Windows Server 2025 New SMB File Services Features

Windows Server 2025 has many new features that we have covered already. However, one area where it will excel is in SMB file services. Microsoft is doubling down on security with Windows Server 2025 in the area of SMB and you will see lots of new features in that area to help admins combat some of the common types of SMB attacks.
Table of contents
Focus on security
Before Windows Server 2025, compatibility and performance were the priorities. Traditionally, security was the last priority in Windows. However, security is now the focus of most of the new features related to SMB. Note the following key security advancements:
- SMB Auth Rate Limiter
- Default SMB Signing
- NTLM Deprecation
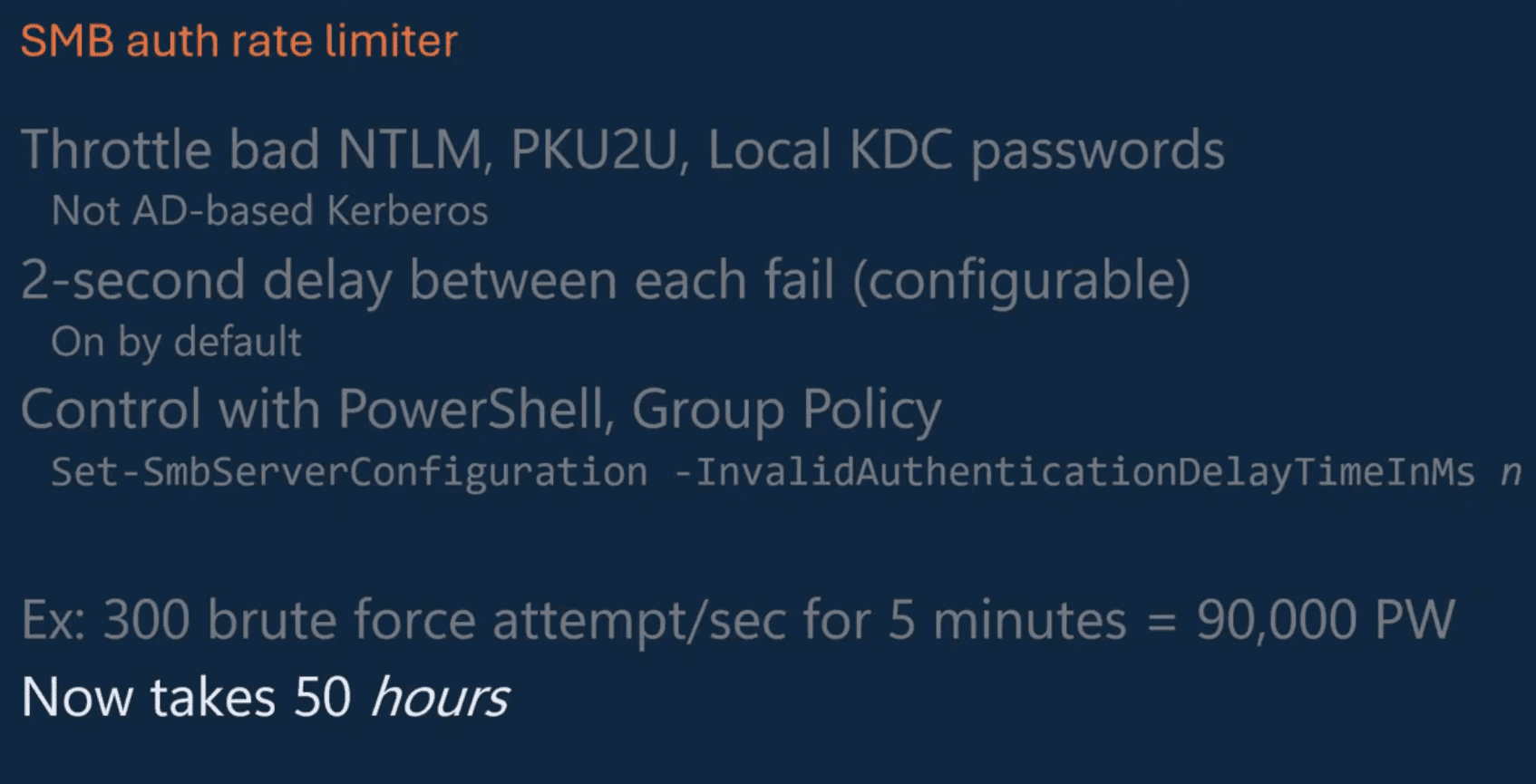
SMB Auth Rate Limiter
This feature introduces a mechanism to throttle bad login attempts, significantly mitigating the risk of brute force attacks. With the new delay between failed authentication attempts, the rate limiter extends the time required to perform such attacks, which increases security without user intervention.
