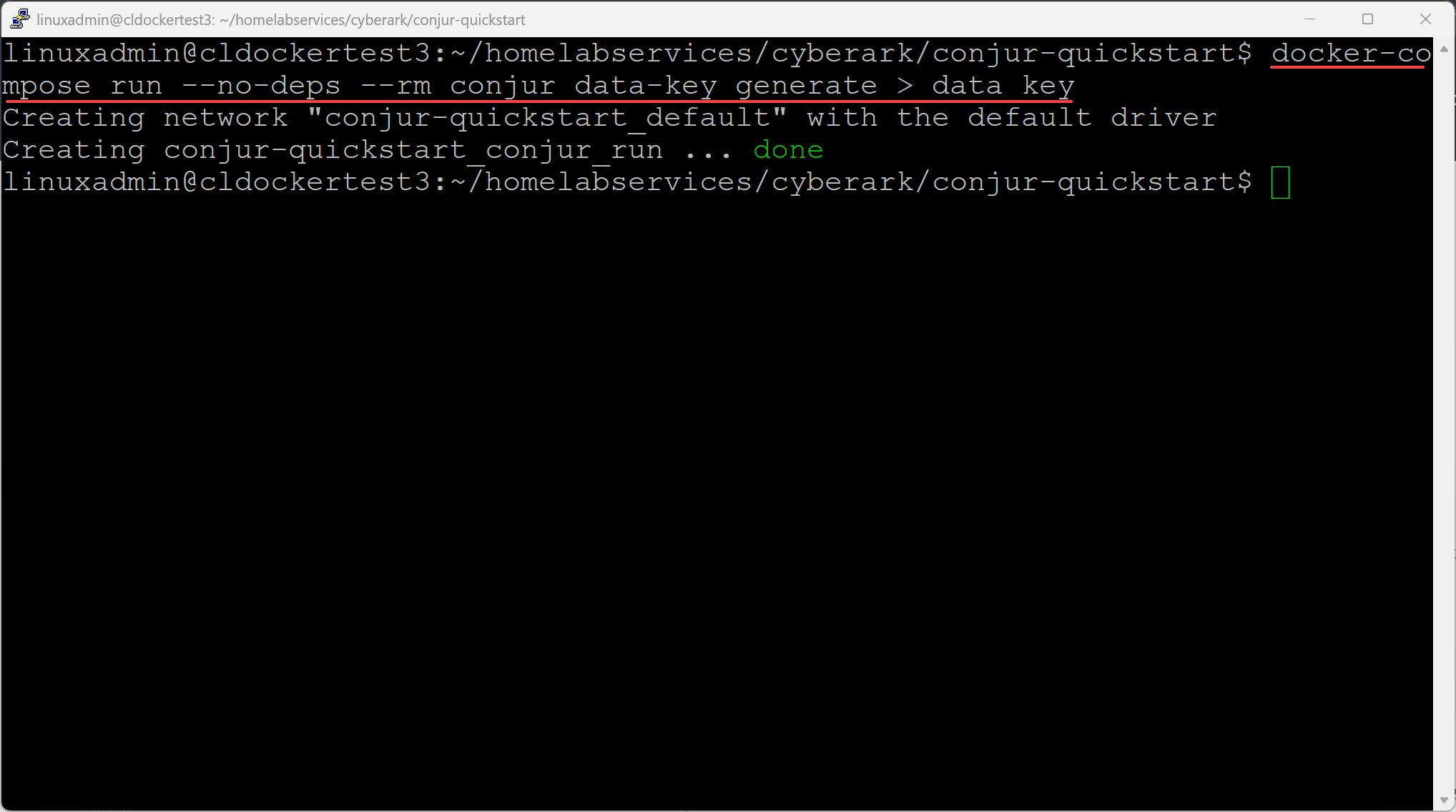
docker-compose pullNow we use the following command to create the master key that will be used to encrypt the database:
docker-compose run --no-deps --rm conjur data-key generate > data_keyNext, we load the master key as an environment variable:
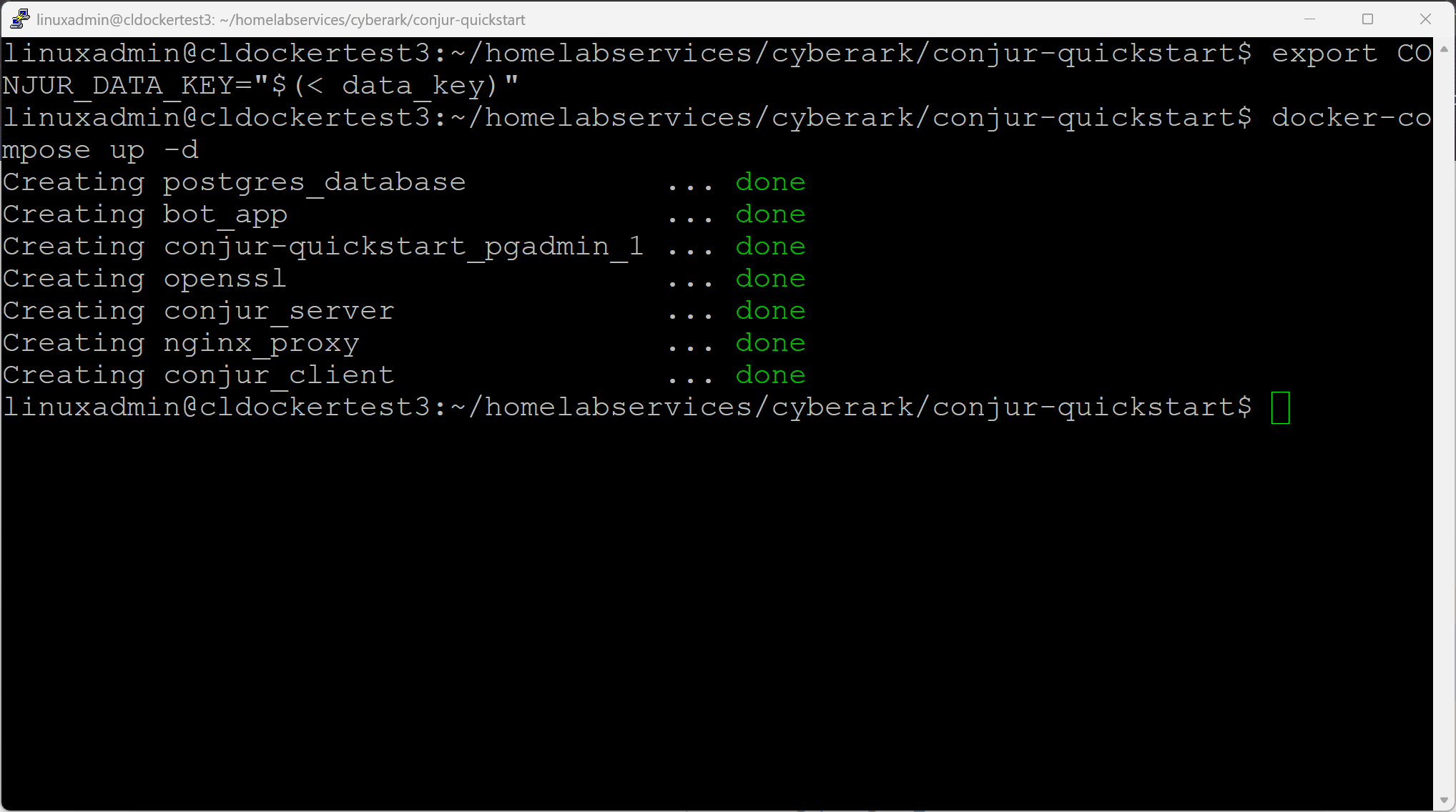
export CONJUR_DATA_KEY="$(< data_key)"Then bring up the Docker Compose stack with the command:
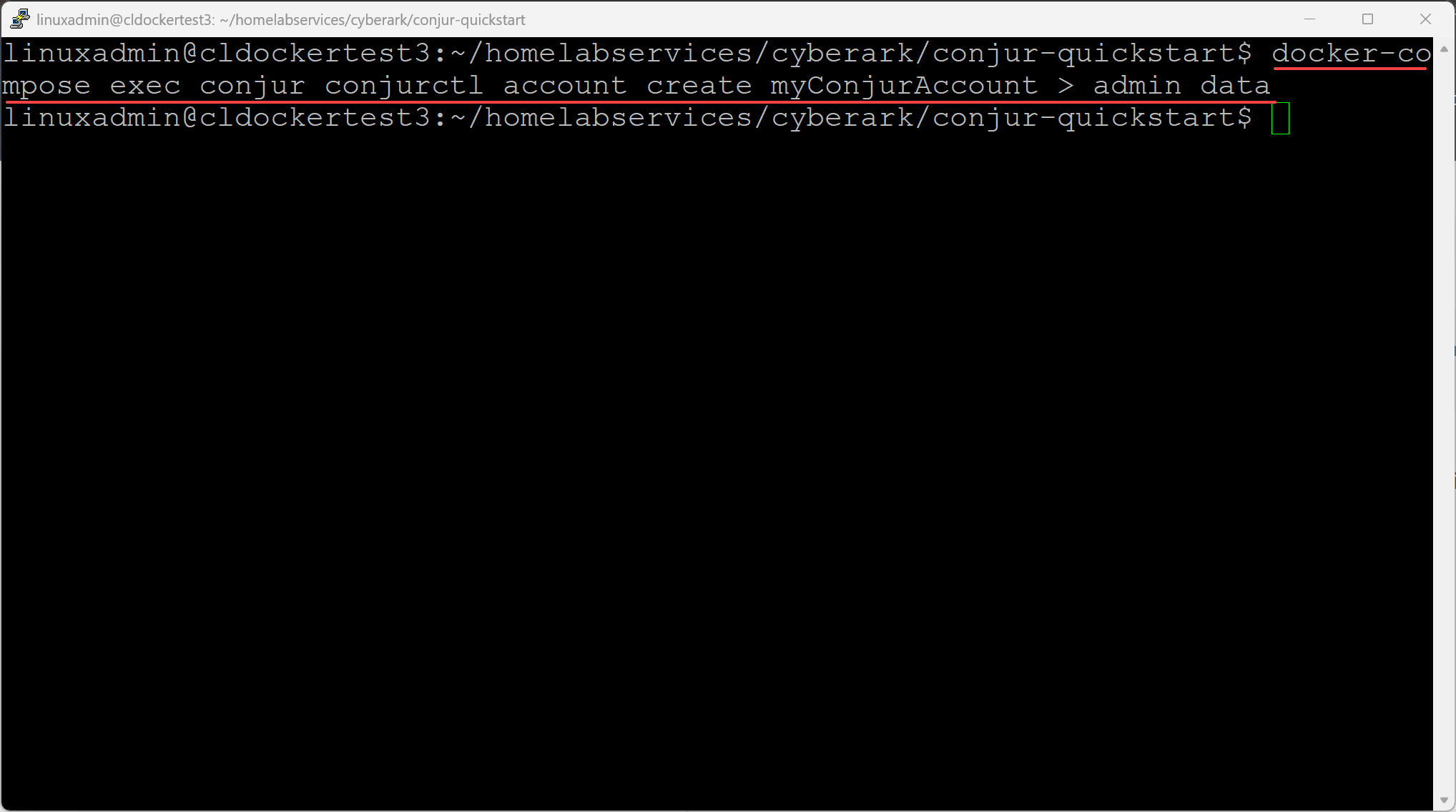
docker-compose up -dNow, we create the admin account with the command:
