Proxmox Networking for VMware vSphere admins

One of the challenges that we run into when we are more familiar with one vendor over another is the difference in the technologies, how they work for customers, what they are called, and how to configure them. On the networking side of things, this can be the case as well. If you are familiar with VMware vSphere and looking to work with and play around with Proxmox, Proxmox networking may be foreign to work with when trying to compare it with VMware ESXi networking, etc. In this Proxmox networking for vSphere admins post for the community, we will look at the equivalent networking configurations in Proxmox compared to vSphere.
Table of contents
1. Proxmox Linux Bridge equivalent to the VMware vSwitch
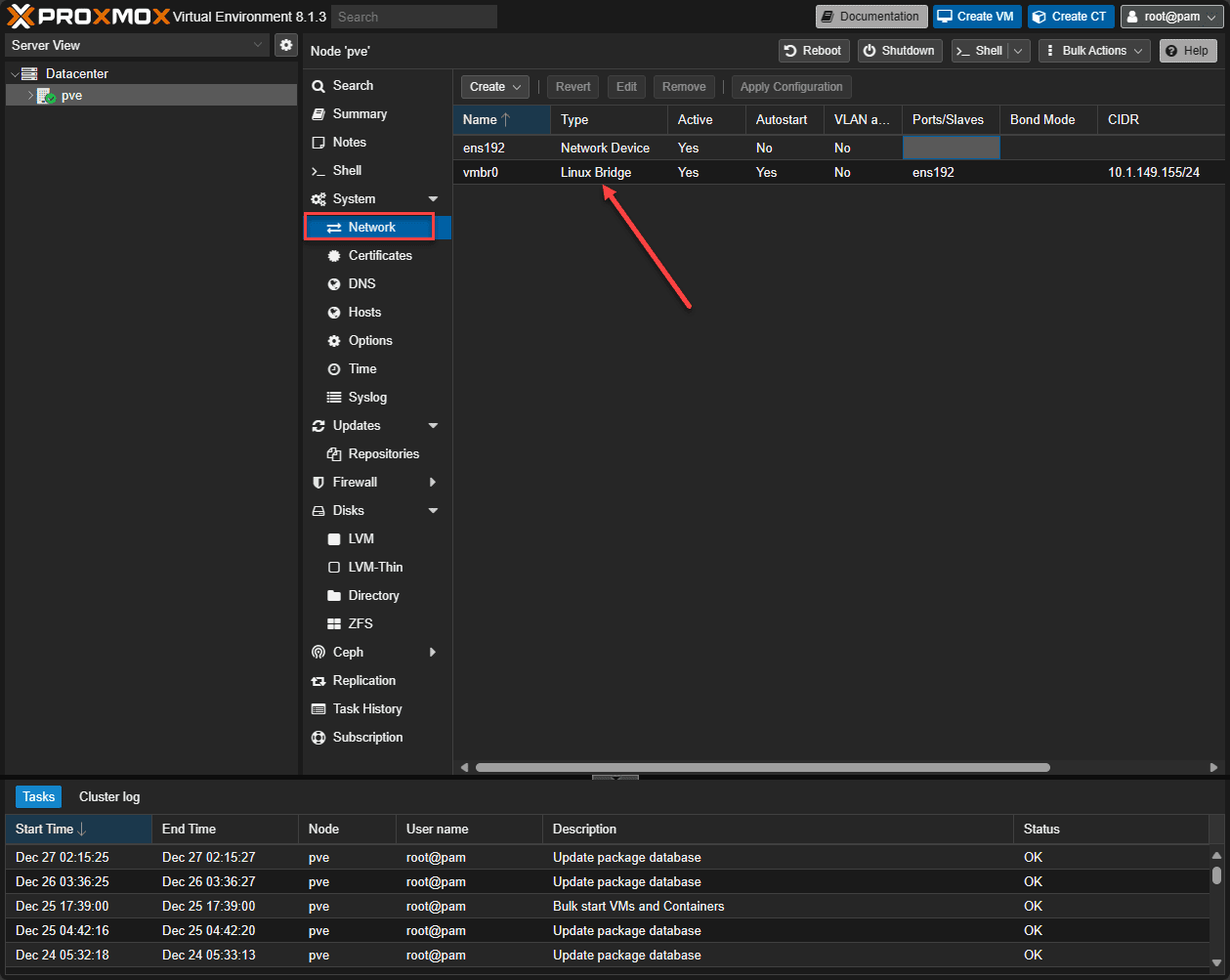
The most equivalent network construct out of the box with Proxmox is the default Proxmox Linux bridge in the Proxmox environment. With the Linux Bridge in Proxmox, you establish the initial connectivity to your Proxmox host with a management IP address. Also, the default Linux Bridge is backed by a physical network adapter(s).