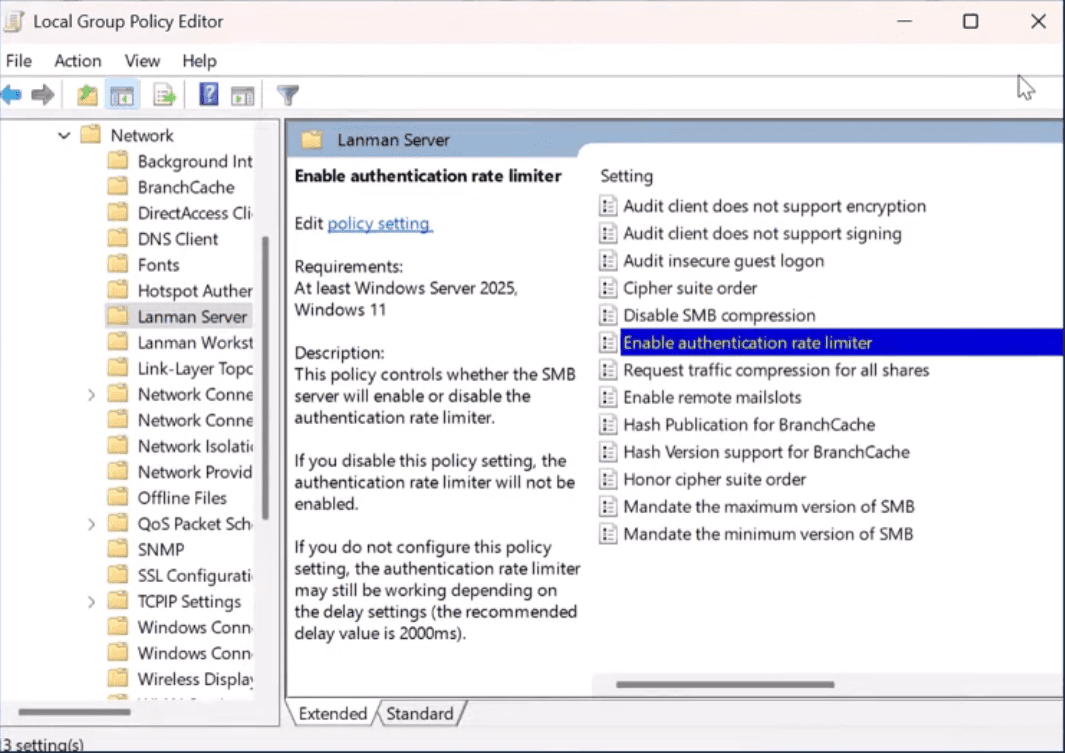
This will also be a group policy setting that can be configured:
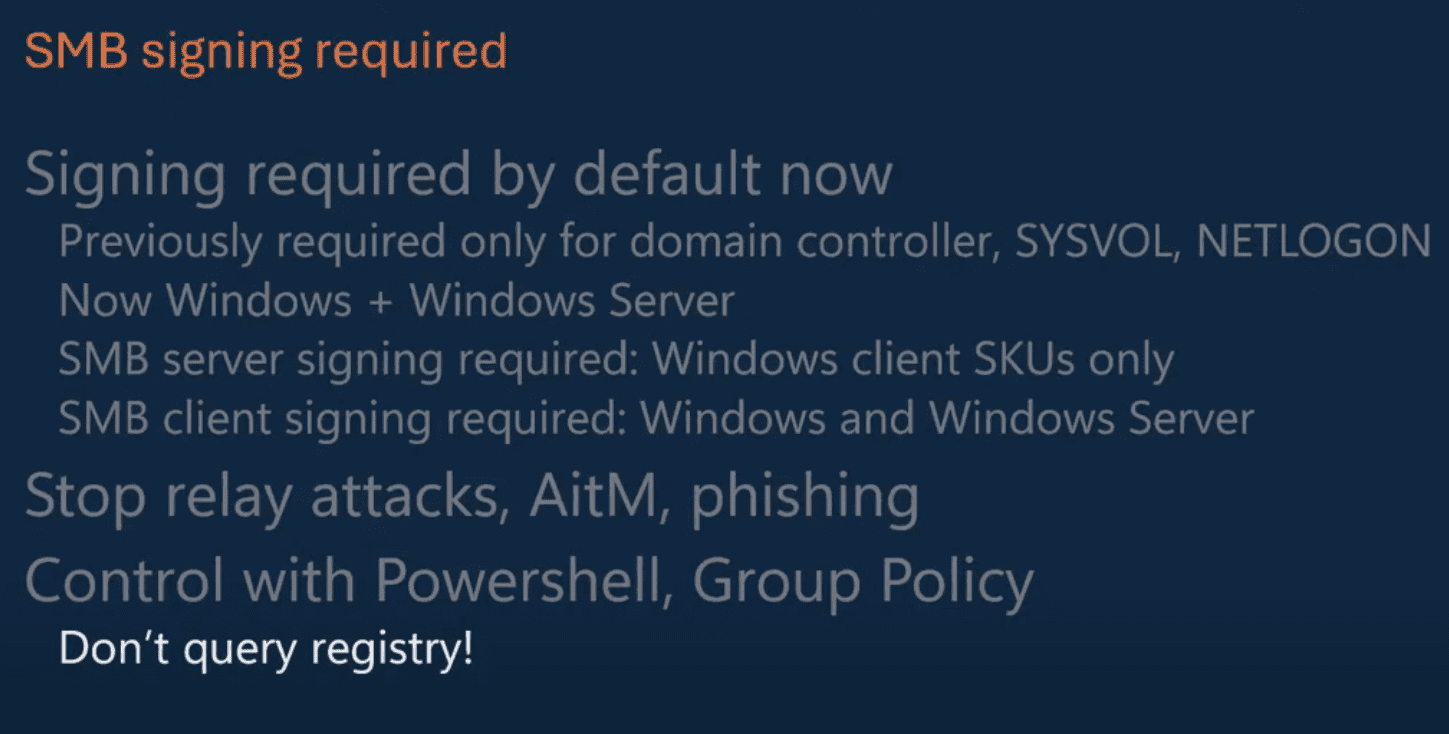
Default SMB Signing
This feature protects the integrity and confidentiality of data. SMB signing will now be enabled by default. This change will protect against relay and man-in-the-middle attacks. It will help make sure that data tampering and eavesdropping are much more difficult for attackers.
Previously, SMB signing was only for domain controller, SYSVOL, and NETLOGON traffic. Now, Windows traffic to Windows Server traffic will require Windows SMB signing.
