vSphere Distributed Switch Configuration and Best Practices Guide
VMware vSphere has many advanced networking features as part of the solution. These allow VIadmins to configure just about any setting they need for their network. By default, the vSphere Standard Switch is the default network configuration that comes “out of the box” with a VMware ESXi host installation and virtual switches. However, there is another kind of switch that has many benefits to your virtual infrastructure, called the vSphere Distributed Switch (VDS). Let’s look at the vSphere Distributed Switch and see what it is and how it is configured.
Table of contents
- What is a vSphere Distributed Switch?
- vSphere Distributed Switch Architecture
- Advantages of Using vSphere Distributed Switch
- Key Features of vSphere Distributed Switch that make them worth it
- Create a VMware vSphere Distributed Switch
- Adding Hosts and Uplink Port Group
- Configuring Distributed Port Group
- Managing Network Traffic with vSphere Distributed Switch
- Migrating to vSphere Distributed Switch
- Best Practices for vSphere Distributed Switch
- Wrapping up
What is a vSphere Distributed Switch?
The vSphere Distributed Switch (VDS) is an advanced virtual network switch with advanced networking features and packet switching for VI admins to use with their virtual machines. It provides centralized management of network configurations at the vCenter Server level so that you can have consistent networking across all hosts added to vCenter.
The vSphere standard switch is only created and available locally to each ESXi host. Even if the network label is the same across all hosts, the management and configuration is performed at the ESXi host level. This leads to scalability issues when you are managing dozens, hundreds, or even thousands of hosts.
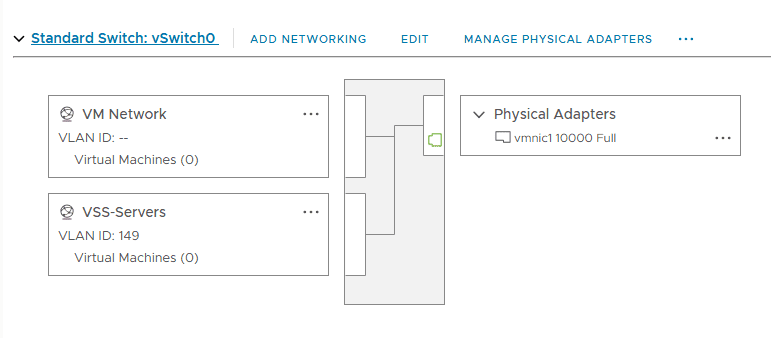
Below is an example of the default vSwitch0 that is installed by default as the first vSphere Standard Switch.
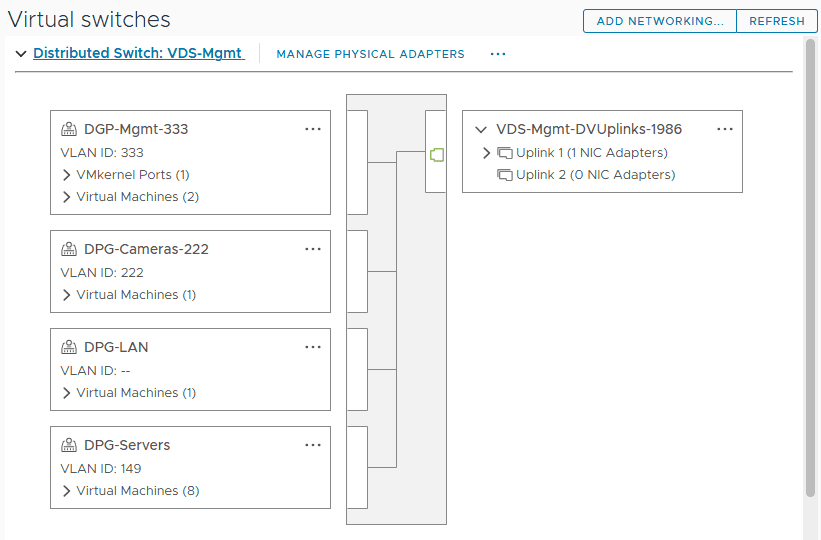
The vSphere Distributed Switch decouples network configuration from individual ESXi hosts and then centralizes it in the vCenter Server so that the configuration is housed centrally in vCenter rather than on each ESXi host. Below is an example of a vSphere Distributed Switch.
vSphere Distributed Switch Architecture
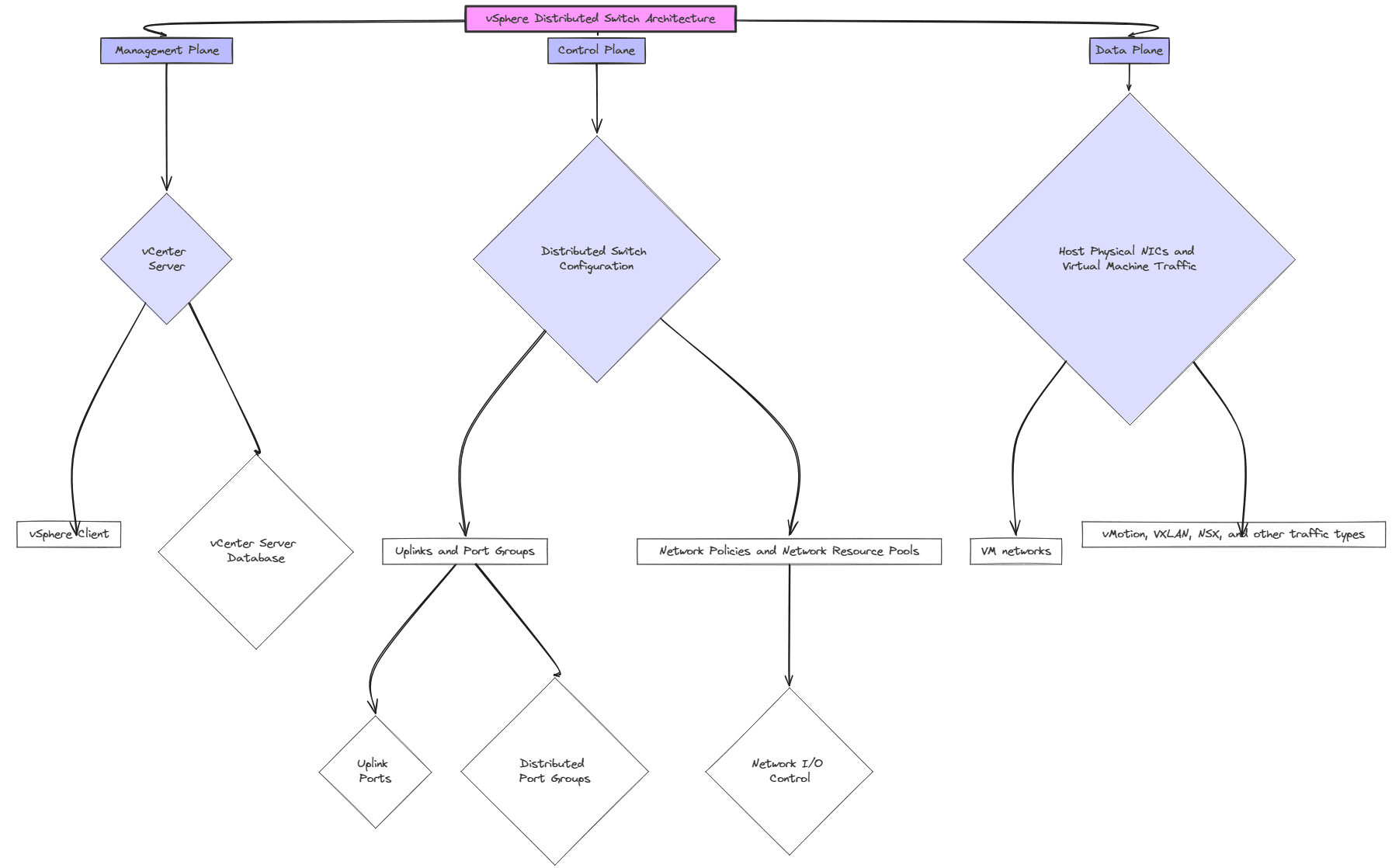
Note the following architecture overview of the vSphere Distributed Switch and the components involved.
Note the following components that are integral to the configuration of the vSphere distributed switch:
- Management plane – includes vCenter Server holds the configuration database and owns the management plane of the VDS
- Control plane – houses the distributed switch configuration, uplinks and port groups, network policies and network resource pools, uplink ports, distributed port groups, network I/O control
- Data plane – holds the host physical NICs and virtual machine traffic along with VM networks, vMotion, VXLAN, NSX, and other traffic types
Advantages of Using vSphere Distributed Switch
There are many advantages to using the vSphere Distributed Switch (VDS) when you need certain features or management reasons. Let’s talk about the advantages of the VDS and the reasons you would use a VDS as opposed to a VSS configuration.
Simplified Network Management
Arguably, one of the major benefits of using a vSphere Distributed Switch is ease of management. Since the management plane for the VDS exists in the vCenter Server, the configuration changes can be centralized for virtual networking configuration in ESXi for your virtual machine.
Having a centralized management plane for your vSphere Distributed Switch means that changes to the network configuration like adding VLANs, changing security configurations, and other settings are made in one place and then the changes are propagated to all the hosts that are assigned to the vSphere Distributed Switch.
