In case you haven’t heard as of yet, there is a new critical VMware vCenter Server critical patch advisory to be aware of that will require patching your vCenter Server. I have gone through the steps to patch vCenter Server so I can show you guys the effort and steps involved to get your VCSA appliance patched for the vulnerabilities. Let’s first look at the VMware vCenter Server critical patch VMSA-2024-0012 and what CVEs it contains and then the steps to apply the needed patch.
Table of contents
CVE-2024-37079, CVE-2024-37080, CVE-2024-37081
Let’s look at the CVEs contained in this VMware security advisory. These include:
- CVE-2024-37079 & CVE-2024-37080 – Multiple heap overflow vulnerabilities with the DCERPC protocol. The severity of this vulnerability has the maximum CVSSv3 base score of 9.8. An attacker with only network access to the vCenter Server may trigger this vulnerability with a special network packet that could lead to remote code execution.
- CVE-2024-37081 – This vulnerability is the local privilege escalation vulnerability due to the misconfiguration of sudo. The maximum CVSSv3 base score for this vulnerability is 7.8.
Here are the affected versions of vCenter Server and VMware Cloud Foundation found in the official documentation for the vulnerabilities here: Support Content Notification – Support Portal – Broadcom support portal.
| VMware Product | Version | Running On | CVE | CVSSv3 | Severity | Fixed Version | Workarounds | Additional Documentation |
| vCenter Server | 8.0 | Any | CVE-2024-37079, CVE-2024-37080, CVE-2024-37081 | 9.8, 9.8, 7.8 | Critical | 8.0 U2d | None | FAQ |
| vCenter Server | 8.0 | Any | CVE-2024-37079, CVE-2024-37080 | 9.8, 9.8 | Critical | 8.0 U1e | None | FAQ |
| vCenter Server | 7.0 | Any | CVE-2024-37079, CVE-2024-37080, CVE-2024-37081 | 9.8, 9.8, 7.8 | Critical | 7.0 U3r | None | FAQ |
Impacted Product Suites that Deploy Response Matrix 3a and 3b Components:
| VMware Product | Version | Running On | CVE | CVSSv3 | Severity | Fixed Version | Workarounds | Additional Documentation |
| Cloud Foundation (vCenter Server) | 5.x | Any | CVE-2024-37079, CVE-2024-37080, CVE-2024-37081 | 9.8, 9.8, 7.8 | Critical | KB88287 | None | FAQ |
| Cloud Foundation (vCenter Server) | 4.x | Any | CVE-2024-37079, CVE-2024-37080, CVE-2024-37081 | 9.8, 9.8, 7.8 | Critical | KB88287 | None | FAQ |
Before upgrading vCenter Server
Before you upgrade vCenter Server, there are a few things to keep in mind and other things you will want to pause or quiesce, such as:
- Backup solutions that are pointed to your vCenter Server. Let these finish their current backups and then pause them.
- Monitoring solutions can either be paused or realize you will get some extra noise once services are restarted on vCenter Server.
- Take a snapshot of the vCenter Server appliance virtual machine.
VMSA-2024-0012 Patch Steps
Let’s look at the following VMSA-2024-0012 patch steps for patching vCenter Server against this vulnerability.
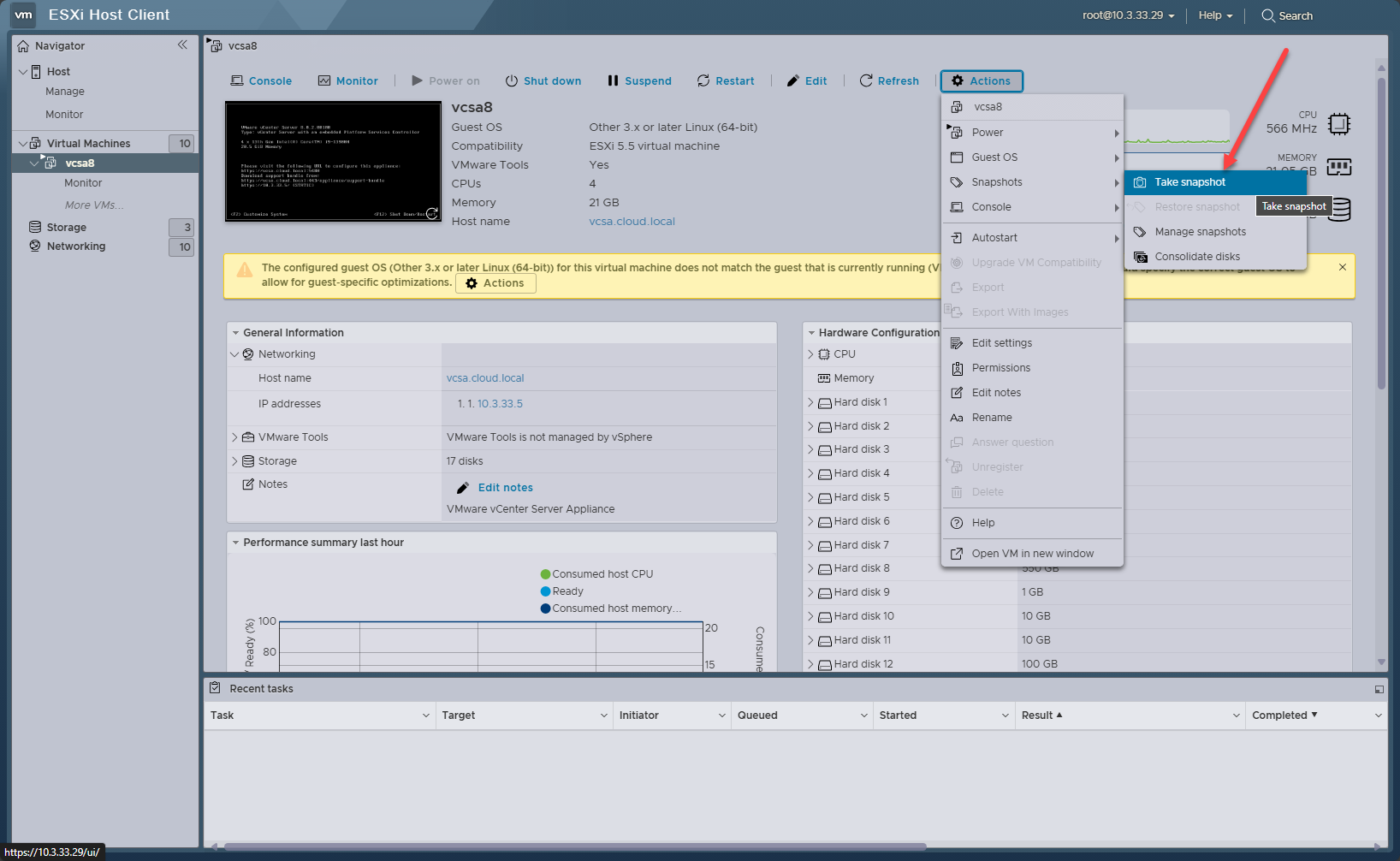
First, log into the host that “owns” the vCenter virtual appliance and take a snapshot of the VCSA virtual machine.