Below:
- Ports/Slaves – This shows the physical network adapter ens192 assigned to the default Linux bridge
- CIDR – Shows the IP address and mask associated with the Linux bridge
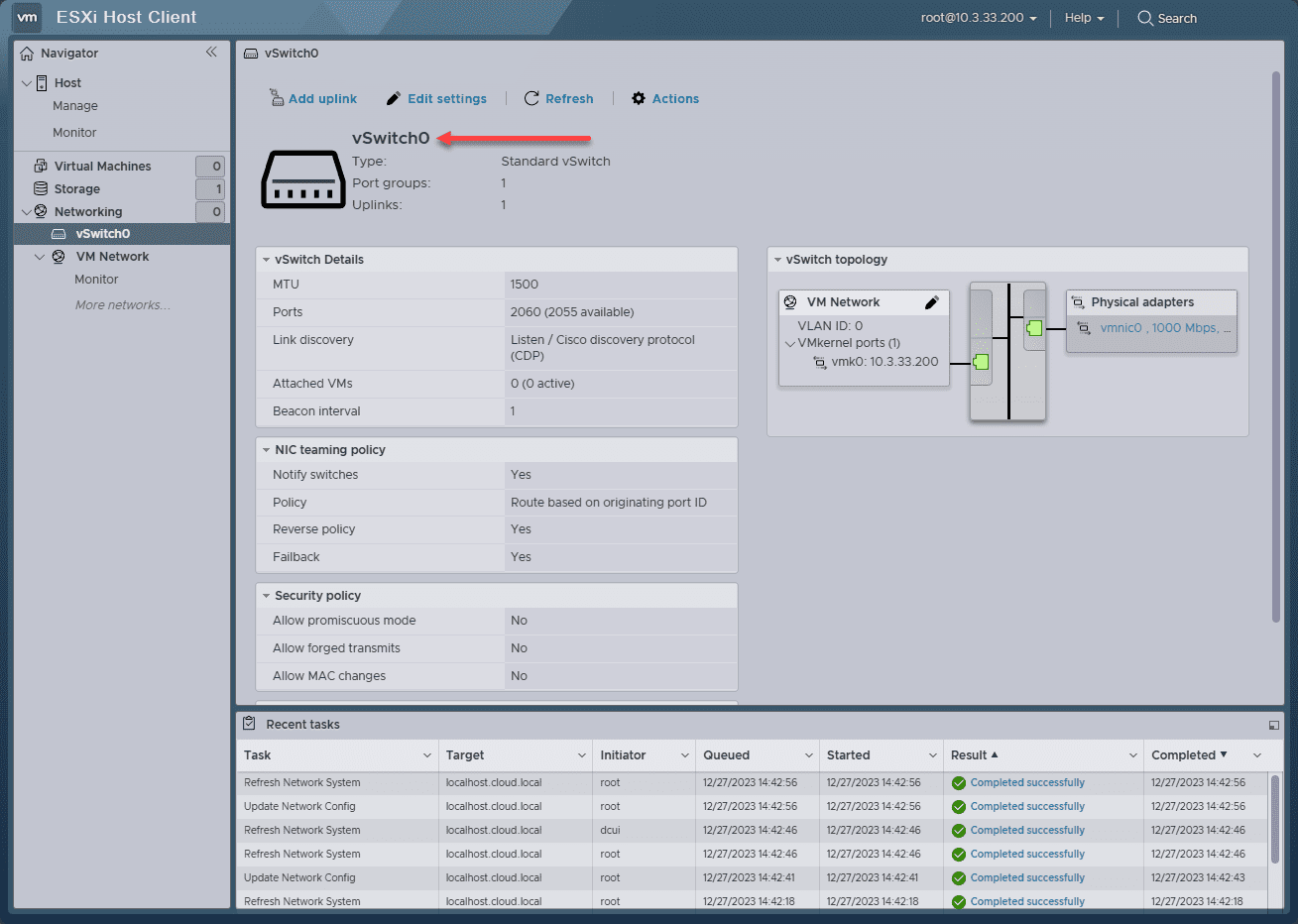
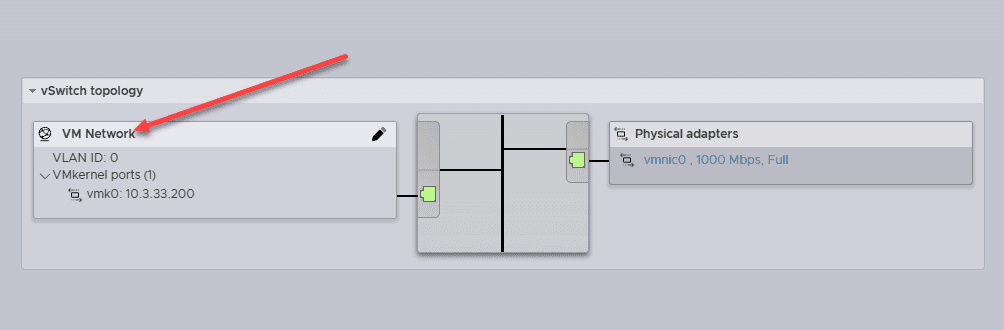
This is very similar to the default vSwitch0 created in VMware ESXi right out of an install. As you can see below, we have a physical network adapter backing vSwitch0.
2. Proxmox Linux VLANs equivalent to VMware vSwitch Port Groups
As most vSphere admins are aware, you have the vSwitch0 and the default VM Network port group as shown above. Port groups in vSphere