Network Monitoring
Another area of enhancement with the vSphere Distributed Switch is monitoring. The VDS offers enhanced monitoring. With the vSphere Distributed switch, you can setup port mirroring and link layer discovery protocol (LLDP). For getting monitoring details at the network level, these are great enhancements that allow network admins and VIadmins to analyze traffic and troubleshoot issues.
With port mirroring admins can capture traffic, and LLDP allows providing visibility in the network topology.
Network Security
One of the advantages when it comes to network security with the vSphere Distributed Switch is that it allows centralized and consistent network security configurations at the network switch level. Instead of depending on changes to be performed locally on each ESXi host, the VDS makes it where you make the change one place and all the ESXi hosts receive the same network change identically.
Private VLANs (PVLANs) can also be used with vSphere Distributed Switches. VIadmins can use PVLANs and network security settings to configure and isolate traffic to prevent unauthorized access and insecure network settings in the virtualized environment.
Key Features of vSphere Distributed Switch that make them worth it
There are several key features that go along with the VDS vNetwork switch. Note the following:
- Centralized management plane
- Advanced networking features
- Distributed port groups
Centralized Management Plane
We have already alluded to this above, but the centralized management plane is one of the key differentiators between the vSphere Distributed Switch and the vSphere Standard Switch. The management plane is housed at the vCenter Server level, while the data plane (where traffic actually flows) is housed at the ESXi host level.
With this separation of management and data plane network configuration, it allows admins to configure, monitor, and setup network settings from vCenter Server. This helps to reduce the overall complexity of the virtual network configuration.
Advanced Networking Features
While we have mentioned port mirroring, there are other advanced networking features to note with vSphere Distributed Switch configurations.
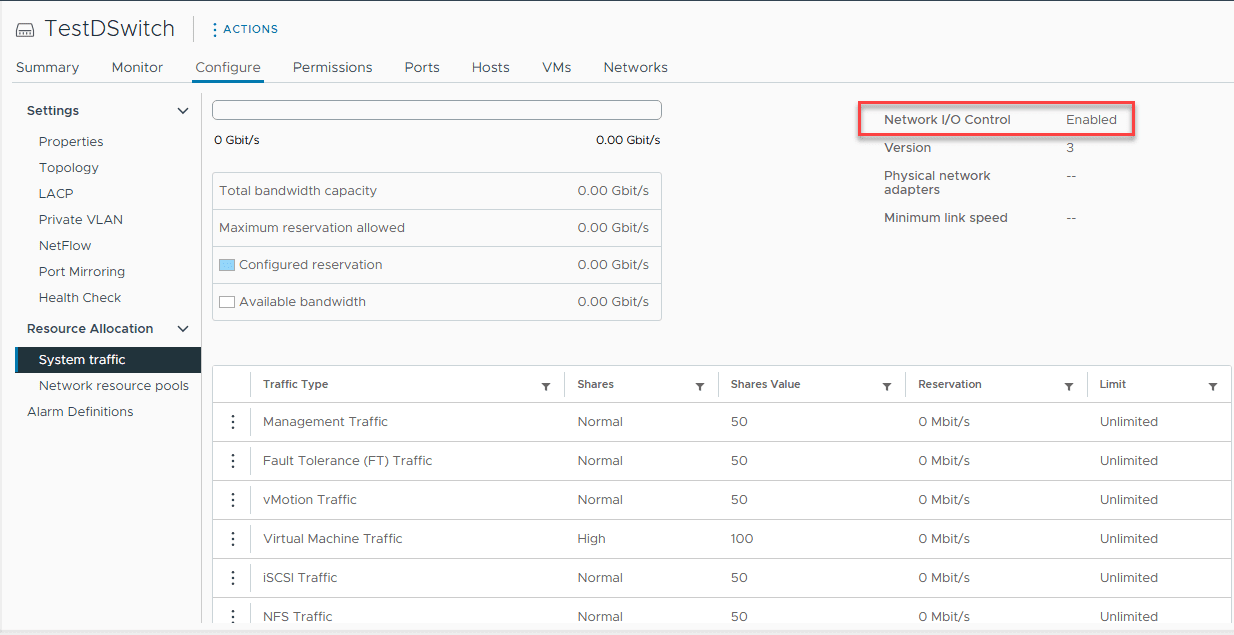
VDS switches can also perfor traffic shaping, and they have something called network I/O control. Traffic shaping allows control over bandwidth usage and network I/O control makes sure that important types of traffic and applications get the necessary bandwidth they need for ultimate performance.
Distributed Port Groups
Like the vSphere Standard virtual switch, port groups are the network component where you connect virtual machines to different virtual networks. Distributed port groups are used to define settings like VLAN IDs. You also set the security policies, and traffic shaping policies at the distributed port group level.
Create a VMware vSphere Distributed Switch
The process to create a vSphere Distributed Switch is straightforward. To set this up, we log in to vCenter Server and navigate to the networking configuration.
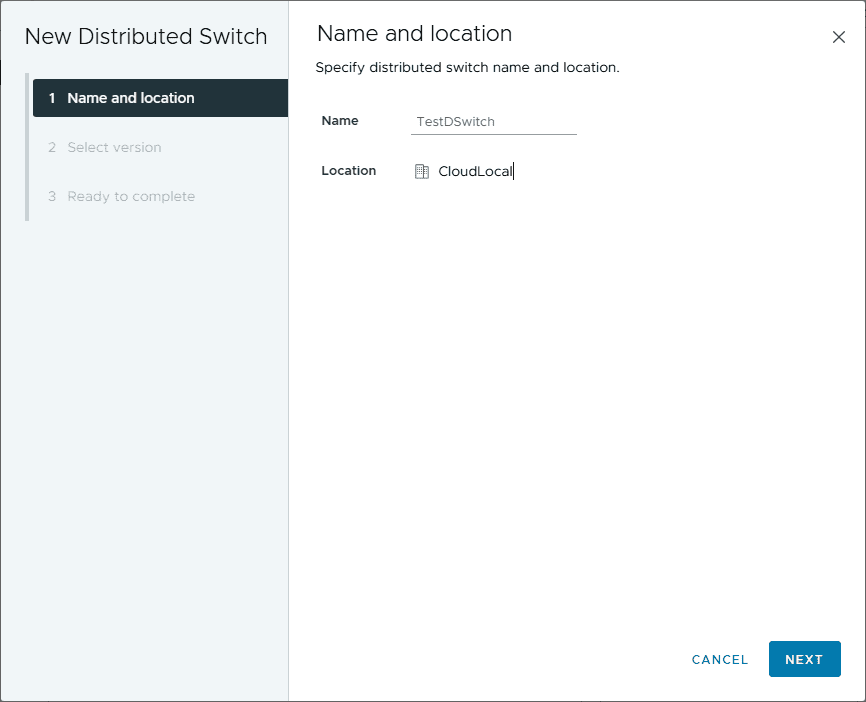
Click the networking icon. Right-click the datacenter (here it is called CloudLocal), click Distributed Switch > New Distributed Switch.
Name the new vSphere Distributed Switch.
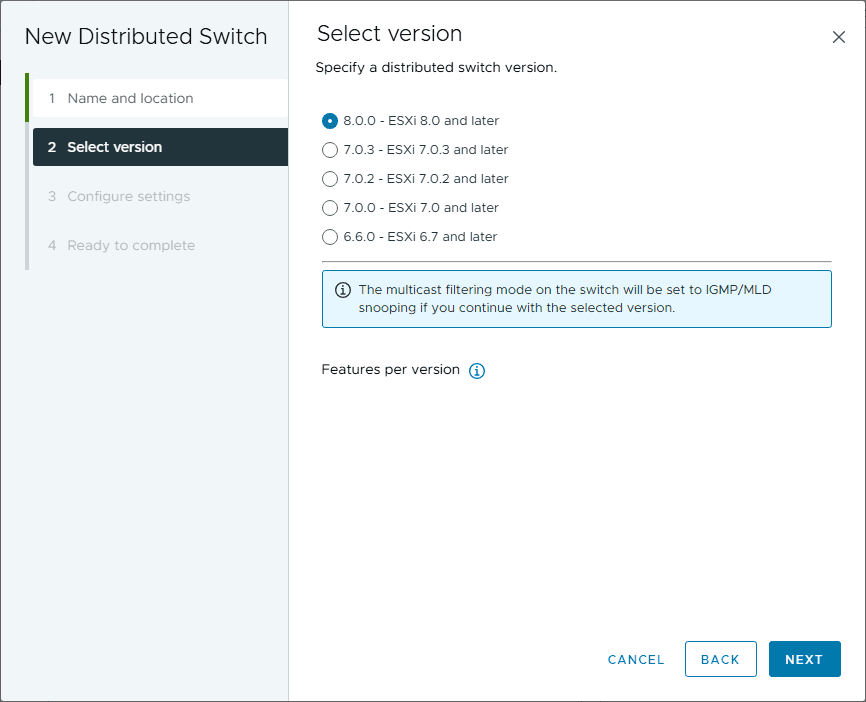
Set the version of the vSphere Distributed Switch.