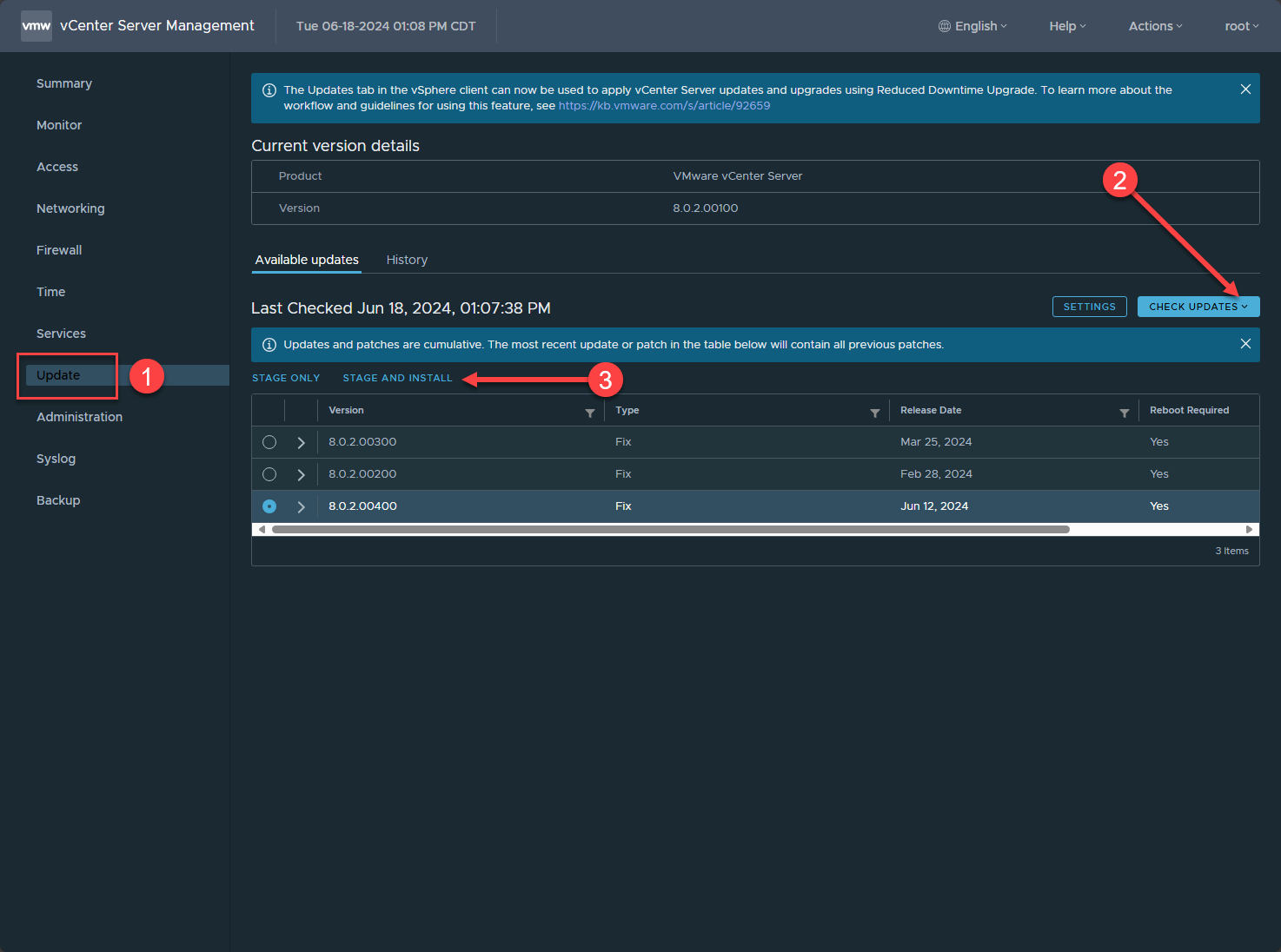
Now, log into the VAMI interface which is found at port 5480. Once logged in, navigate in the vCenter appliance to Update and then click the Check Updates button. Choose CDROM + URL. It will retrieve the available patches for your vCenter Server appliance. Once you choose the latest update for this VMSA, which is dated June 12, 2024 for vCenter Server 8.x. Click the Stage and Install button.
