Security Onion Install: Awesome Open Source Security for Home Lab

Security Onion is at the top of the list if you want an excellent security solution to try in your home lab or even for enterprise security monitoring. It provides many great security tools for threat hunting and overall security and is fairly easy to get up and running quickly.
Table of contents
- What is Security Onion?
- Installation Media
- Security Onion installation architecture and OS
- Frequently Asked Questions about Security Onion
- How Does Security Onion Ensure Secure Network Configuration?
- What Makes Security Onion a Preferred Choice for Security Teams?
- Can it be Deployed in a Virtual Machine?
- How Does Security Onion Handle Log Management?
- What Role Do Docker Containers Play in Security Onion?
- Is Security Onion Suitable for Small Business Networks?
- How Does the Community Contribute to Security Onion’s Development?
- How Does Security Onion help with threat hunting?
- Can it Integrate with Windows Server Environments?
- How Does it Enable Efficient Security Monitoring?
- Wrapping up
What is Security Onion?
Security Onion, by Security Onion Solutions, makes setting up a security system extremely easy by bundling various tools and services together to create an excellent solution against online threats. It is a free and open platform and is popular among security teams thanks to its capabilities in intrusion detection, security monitoring, and managing logs.
It provides a tool to analyze, identify, and alert on any suspicious activities or potential threats. Note the following features:
Network visibility – collect events from your network from Zeek, Suricata, and other network monitoring IDS tools
Host visibility – it supports the Elastic Agent for event collection from endpoints
Static analysis (PCAP and EVTX import) – You can import full capture files and Windows Event log files to review and analyze events
Security Onion desktop – This Linux desktop provides security professionals the tools needed to analyze the network and host events.
Intrusion Detection and Threat Hunting
You can use the Elastic Stack and various other components it enables security teams to perform in-depth analysis of network traffic identifying potential threats and anomalies that could indicate a breach or attempted attack.
Monitoring and Log management
When it comes to security monitoring and log management, Security Onion offers a structured and efficient way to handle, analyze, and store log data. This is crucial for organizations to comply with various data protection regulations and have a historical record of network activities, which can be invaluable during incident response and forensic investigations.
Community support
There is a wide range of community support for Security Onion. If you have questions about the platform, there are also a lot of blog posts and YouTube videos going over how to configure and set things up. One thing to note though, the 2.4 release has some differences with how things are allowed and configured now compared to the more command-line driven approach of previous versions.
Installation Media
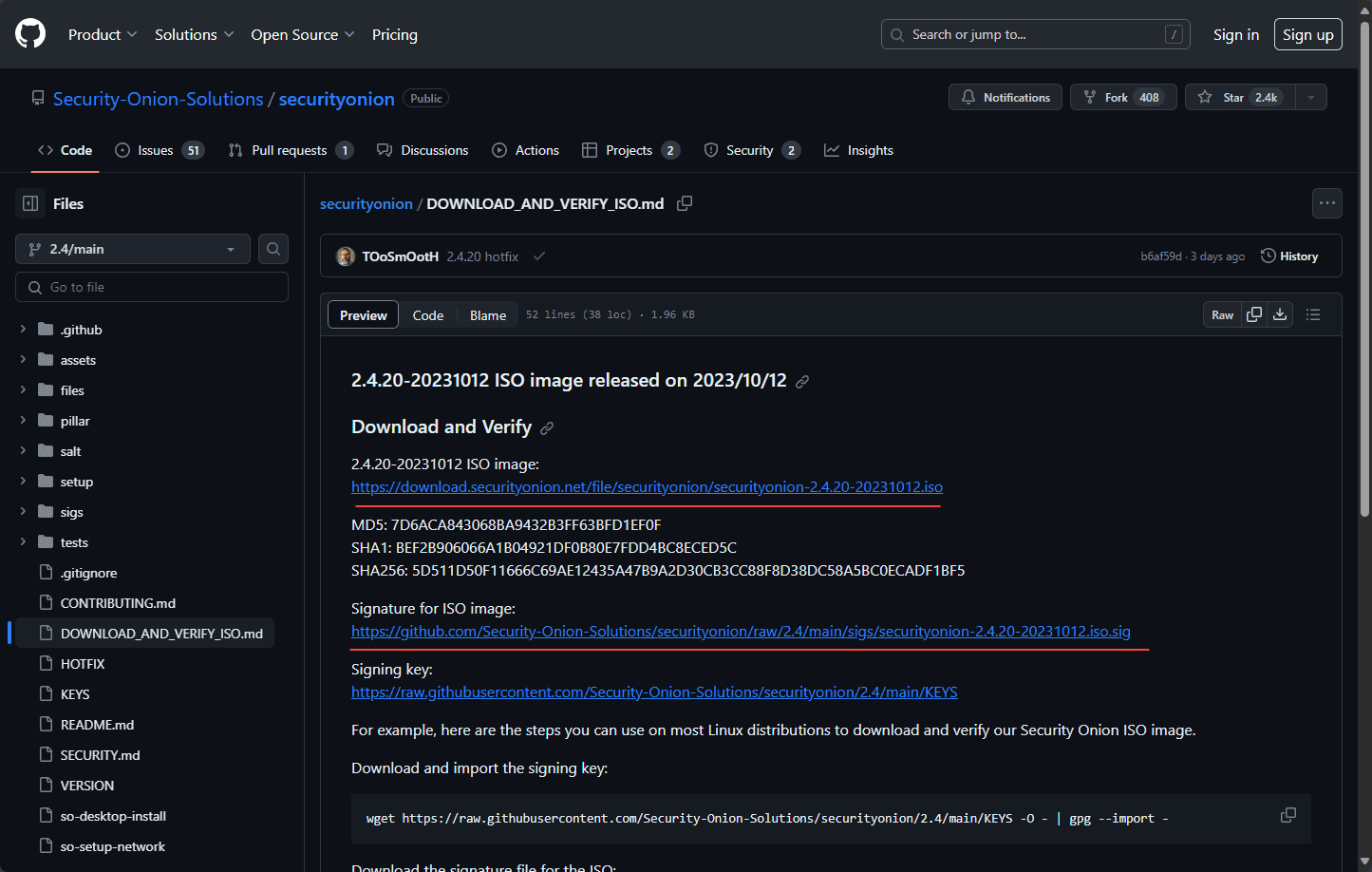
Security Onion Solutions provides Security Onion by means of an ISO image. The ISO, available through the official Security Onion website, is a pre-configured image containing everything you need for the installation. As a note, the ISO is very large (around 15 GB). So, definitely download this on a healthy connection.
Download it here: securityonion/DOWNLOAD_AND_VERIFY_ISO.md at 2.4/main · Security-Onion-Solutions/securityonion · GitHub.
Security Onion also provides the checksum for the ISO image, which is good for validating the integrity of the downloaded Security Onion ISO image making sure it is not altered in any way or corrupted.
Security Onion installation architecture and OS
Security Onion is deployed in a virtual machine when you boot from the ISO. Docker containers are used for the underlying security tools and services, which helps isolate and reduce conflicts between different software components. You will see the Docker configuration as part of the installation process in the screenshots below.
Underlying operating system
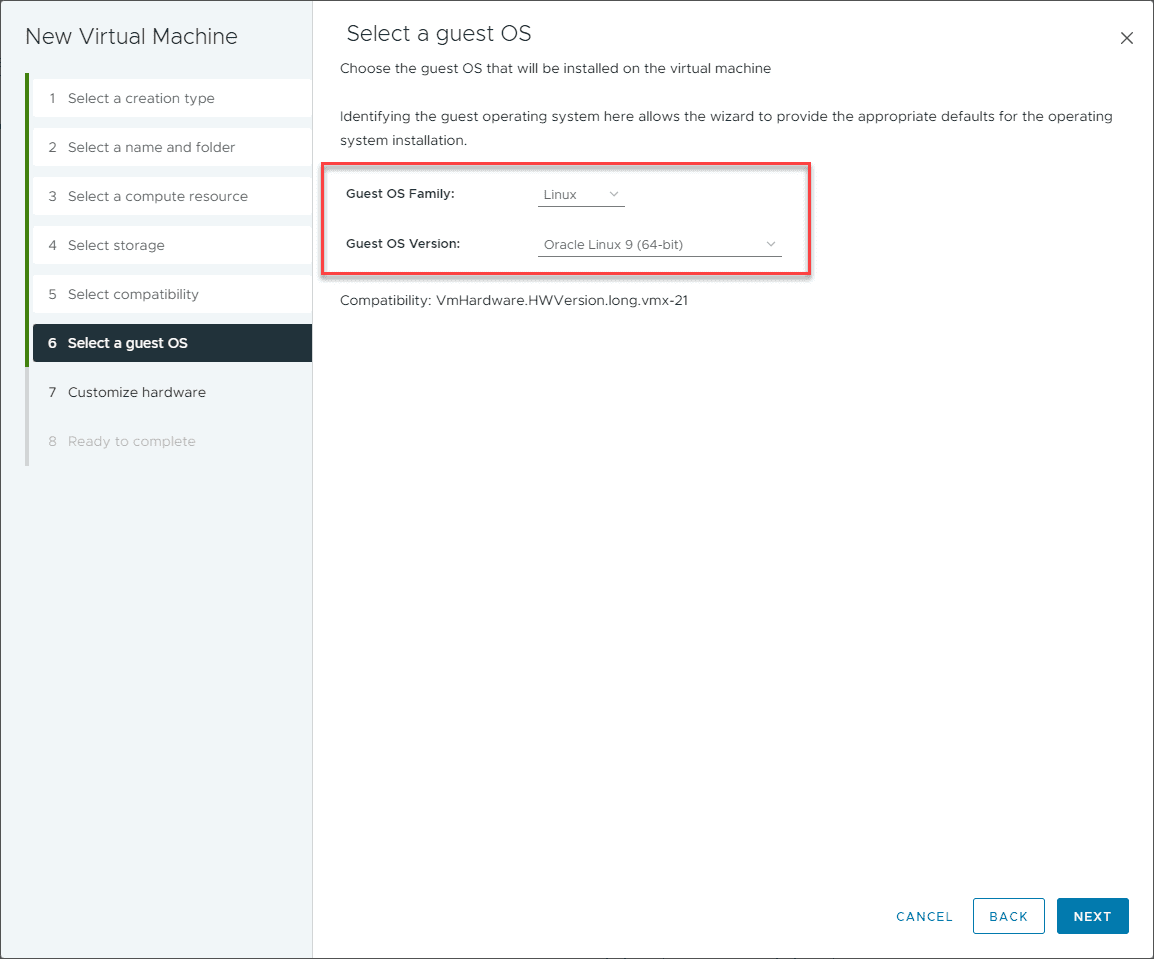
With the recent change in RedHat open-source licensing, Security Onion is now built on top of the Oracle Linux 9 distribution, an open-source Linux distribution. Below, I am creating a VMware vSphere VM with the Guest OS Version set to Oracle Linux for the installation.