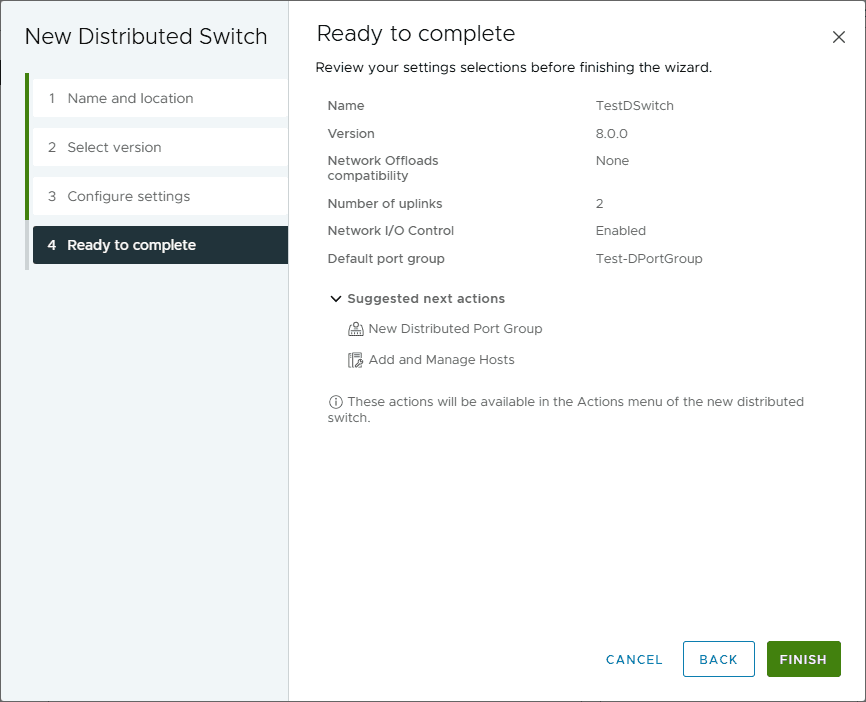
Next, configure the settings for the new vSphere Distributed Switch, you can set the network offloads compatibility and network I/O control settings, which are enabled by default. You can select to create a default port group and the default port group name.
Finally, we are ready to complete the creation of the new distributed switch. Click Finish.
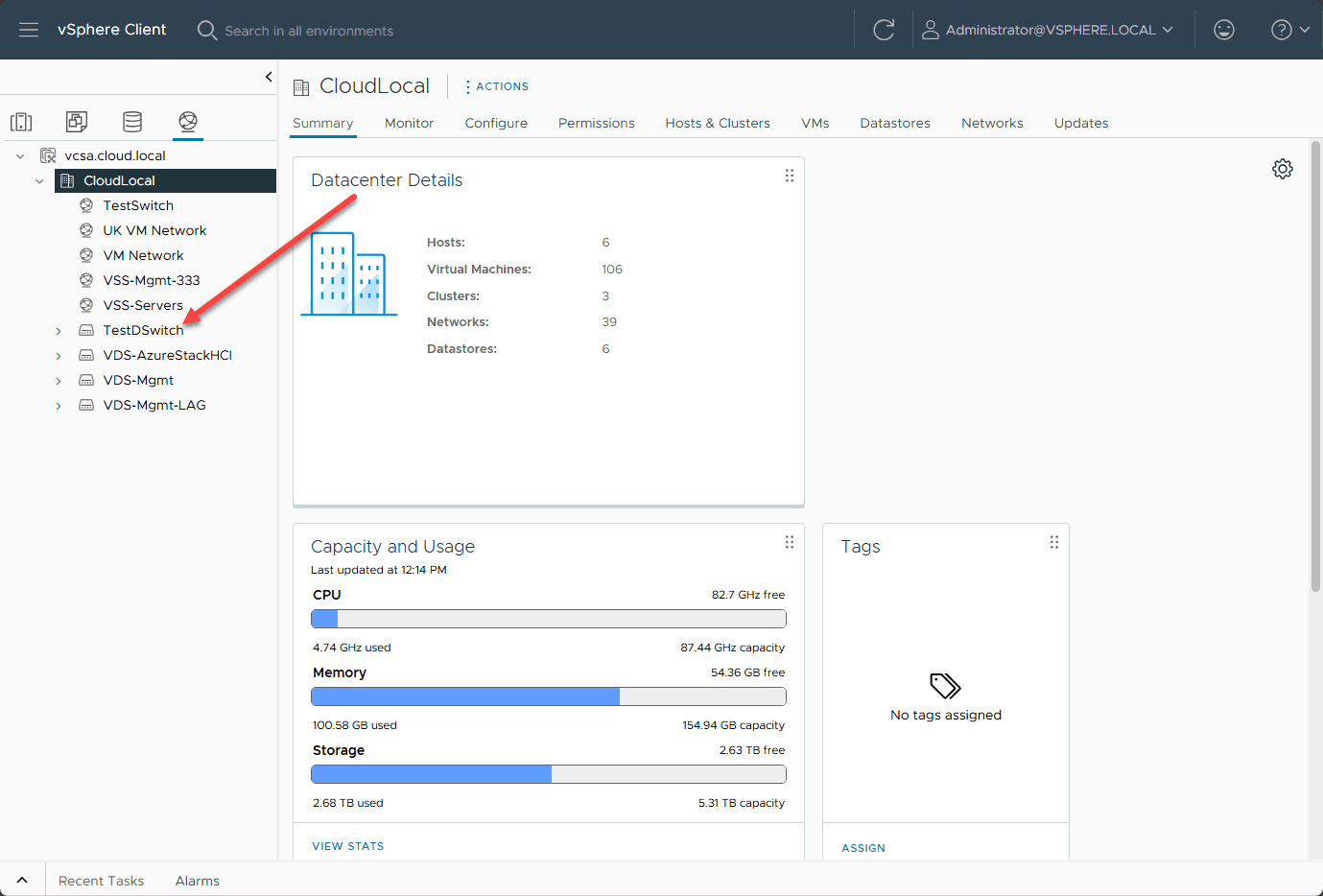
After creating the switch, it is listed in our virtual networks.
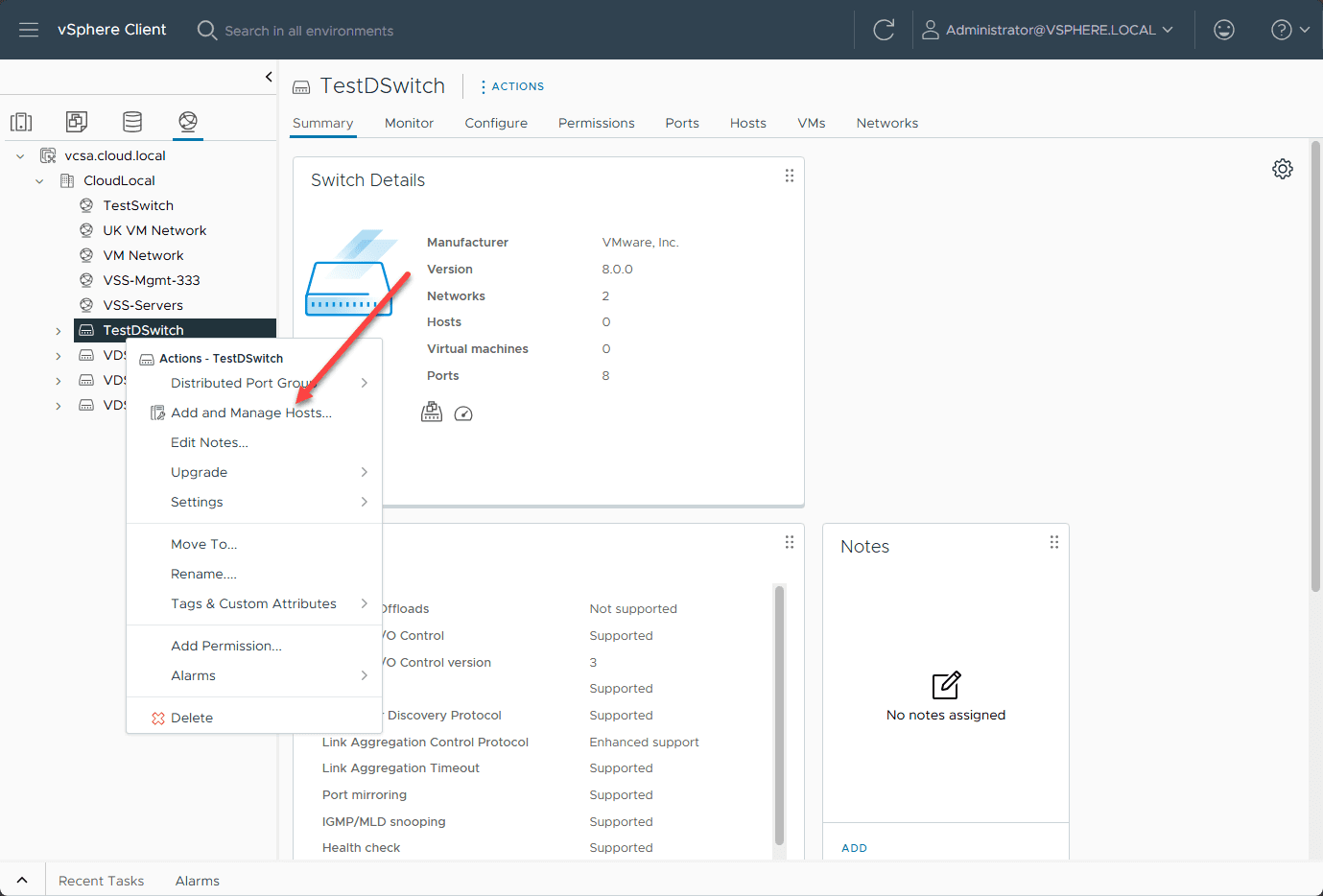
Adding Hosts and Uplink Port Group
Once you create the vSphere Distributed Switch and vSphere Distributed port group, these are not automatically added to every ESXi host in the environment. You have to add hosts to the virtual switch. The uplink port group is used to manage physical network adapters. It helps with redundancy and load balancing. With load balancing configuration setups, network traffic is spread across multiple adapters and helps provide high availability.