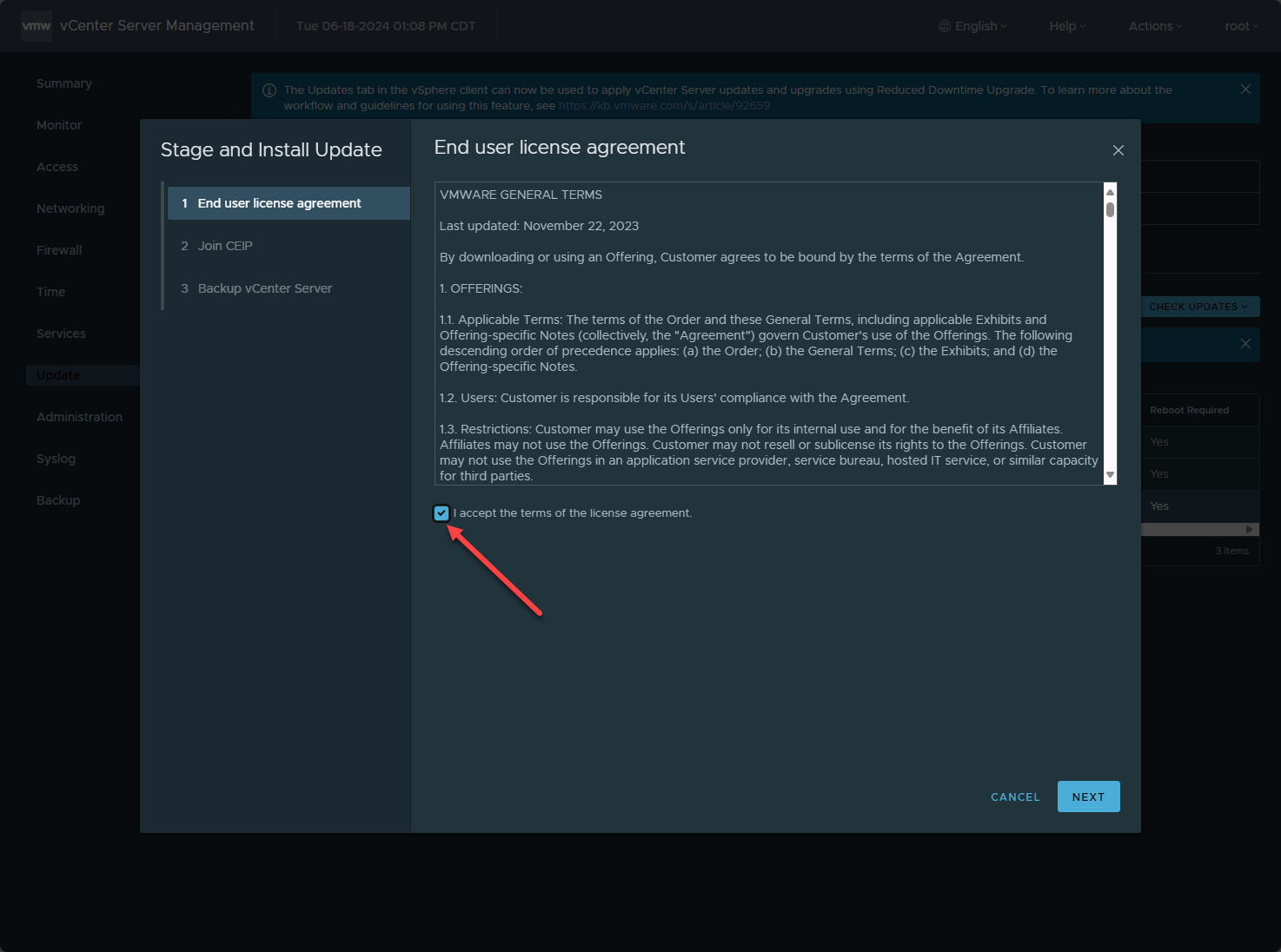
This will launch the end user license agreement. Place a check in the I accept the terms of the license agreement checkbox and click Next.
