Wazuh Open Source SIEM: XDR for Enterprise and Home Lab
The cybersecurity landscape is evolving. Many commercial security platforms offer value, including SIEMs and others. However, an open-source solution called Wazuh stands out as a powerful open-source security platform, offering tools for threat detection, regulatory compliance, and much more. Let’s look at Wazuh and better understand its components and features that help everyone, from a chief information security officer to a home lab user, to benefit from better security in their respective environments.
Table of contents
What is Wazuh?
Wazuh operates as a security platform, offering both Extended Detection and open-source unified XDR and Security Information and Event Management (SIEM) functionalities for log data analysis. It is designed to protect endpoints as well as cloud workloads.
It provides an endpoint security agent (Wazuh agent), a multi-platform component that runs on endpoints you want to monitor. The agent provides prevention, detection, and response capabilities.
Architecture
The Wazuh solution consists of a universal agent and three central components: the Wazuh server, the Wazuh indexer, and the Wazuh dashboard. Each of these components plays a vital role:
Wazuh Server: The management server is central to the operations of Wazuh. It’s responsible for analyzing data collected from the agents and rendering decisions based on configured rules.
Wazuh Indexer: The indexer plays a role in storing the generated security alerts data efficiently, allowing for rapid queries and data retrieval.
Wazuh Dashboard: The dashboard provides a graphical user interface (GUI) where users can visualize the security alert data and conduct analyses, aiding in swift decision-making and incident response.
Licensing
Being open source, Wazuh is freely accessible and adaptable, adhering to the terms set by the GNU General Public License (version 2) and the Apache License, Version 2.0 (ALv2). This also helps with vendor lock in, at least from a budget perspective.
Wazuh Benefits
Note the following benefits of Wazuh:
- Security Data Analysis – Wazuh diligently scrutinizes security data, offering insights necessary for incident response. With its data analysis capabilities, it filters through logs and security events, providing a view of the security posture within an organization.
- Data Visualization Tool Integration – Wazuh’s compatibility with various data visualization tools allows for a security data analysis. These tools allow the visualization of live and historical data so you can understand the security events in your infrastructure.
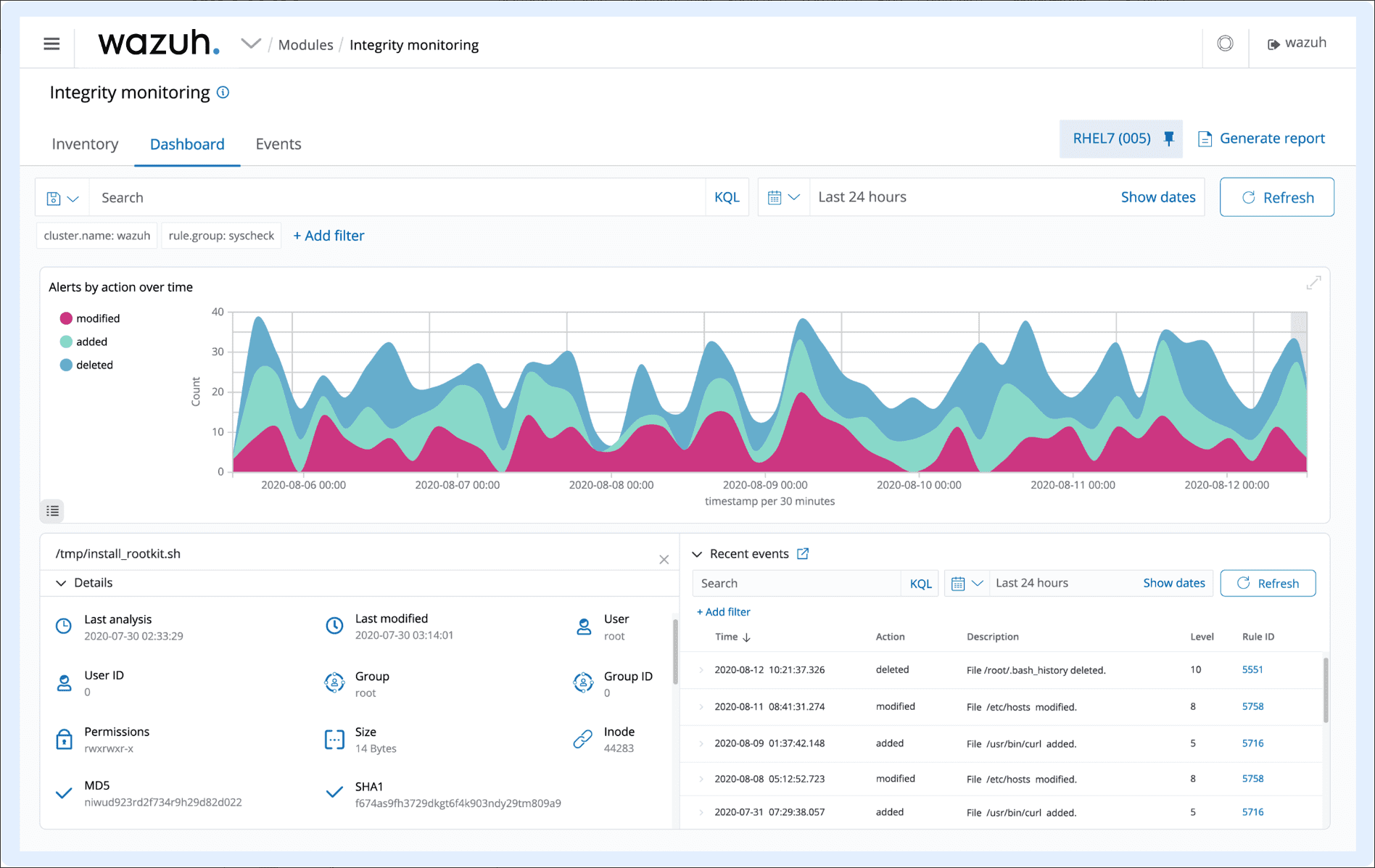
- Comprehensive Integrity Monitoring – Wazuh offers integrity monitoring services. It keeps track of and alerts on any changes in files, ensuring the data’s integrity and the system’s overall security is maintained.
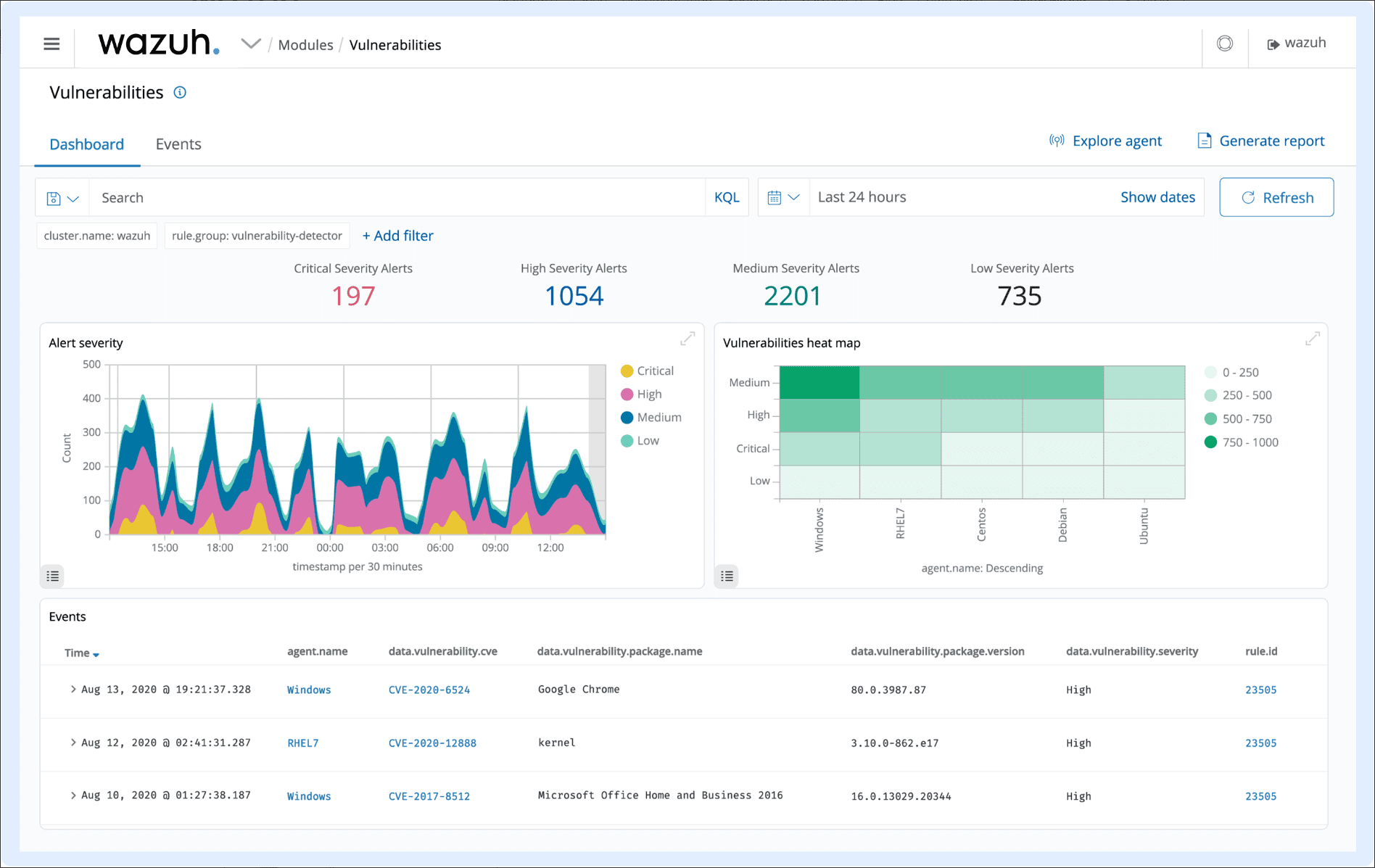
- Proactive Vulnerability Detection – Wazuh implements a vulnerability detection mechanism, identifying known vulnerabilities in installed applications and operating systems. Staying alert helps protect your system’s defenses against possible external threats.