Ensuring Compatibility and Preparing for Installation
Before installing, make sure your system meets the recommended hardware specifications. With the security onion ISO image and installation, you need to pay attention to details like network adapters and storage to make sure you have a smooth installation and operation of SO. Otherwise the install is straightforward.
Having a dedicated network adapter for the management network and another for a network “sniffing interface” (port mirroring) is the configuration that most will configure.
Other notables from the install:
24 GB of memory is recommended and you will see a warning if you don’t meet this
You must have (2) network interfaces or the installation will end
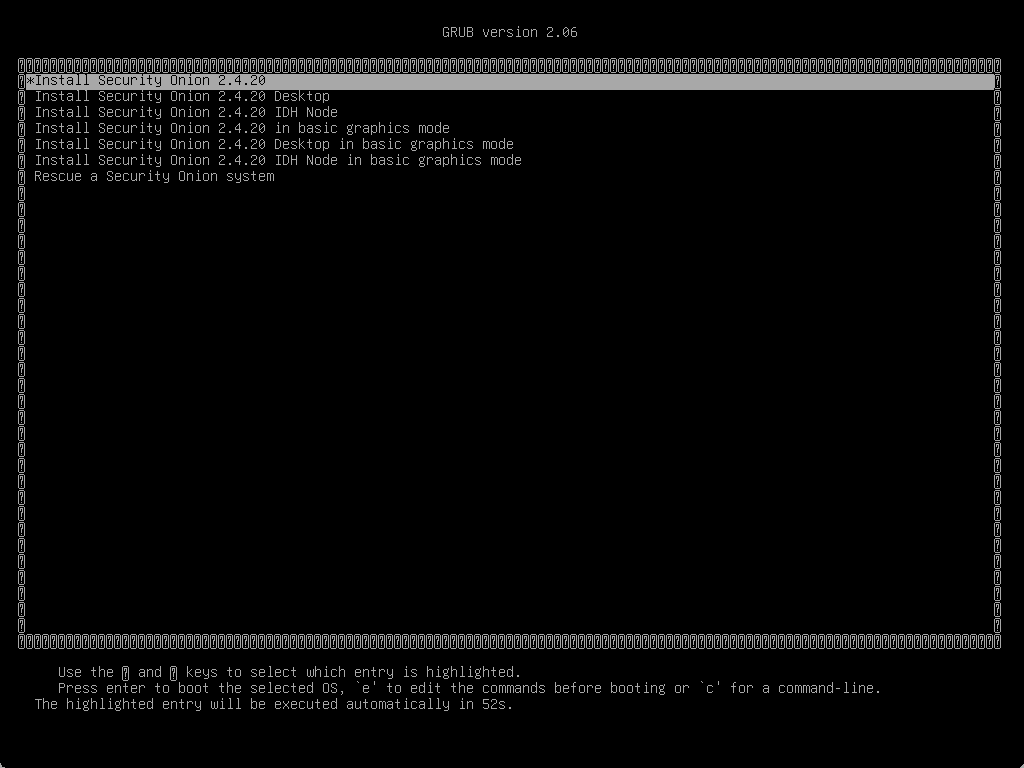
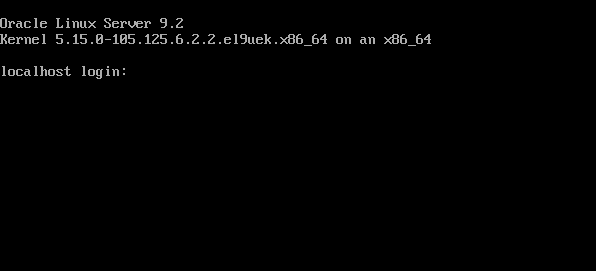
Running the ISO installer
Below, is booting from the ISO image.
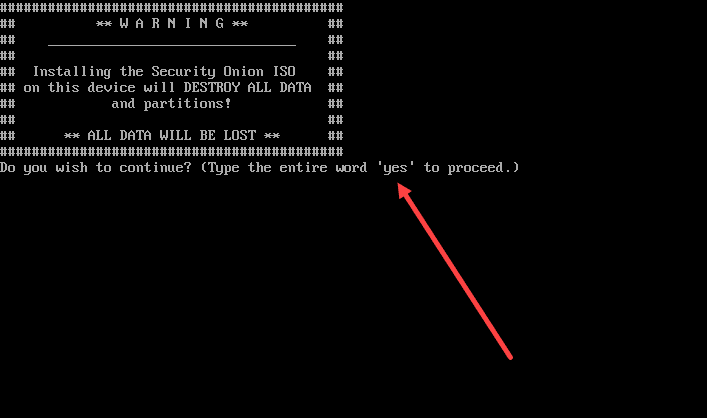
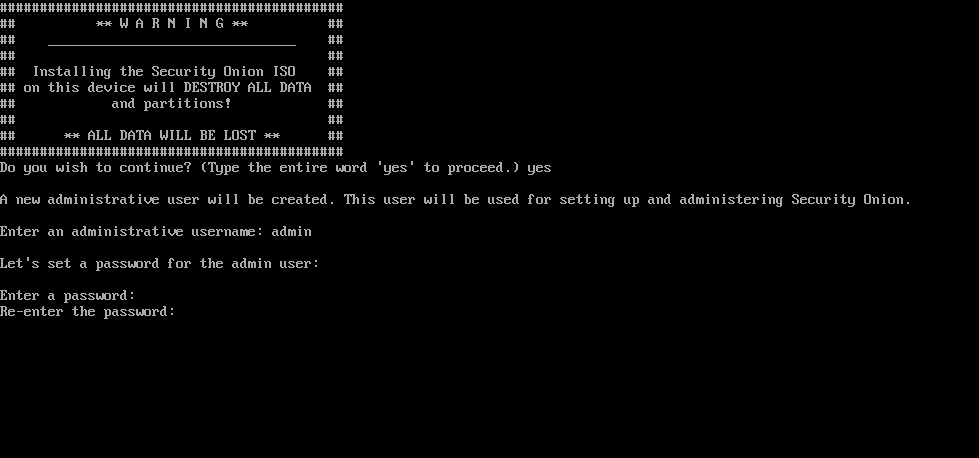
Type Yes to allow it to destroy the contents of the drive.
Enter the name of the admin user you want to use and then setup a password.
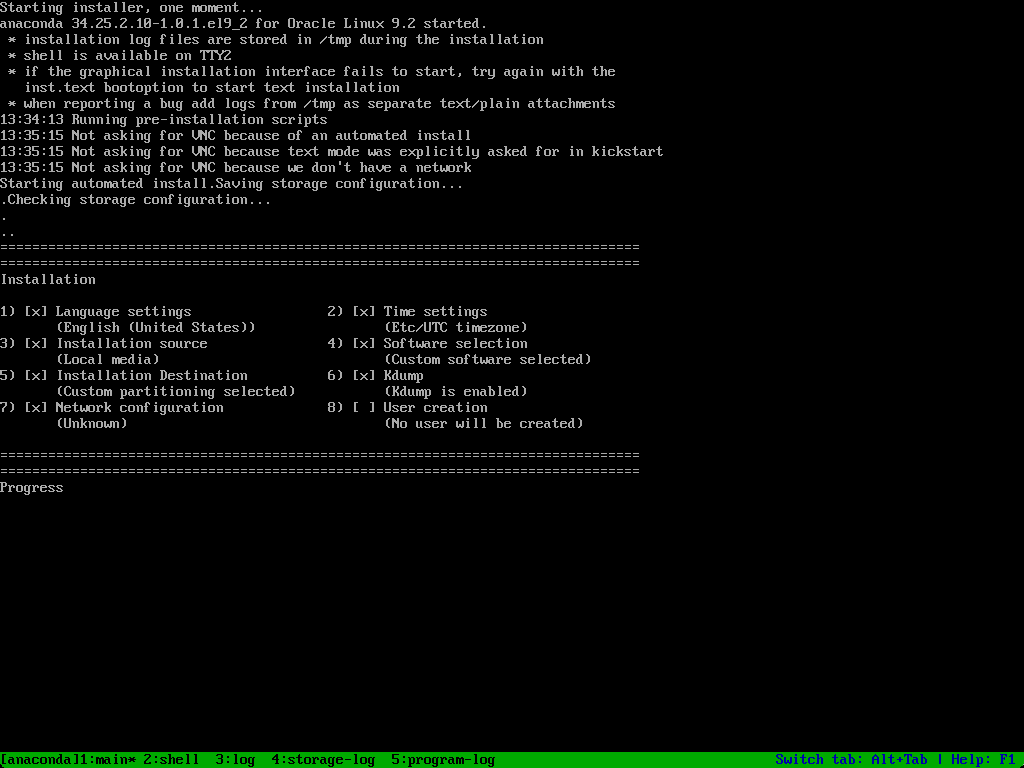
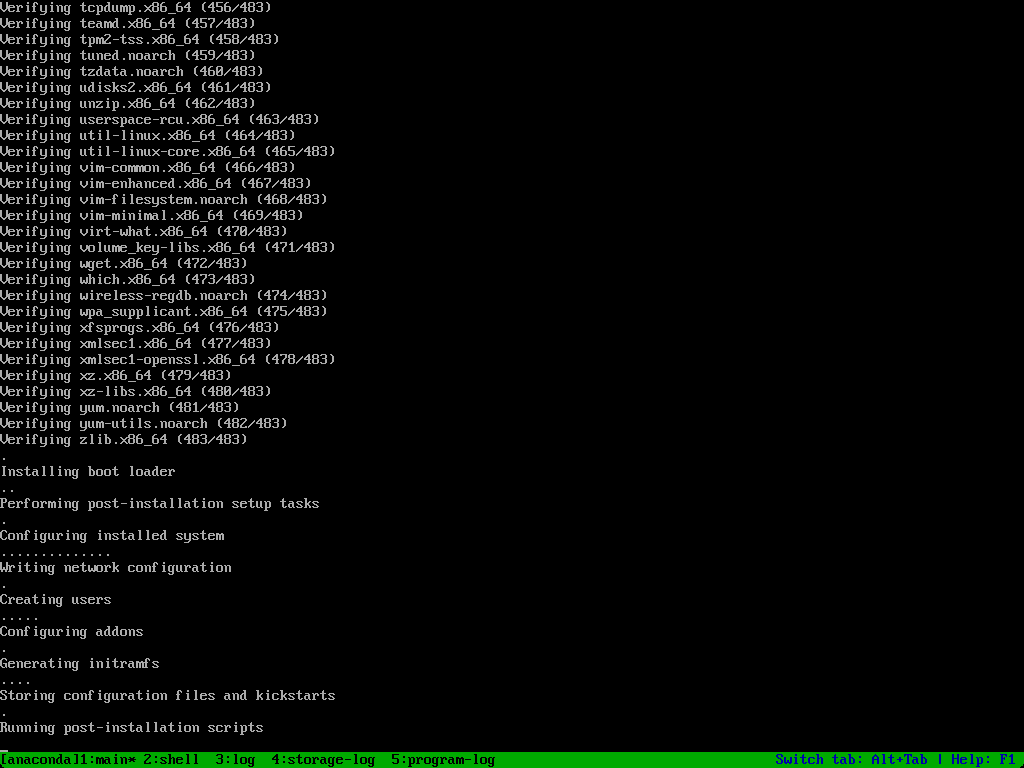
The installation begins.