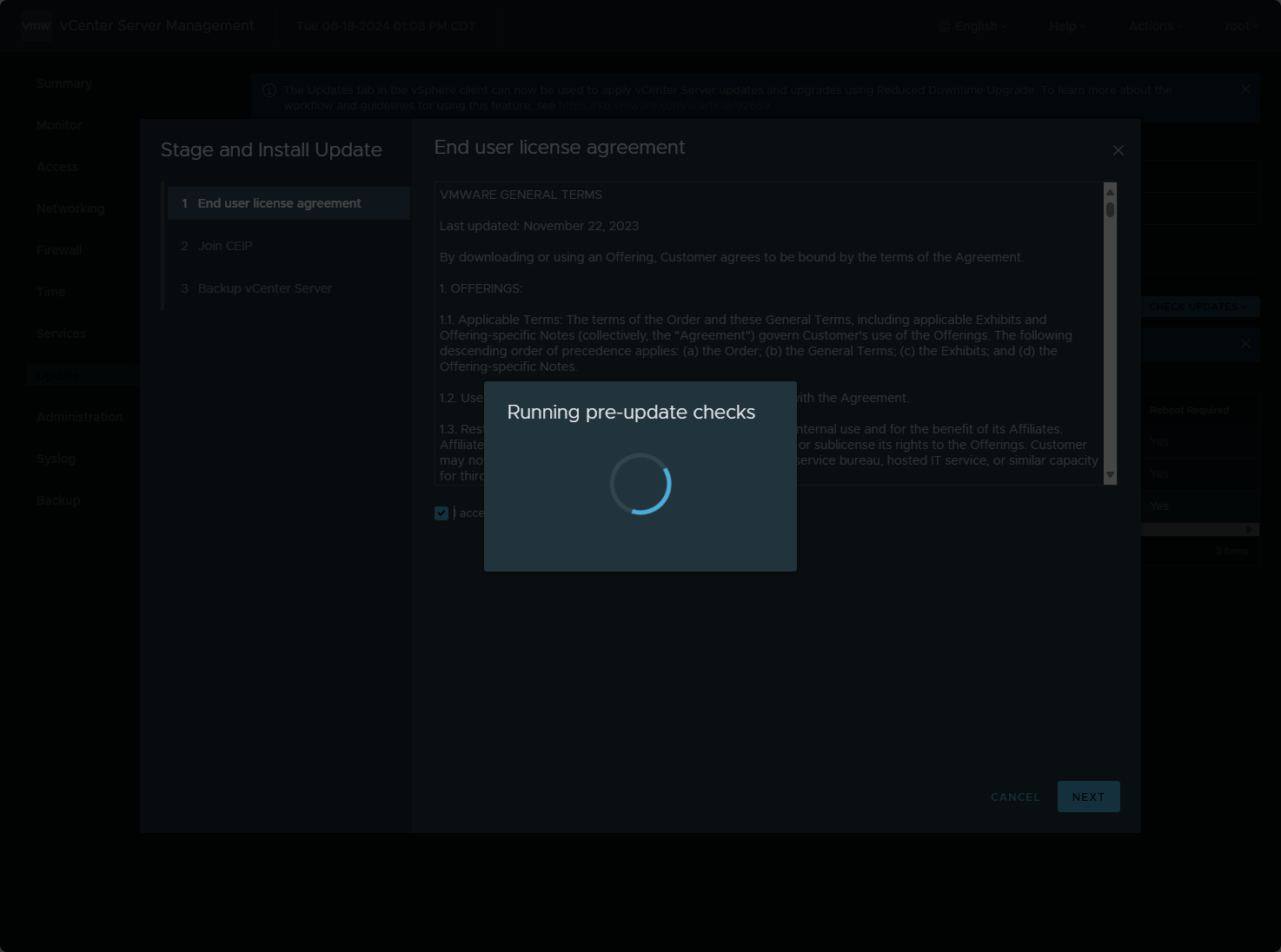
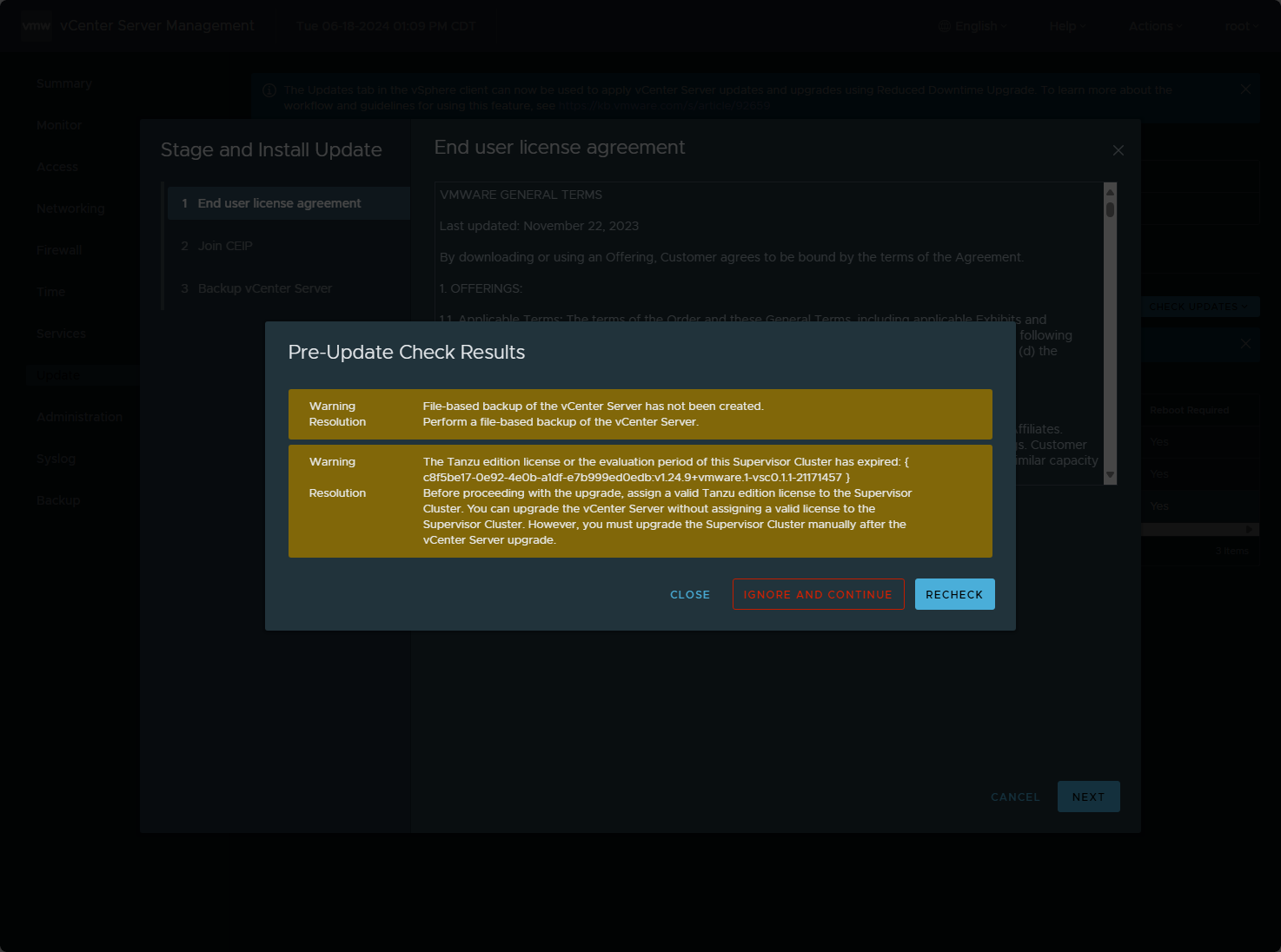
The update process will run prechecks on the vCenter Server appliance.