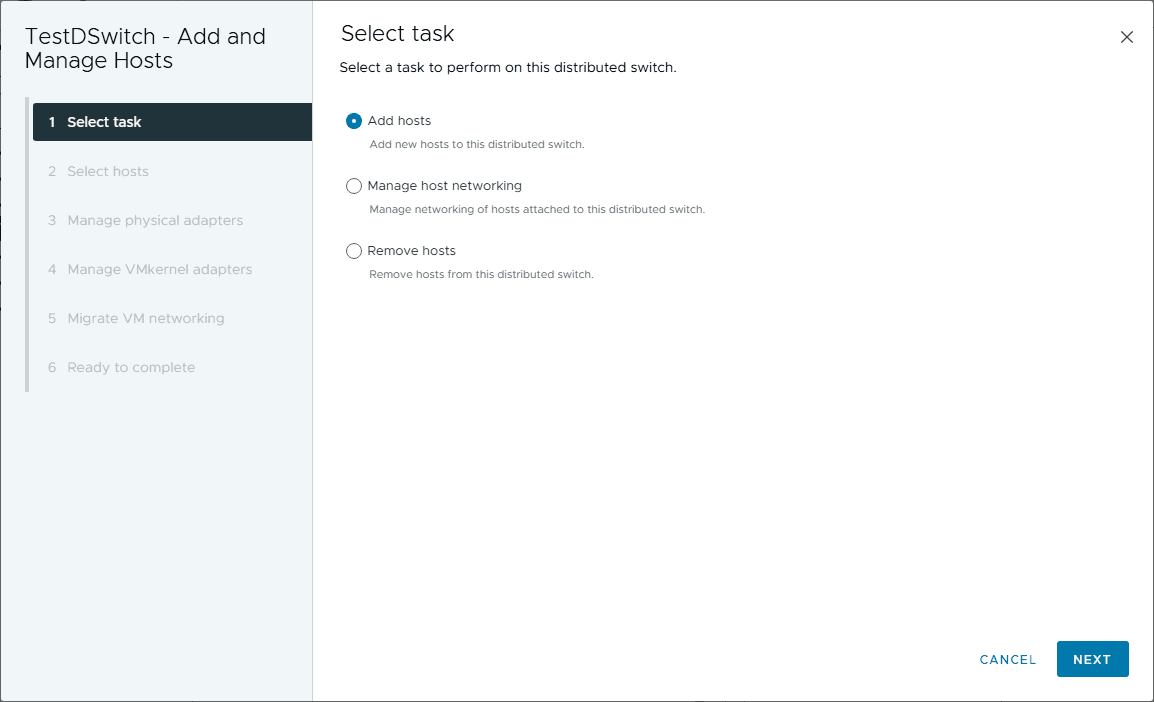
As you can see with the select task screen, you can:
- Add hosts – This is the option needed after you created a new vsphere distributed switch. We need to add hosts to it
- Manage host networking – Once you have added hosts to the VDS, you can use the manage hosts networking option to change configuration settings for the host
- Remove hosts – Use this option to remove a host from a VDS
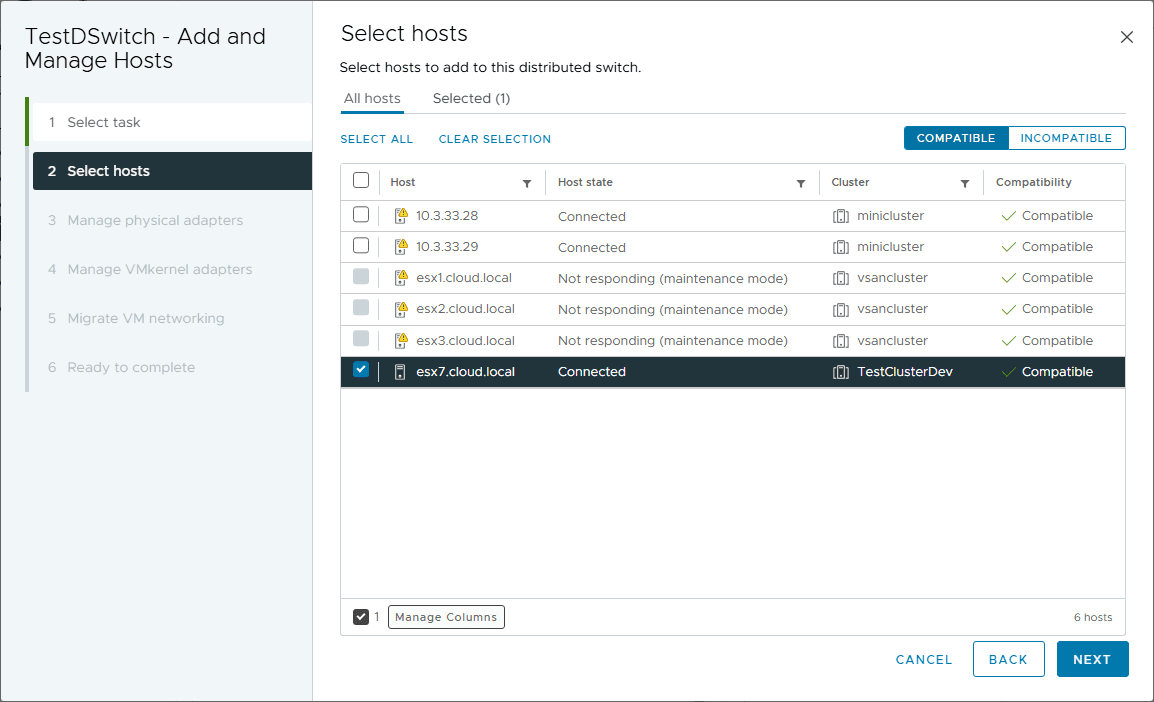
Select your host from the environment.
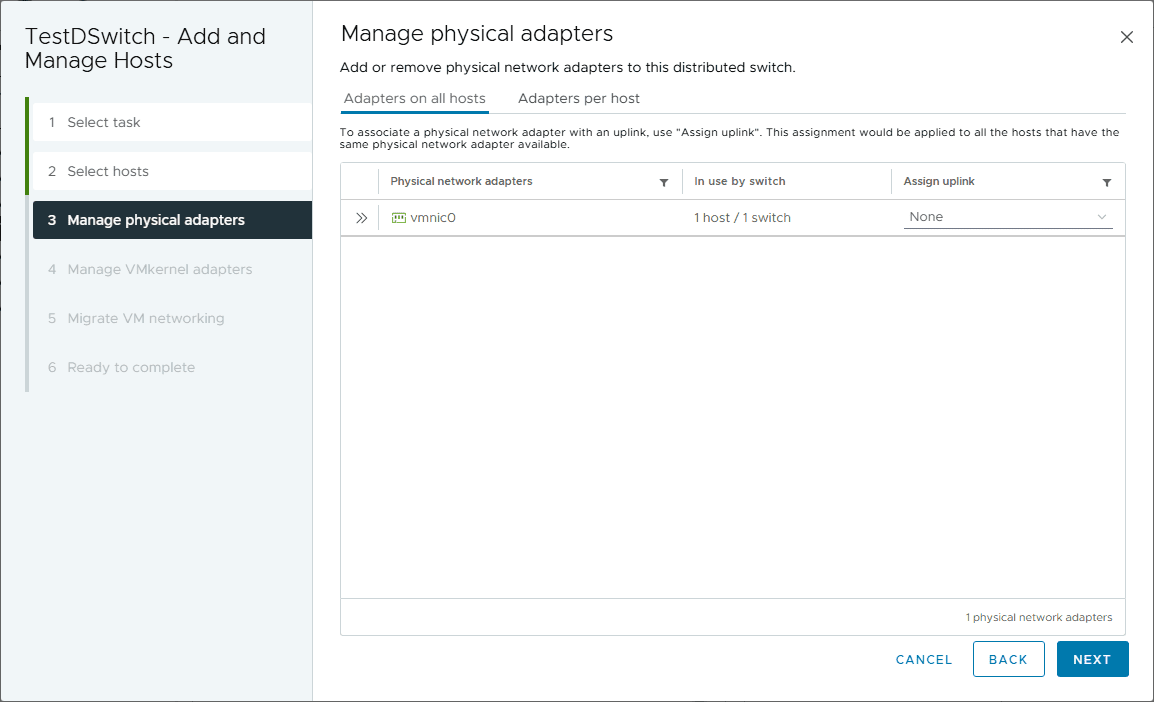
Manage physical adapters. On this screen, you select the uplink “slot” you want to assign the vmnic to in the configuration.