- Increased Security Visibility – With Wazuh, you gain visibility over your network’s security events and alerts. This enhanced visibility is crucial for identifying and responding to security threats promptly and effectively.
- Strengthened Security Controls – Implementing Wazuh allows for the strengthening and fine-tuning of security controls. Its features enable the configuration and management of security policies, for a tight and effective security framework that helps with various security concerns.
- Meeting Regulatory Compliance Standards – Wazuh helps your systems meet regulatory compliance standards. It features tools and features designed to assist with compliance over time.
- Integrating Threat Intelligence – Wazuh integrates threat intelligence into its suite of tools for a proactive approach to threat detection and prevention. It uses information from various sources to identify and respond to active threats.
Wazuh’s Features
Note the following features found in Wazuh:
Regulatory Compliance Assistance
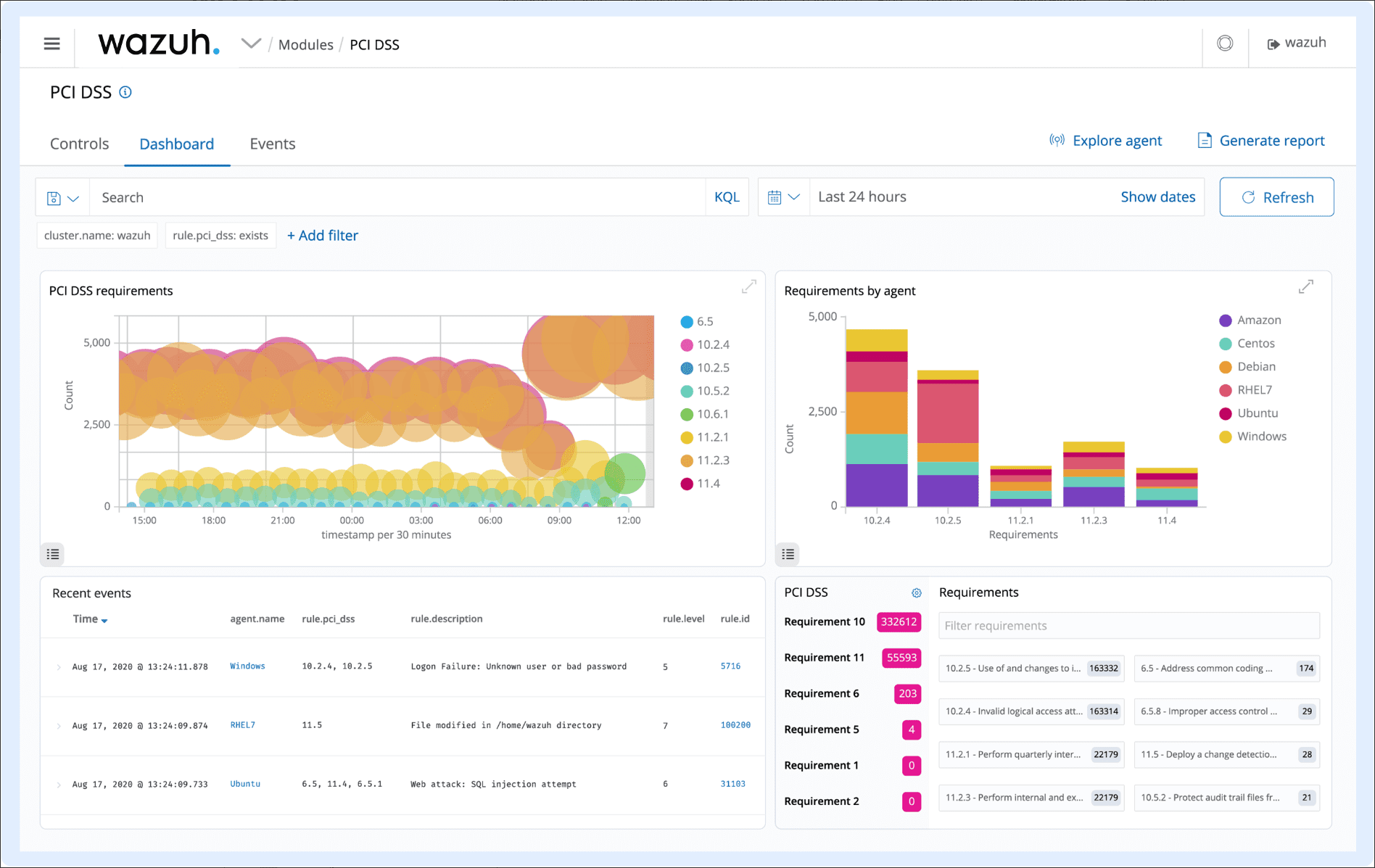
Navigating the maze of regulatory compliance standards can be daunting. Wazuh significantly eases this burden by providing tools and features tailored to meet and even exceed the requirements set by regulatory bodies. Whether PCI DSS compliance or other standards, Wazuh is equipped to ensure compliance efficiently.
Threat Detection Mechanisms
Wazuh excels in real-time threat detection, offering a set of mechanisms that diligently monitor and analyze collected log data, identifying potential threats swiftly. This proactive approach ensures that your system is always a step ahead, effectively mitigating risks and safeguarding your digital assets.
File Integrity Monitoring (FIM)
Ensuring the integrity of your files is crucial in today’s digital age. Wazuh’s File Integrity Monitoring feature scrutinizes files to detect and alert administrators about unauthorized or unexpected changes, playing a pivotal role in your security strategy.
Use Cases
Security Analytics
Wazuh facilitates collecting, aggregating, indexing, and analyzing security data, which is important for detecting intrusions, threats, and behavioral anomalies. It uses a lightweight agent to perform monitoring and response capabilities, while its server component is responsible for security data analysis.
Intrusion Detection
Wazuh agents scan for the presence of malware, rootkits, and suspicious anomalies. These agents can identify hidden files, disguised processes, and unregistered network listeners. The server component of Wazuh further enhances intrusion detection capabilities by employing a signature-based approach to analyze log data for potential indicators of compromise.