docker-compose exec conjur conjurctl account create myConjurAccount > admin_dataAn account named myConjurAccount is created and the admin user is initialized, following keys are created and stored at admin_data file:
- admin user API key. Later on, we will use this key to log in to Conjur.
- myConjurAccount Conjur account public key.
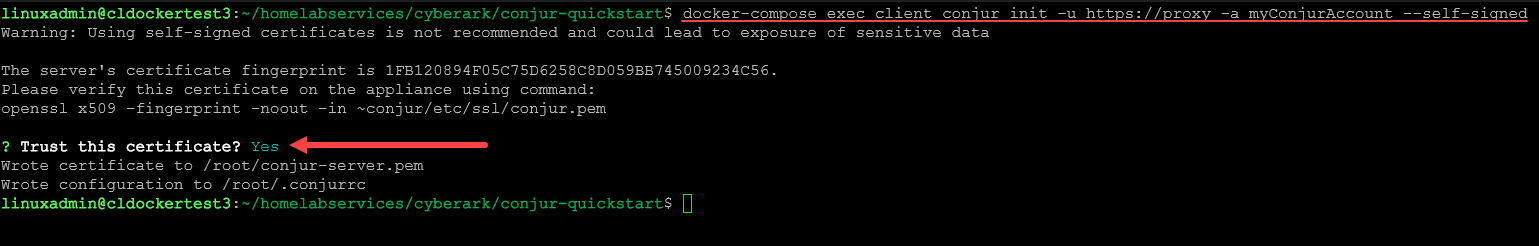
Finally, we connect the client container with the server container. Their documentation mentions this is a one-time action. This will remain connected for the duration of the container’s life or until a different initcommand is issued. You will be prompted to trust the TLS certificate of the Conjur server:
Setup and define your policy
Policies define Conjur entities and the relationships between these. Entities in the Conjur world are anything from a policy, host, user, layer, group, or variable. The git project we downloaded contains a sample application policy called BotApp.yml.