The post-script installation signals the end of this first phase.
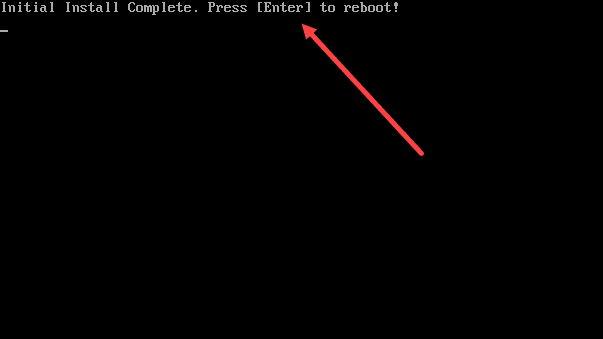
Once the first part of the installation is complete, it will have you hit ENTER.
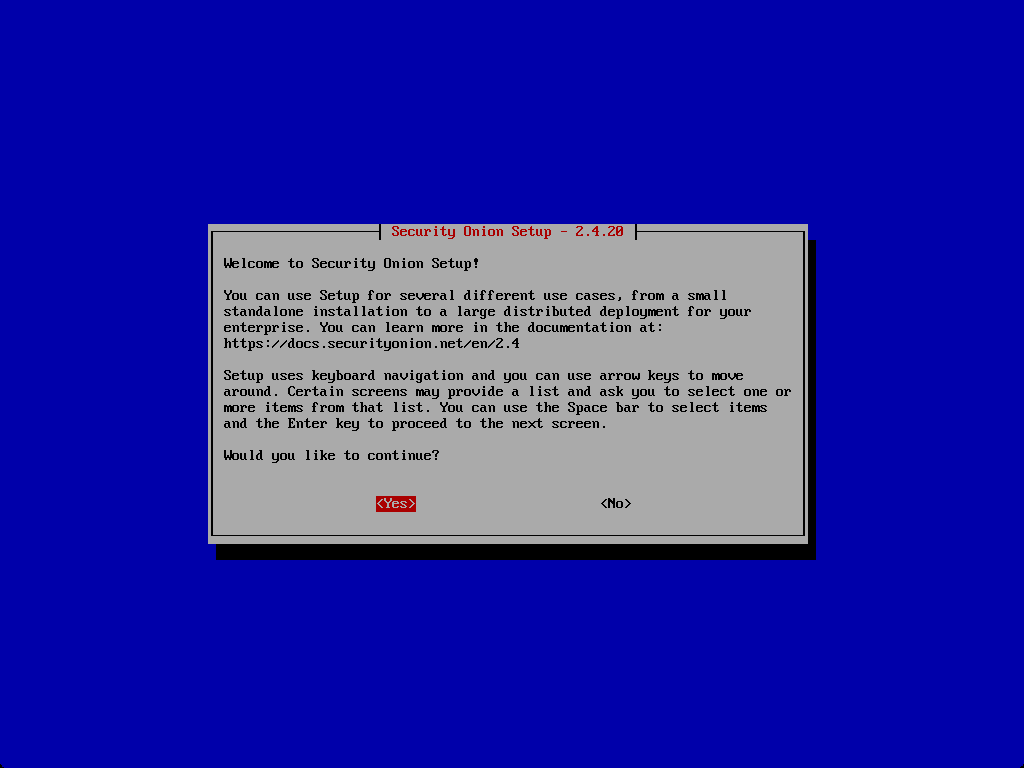
Setup wizard after installing the ISO
There is another Setup wizard of sorts after you install the ISO.
Continue the installation.
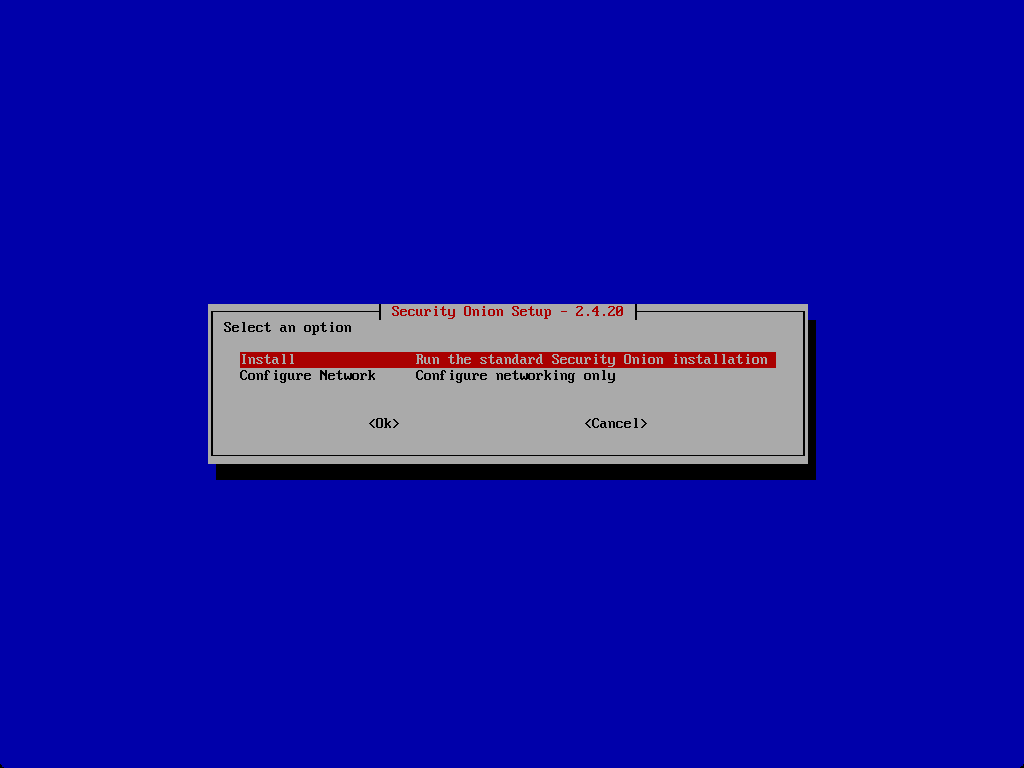
You can begin the install configuration or network configuration if you need to revisit.
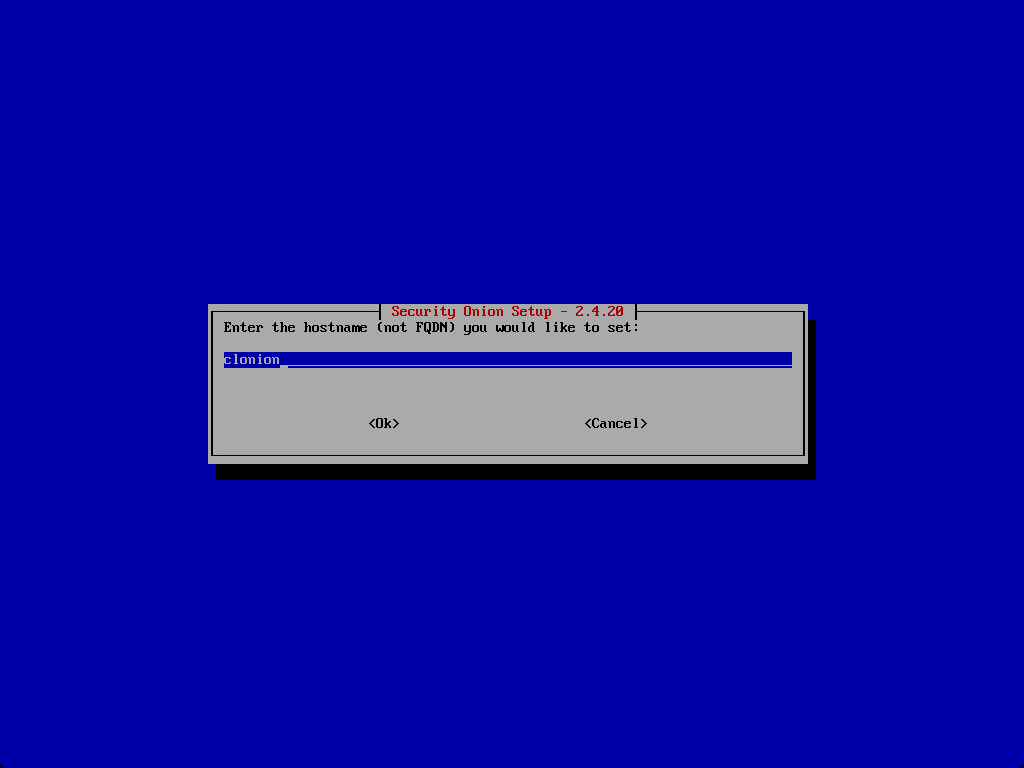
Enter the hostname.