Log Data Analysis
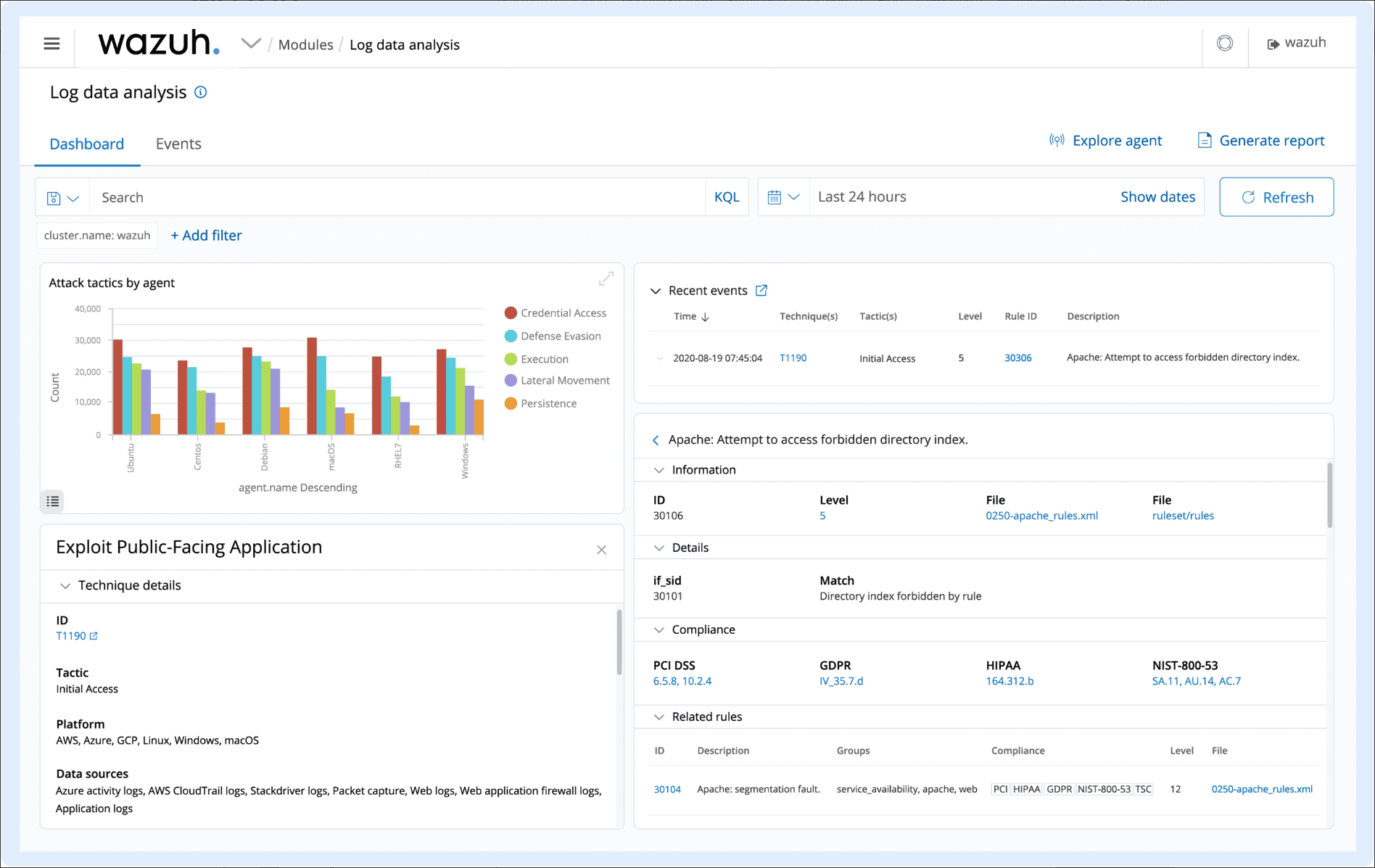
With Wazuh, operating system and application logs are read and forwarded by agents to a central manager for rule-based analysis and storage. This approach helps identify application or system errors, misconfigurations, malicious activities, and various other security and operational issues.
File Integrity Monitoring (FIM)
Wazuh notes changes in content, permissions, ownership, and attributes of files. It can identify the users and applications active in creating or modifying files. Also, the File Integrity Monitoring capabilities of Wazuh can work in tandem with threat intelligence to identify and flag potential threats or compromised hosts.
Vulnerability Detection
Wazuh agents pull software inventory data and forward this information to the server. Here, it gets correlated with updated CVE databases that help identify well-known vulnerable software. This process facilitates the discovery and mitigation of potential vulnerabilities in critical assets.
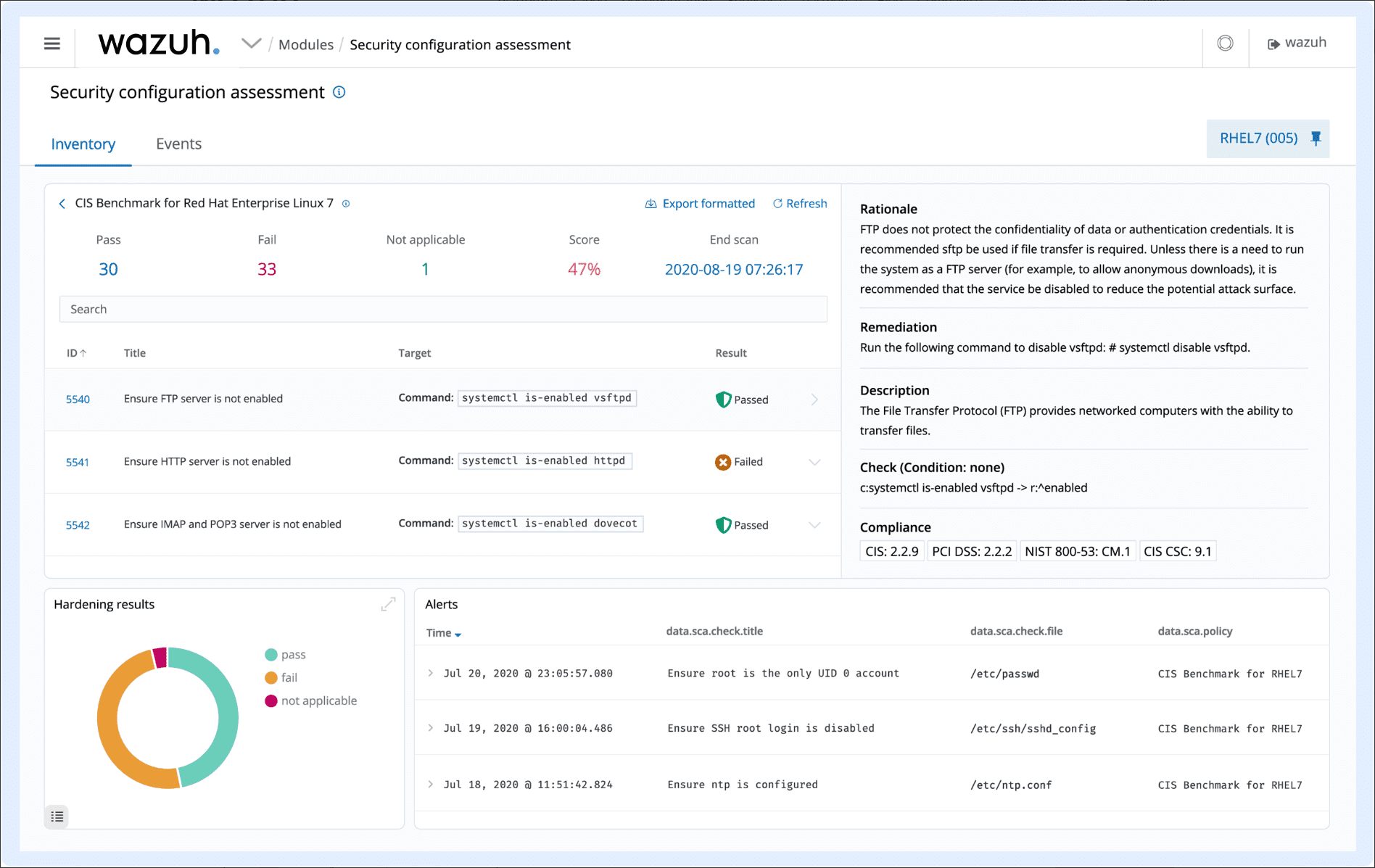
Configuration Assessment
Wazuh monitors system and application configuration settings to ensure compliance with security policies, standards, and hardening guides. The platform performs periodic scans to identify and alert on applications that are either known to be vulnerable, unpatched, or insecurely configured.