allow you to create VLAN-tagged network labels in vSphere to assign VLAN tags to the virtual machines connected to them.
In Proxmox networking with the default Linux Bridge, the port group construct carries over to what is known as a Linux VLAN. By default, when you create a VM in Proxmox without any other configuration, you can attach the VM to the default vmbr0 bridge, which is essentially VLAN 0 and assumes untagged traffic.
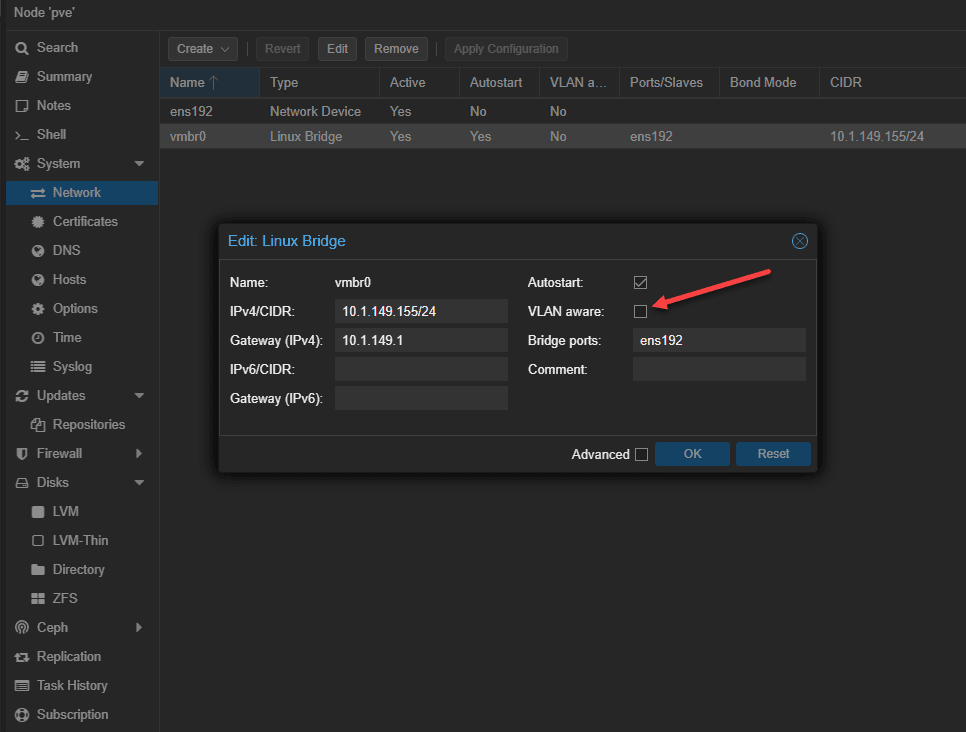
Unlike the VMware default vSwitch0 and VM Network port group, the default Proxmox Linux Bridge is not VLAN-aware out of the box. You have to enable this.