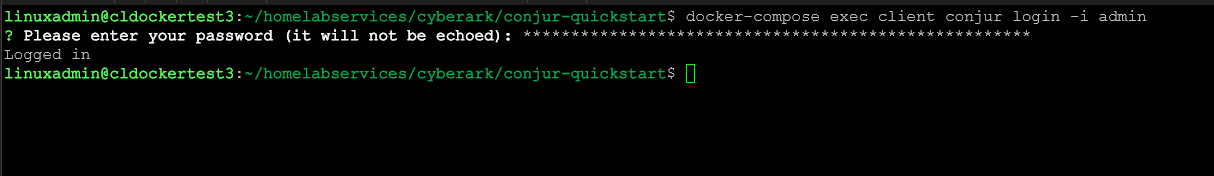
First we will login as admin. You will need the API key found in the admin_data file.
docker-compose exec client conjur login -i adminNow we can load the policy and then log back out:
docker-compose exec client conjur policy load -b root -f policy/BotApp.yml > my_app_data
docker-compose exec client conjur logoutStore the secret
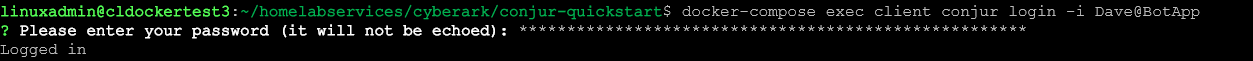
Now that we have the policy loaded, let’s store a secret. You will need the API key in the my_app_data file.
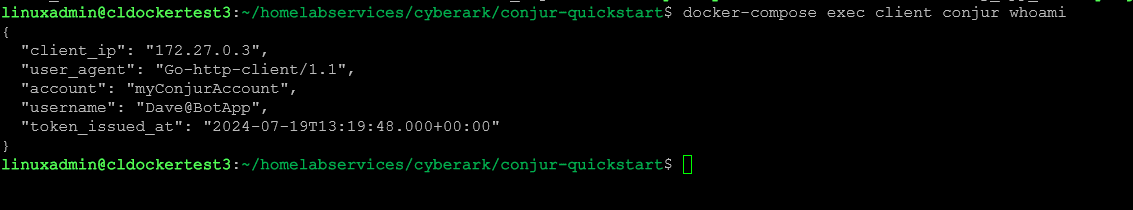
docker-compose exec client conjur login -i Dave@BotAppTo verify you are logged in correctly, use the following command:
docker-compose exec client conjur whoamiNow we generate a secret value:
secretVal=$(openssl rand -hex 12 | tr -d '\r\n')Finally, let’s store the secret:
docker-compose exec client conjur variable set -i BotApp/secretVar -v ${secretVal}Run the CyberArk Conjur demo app
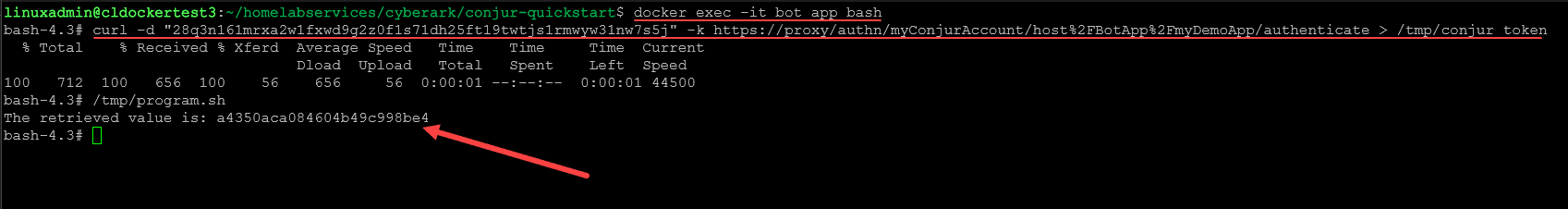
Now we need to start a Bash session, generate a Conjur token and then fetch the secret. First login to a Bash session:
docker exec -it bot_app bashNext, generate a Conjur token. You will need to look at your my_app_data file and get your BotApp API token.
curl -d "<BotApp API Key>" -k https://proxy/authn/myConjurAccount/host%2FBotApp%2FmyDemoApp/authenticate > /tmp/conjur_tokenFinally, fetch the secret:
/tmp/program.shConjur Server and Conjur Secrets Manager Enterprise
There is also an enterprise version of CyberArk Conjur. The enterprise version provides more features, such as enhanced support and scalability. It also has more integration capabilities. Larger organizations with complex secrets management needs will likely benefit from the additional features found in the paid solution.
Learn more about the paid solution here: Identity Security and Access Management Leader | CyberArk.
Wrapping up
As we have seen in the walkthrough, the CyberArk Conjur open source secrets management solution is easy to get up and running with and can start storing your secrets without much effort. For most basic tasks and use cases, the open source solution will likely provide what is needed for most organizations or if you are looking for a secrets management platform for your home lab. Have you tried CyberArk Conjur open source as of yet? What secrets management solution are you using in your environment?