Make a note of the vCenter Server pre-update check results. Here I have a couple of warnings but nothing to prevent the installation of the patch. Press Ignore and Continue to move forward.
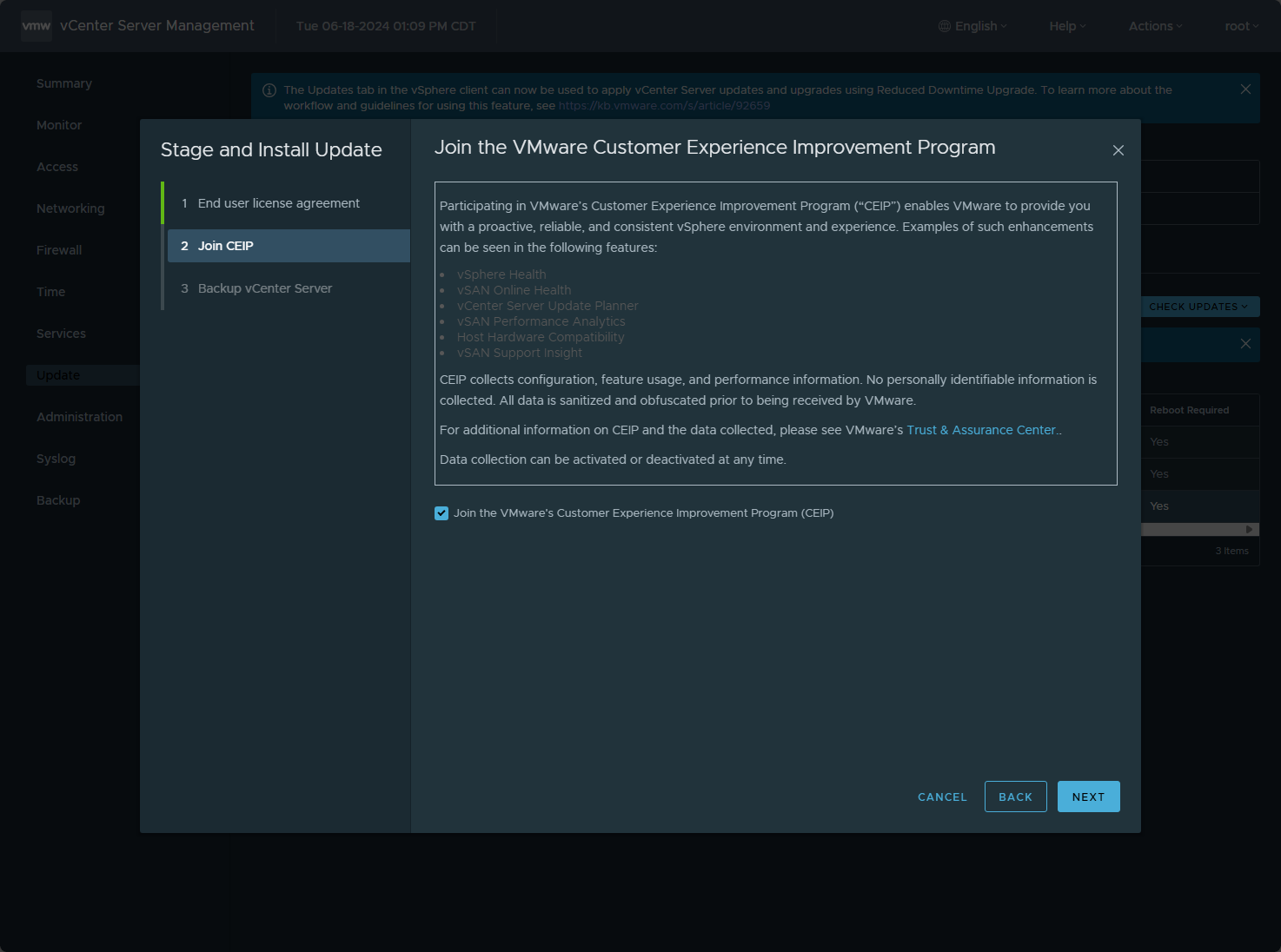
You can choose whether or not you want to join the customer experience improvement program. Make your selection and click Next.