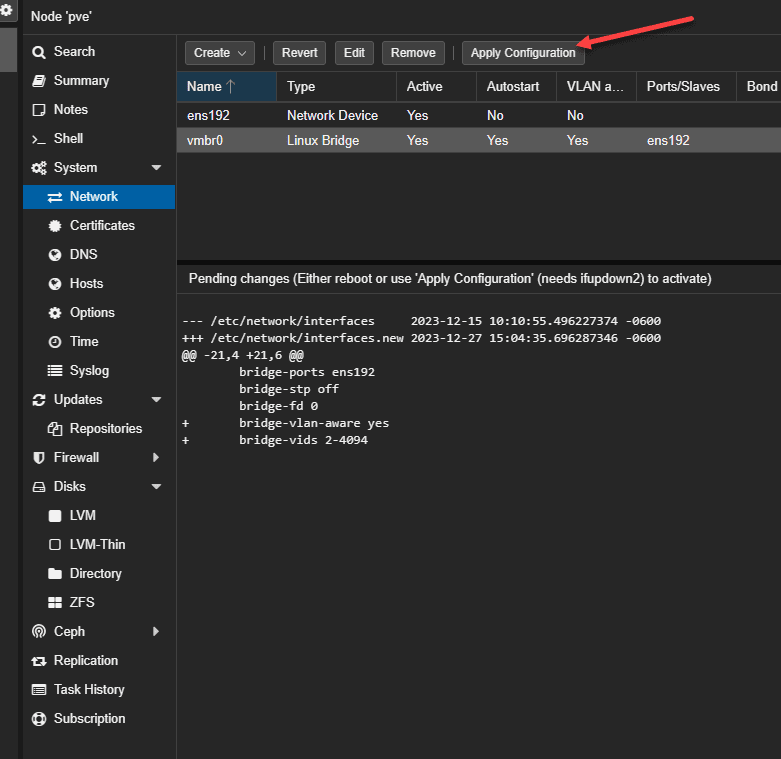
When you edit the default Linux Bridge, you will see the checkbox VLAN aware available on the Linux Bridge properties. Also, you will see basic networking configurations like the IP address and subnet, gateway for routing, etc. Place a check box in the VLAN aware checkbox.
Now we can apply the configuration. Click the Apply Configuration button. Also, in the preview of the Pending changes, you will see the new VLAN bridge-ports configuration set to auto, containing the configuration lines:
bridge-ports ens192
bridge-stp off
bridge-vlan-aware yes
bridge-vids 2-4094This configuration essentially makes the default Linux Bridge able to understand VLANs and VLAN traffic, so we can add Linux VLANs.