- SMB server signing required: Windows client SKUs only
- SMB client signing required: Windows and Windows Server
- It can be controlled with PowerShell and Group Policy
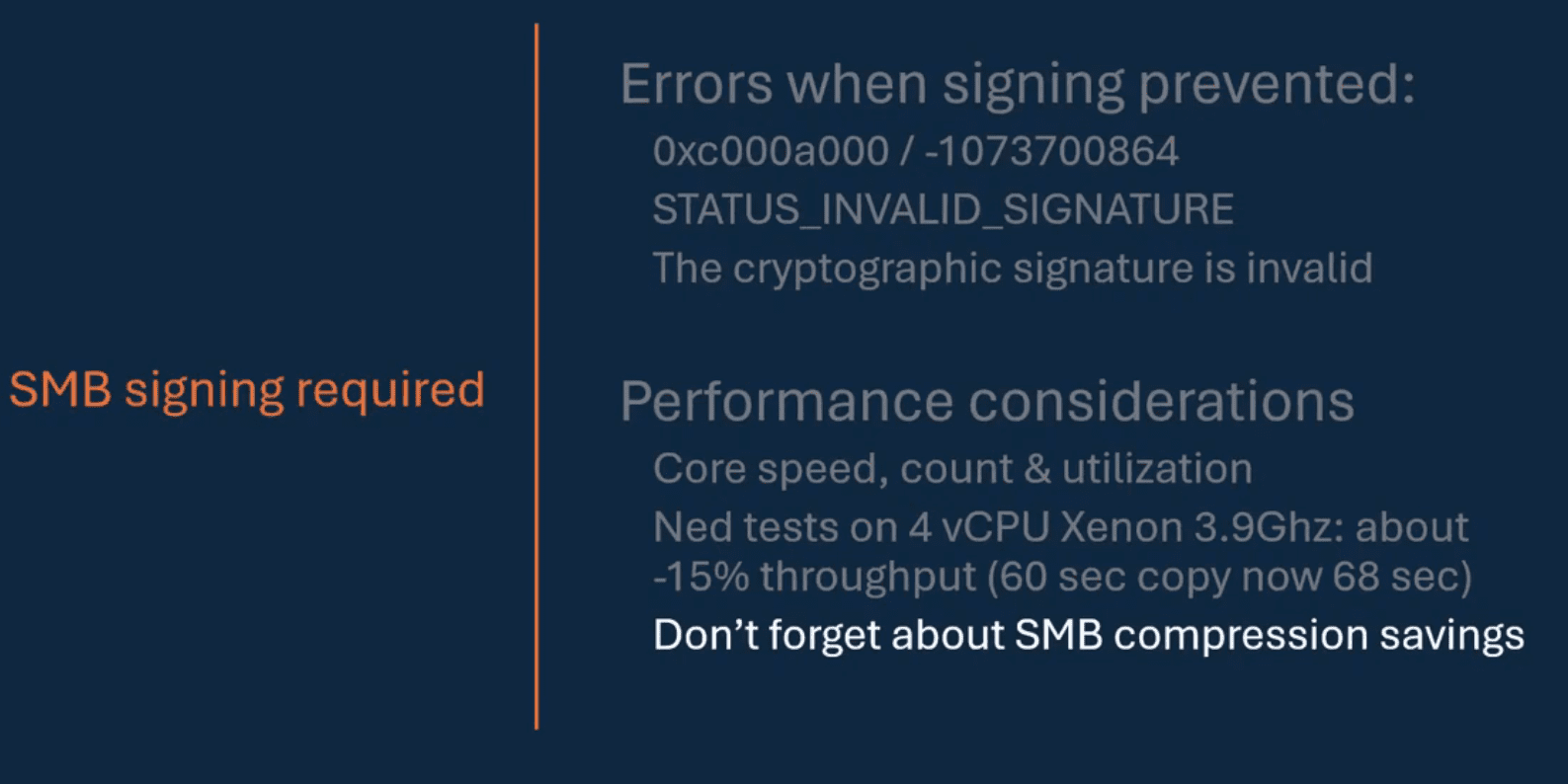
Below is are the effects of SMB signing that you will want to consider.