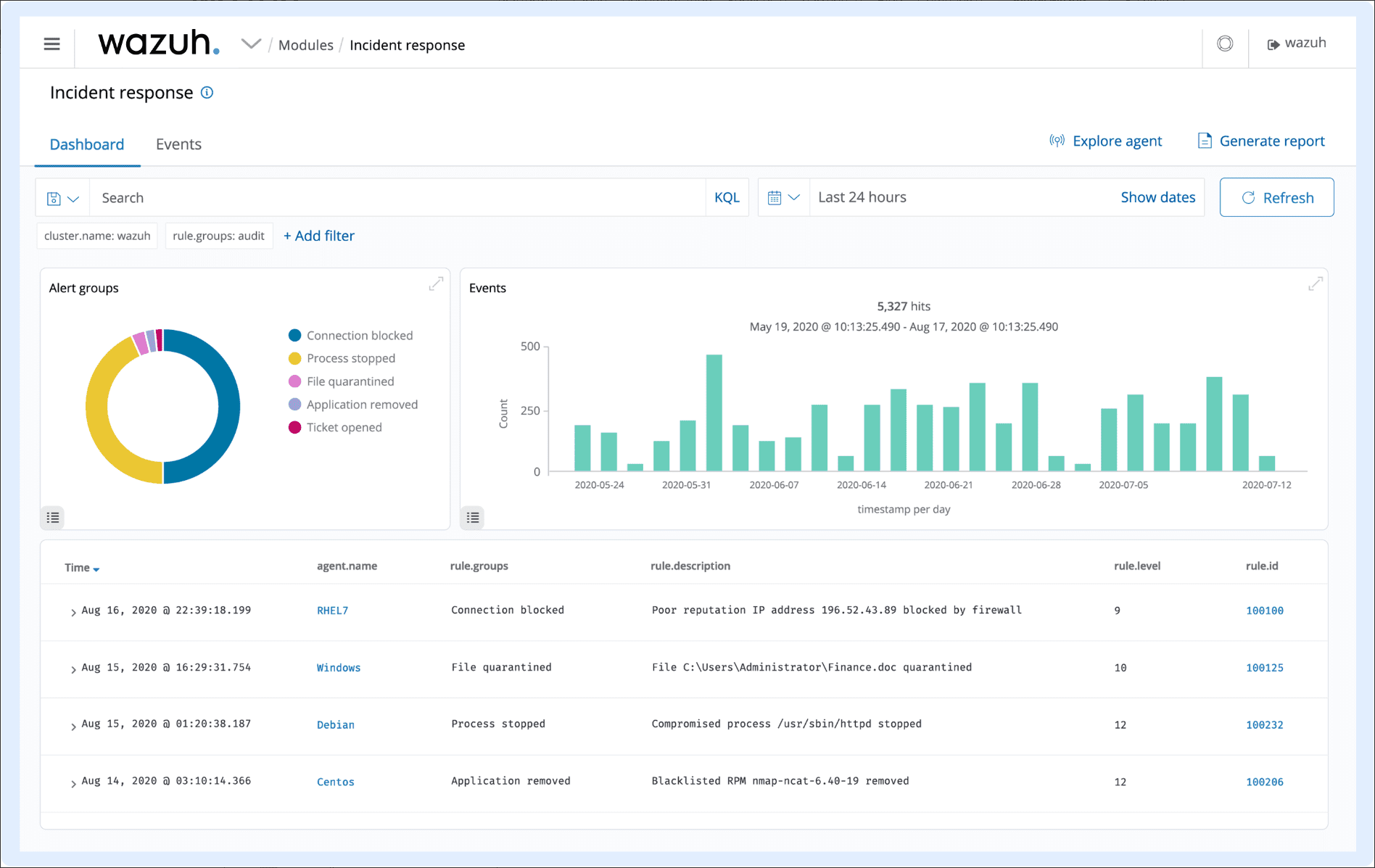
Incident Response
Active responses to counteract ongoing threats are provided out-of-the-box by Wazuh. These responses can vary from blocking access to a system from identified threat sources to running commands remotely for live forensics or incident response tasks.
Regulatory Compliance
Wazuh provides a set of security controls necessary for compliance with various industry standards and regulations. It helps meet technical compliance requirements.
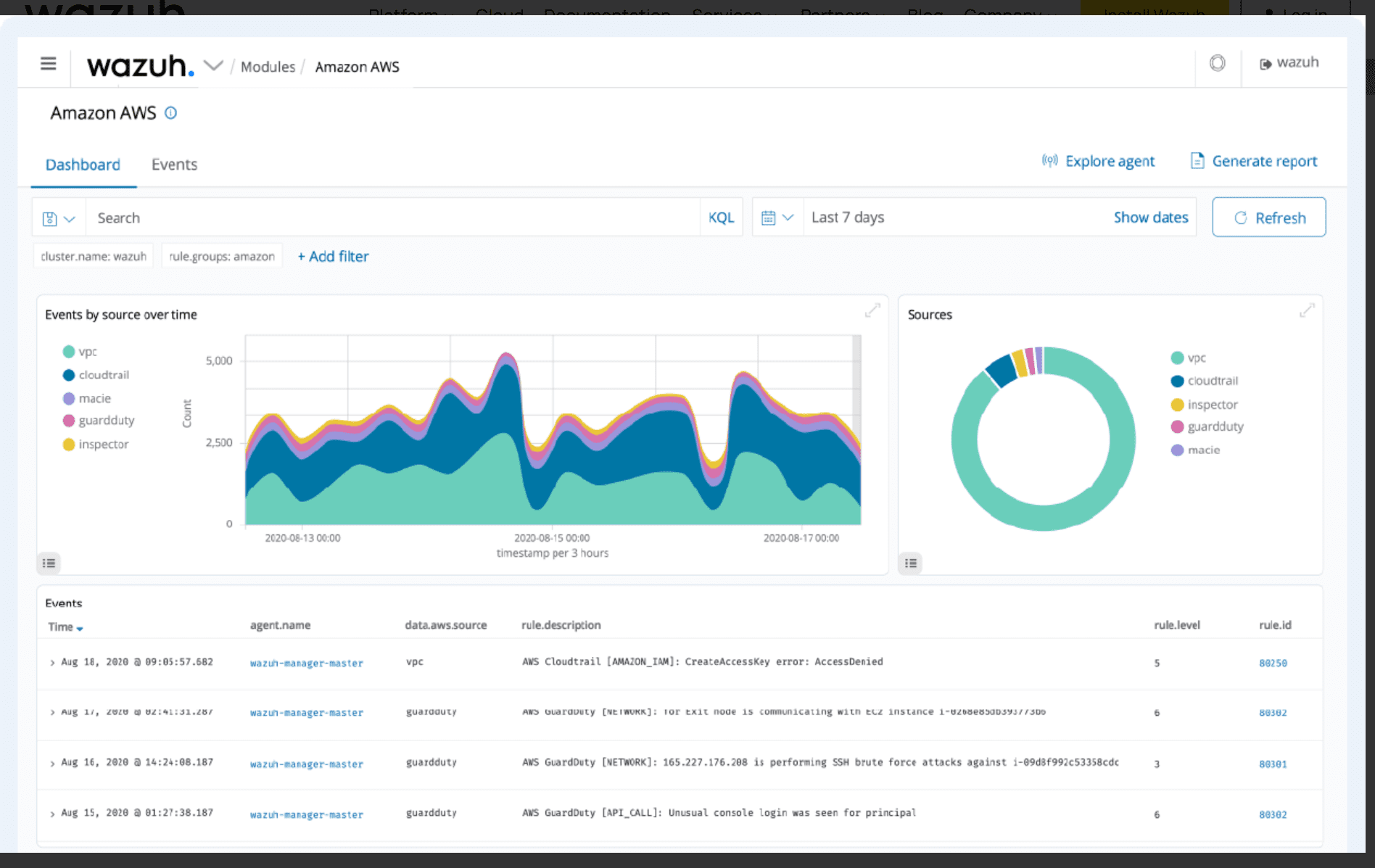
Cloud Security
Wazuh monitors cloud infrastructure at the API level through integration modules designed to pull security data from public cloud providers. The platform provides rules for assessing the configuration of cloud environments, and its agents are deployed for monitoring at the instance level within cloud environments.