VMkernel network adapters allows you to assign the port group on the new vSphere Distributed Switch.
On step 5, you get to the Migrate VM networking screen. Once you get here, you have the ability to confgure the VM networking on a per network adapter level or configure per virtual machine. The per virtual machine level is a more granular approach where you can choose exactly which virtual machines are moved to the new vsphere distributed switch and vsphere distributed port group.
Below is the screen showing the virtual machine networking for migrating “per virtual machine” to show what this screen looks like.
Ready to complete adding a host to the new vSphere Distributed Switch VDS.
Configuring Distributed Port Group
Configuring the distributed port group is required to set configuration such as VLAN IDs, security policies, and traffic shaping policies. Administrators can also configure load balancing and failover policies for the port groups.
Right-click on the vSphere Distributed Switch you want to add the port group to
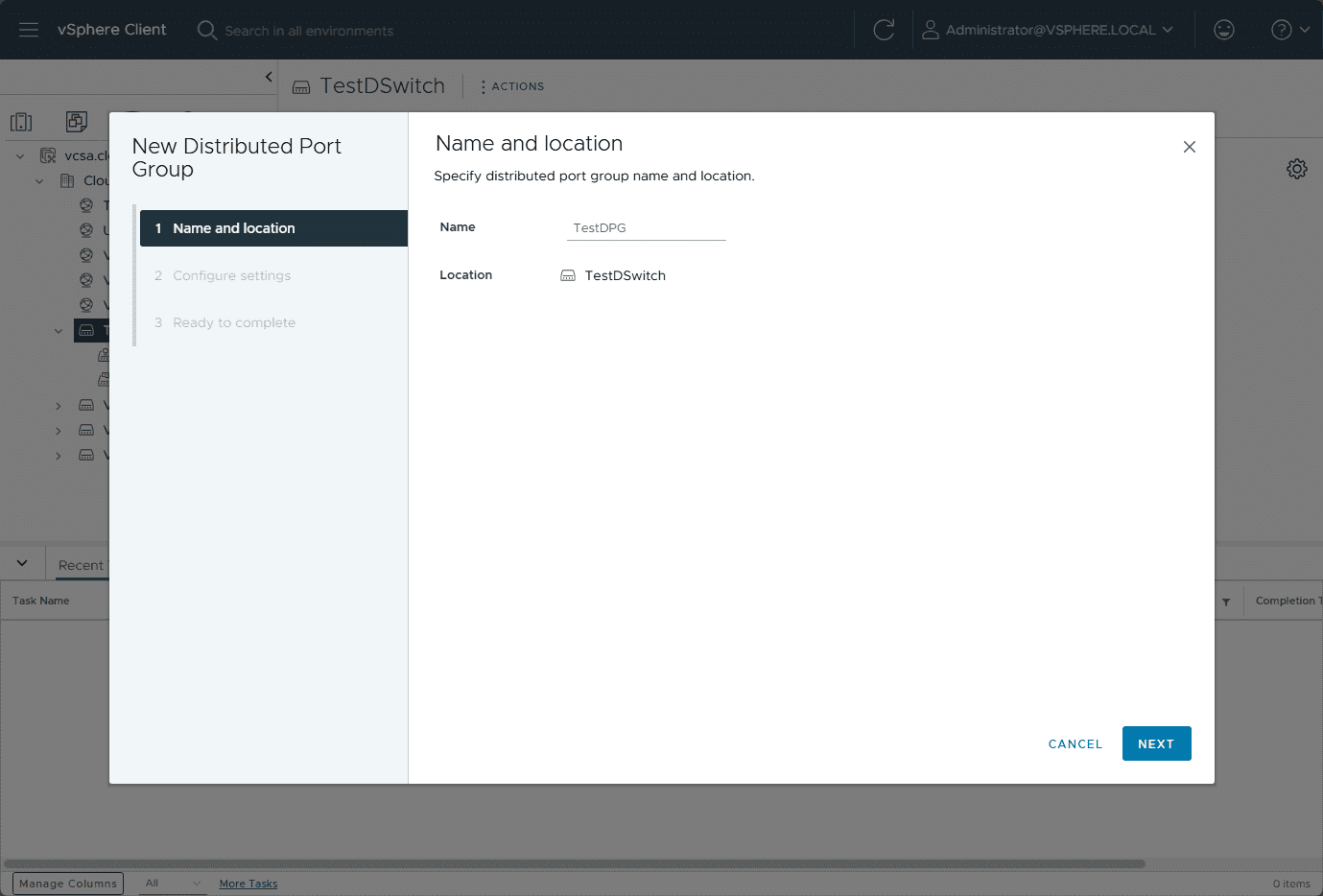
Name of the new distributed port group.
Configuring settings for the port group, including the port binding, port allocation, number of ports, network resource pool enablement, VLAN tags, and we are checking the box to customize the default policies configuration.
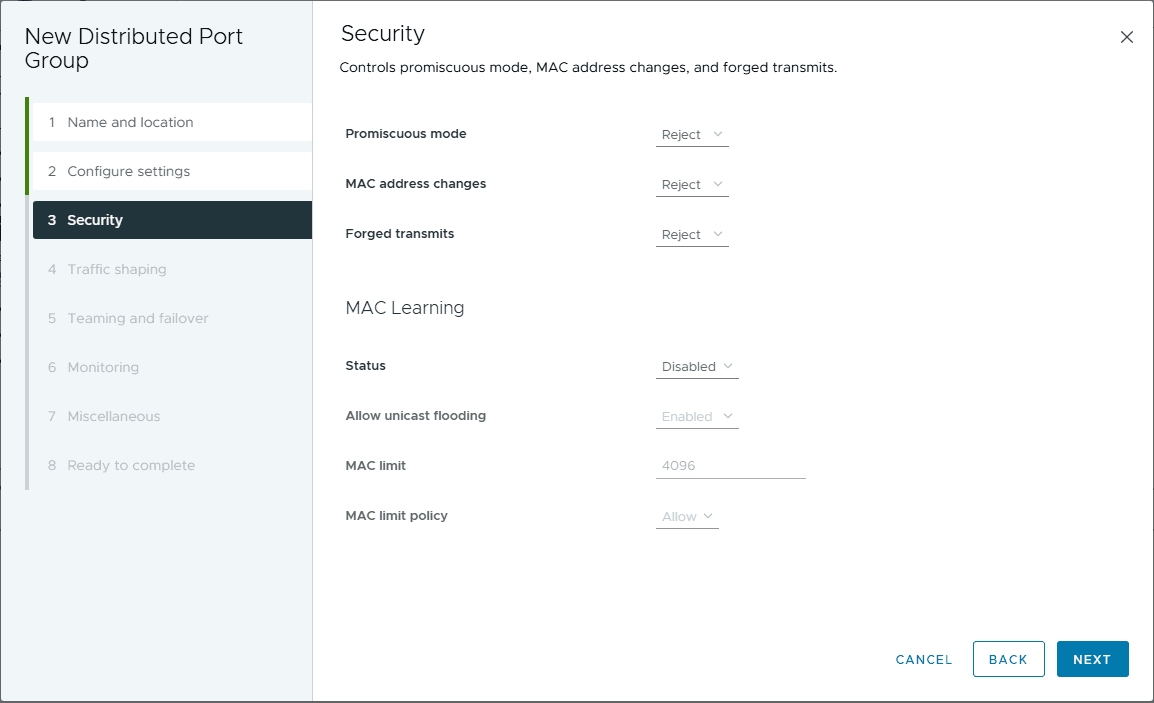
Next, we can set the security policy settings, including promiscuous mode, mac address changes, forged transmits, and mac learning (which is great for home labs and nested virtualization).
