7 Hashicorp Vault Alternatives in 2024

Hashicorp Vault is a popular solution for ones looking at secrets management with DevOps and other workflows. However, there are alternatives out there that have similar features and may offer a better solution for your use case. We will consider 7 Hashicorp Vault alternatives in 2024 to see which one might suit your needs best.
Table of contents
Brief overview of Hashicorp Vault
As a brief overview, Hashicorp Vault is a solution that allows secure management and access to organization secrets. You can store key-value pairs, certificates, and other sensitive data, and have RBAC access configured for all your secrets being accessed.
The solution can run inside a Kubernetes cluster, a Docker container, or it can be hosted in the Hashicorp Cloud.
Why choose a Hashicorp Vault alternative?
One of the big things going on right now with Hashicorp is that it was recently bought out by IBM. From experience, buyouts make people nervous and create uncertainty, as we have seen in other solutions this year ;). So, this reason doesn’t just apply to Vault secrets management solution but the entire Hashicorp catalog.
However, there may be other reasons people want to use something different or that works better for their use case, especially if they are invested in the cloud, such as Azure or AWS, as we will see.
1. Azure Key Vault
If you are invested in the Microsoft ecosystem and migrating resources to Microsoft Azure, using the Azure Key Vault is a natural progression for key management.
Azure Key Vault can manage secrets and encryption keys, and also certificates. So it can secure access and compliance for those invested in Azure. It also provides advanced security features and API key management.
Pros:
- Integration with Azure is seamless if you are already invested there
- Good security features and capabilities
- Industry compliance with regulatory, etc
- API keys management
- Scalable with Azure infrastructure
Cons:
- Best suited for Azure environments, limited cross-platform capabilities
- Potentially higher costs for extensive use
- Learning curve for non-Azure users
2. AWS Secrets Manager
Similar to the discussion ones are having who are moving to Azure and using the Azure Key Vault, AWS Secrets Manager is a viable solution for secrets management for ones investing in Amazon AWS.
As you would imagine, the AWS Secrets Manager integrates tightly with AWS services. So for instance, you can have AWS Secrets Manager rotate passwords in the Amazon Relational Database Service (RDS). With AWS Secrets Manager, you can streamline secret sharing and management. Secrets Manager provides end-to-end secret encryption so keeps information secure along the way. As you can access any other AWS service, you can access secrets manager from both in the cloud and on-premises environments.
Pros:
- Integratio with AWS infrastructure
- Secure secret sharing
- End-to-end encryption
- Automated secrets rotation
Cons:
- Works best with AWS environments
- Can potentially be costly depending on how much it is used
- Limited integrations with services outside of AWS
3. Akeyless Platform
Akeyless is a platform that touts itself as the #1 Hashicorp Vault alternative on their website. Their solution also touts “faultless” secrets management with their SaaS solution, which is an interesting solution to the challenging issue of keeping secrets safe. It allows you to protect and automate access to secrets, including credentials, certificates, and keys.
Their solution combines a cloud-native architecture and robust security framework with their vaultless technology and its use cases includes DevOps cloud workloads and also legacy environments.
Pros:
- Vaultless technology
- Multi-cloud support
- Strong security framework
- Supported by many vendors
- Good management and flexibility
Cons:
- Pricing may be expensive for smaller orgs
- Training may be needed
Learn more about the Akeyless platform here: SaaS Secrets Management | Akeyless.
4. CyberArk Conjur
CyberArk Conjur is an open-source secrets management tool that you can use to do a number of things. These include securing Ansible SSH keys and secrets in playbooks, securing CI/CD pipelines to remove secrets within Jenkins, and provides secure kubernetes secrets. You can lock down Kubernetes secrets with RBAC, native authentication and a few other nice-to-haves.
Pros:
- Helps with compliance with regulatory
- Strong security
- Integration with many platforms
- Open-source
- Good docs and support
Cons:
- Can be complex to setup and manage
- Learning curve
- Limited features in the open-source version compared to enterprise version
Learn more about CyberArk Conjur here: Secrets Management | Conjur.