There are new SMB signing Audit events:
Microsoft-Windows-SmbClient/Audit
ID: 31998
Message:
The SMB client observed that the server doesn't support signing
Server name:
Client requires signing
Microsoft-Windows-SmbServer/Audit
ID: 3021
Message:
The SMB server observerd that the client doesn't support signing
Server name:
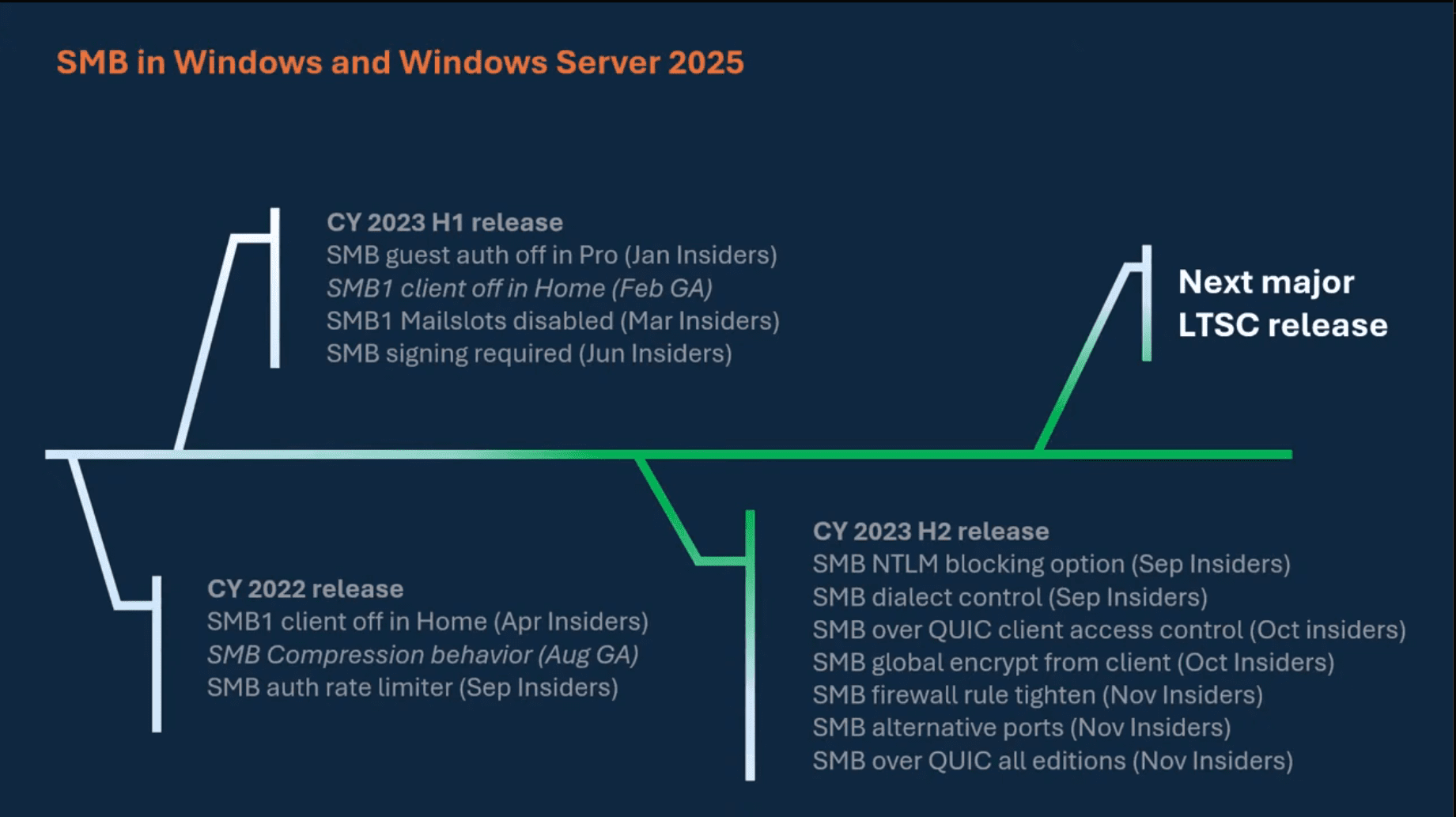
Client requires signing:Below are new features added and the timeline of addition for SMB in Windows and Windows Server 2025.