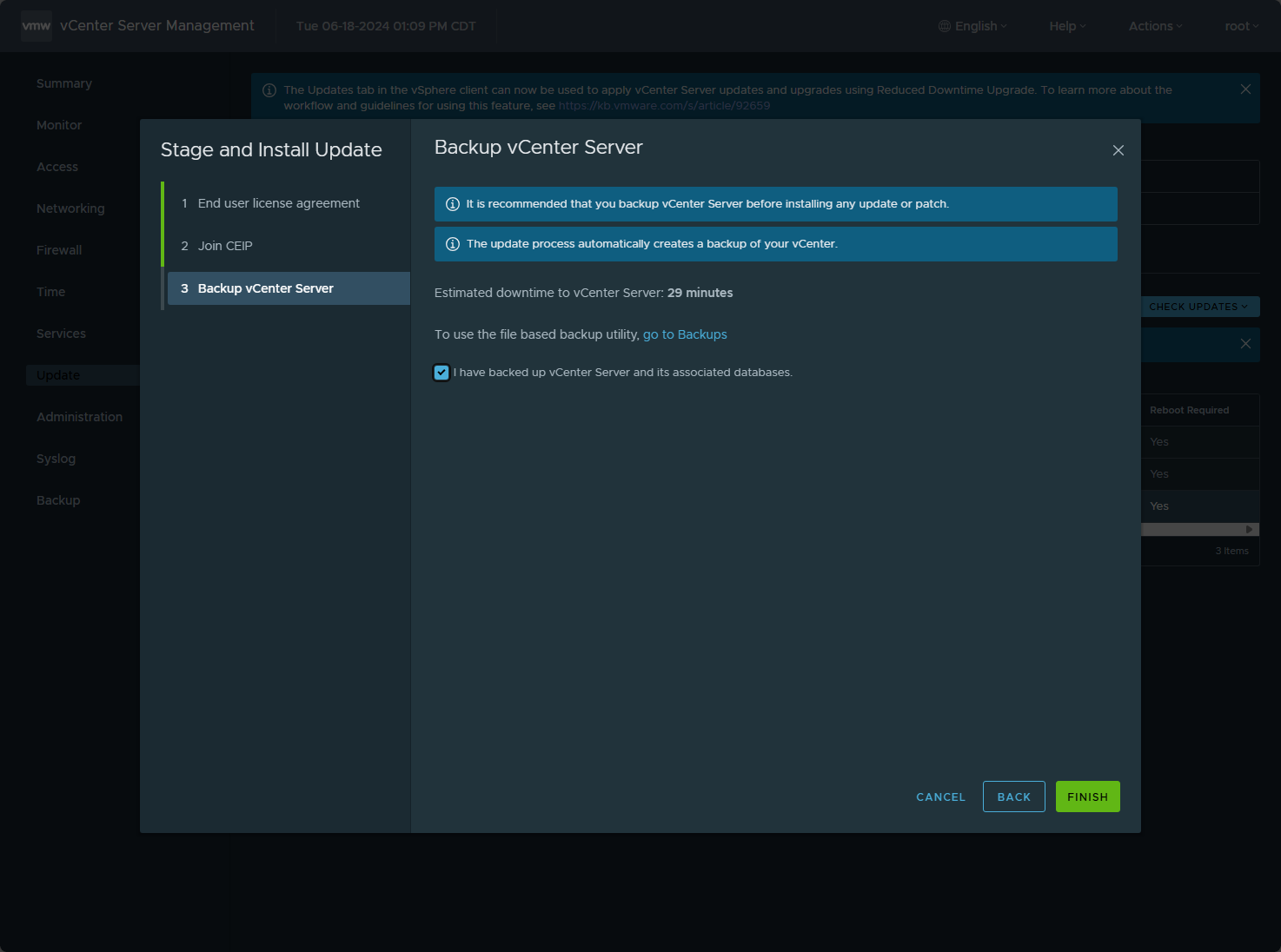
You will get prompted to back up vCenter Server. It will look for file-level backups to be running. However, since we have taken a snapshot, I clicked Finish.