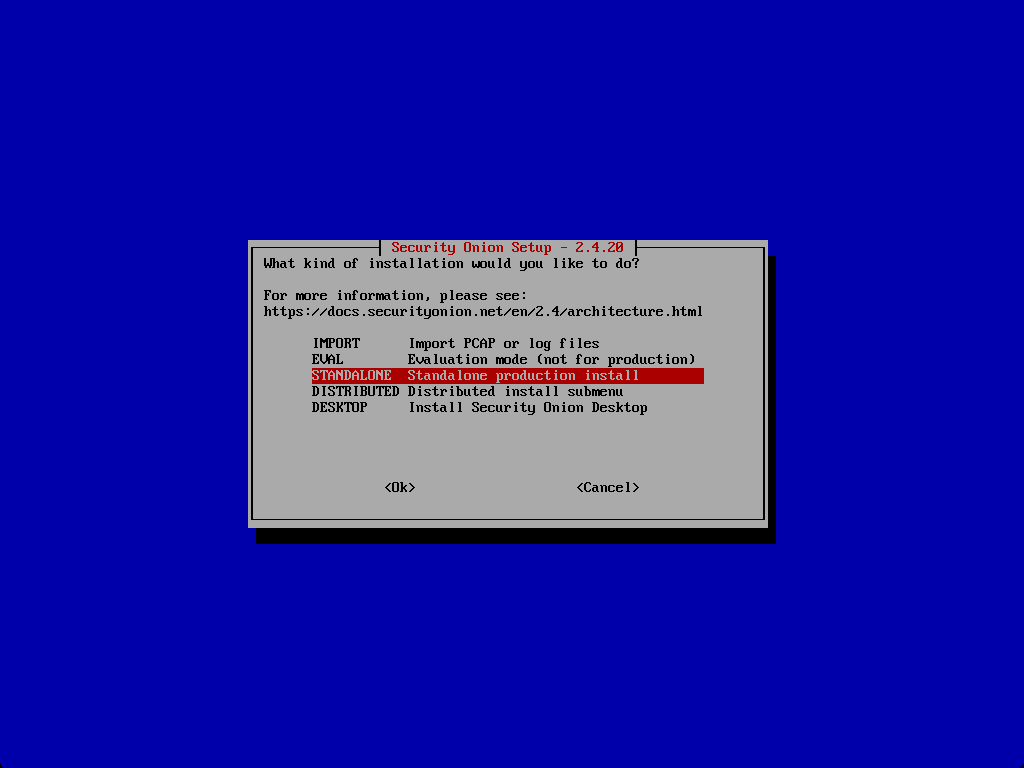
Here I am running the STANDALONE installation.
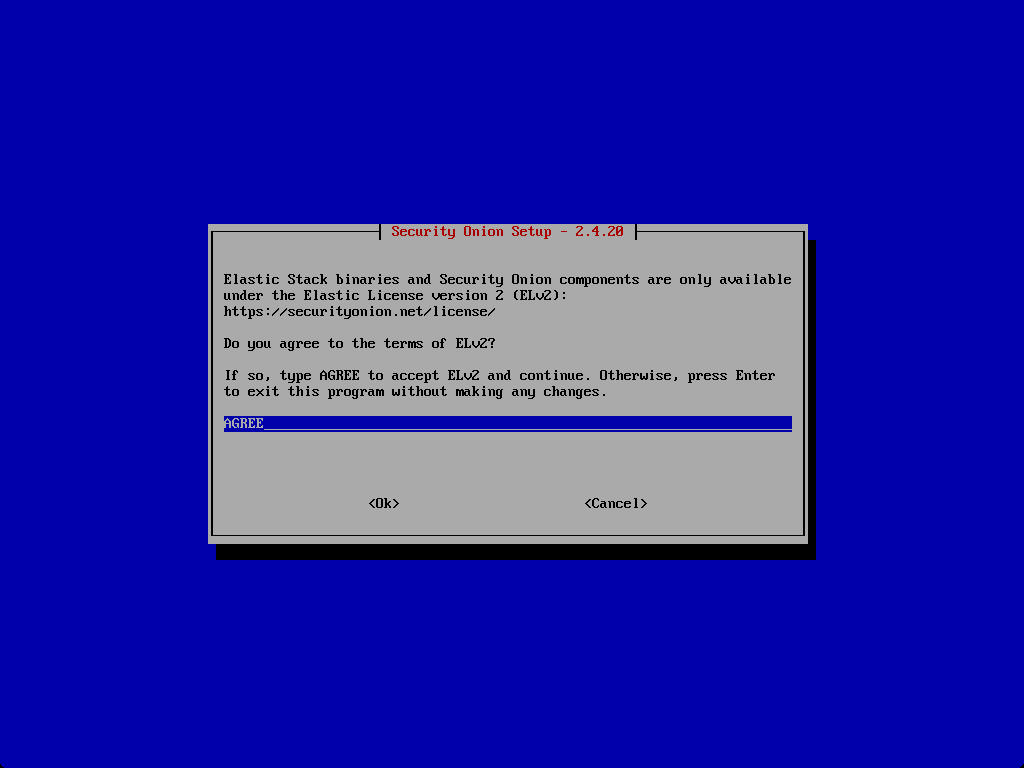
Type AGREE to agree to the EULA for Elastic.
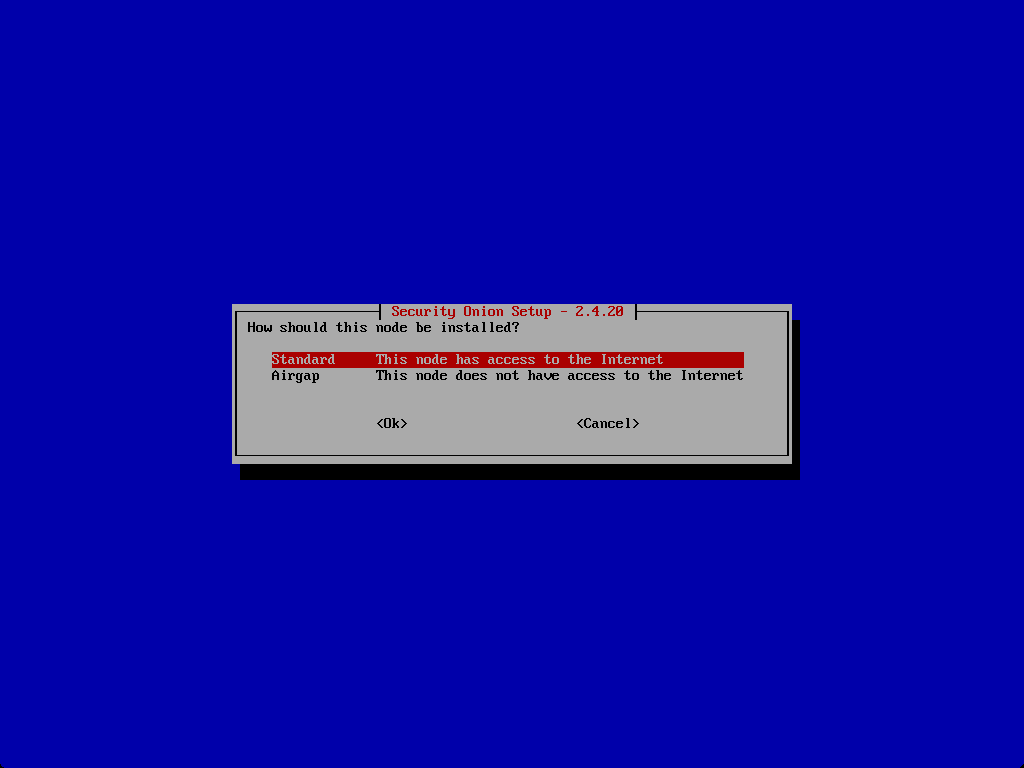
Standard or airgap configuration.
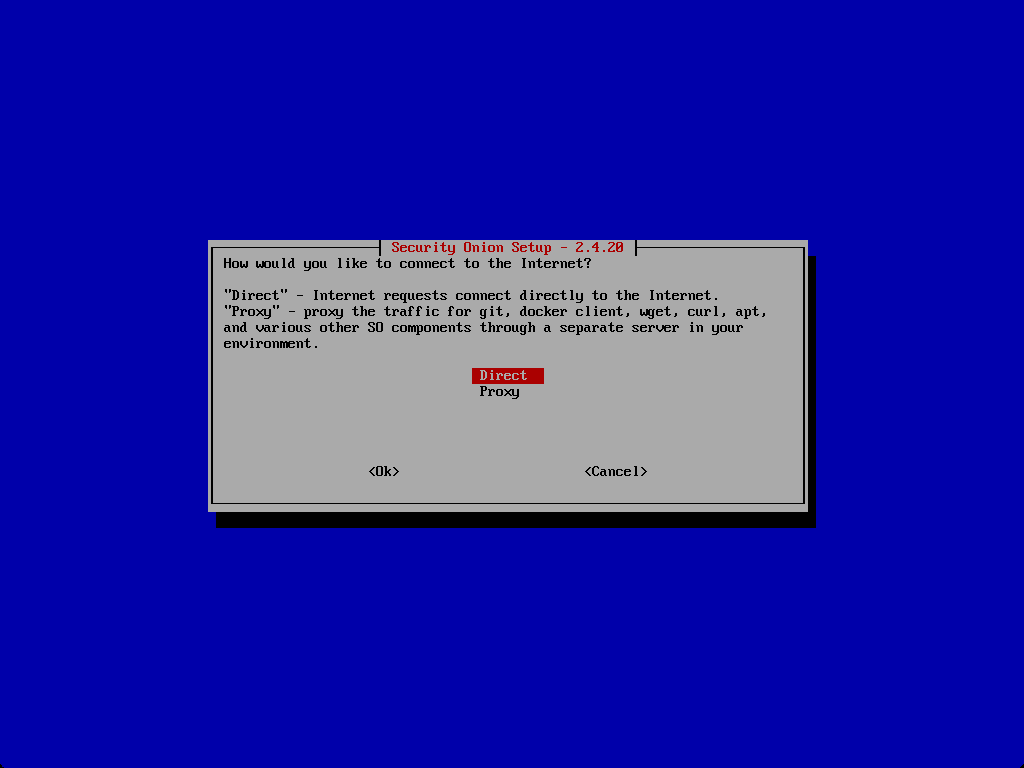
Direct or Proxy connection.