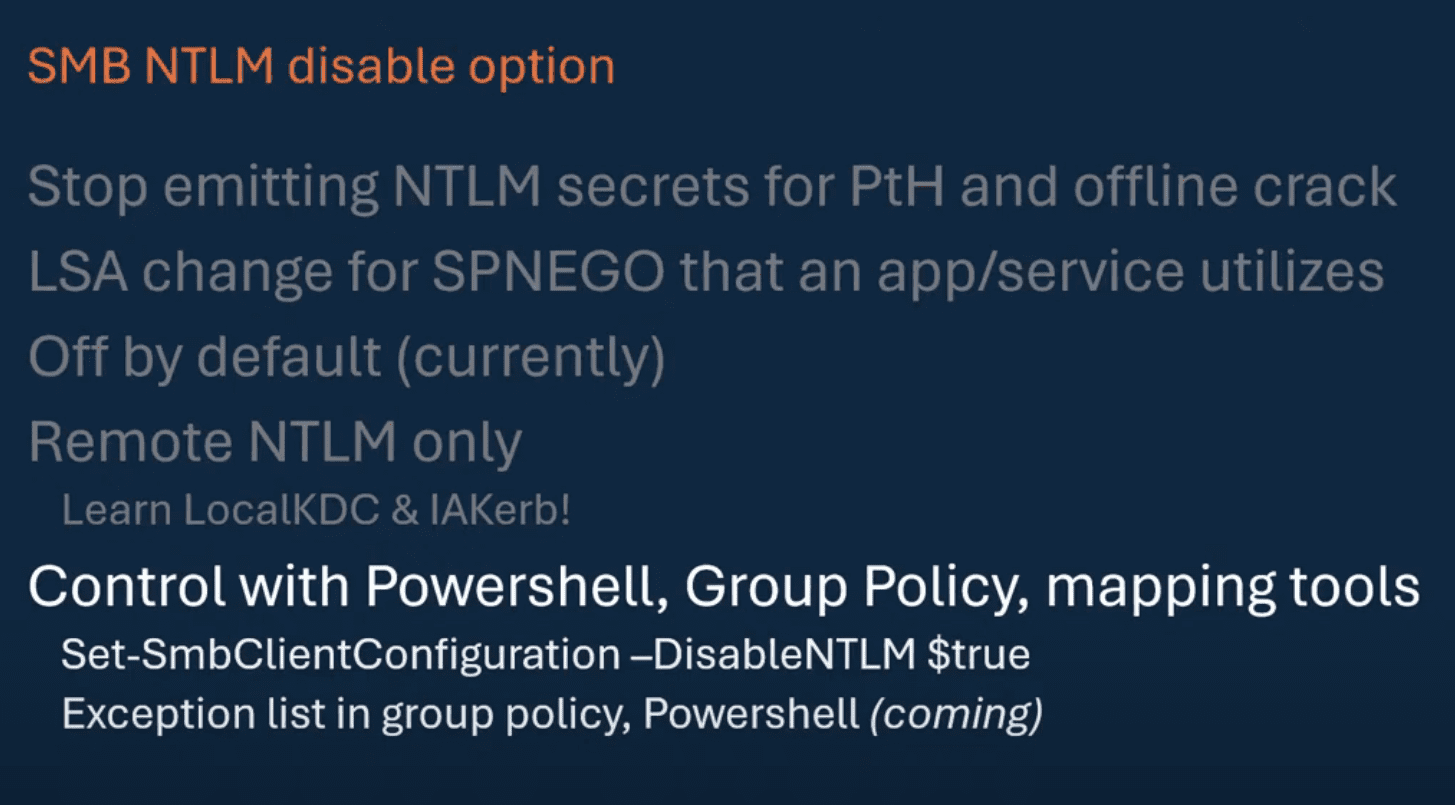
NTLM Deprecation
Windows Server 2025 moves away from NTLM in favor of more secure authentication methods. This is an important step in eliminating older, less secure authentication protocols.