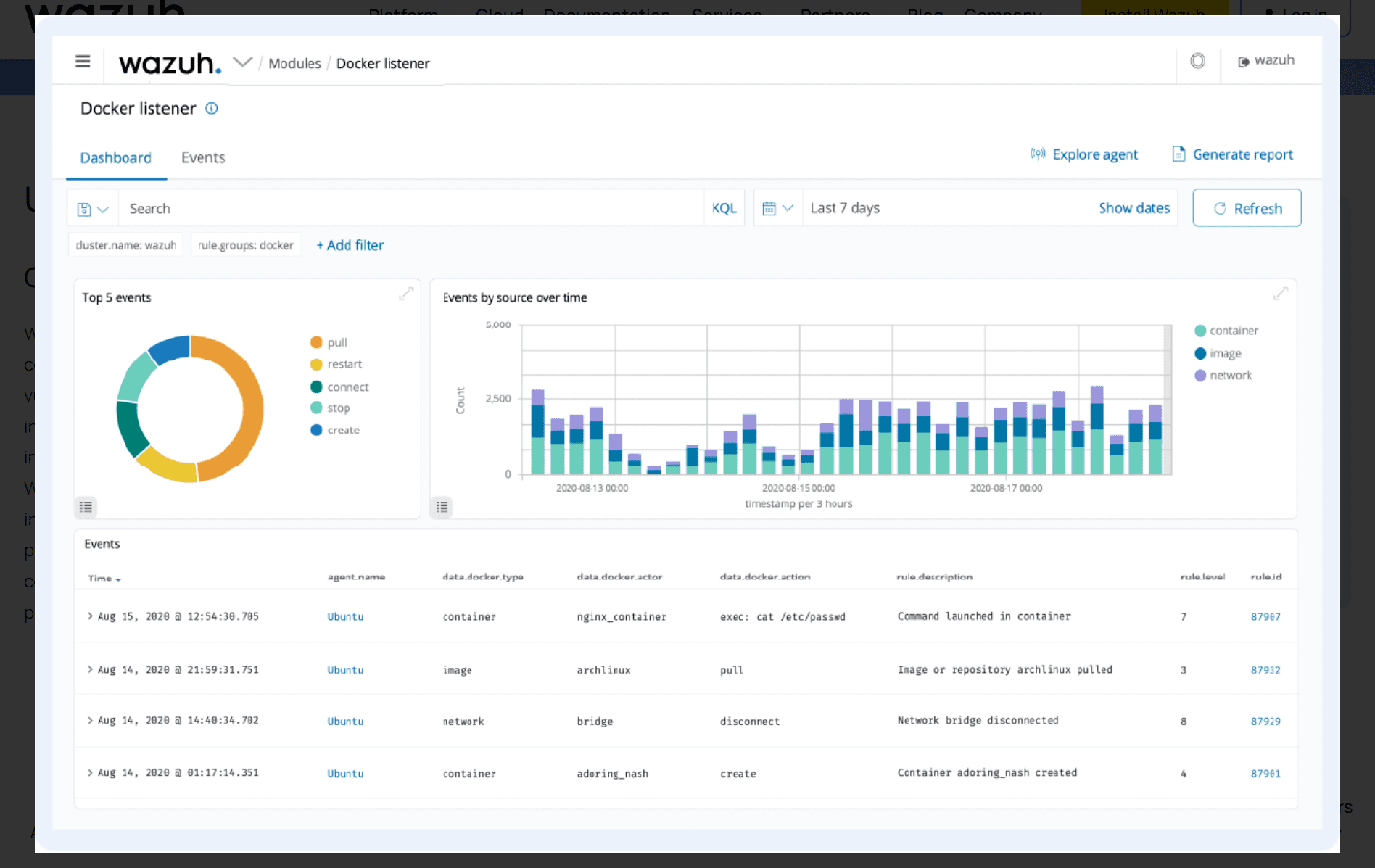
Containers Security
Wazuh ensures security visibility into Docker hosts and containers, providing a mechanism for monitoring their behavior while detecting threats, vulnerabilities, and anomalies. The platform has native integration capabilities with the Docker engine, allowing for comprehensive monitoring of images, volumes, network settings, and containers.
Installation Requirements
For installation, the hardware prerequisites depend on the number of endpoints and cloud workloads you intend to protect. The hardware specs provide a guide for the amount of data anticipated for analysis and the volume of security alerts to be indexed and stored.
The quickstart guideline suggests that a single host for the Wazuh server, indexer, and dashboard can monitor up to 100 endpoints, with 90 days’ worth of alert data being queryable and indexed.
The hardware requirements for varying numbers of agents are outlined, ranging from 4 vCPU and 8 GiB RAM for 1-25 agents to 8 vCPU and 8 GiB RAM for 50-100 agents, with corresponding storage needs.
A distributed approach is advised for deployment in larger environments, with multi-node cluster configurations available for both the Wazuh server and indexer to facilitate high availability and load balancing.
Supported Operating Systems
The Wazuh central components are compatible with 64-bit Linux operating systems, with specific recommended versions with each operating system, including:
Amazon Linux 2
CentOS 7 and 8
Red Hat Enterprise Linux 7 to 9
Ubuntu 16.04 to 22.04.
Browser Compatibility
Wazuh is compatible with modern web browsers, including Chrome, Firefox, and Safari, for the web user interface. Other browsers based on Chromium may work. As a note, Internet Explorer 11 is not supported (not that anyone will be using that).
Installing Wazuh
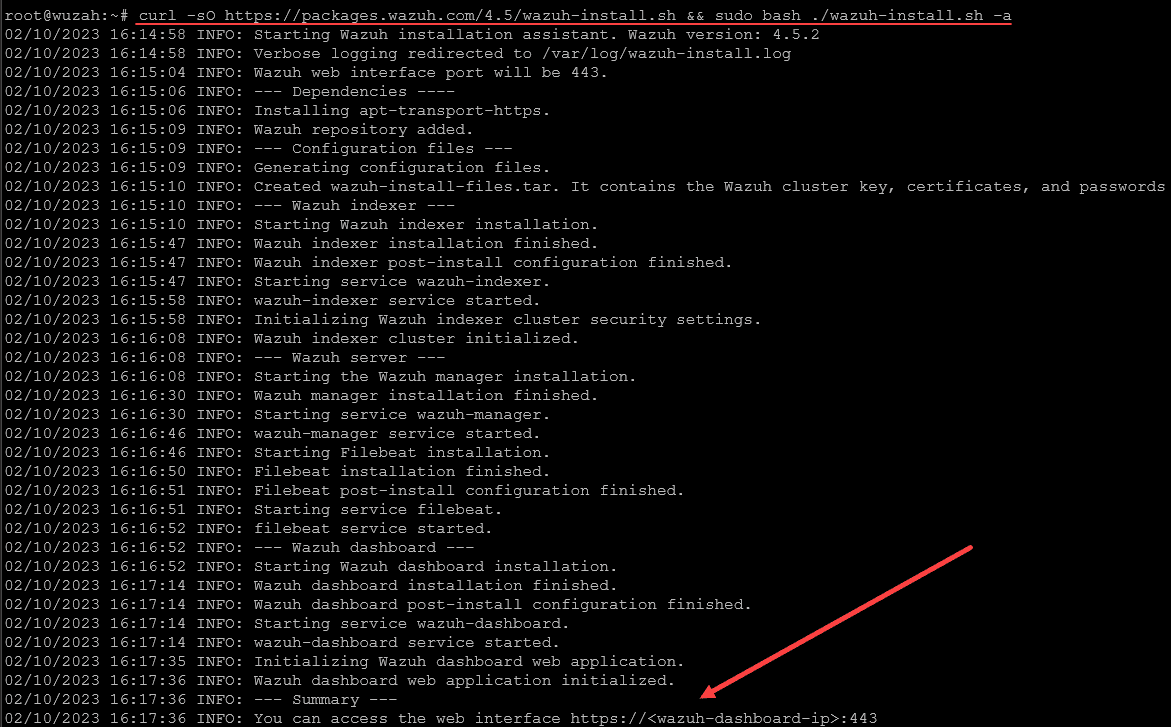
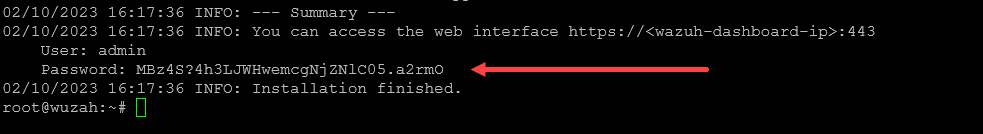
To install Wazuh, you will download and execute the Wazuh Installation Assistant through the command-line interface using the curl command as shown in the below command:
curl -sO https://packages.wazuh.com/4.5/wazuh-install.sh && sudo bash ./wazuh-install.sh -aWhen the install completes, the terminal will display access credentials (username and password) and a confirmation message indicating a successful installation.
Initial Access
For initial access to the Wazuh web interface, navigate to https://<wazuh-dashboard-ip> and use the provided credentials:
Username: admin
Password: <ADMIN_PASSWORD>
First login and certificate warning
Upon first access, users might encounter a browser warning due to the certificate not being issued by a recognized Certificate Authority (CA). This is expected. Accept the certificate as an exception (often required in a development or test environment) or configure the system with a certificate issued by a trusted authority for production environments.
Retrieving Passwords
Passwords associated with the Wazuh indexer and Wazuh API can be found within the wazuh-passwords.txt file, located in the wazuh-install-files.tar archive. You can use the following command to display these:
sudo tar -O -xvf wazuh-install-files.tar wazuh-install-files/wazuh-passwords.txtUninstallation
In cases where you want to uninstall Wazuh central components, the Wazuh Installation process can be invoked with the -u or –uninstall options.