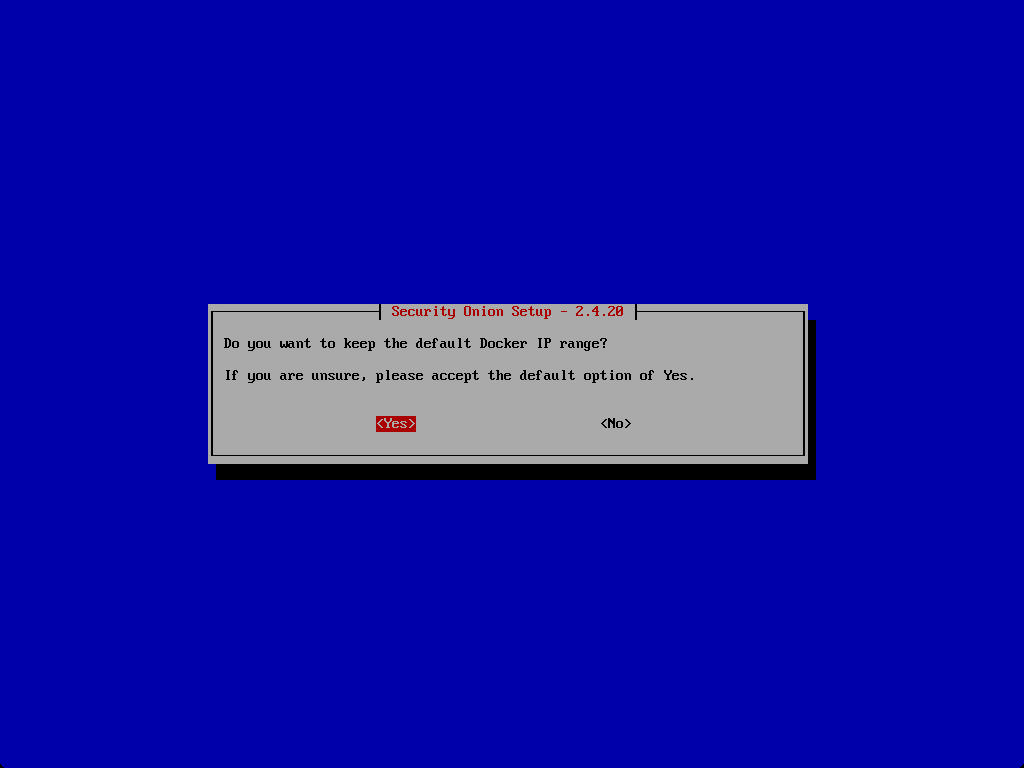
A question on the Docker IP range. It will ask if you want to keep the default IP configuration. The management interface configuration controls and configure the Security Onion console and should be assigned a static IP address to avoid conflicts and ensure consistent access to the web interface.
Configuring the sniffing interface in promiscuous mode also enables it to analyze and monitor all network traffic.
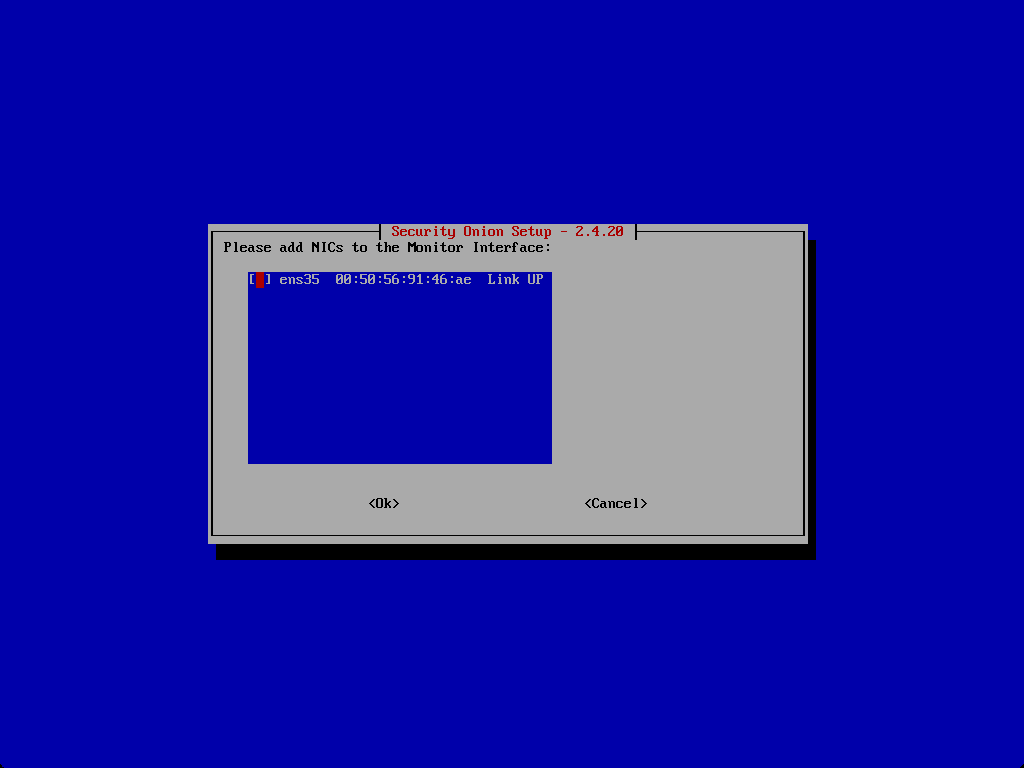
Add NICs to the monitor interface.
Add an IP range to the allowed list of IPs that are allowed to connect in the analyst configuration to manage the Security Onion installation.
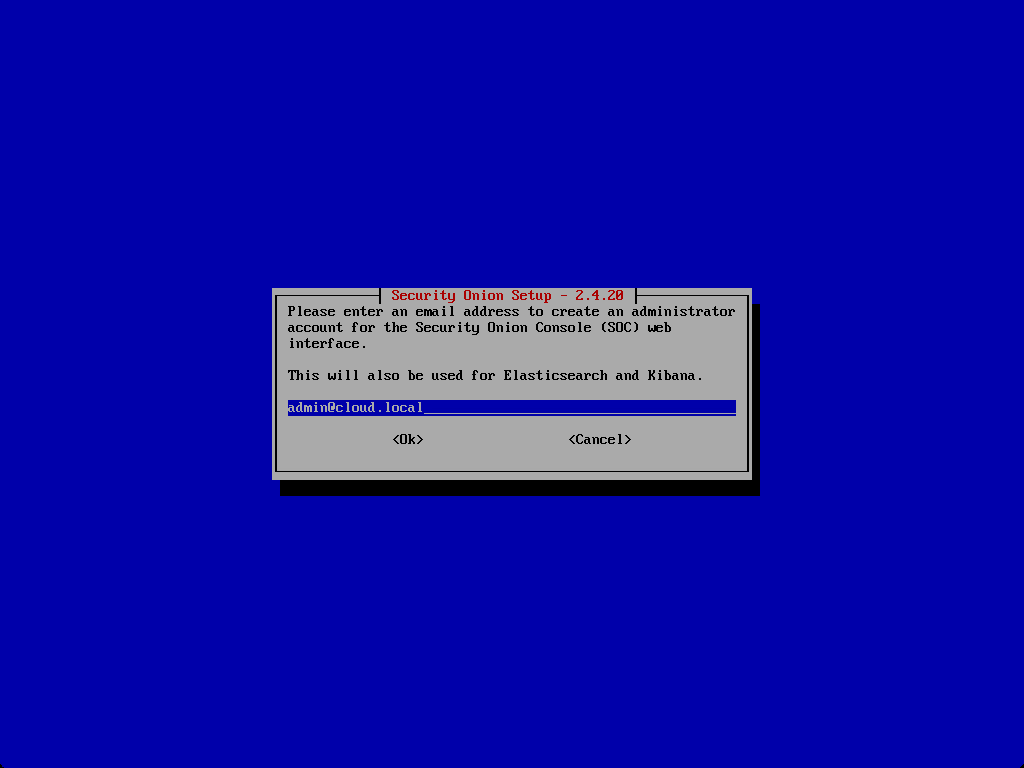
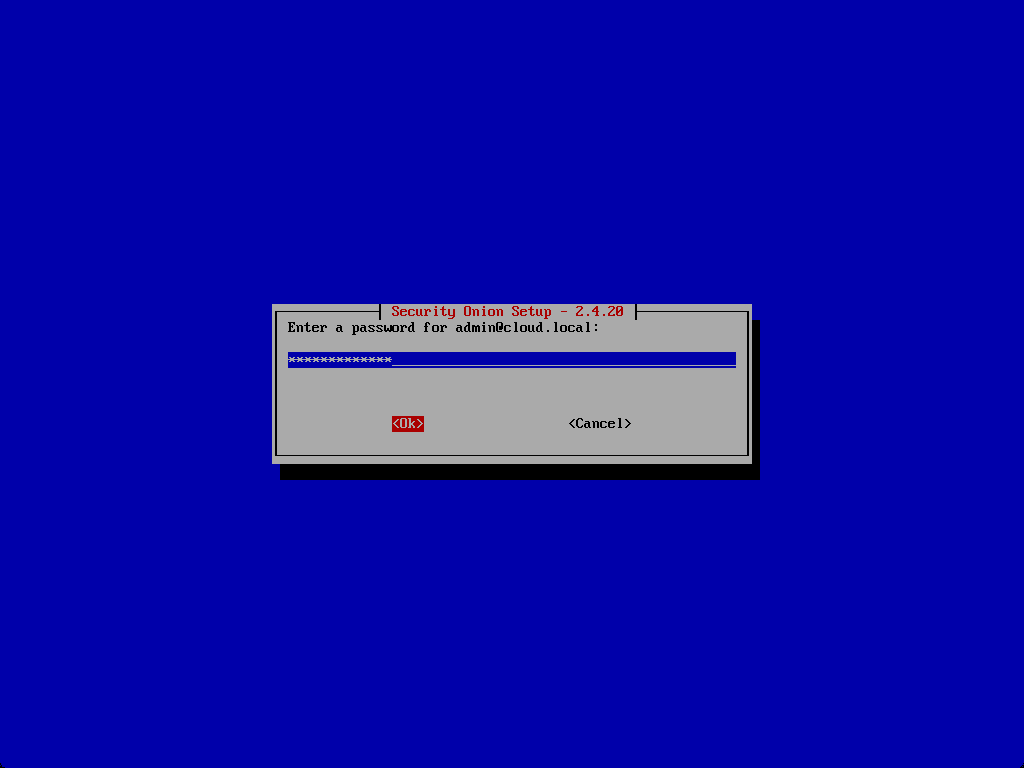
Enter a password for your account configured.