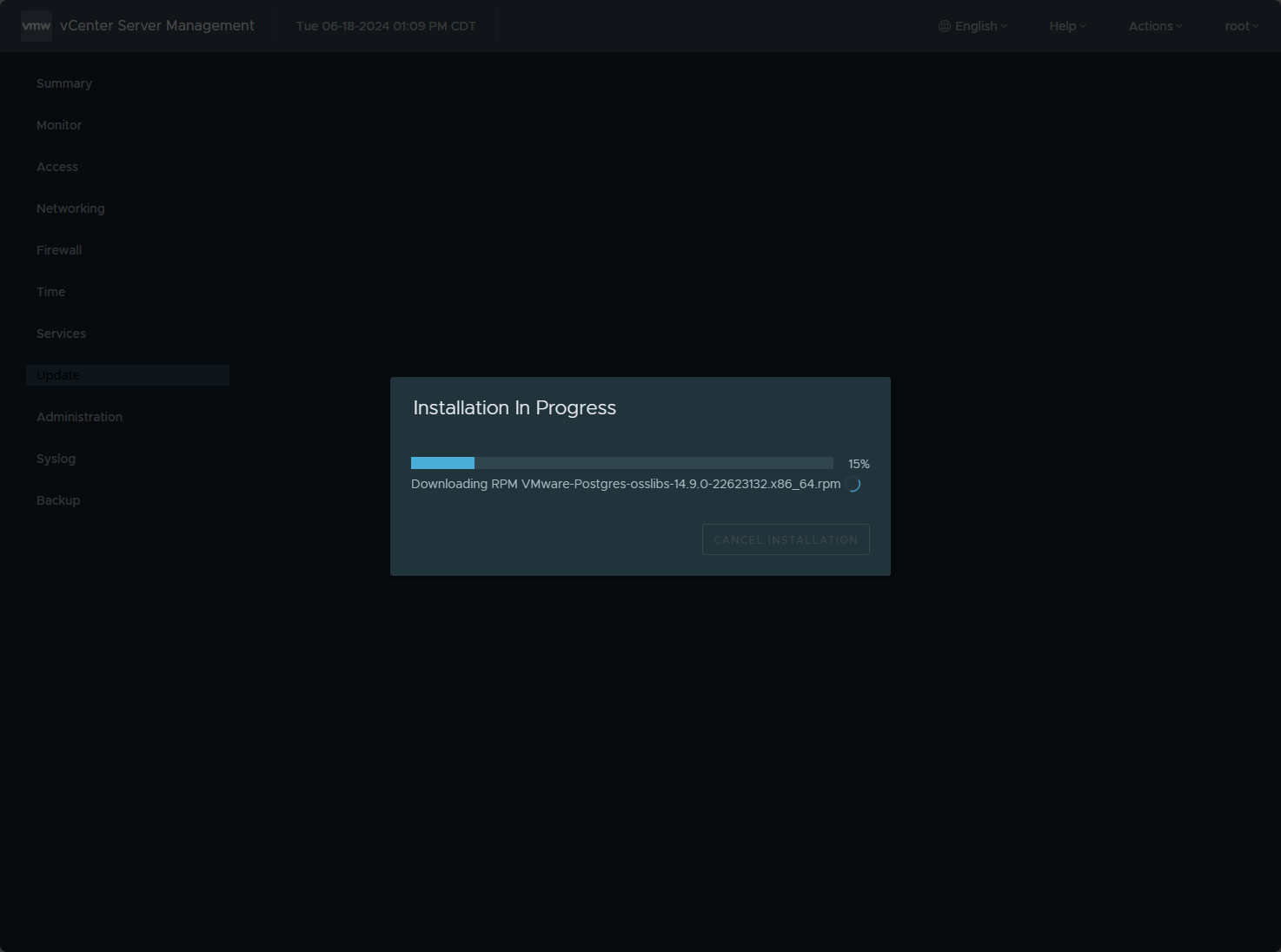
The update process begins.
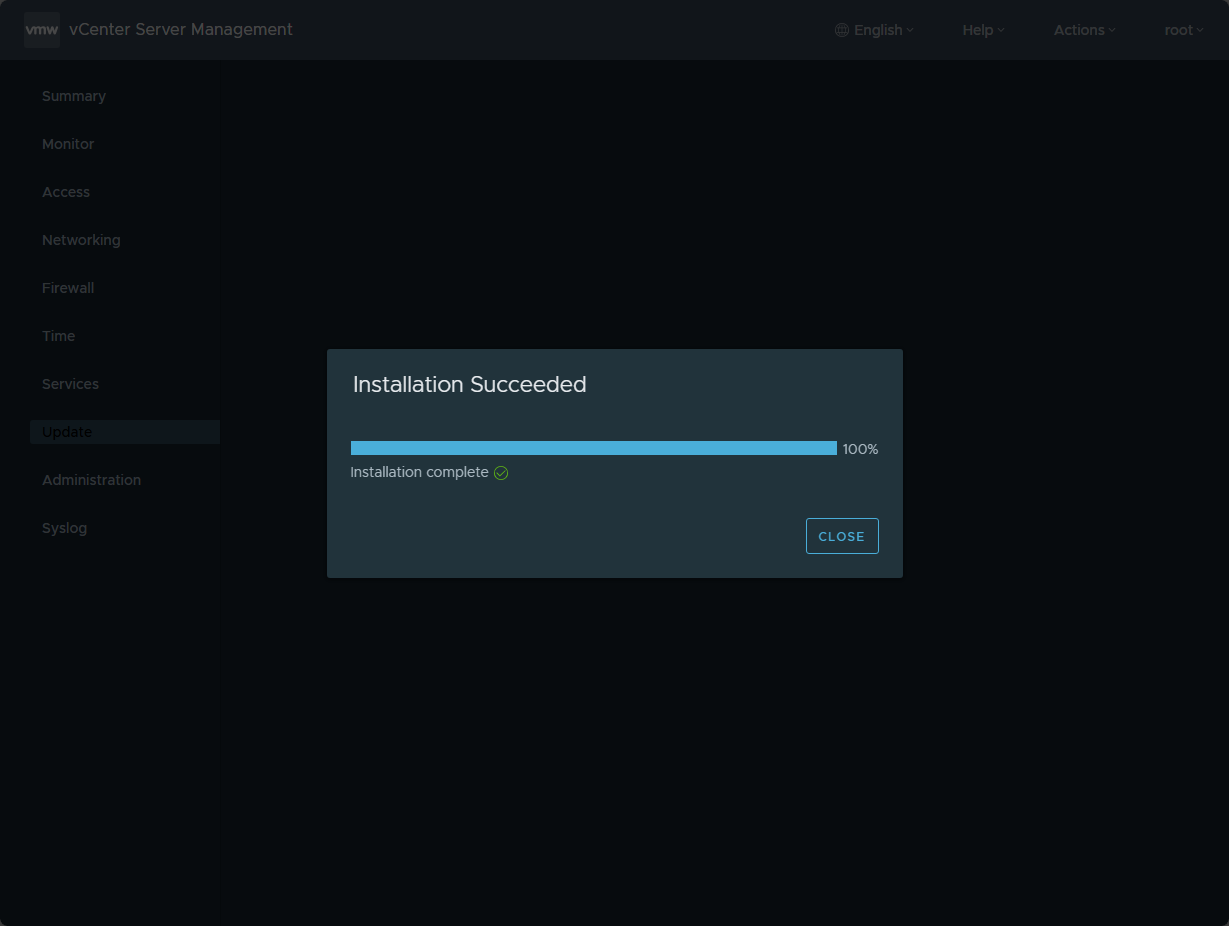
After several minutes the installation of the vCenter Server patch completes successfully.