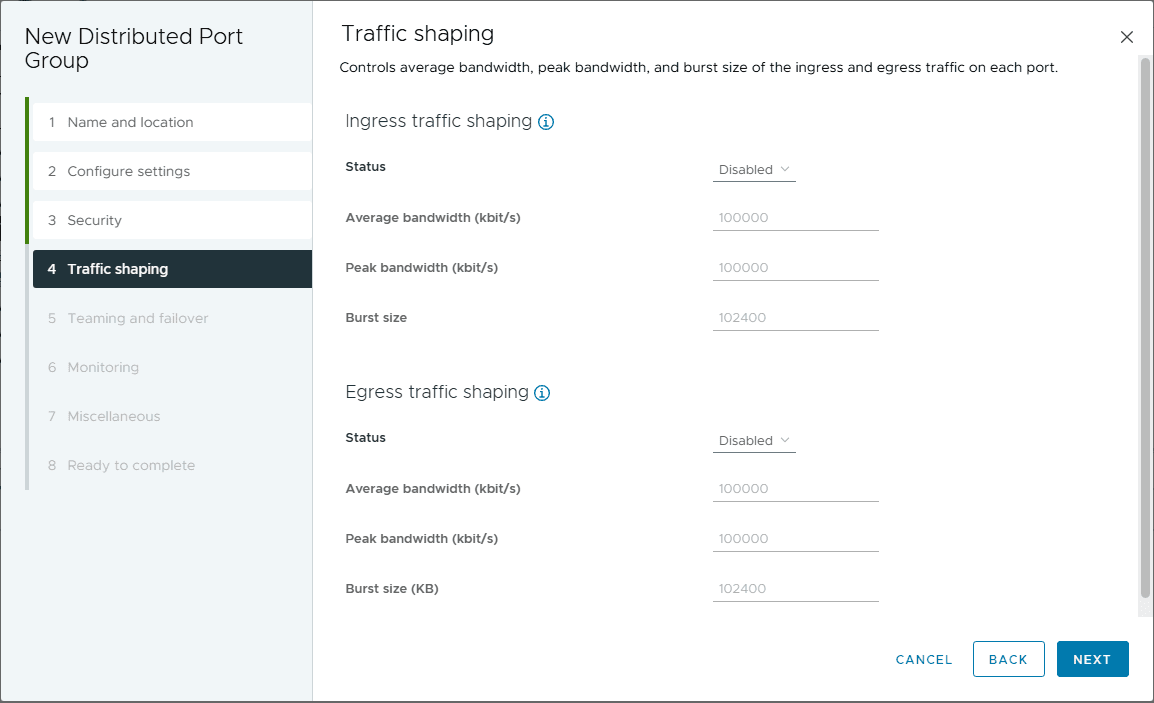
You can configure traffic shaping for the port group as well, both ingress and egress.
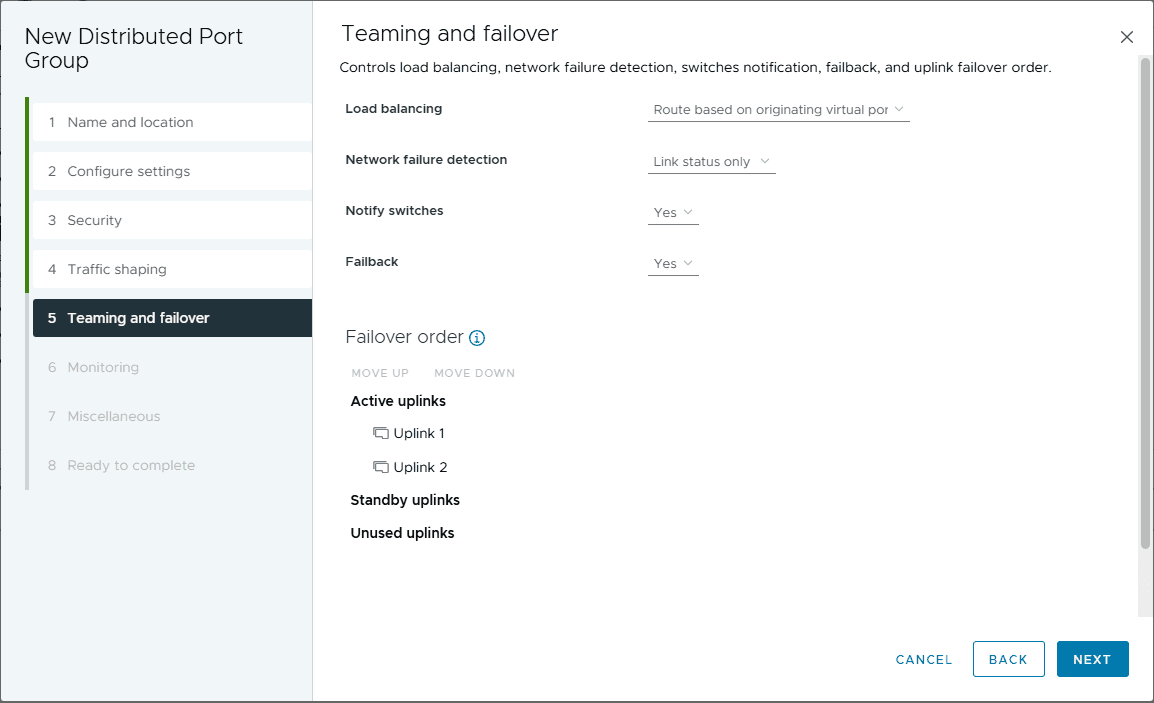
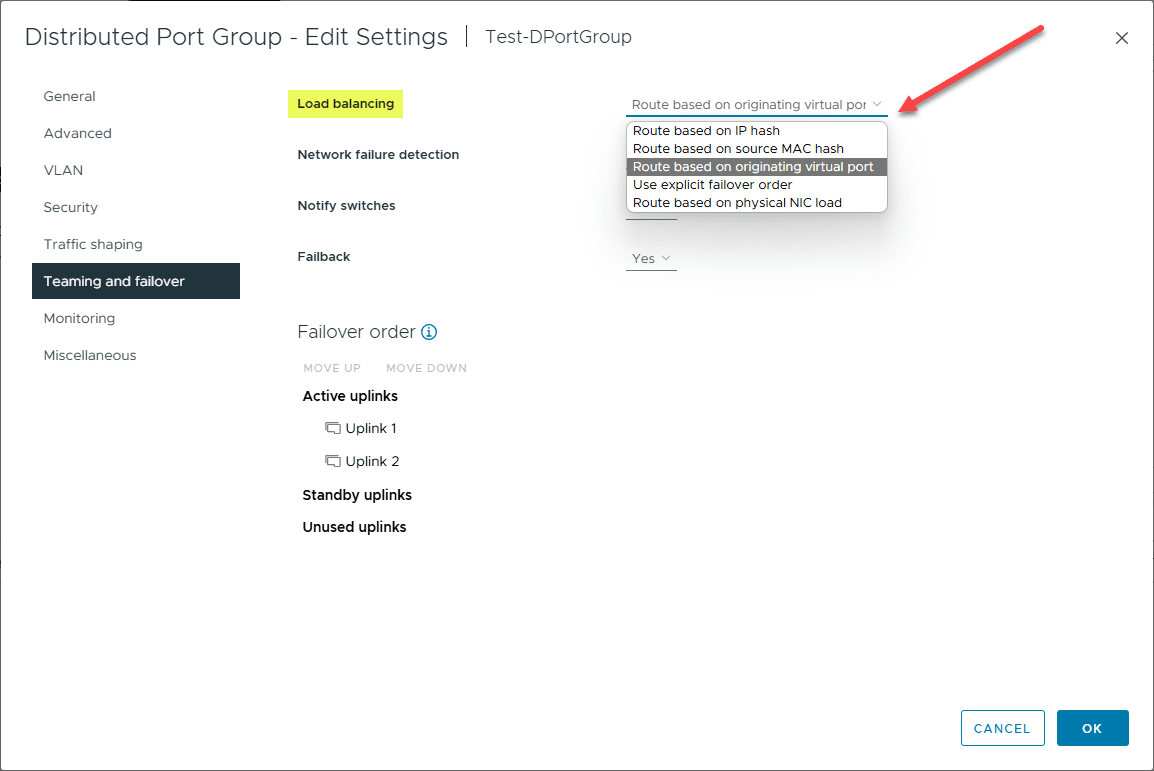
Next is teaming and failover. You can set the load balancing configuration you want to implement, along with the failover order.
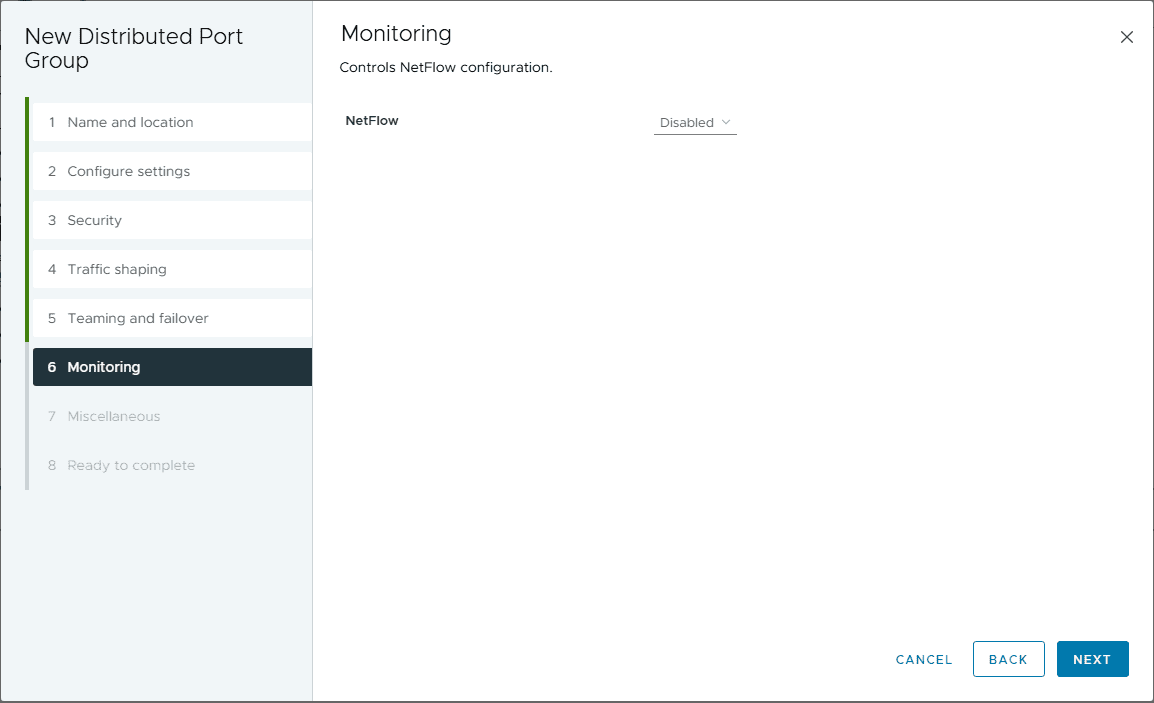
Enable netflow monitoring.