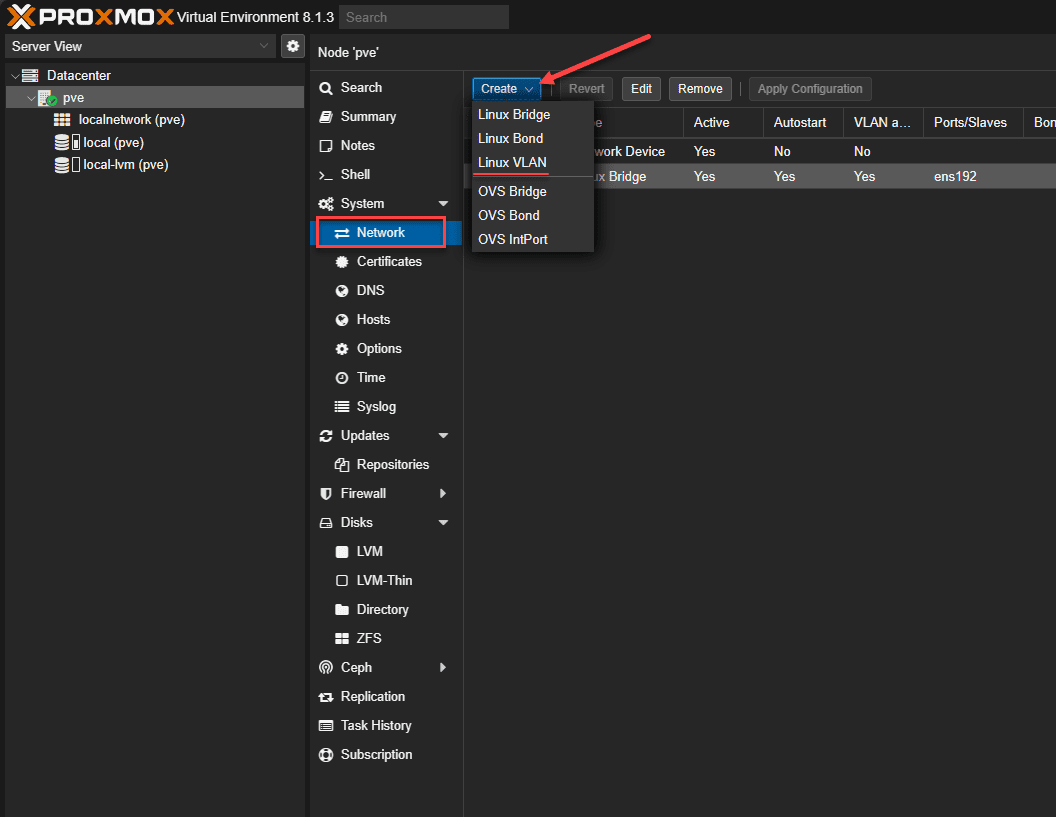
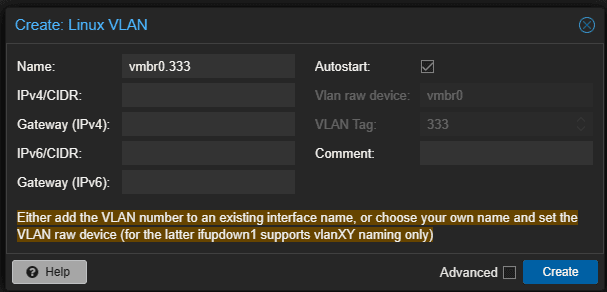
Now we can populate the new Linux VLAN with the appropriate configuration. Once you name the VLAN with the parent vmbr0 interface, you will see the VLAN raw device and VLAN Tag greyed out. This essentially says we are creating a new Linux VLAN on the parent Linux Bridge interface, vmbr0.
Under the Advanced checkbox, you can set the MTU value in case you are wondering.