Adding agents
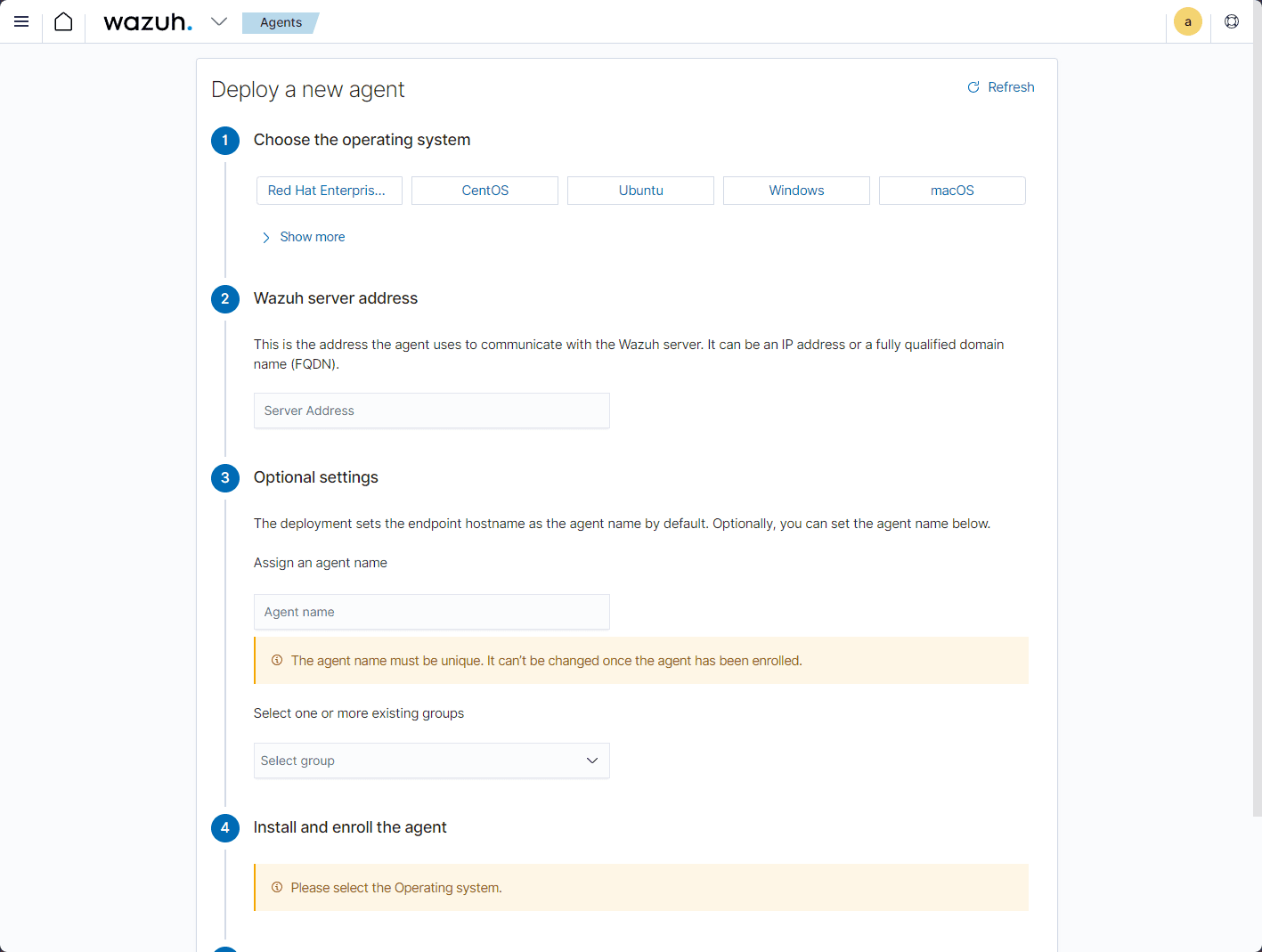
After you install the Wazuh dashboard, your next step is to install the agents. Agents can be deployed across many different platforms, including laptops, desktops, servers, cloud instances, containers, and virtual machines. It is lightweight and has many capabilities to provide many different security capabilities on your endpoints.
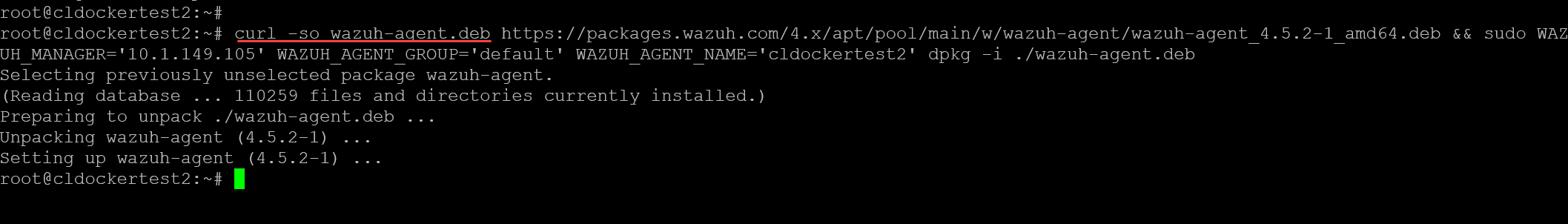
Once you select your options, it will generate a curl command customized for your environment for Linux.
After you generate the curl command, paste it in the target device. Below I have a test Ubuntu Server 22.04 LTS machine I am onboarding into Wazuh.
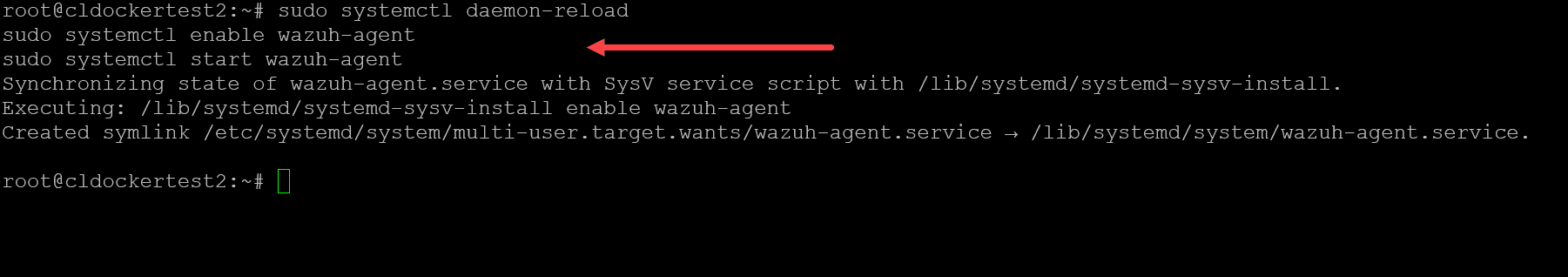
It will have you reload the agent installation:
sudo systemctl daemon-reload
sudo systemctl enable wazuh agent
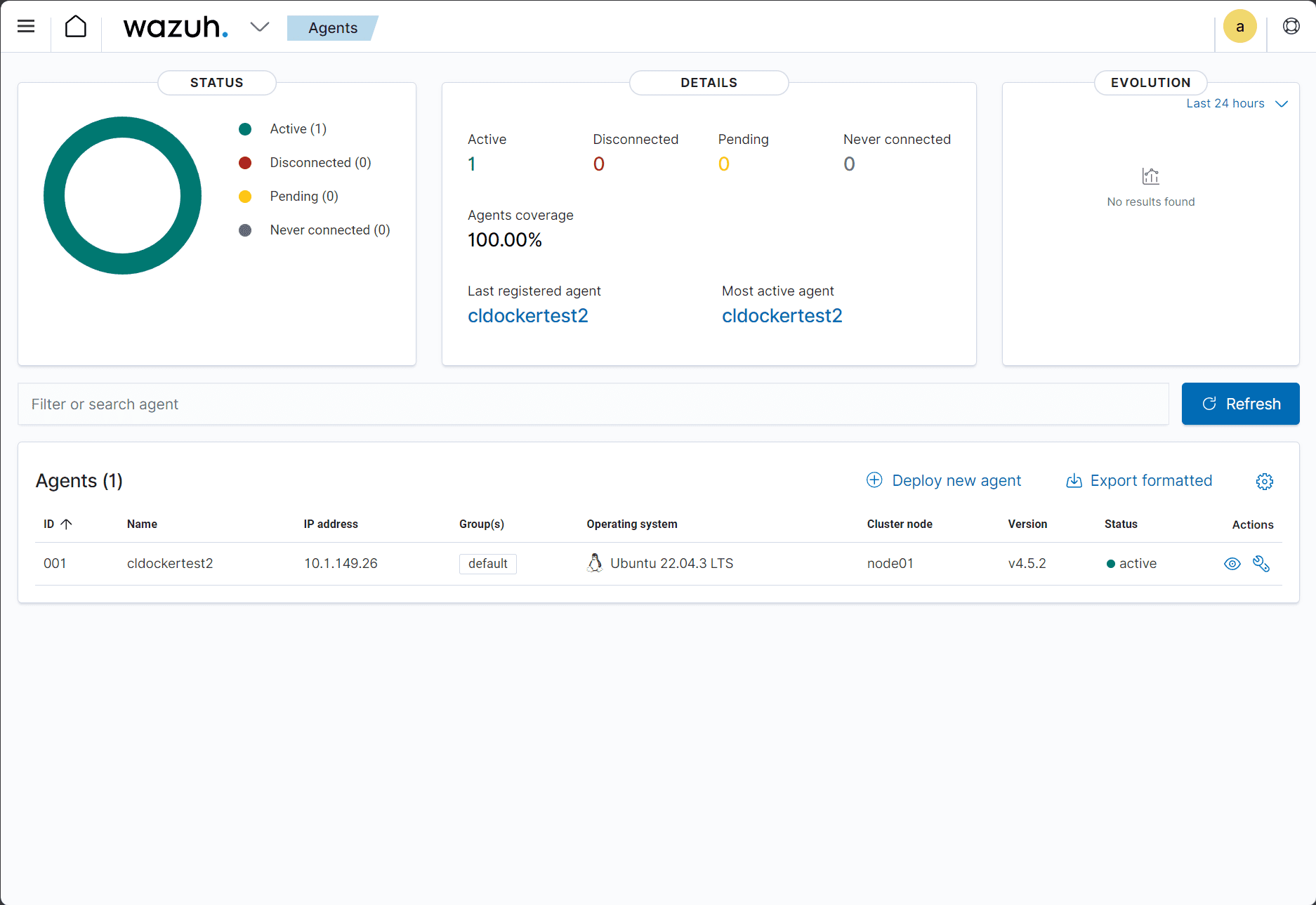
sudo systemctl start wazuh-agentThe Ubuntu Server is onboarded and we start to see metrics on the machine.