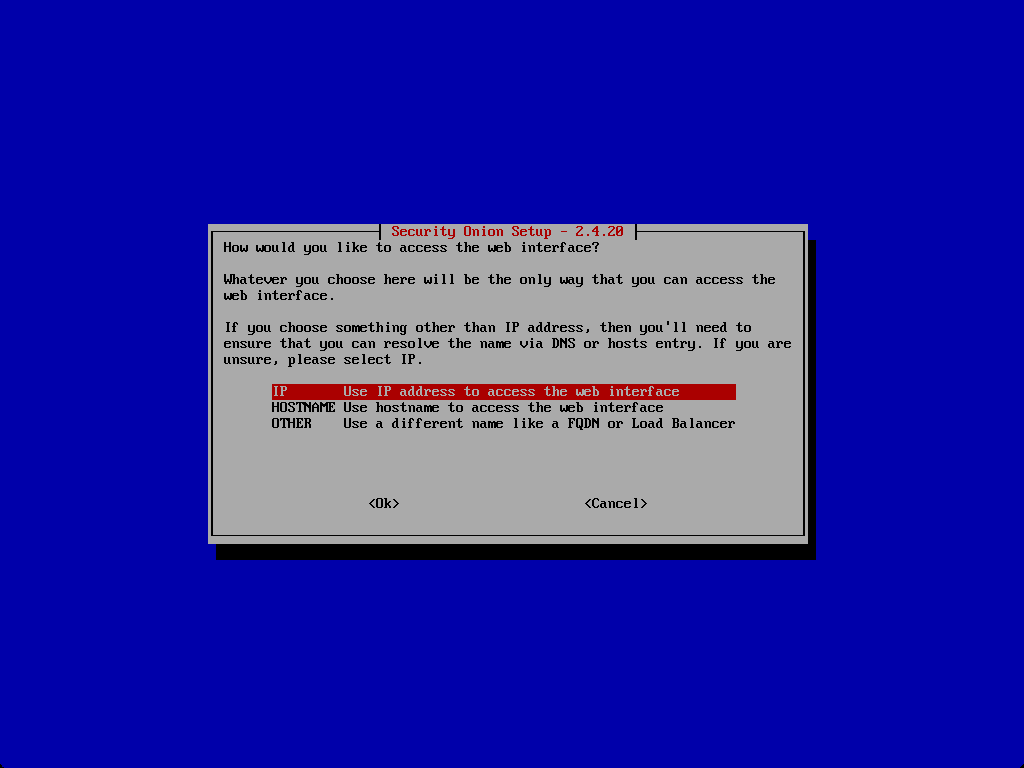
How do you want to connect to the installation.
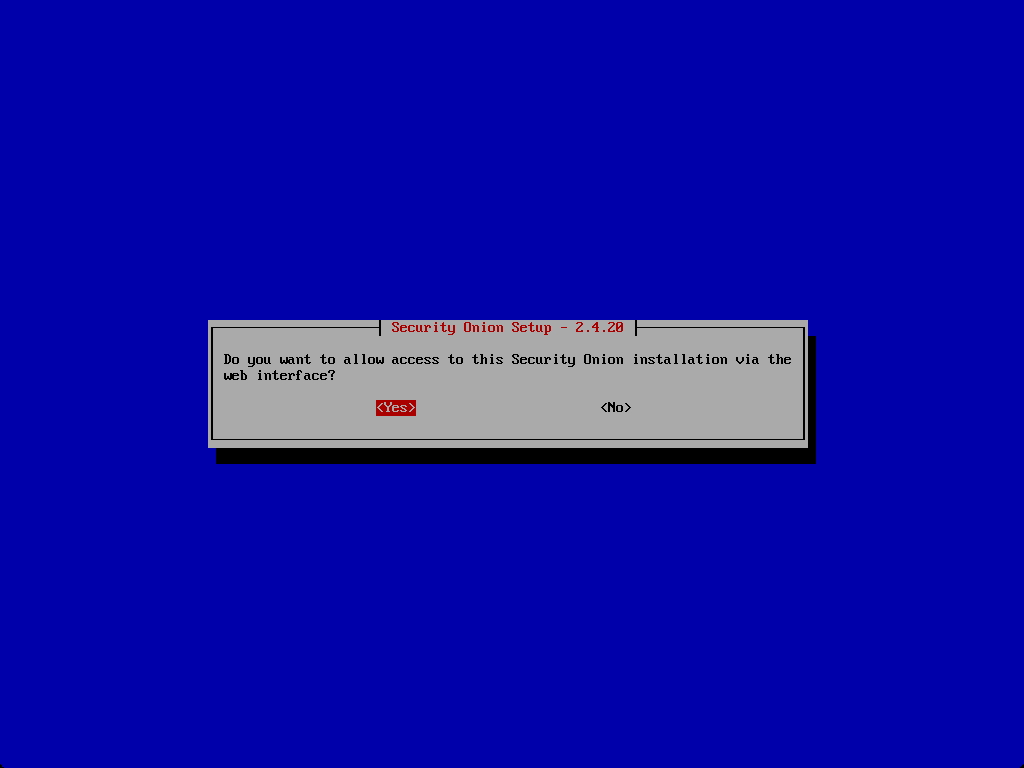
Do you want to allow access to the web interface?
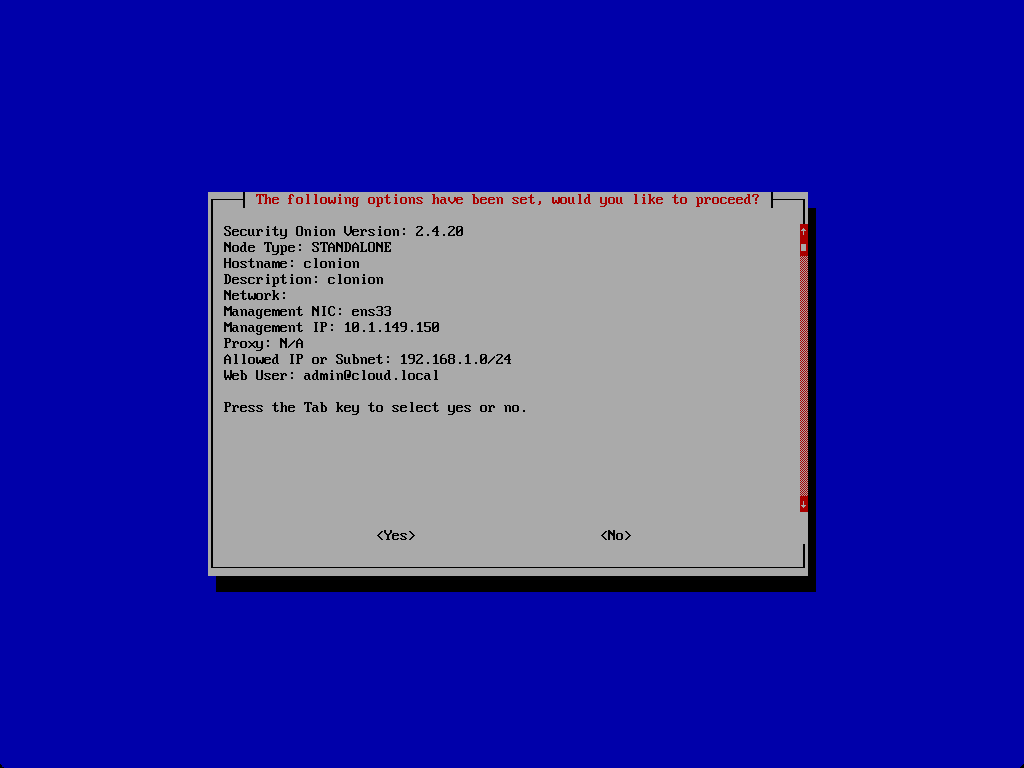
Summary of changes.