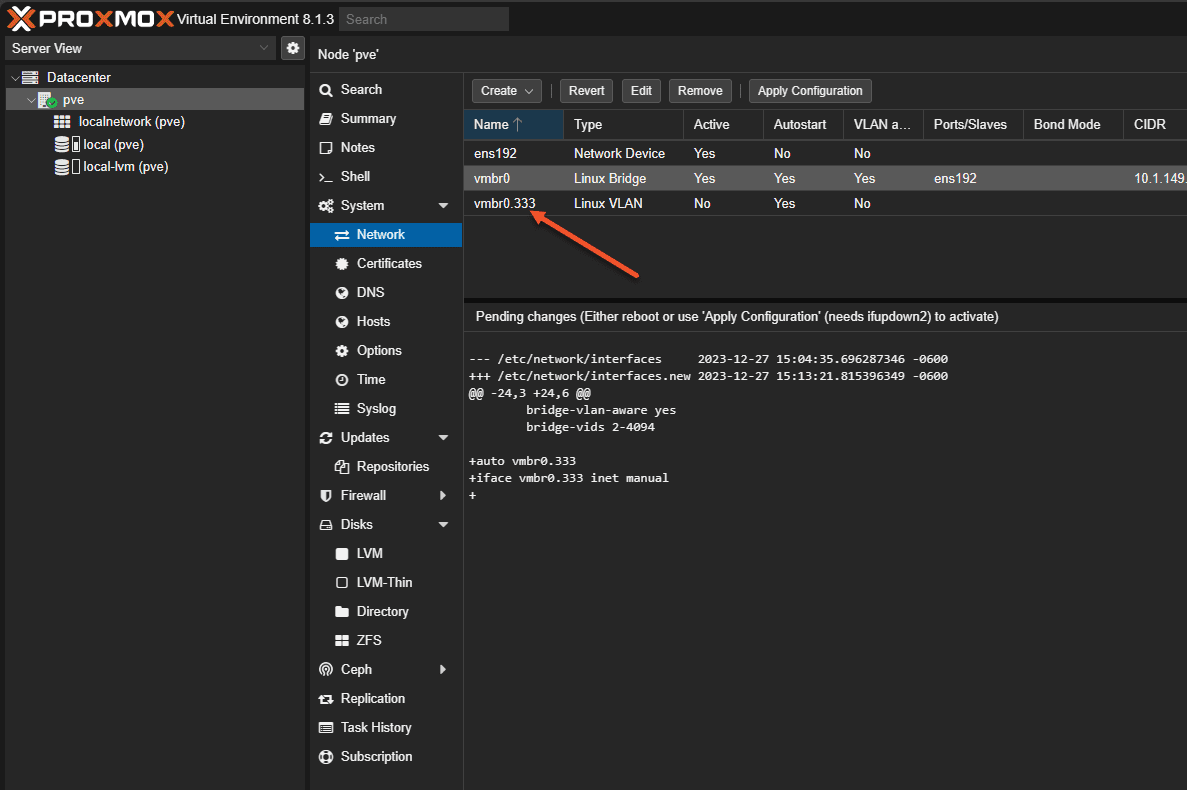
Now that we have created the child VLAN interface on the vmbr0 Linux bridge, you can see the vmbr0.333 interface listed now under the network configuration in the navigation tree of System > network.
3. Distributed Switches
In case you are wondering, Proxmox doesn’t have an equivalent construct like the vSphere Distributed Switch. The vSphere distributed switch is managed and controlled from vCenter Server. Proxmox doesn’t have a centralized management platform like vCenter Server.
Proxmox admins would need to manage complex network setups manually with scripting or use third-party tools available for Proxmox for centralized network management.
4. Network Adapters
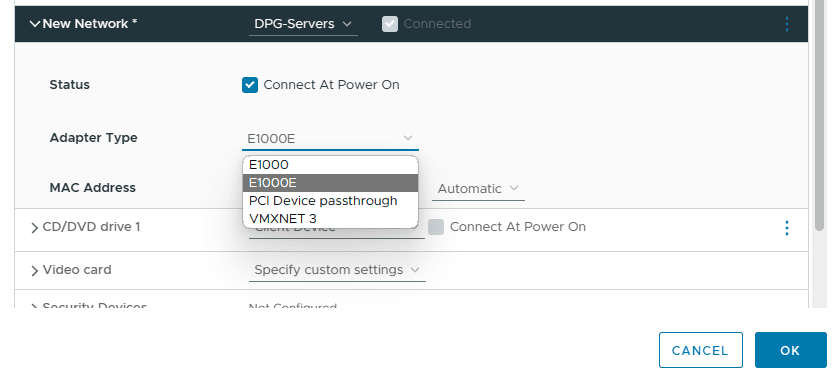
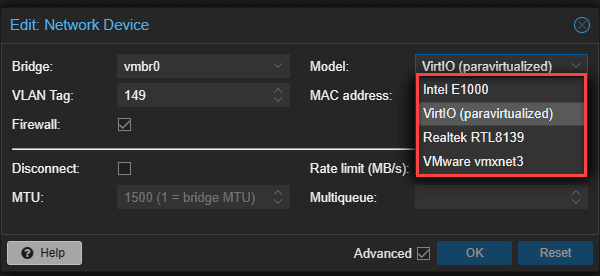
When it comes to network adapters for a virtual machine or container, both Proxmox and VMware vSphere support different types of network adapters. These include:
- VMXNET3
- E1000
- PCI Passthrough
- VirtIO (Proxmox)
Below you see the vnic options for a virtual machine.