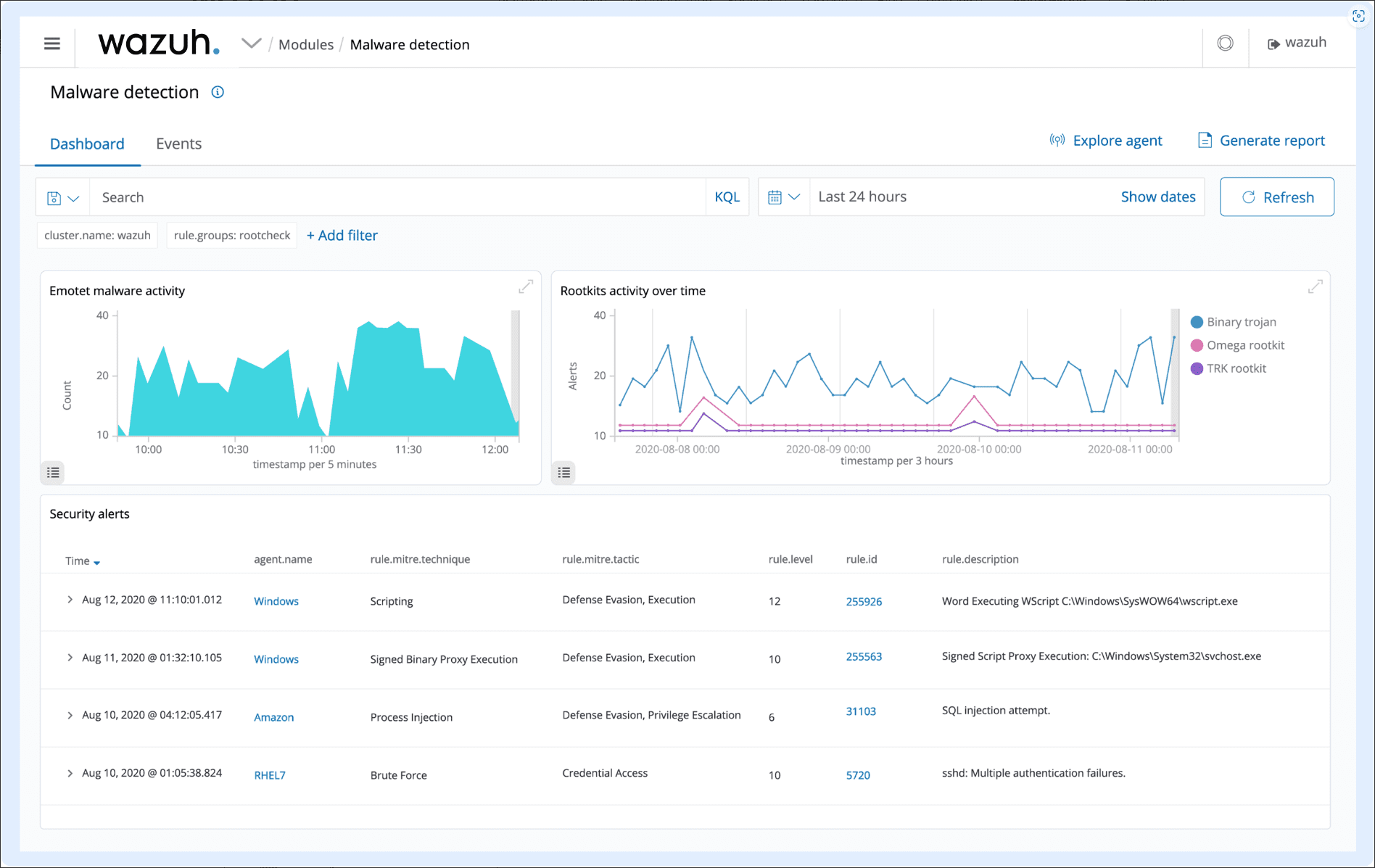
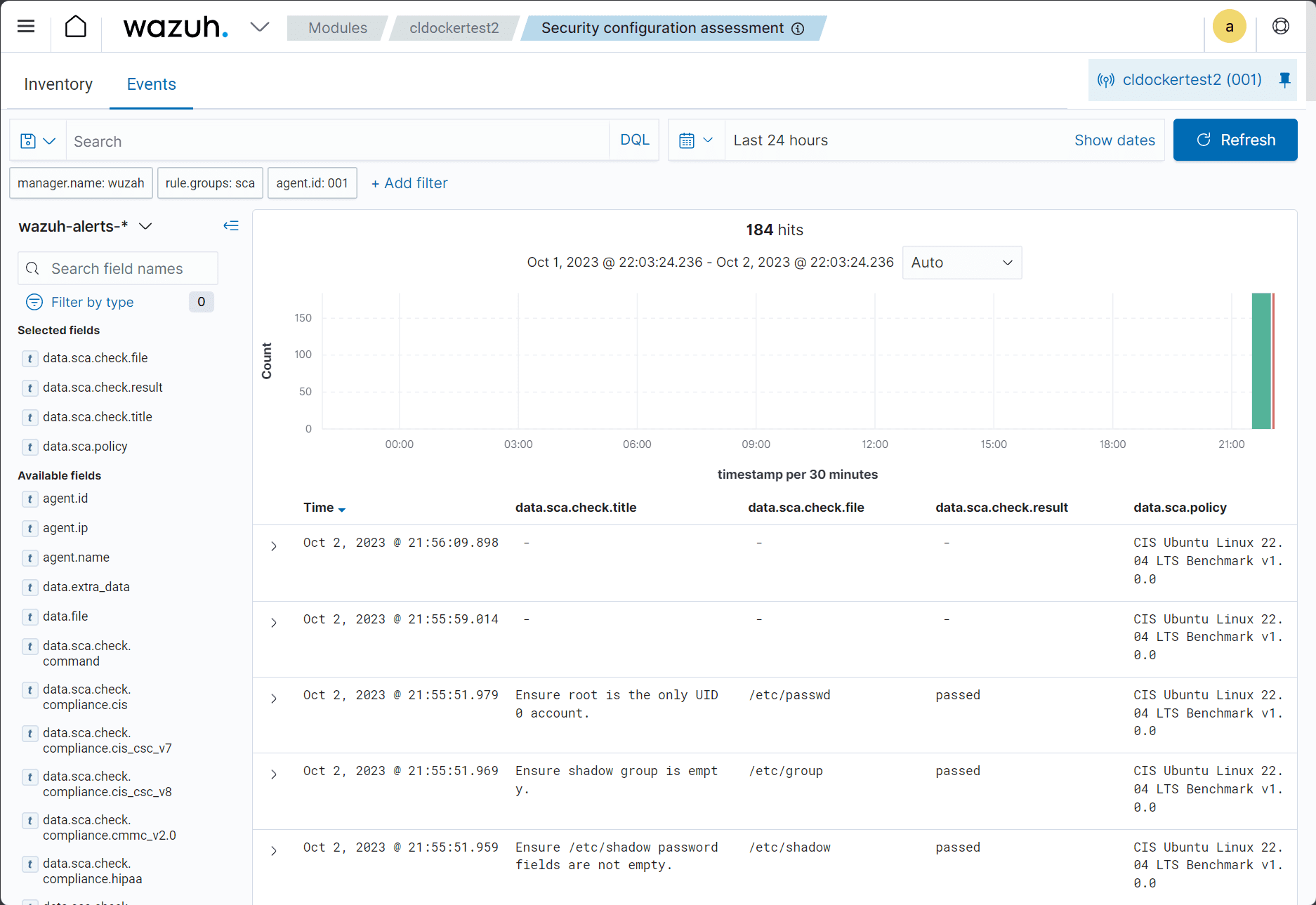
Looking at the security configuration assessment.