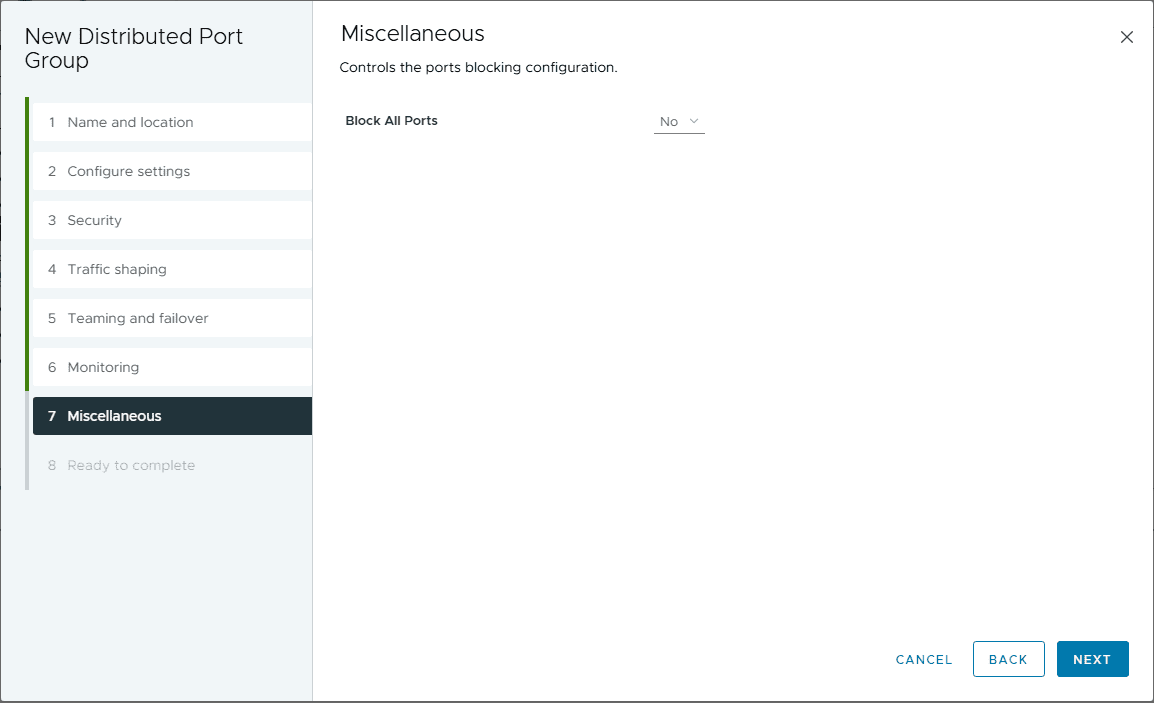
Miscellaneous settings, including implementing block all ports.
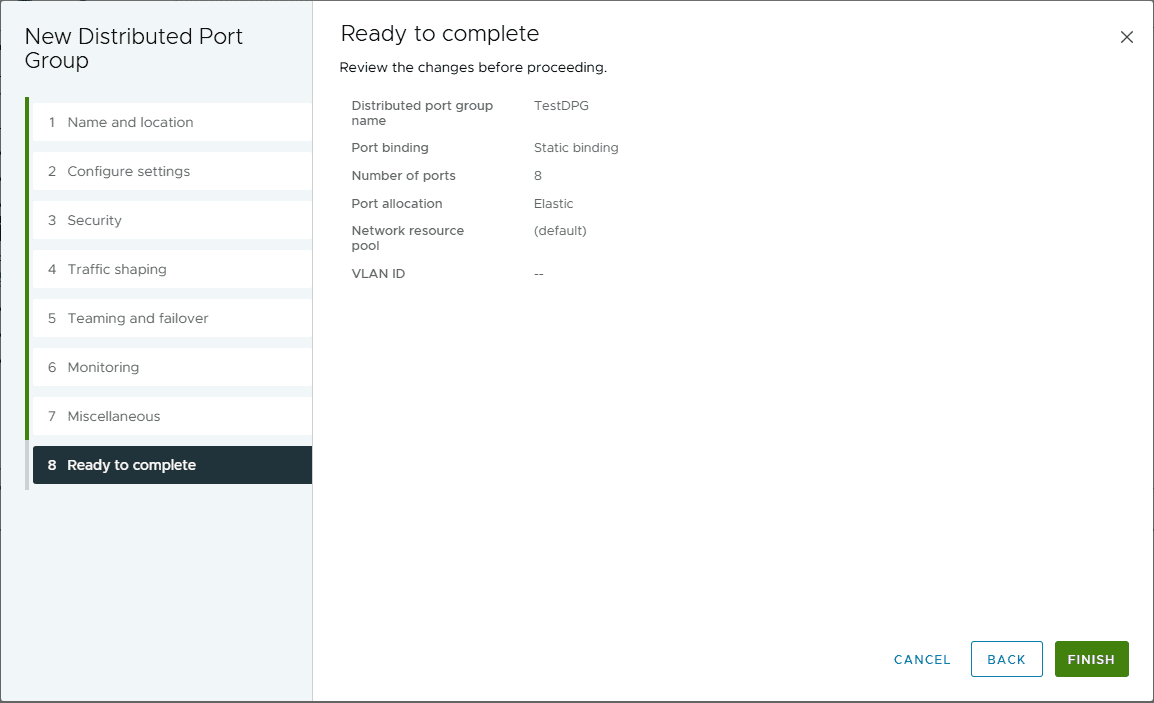
Ready to complete the configuration of the new vSphere distributed port group.
Managing Network Traffic with vSphere Distributed Switch
Traffic Shaping and Network I/O Control
Traffic shaping policies can manage the bandwidth for different types of network traffic. Network I/O Control allows VI admins to prioritize critical traffic over less important traffic.
Link Aggregation Control Protocol
Link Aggregation Control Protocol (LACP) is used for combining multiple network connections into a single logical link. This helps to increase bandwidth and it also provides redundancy. With this configuration you can improving overall network reliability. LACP also allows for dynamic adjustment of the aggregated links.
Load Balancing Configuration
Load balancing in vSphere Distributed Switch is configured to distribute network traffic evenly across physical network adapters. This helps prevent network bottlenecks and ensures optimal performance. Load balancing policies such as route based on originating virtual port or route based on IP hash can be selected based on the network setup.
Migrating to vSphere Distributed Switch
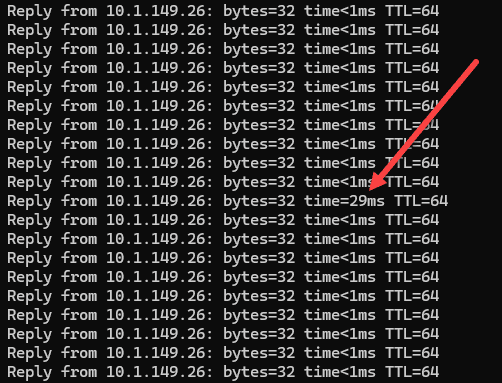
Migrating VM networking to a vSphere Distributed Switch includes moving virtual machines from standard switches to the distributed switch. You can migrate VMs in real time without shutting them down, with minimal impact. The process migrates port groups and makes sure that network configurations are consistent.
You can do this when you Add and Manage hosts in the vSphere Distributed Switch configuration. On step 5, you can configure the virtual machine networking, select the VM, then select the distributed port group you want to attach it to.
No dropped pings, just a slightly elevated ping when it cuts over.
Managing the Host Proxy Switch
Host proxy switches act as intermediaries during the migration process. They ensure that network settings are applied correctly to the ESXi hosts. Host proxy switches help maintain network connectivity during the migration.
Best Practices for vSphere Distributed Switch
Note the following best practices for using vSphere Distributed Switches.
Don’t use VDS just to use VDS
vSphere Distributed Switches add complexity to the environment when compared to vSphere Standard Switches. You have to be licensed to use them. If you have only 3 hosts and a couple of VLANs, you will probably not benefit greatly from a management perspective by using vSphere Distributed Switches.
However, keep in mind that if you are going to use LACP even with a small number of hosts or you need port mirroring, you can’t do this with vSphere Standard Switches.
High Availability
High availability is critical for vSphere Distributed Switches. Using features like LACP and multiple uplink port groups helps maintain network connectivity even if one or more physical network adapters fail. Make sure you have multiple uplinks and failover policies should be configured to handle network failures.