5. Mozilla SOPS (Secrets OPerationS)
Mozilla SOPS (Secrets OPerationS) is an open-source tool that can help with taking care of managing secrets in a secure way. SOPS encrypts files using AWS KMS, GCP KMS, Azure Key Vault, or PGP. You can use SOPS to work with structured data formats, including but not limited to YAML, JSON, ENV, and INI files.
Pros:
- Supports multiple cloud environments for key management (AWS, GCP, Azure)
- Encrypts structured data formats (YAML, JSON, ENV, INI)
- Easy integration
- Strong community support
- Flexible and versatile
Cons:
- Requires setup and configuration for each cloud provider
- May require additional scripting for complex workflows
- Limited to file-based secret management
- Not as feature-rich as some commercial products
Learn more about SOPS here: SOPS: Secrets OPerationS (getsops.io).
6. Doppler
Doppler is another solution that is available as a SaaS product. This means you can get setup in a fully managed solution pretty easily without having to design the underlying architecture. Doppler allows managing secrets as you would expect and is compatible with multiple cloud providers and development tools. Its focus seems to be ease of use and automation capabilities.
Pros:
- Fully managed
- Quick setup (they tout 30 minutes for some teams)
- Centralized management of environment variables and secrets
- Integration with multiple cloud providers
- User-friendly interface
- Automation features for secret rotation and management
Cons:
- Some limitations compared to other commercial products
- May need additional customization for complex workflows
Learn more about Doppler secrets management here: Doppler Secrets Management.
7. Kubernetes Secrets
Kubernetes Secrets is an open-source solution. It is used for managing sensitive information in Kubernetes environments. It can store information such as passwords, tokens, and keys. As you would expect, it also provides strong integration with existing Kubernetes workflows.
Pros:
- Strong Kubernetes integration
- Cost-effective and flexible
- Open-source community support
Cons:
- Secrets are stored unencrypted in the API server’s underlying data store (etcd)
- Anyone with API access can retrieve or modify a Secret
- Limited to Kubernetes environments
- Basic features when compared to enterprise solutions
- Requires Kubernetes knowledge and expertise
- Does not support hardware security modules
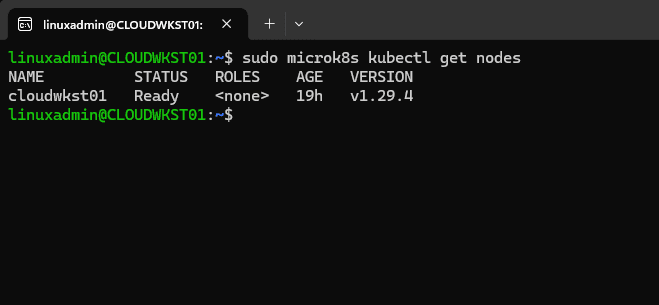
Below is an example dev Microk8s cluster.
To use kubectl to create a new generic DB user password might look like something like the below:
kubectl create secret generic db-user-pass \
--from-literal=username=admin \
--from-literal=password='S!B\*d$zDsb='Wrapping Up
Hashicorp Vault is a great solution for secrets management and you can use it for free. However, some may not want to be tied to the Hashicorp ecosystem moving forward with the buyout from IBM and other reasons. As we can see with these Hashicorp Vault Alternatives we have considered, there are many great secrets management software solutions with enterprise features out there for secrets management that allow for storing secrets and other sensitive data so that these are much less likely to be compromised. Let me know in the comments what solutions you are using and if there is one not on the list that works well.










I am missing OpenBAO as an open source Alternative. This is a fork of HC Vault.
Claus,
Thanks so much and great call out! Definitely this is a good one to add to the list. I will update and provide some links.
Thanks again,
Brandon