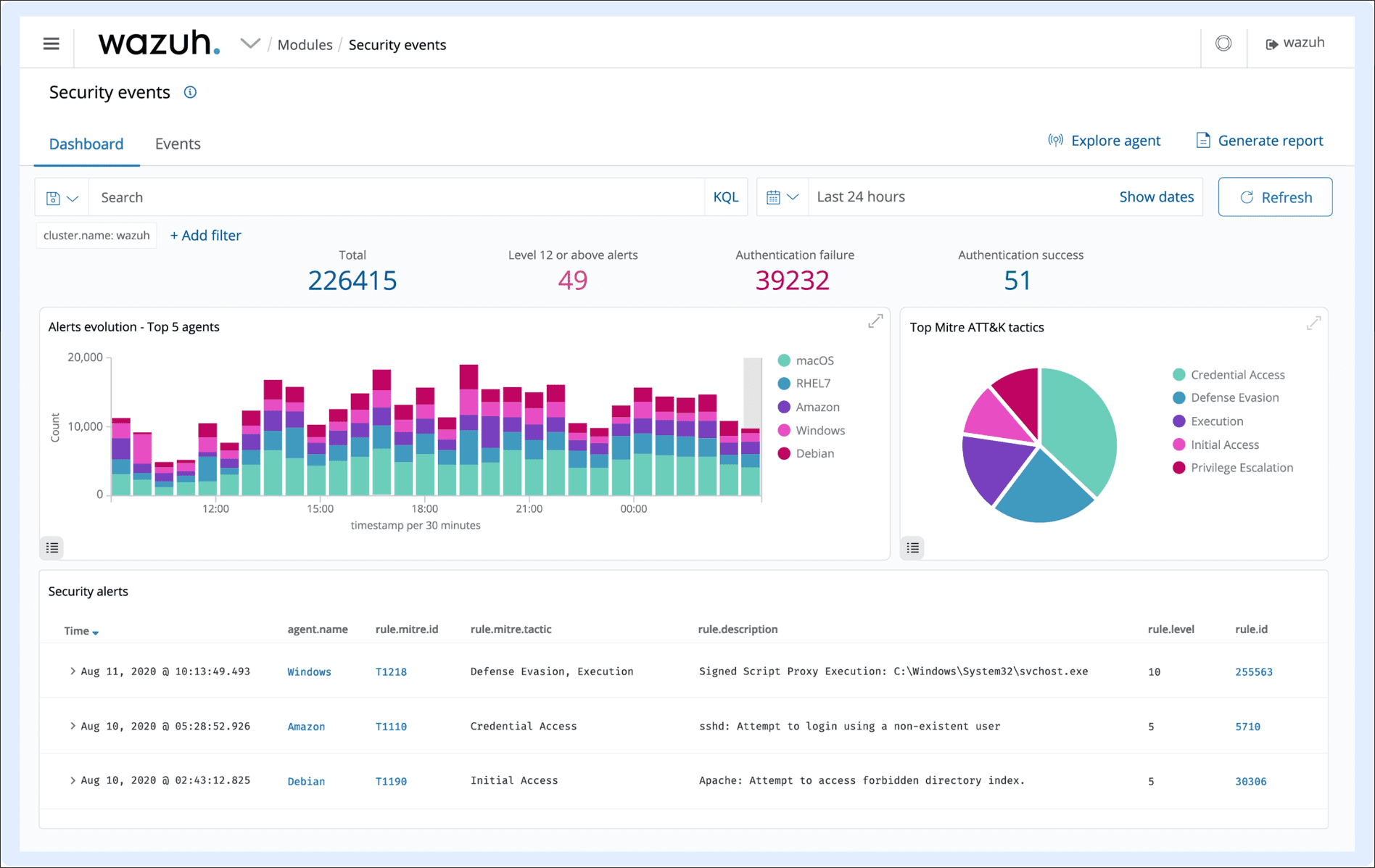
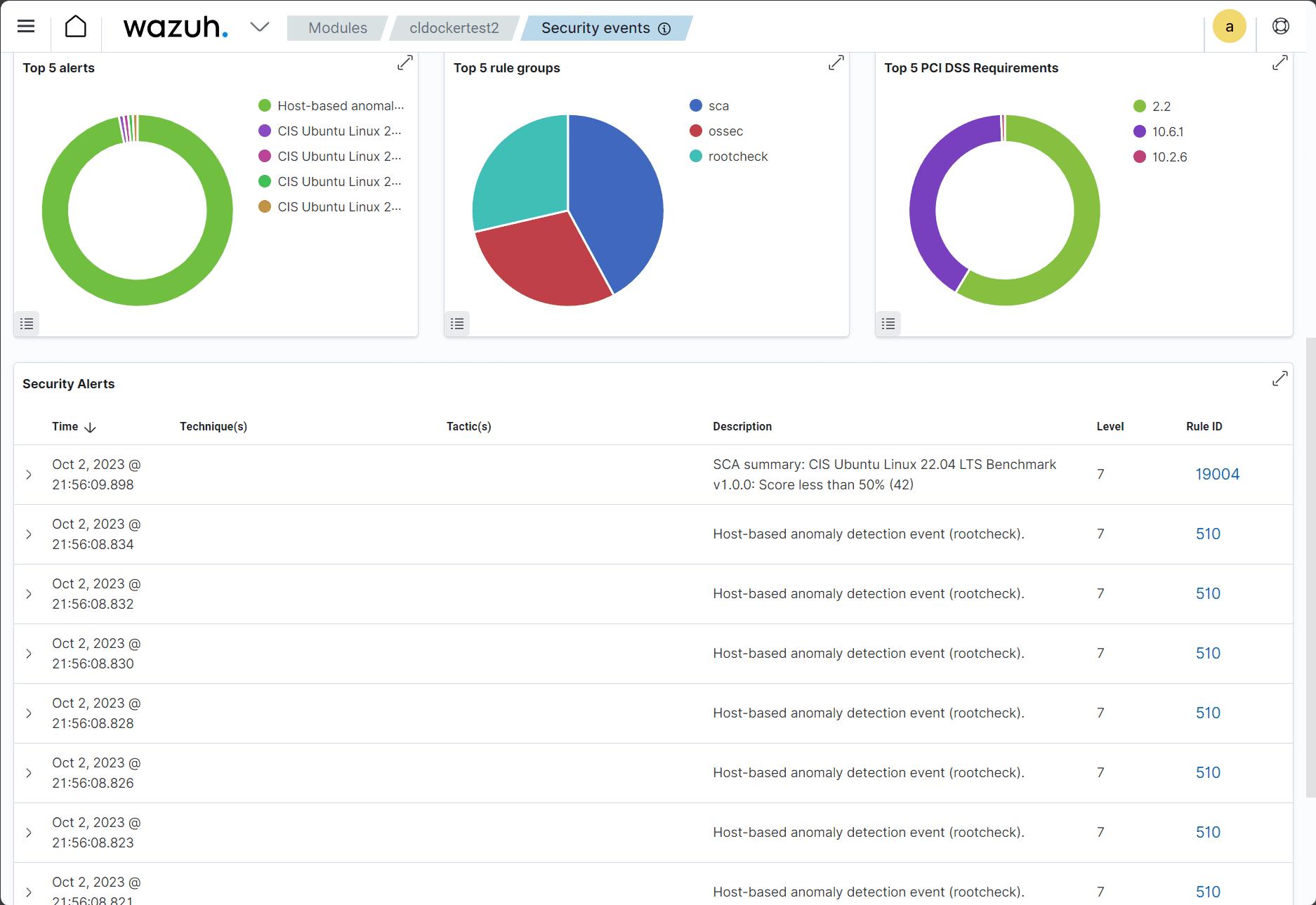
Looking at security events for the agent machine.
Wrapping up
If you are looking for a free and open-source security solution with the feel and polish of an enterprise solution, Wazuh is definitely a solution to check out. With features like threat detection, file integrity monitoring, and support for cloud environments, its feature set will impress chief information security officers and IT security professionals alike.
It can help protect on-premises infrastructure, cloud workloads, or hybrid environments, which will cover most use cases across the board. It is also a great tool to run in the home lab, where free and open-source software provides a great alternative to paid solutions for keeping things secure and effectively monitoring your servers and endpoints.










Very nice, I want re-post this.