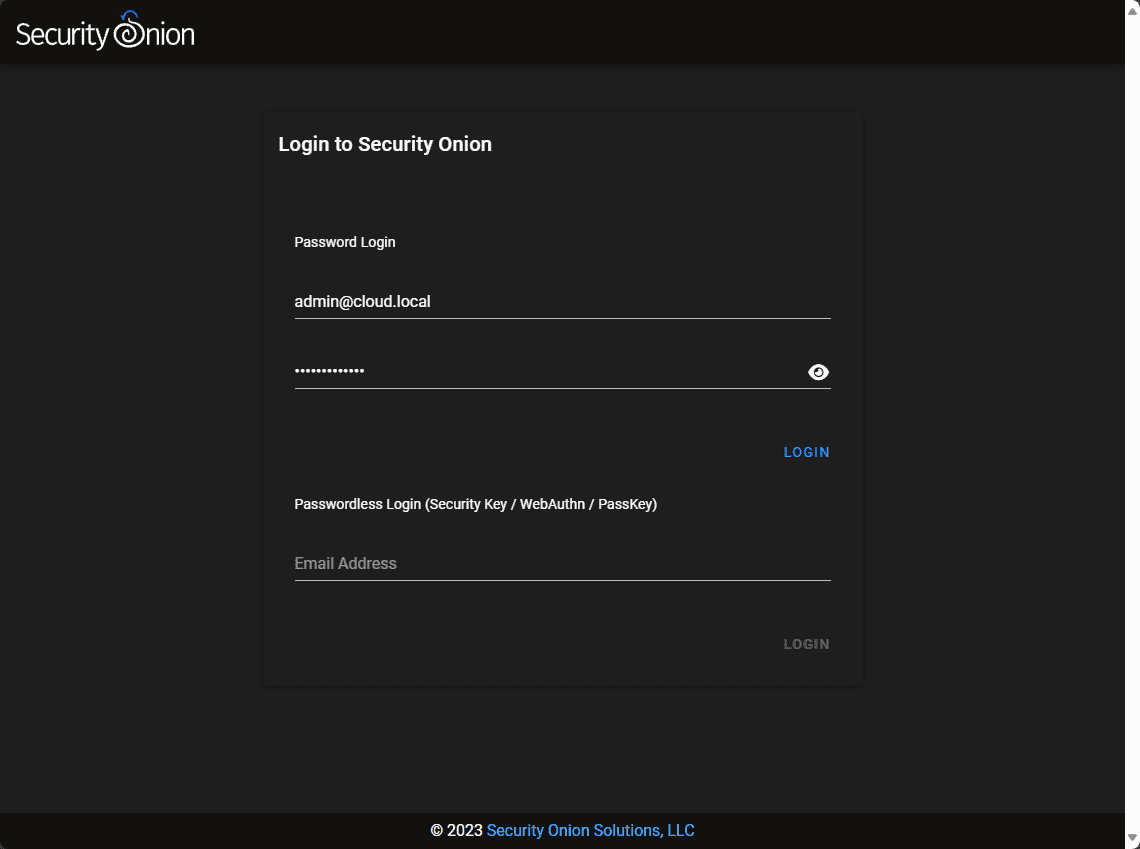
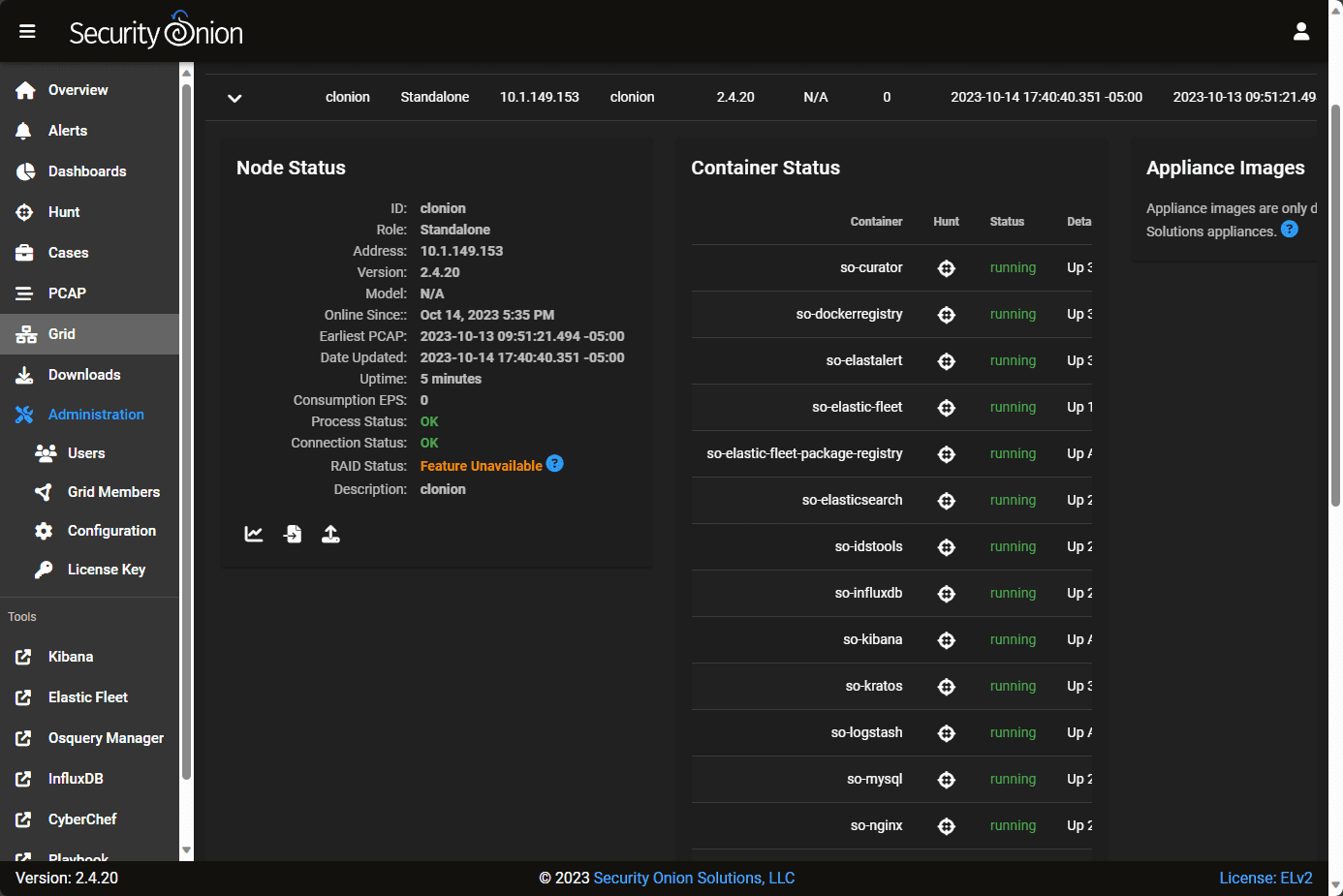
Logging into the Security Onion installation.
On the left-hand side, you will notice you have access to many different tools, including Kibana, Elastic Fleet, Osquery Manager, InfluxDB, CyberChef, Playbooks, etc. On the Grid screen, you can view the configuration of the underlying Security Onion containers.
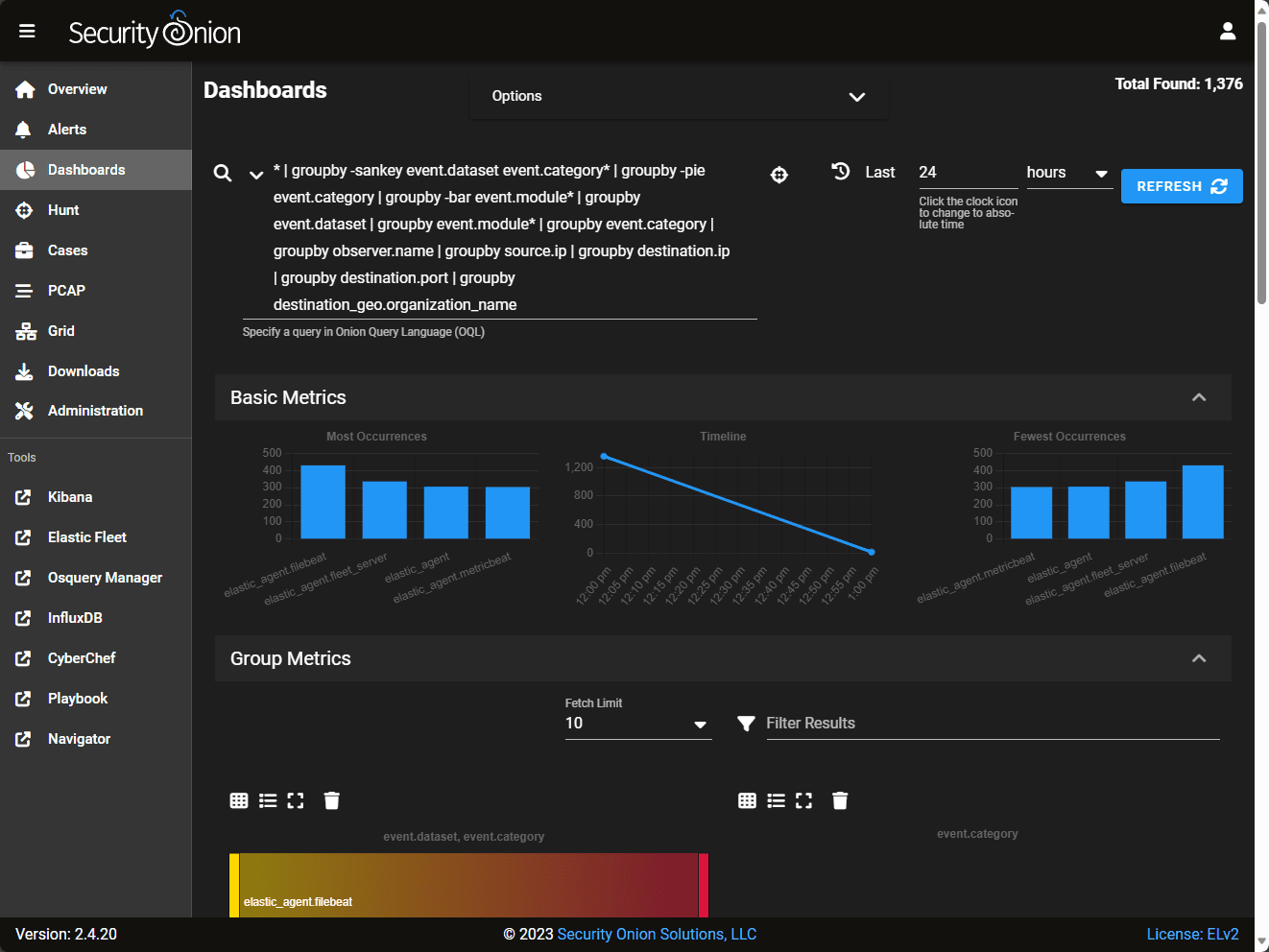
Default dashboards in Security Onion.