Below are the options when creating a new virtual machine in Proxmox.
5. Network I/O Control
VMware has many tools for network traffic priority, bandwidth allocation, and other network capabilities. Proxmox does not contain network I/O control features built-in that are found in VMware vSphere. You can use Linux tools in Proxmox to help control network bandwidth.
With Proxmox, you can take advantage of one or many of the following Linux networking tools:
- Traffic Control (tc):
- tc is a tool in the Linux iproute2 package. It allows you to control the traffic going through your network interfaces. You can create rules for traffic shaping and prioritization. You can also use it for Quality of Service (QoS) rules.
- iptables:
- iptables can also be used for basic network traffic control. It allows packet filtering and can be combined with tc for more granular control.
- ethtool:
- ethtool is used for querying and controlling network driver and hardware settings. It can be used to adjust settings like speed, duplex, and autonegotiation on Ethernet interfaces, which can indirectly influence network performance.
- nftables:
- nftables can be used to set up basic traffic control mechanisms.
- Wondershaper:
- Wondershaper is a simpler tool designed to limit the bandwidth of specific network interfaces. It’s a good choice for basic bandwidth management.
- VLAN Configuration:
- Configuring VLANs like we discussed above, can help segment network traffic for more efficient network utilization. Linux’s native VLAN configuration tools can be used with Proxmox for this purpose.
- Network Namespaces:
- Linux network namespaces can be used to isolate network environments for different VMs or containers. This can help manage network traffic and ensure that different services don’t interfere with each other’s network resources.
- Monitoring Tools (like iftop, nload, bmon):
- While not directly involved in controlling traffic, monitoring tools are crucial for understanding network usage and identifying bottlenecks. Tools like iftop, nload, or bmon provide real-time network bandwidth usage information.
- Cgroups (Control Groups):
- Cgroups, a Linux kernel feature, can be used to limit and prioritize network bandwidth usage among different processes and VMs. While more commonly used for managing CPU and memory resources, cgroups can also be configured to control network I/O.
6. Software-defined networking (SDN)
VMware has a very well-known platform for software-defined networking, known as VMware NSX. The NSX platform is a paid solution on top of vSphere that allows admins to create logical software-defined overlay networks on top of the physical underlay network.