Monitoring and maintenance
Regular monitoring and maintenance help keep the vSphere Distributed Switch healthy. You can use tools like network health check and proactive network monitoring to detect and resolve issues before they impact the virtual environment.
Backup your vCenter and VDS configuration
When using VDS configurations, backing up your vCenter Server becomes even more critical. Since the VDS configuration lives in vCenter, losing vCenter Server would not be good when you have all distributed switches across the environment.
Wrapping up
As we have seen, vSphere distributed switches have many advantages over vSphere Standard Switches. They can do things like LACP, traffic shaping, port mirroring, and provide an easier management experience, if you have lots of hosts and VLANs. They have their place in the environment. There are still many situations where VSS makes the most sense, and in many small to mid-sized environments, VSS switches work just fine.




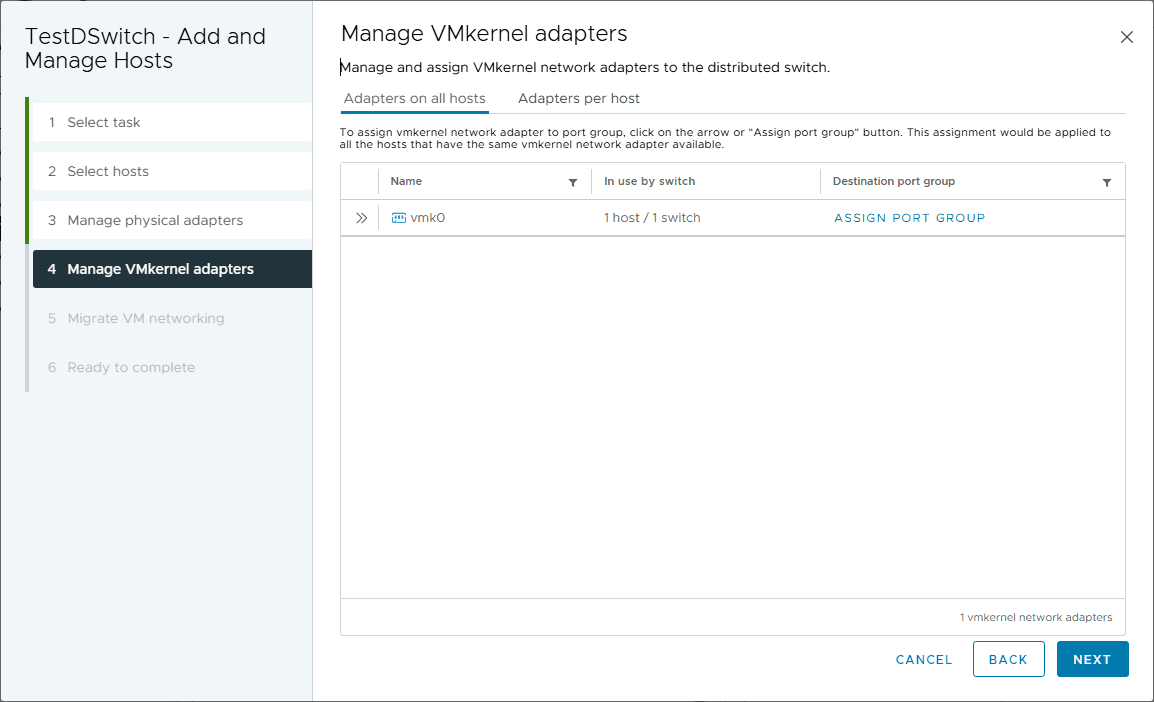
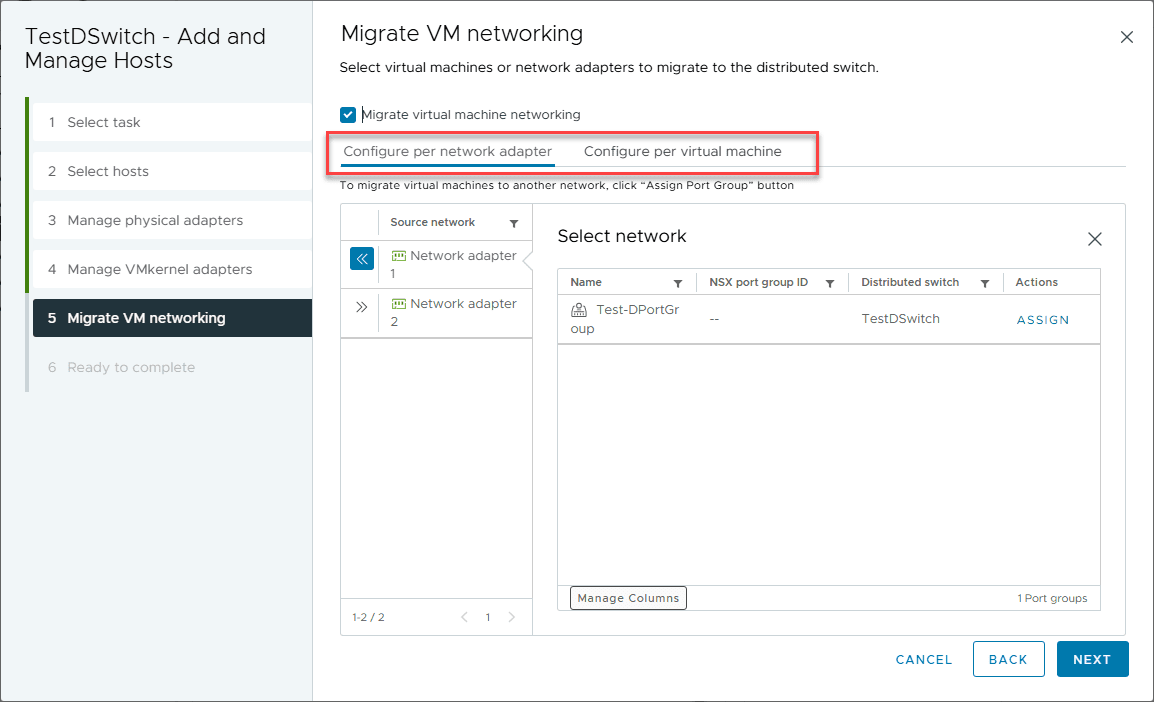
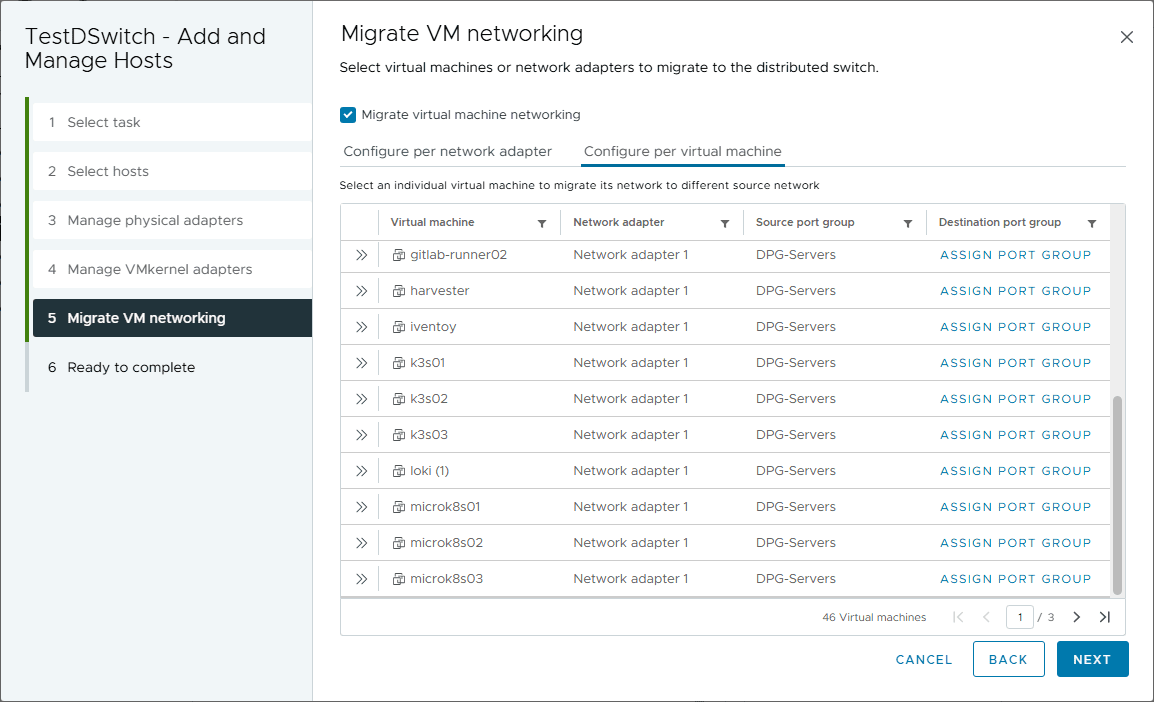








Creating VMkernel adaptors is where I always have to click around and figure out how all over again. It’s not done often, so I have an excuse, but it’s not an intuitive process.
Jeff,
I am totally with you. It seems like they could improve the interface on that side to be a little more intuitive and user friendly.
Brandon