As shown in the graphic above, this can be controlled with PowerShell, Group Policy, and mapping tools:
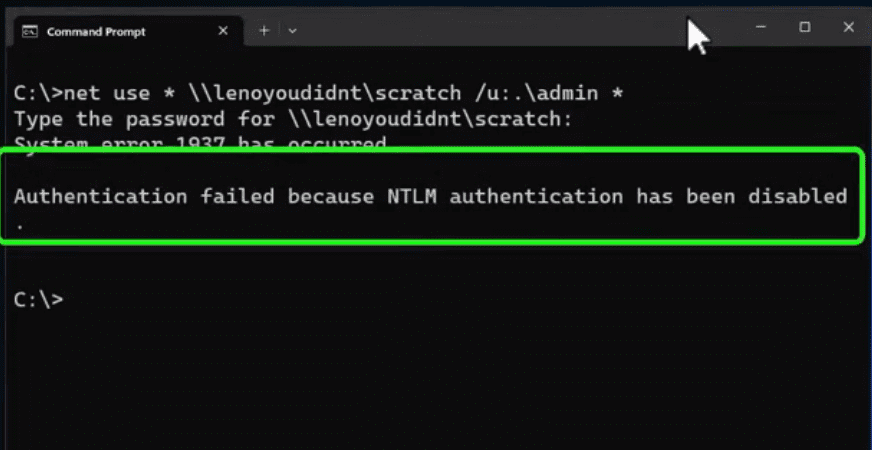
Set-SmbClientConfiguration DisableNTLM $trueWhat error do you get when you disable NTLM using the PowerShell cmdlet above?
More advancements
Aside from security, Windows Server 2025 introduces several functional improvements that enhance user experience and system efficiency:
- SMB Compression
- SMB Over QUIC
SMB Compression
Changes in SMB compression facilitate more efficient data transfers, especially over congested or narrow networks. This improvement is not just about faster data handling but also about optimizing network performance in diverse environments.
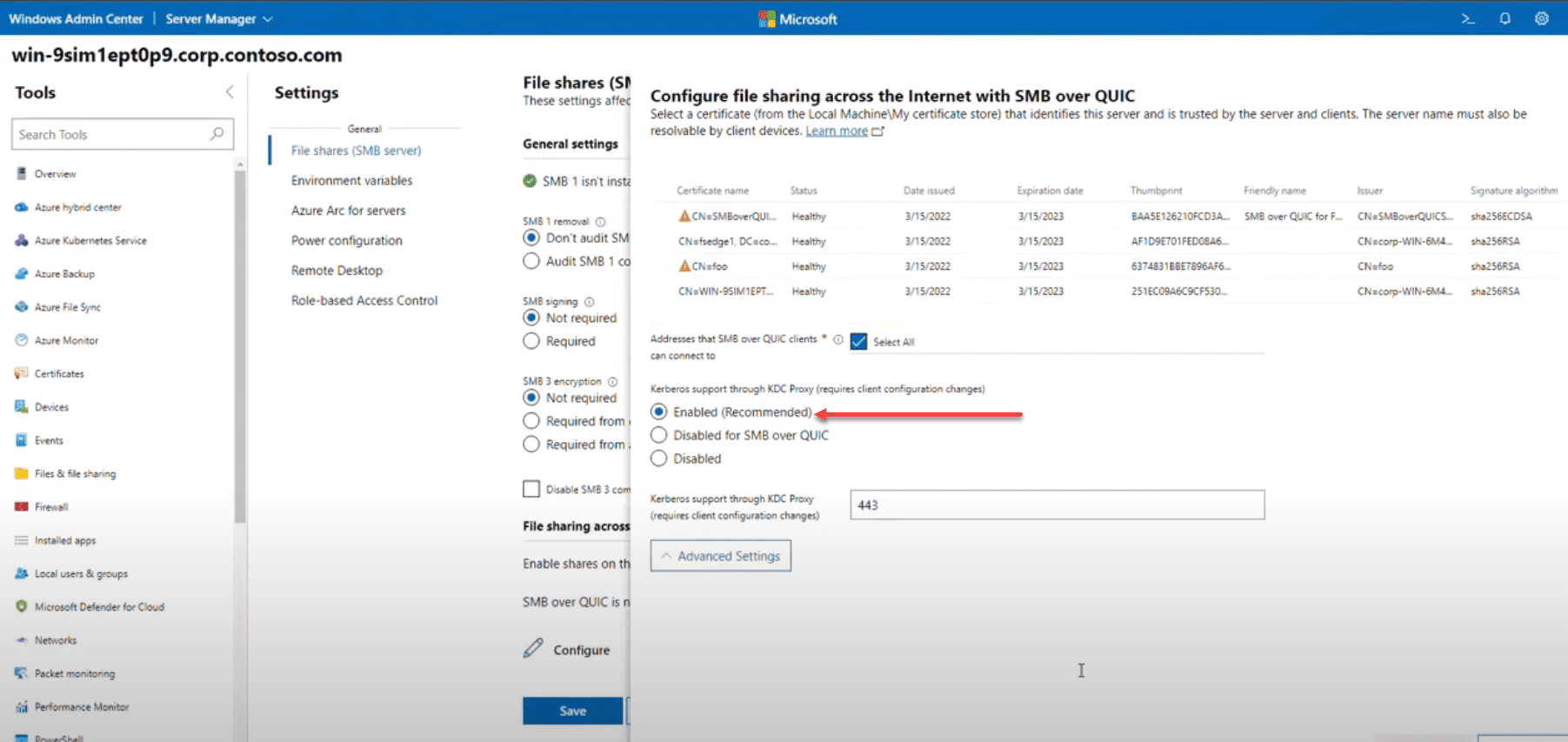
SMB over QUIC
This protocol, replacing TCP, ensures that SMB traffic is more secure and reliable over the internet. QUIC is inherently encrypted and does not require a VPN, making it ideal for remote access and cloud interactions.
Note the following benefits:
- Secure and reliable transport built on UDP
- Encryption is always required
- Handshake is authenticated using TLS 1.3
- Does not require VPN
- Runs over 443 by default
- SMB for telecommuters, mobile devices, cloud, high security
- Mutual auth through certificate exchange
- Allow and block specific client access
- ACL based on client certificate + chain
- Certificates identified by SHA256 hash or issuer name
- Access granted if no deny entry + allow entry
- Very granular control with operational overhead
Easier management and configuration
Windows Server 2025 simplifies the management of SMB features through enhanced group policies and PowerShell commands. This makes it easier for administrators to configure and focus on security:
- Group Policy and PowerShell Enhancements: New settings and configurations can be managed more easily through these tools. For example, administrators can adjust the SMB auth rate limiter and manage SMB signing via group policies or PowerShell scripts.
- Improved Diagnostic and Management Tools: New features will provide administrators with more tools for diagnosing and managing the behavior across the network.
Future changes
As SMB continues to evolve, Windows Server 2025 introduces forward-looking changes that anticipate future network needs and security challenges:
- Global SMB Settings: These settings will allow for more granular control over SMB traffic, ensuring that security and efficiency are maximized across all network interactions.
- Client Access Control over SMB: With enhanced client access controls, administrators can specify which clients can access the network, providing an additional layer of security and management.
Windows Server 2025 has a much stronger emphasis on security, improved functionality, and easier management. These enhancements help to meet the security challenges of modern network environments.