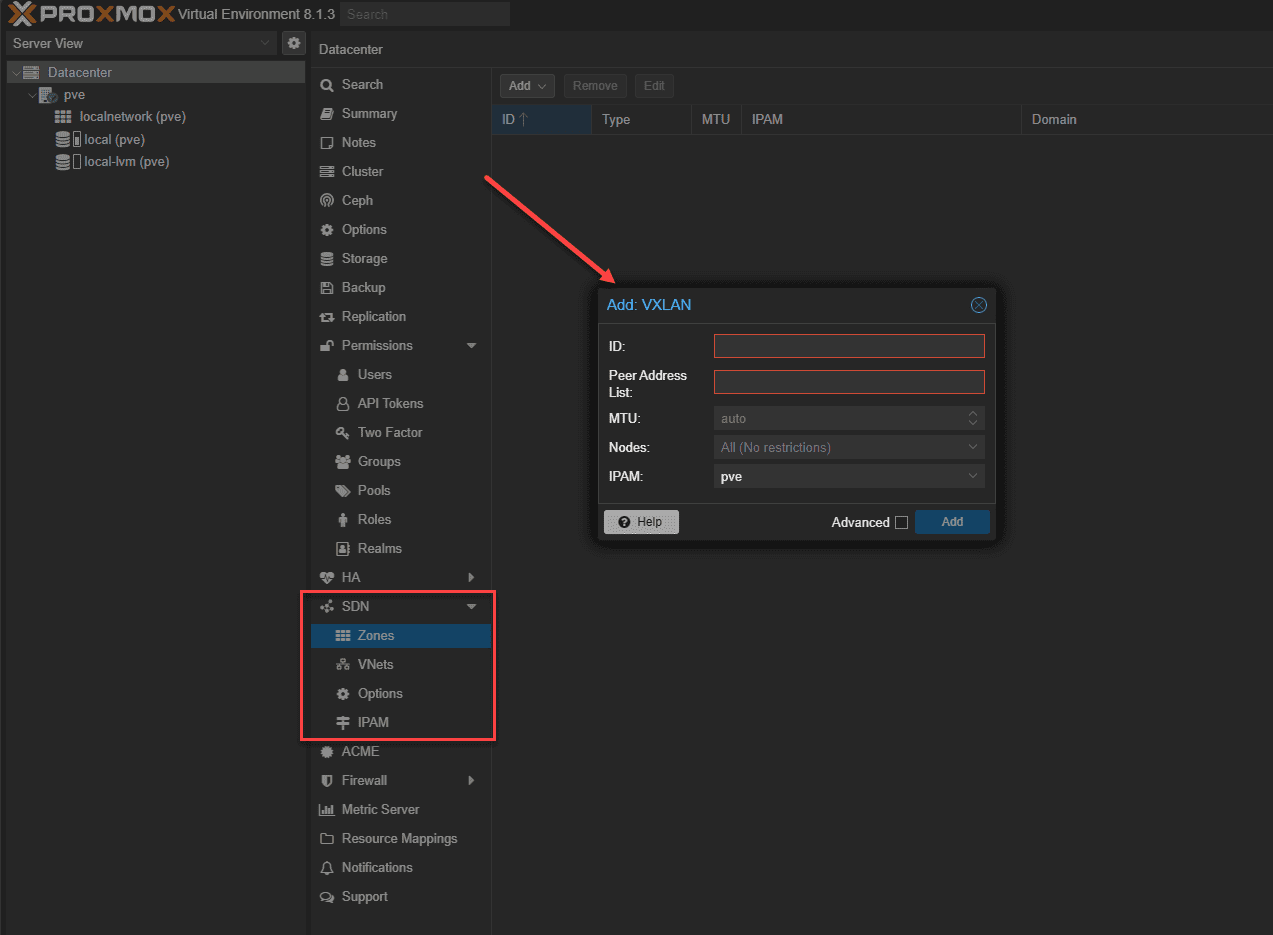
New with Proxmox 8.1 is the introduction of software-defined networking capabilities. You can read the official documentation here. The latest version of Proxmox VE comes with core SDN packages pre-installed. You now have the option for SDN technology in Proxmox VE, allowing admins to create virtual zones and networks (VNets). SDN can also be used for advanced load balancing, NAT, and other features.
Admins can administer intricate network configurations and multi-tenant environments directly through the web interface at the datacenter level in Proxmox. It allows creating network infrastructure that is more adaptive and responsive and can scale in line with evolving business requirements.
7. Troubleshooting
As you start to work with Proxmox networking, there may be a need for troubleshooting things when networking isn’t working correctly. Checking the obvious things like VLANs, VLAN tagging configuration, both in Proxmox, and on your physical network switch are important. If you are using DHCP and DNS to connect to the host, is DHCP handing out the correct IP, and do you have records to resolve the Proxmox host?
Wrapping up
No doubt you have seen various posts and content thread posts from the search forums and community support forums like the Proxmox support forum related to networking issues. These can be challenging, especially when coming from another hypervisor. Hopefully, this post will help visitors understand Proxmox networking and the security enhancements available like VLANs, SDN, and others. Proxmox networking isn’t so difficult to setup once you understand the equivalents from other virtualization environments you may be familiar with.







perfect timing 🙂
Awesome! Yes!