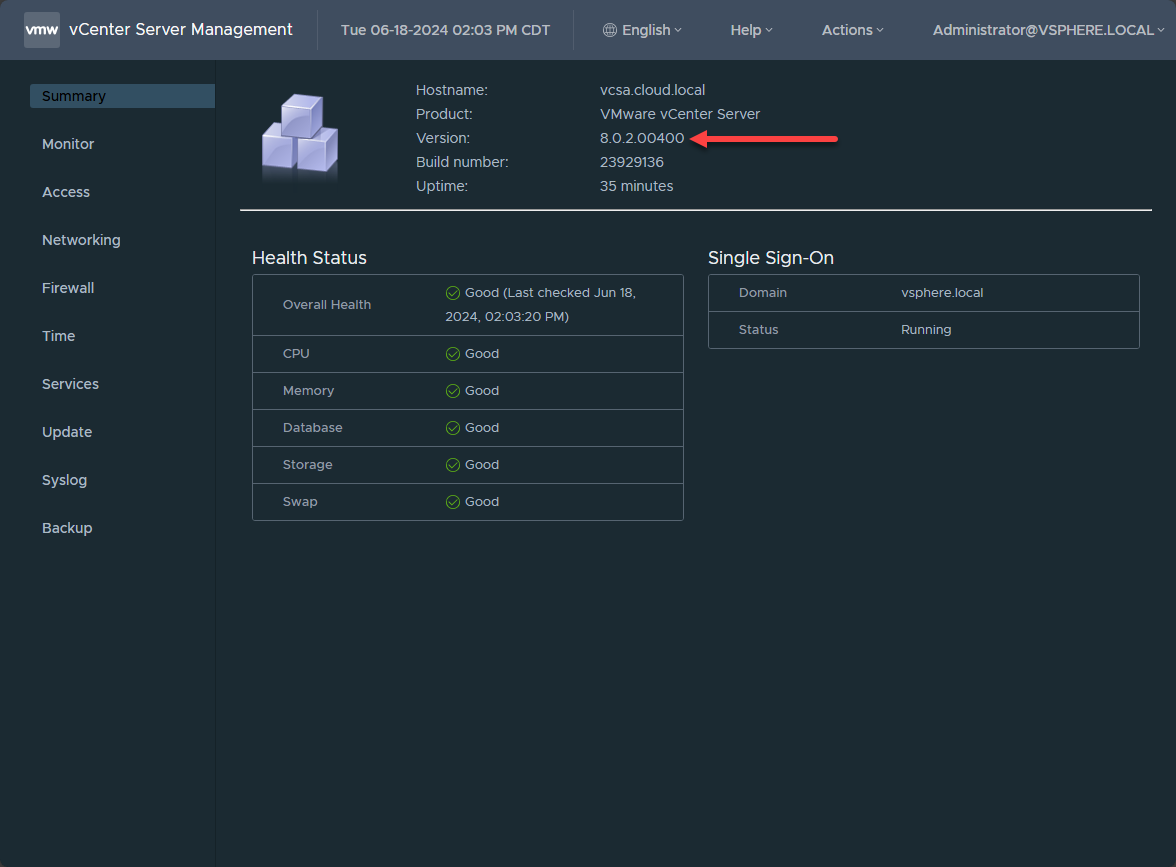
In the Summary screen after logging back into the VAMI interface, we can see the current version of the vCenter Server appliance to verify the installation incremented the version.
Next steps
There are a few next steps once we have vCenter Server upgraded. My recommendation here is to leave the snapshot on for a while to verify things in your environment are still working as expected. Also, do the following:
- Reenable your backups
- Reenable monitoring solutions
- After a day or so and everything looks ok, delete the snapshot on your vCenter Server appliance
Wrapping up
The new VMware vCenter Server VMSA-2024-0012 critical patch is one that you want to get installed as soon as possible due to the severity of the vulnerability. As outlined, the process to patch vCenter isn’t too difficult using some common sense and having a snapshot on your vCenter Server appliance. Keep the other solutions in mind that tie in with vCenter Server to make sure these are properly paused or you understand the fallout once vCenter Server services are restarted.
Google is updating how articles are shown. Don’t miss our leading home lab and tech content, written by humans, by setting Virtualization Howto as a preferred source.



I upgraded my two vCenter Servers at 6:30am this morning.
Jeff,
Definitely a bad vulnerability with this one. I think VMware vSphere environments are now the target for many of the ransomware gangs. Definitely something to stay on top of for sure!
Brandon
Hello, I would recommend before taking the snapshot to shutdown the vCenter. As far as I am aware, online snapshots of vCenter are not oficially supported by the vendor. While this will
work most of the time, an offline snapshot provides a better revert point.
rotechhype,
Thank you for the comment and great point. Snapshots with memory on vCenter could probably cause weird issues. It would definitely be a good idea to not snap memory on your VCSA.
Brandon
Hi, thanks for this vcenter patch update post,
if you have made same like this post for esxi patch update, kindly share the link to [email protected]