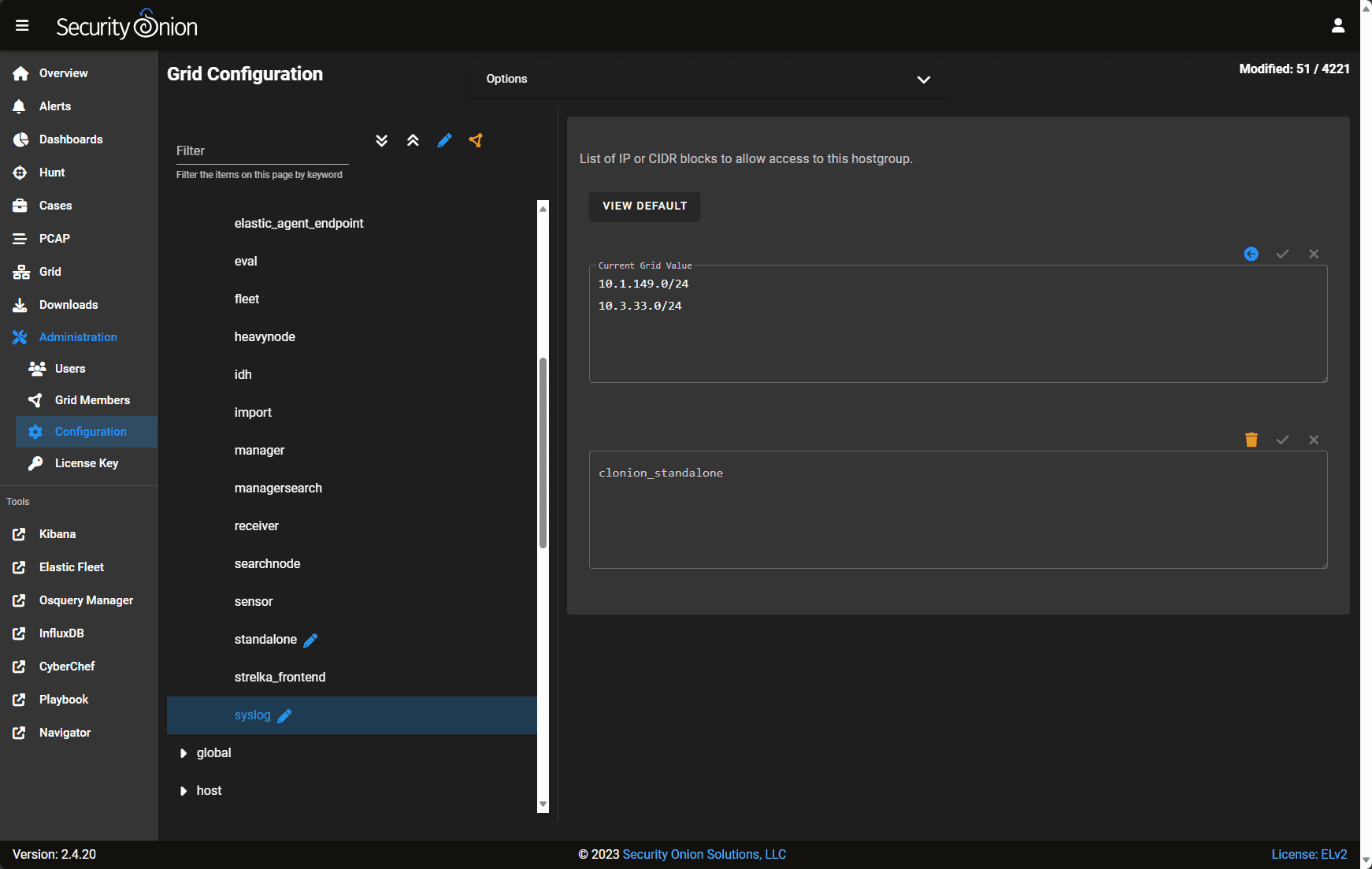
Configuring for Syslog
Adding IP ranges for Syslog is straightforward. You can add your allowed IP ranges under the Administration > Configuration> Firewall > Syslog configuration.
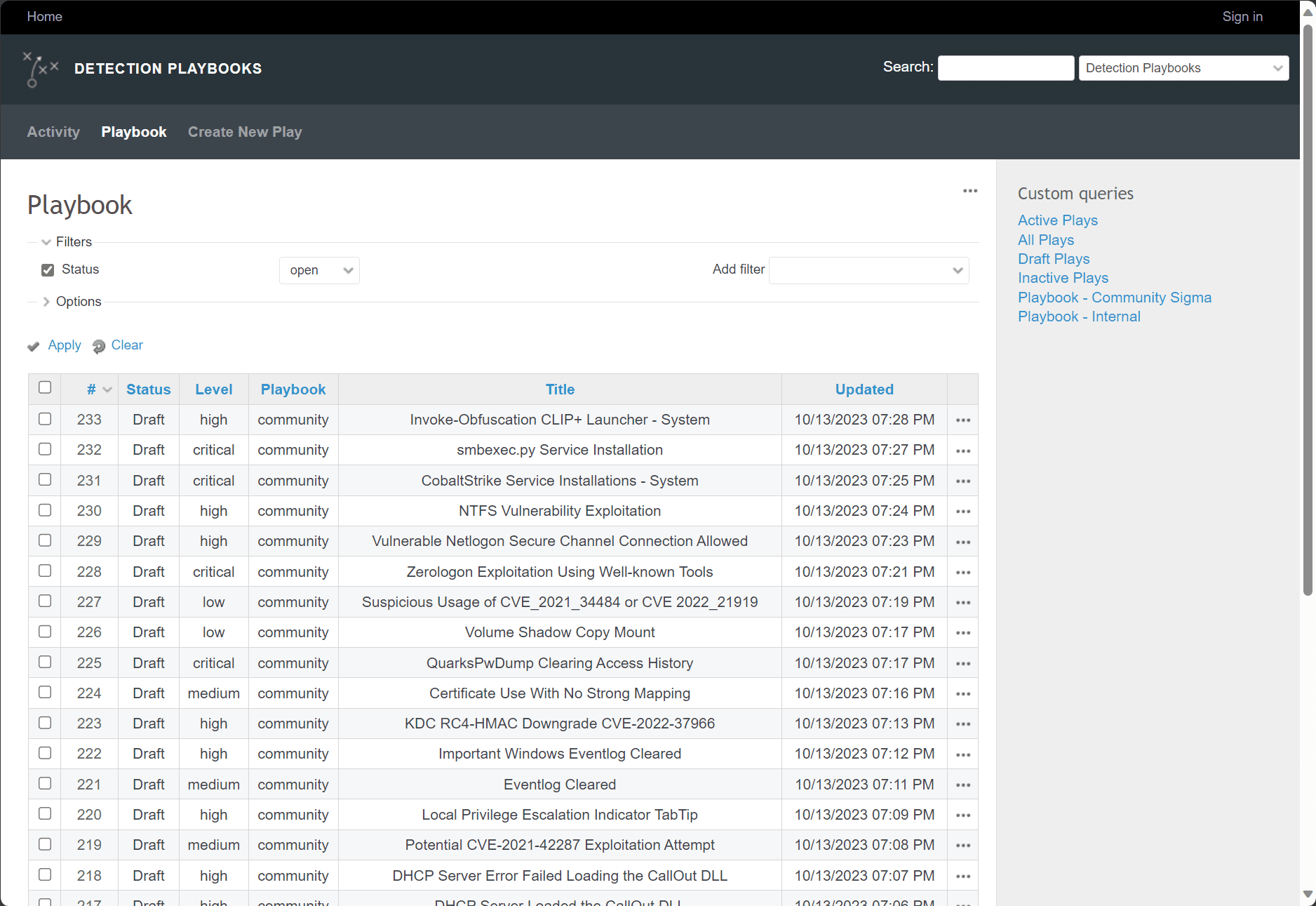
Viewing detection playbooks.
Frequently Asked Questions about Security Onion
How Does Security Onion Ensure Secure Network Configuration?
It provides a detailed guide for network configuration, so the management network and sniffing interface are set up correctly and securely. The management interface is typically configured with a static IP address to maintain consistent access, while the sniffing interface is often set in promiscuous mode to analyze all network traffic.
What Makes Security Onion a Preferred Choice for Security Teams?
Security teams often use SO due to its open-source nature and the full suite of tools it provides for security monitoring and log management. The platform is a free solution and offers various functionalities, such as threat hunting and data analysis, which are crucial for maintaining network security.
Can it be Deployed in a Virtual Machine?
Actually, this is the preferred installation method. Make sure you have a healthy VM configured, though, as it runs a multitude of containers underneath the hood, so good CPU and RAM resources are a must for optimum performance. This allows users to utilize its security tools and services without dedicating physical hardware to the system. Deploying in a VM provides all the benefits of a virtualized environment, including snapshots, backups, etc.
How Does Security Onion Handle Log Management?
Log management in Security Onion is handled in a structured manner, ensuring that log data is stored efficiently accessible, and analyzable when needed. The platform provides tools that allow users to sift through log data, identify patterns, and extract valuable insights, which can be pivotal during incident investigations and when complying with data protection regulations.
What Role Do Docker Containers Play in Security Onion?
Docker containers in Security Onion encapsulate the various security tools and services, providing isolation and minimizing software conflicts. It helps make sure each tool and service runs in a stable environment and does not interfere with the functionality of others, thereby maintaining the integrity and reliability of the security services provided by the platform.
Is Security Onion Suitable for Small Business Networks?
Security Onion is a great platform regardless of the business size. Being free and open source, it is an excellent option for small businesses with limited budgets on cybersecurity solutions.
How Does the Community Contribute to Security Onion’s Development?
The Security Onion community, comprised of users and developers, plays a vital role in its development and evolution. Community members contribute by developing new features, identifying and fixing issues, and sharing knowledge and solutions. This collaborative approach ensures that Security Onion remains up-to-date with the latest security technologies and threats, providing a dynamic and evolving platform for network security.
How Does Security Onion help with threat hunting?
It has many tools as part of the solution that enables security teams to engage in threat hunting proactively. By analyzing network traffic and log data, teams can identify patterns and anomalies that may indicate a security threat.
Can it Integrate with Windows Server Environments?
Yes, it can integrate with Windows Server environments for log management and data analysis. By forwarding Windows logs to Security Onion, teams can analyze and correlate this data with other network activities, providing a complete view of the network environment and enhancing the ability to identify and respond to security incidents.
How Does it Enable Efficient Security Monitoring?
It enables efficient security monitoring by providing real-time network traffic and activity insights. The platform allows teams to set up alerts for specific events or anomalies, allowing them to identify and address potential threats quickly. Additionally, the data collected is stored and can be analyzed to determine trends, patterns, and potential vulnerabilities within the network.
Wrapping up
Security Onion offers many tools and capabilities that fill many different security needs, from intrusion detection to log management. The deployment is straightforward. However, you will want a healthy virtual machine configured with quite a bit of RAM and CPU power for optimal results. I found it easy to get up and running in a VMware vSphere VM with Security Onion and get a basic log management setup. There is a world of things this solution can do. Hopefully, this post will help you get up and running quickly with one of the best and most complete open-source security platforms out there.