Ansible Semaphore: Awesome Open Source Ansible GUI
Ansible is an awesome automation tool that I use in the home lab and production environment regularly. However, sometimes it is nice to have a GUI to point and click around to configure jobs, inventory, etc. Ansible has a commercial product called Ansible Tower and also an open-source product AWX that you can stand up. However, these may be a bit challenging and a little non-intuitive. If you are looking for a great open-source GUI solution for Ansible, Ansible Semaphore is a fantastic Ansible GUI that will likely fit your needs.
Table of contents
- What is Ansible?
- What is Ansible Semaphore Ansible GUI?
- Supported Environments for installation
- Implementing Ansible Playbooks
- Leveraging Job Templates and Access Control in Semaphore
- Semaphore Installation Process
- Ansible Semaphore UI
- Configuring Semaphore for Your First Project
- Frequently Asked Questions
- Automation tools for Home lab
- Wrapping up
What is Ansible?
Ansible is an open-source software tool for automation used widely by system administrators and DevOps engineers across the globe. It’s designed to facilitate the automation of tasks such as software deployment, configuration management, and infrastructure orchestration.
Manual and repetitive system administration tasks can be automated using Ansible, increasing efficiency and reliability in IT environments.
At its core, Ansible utilizes a simple, human-readable language – YAML (Yet Another Markup Language) to define automation jobs in what’s known as Ansible playbooks.
These playbooks guide Ansible on what tasks to execute, making them a fundamental component of the Ansible architecture.
What sets Ansible apart from other automation tools is its agentless design. Instead of installing agent software on remote machines, it leverages existing SSH connections to manage and command remote hosts.
This results in less overhead and fewer security vulnerabilities, offering a more secure solution for managing tasks.
What is Ansible Semaphore Ansible GUI?
Ansible Semaphore project, an open-source alternative to Ansible Tower, provides a web-based user interface for managing Ansible.
The simple task and job templates and the convenience of running Ansible playbooks directly from the UI make Semaphore a top-tier choice for Ansible automation.
It provides an easy way to configure a front-end GUI for your Ansible code, providing additional features, and is relatively easy to use and set up.
You can visit the official site for Ansible Semaphore here: Ansible Semaphore is a modern open-source UI for Ansible (ansible-semaphore.com).
Ansible Semaphore features
Note the following features, including:
Responsive UI
Intuitive UX
Access control for team members
Logging – All activity is recorded in the system. You can easily restore the sequence of events
Notification via telegram or via e-mail
Designed for DevOps in mind with Docker deployment, CI/CD, etc
Separate production and other environments with Build & Deploy functionality
Restore your configuration with Rollback
Pipelines – great integration with git and other DevOps tools
Supported Environments for installation
Ansible Semaphore is supported for installation using the following:
Snap
Package manager
Docker
Binary file
You can check out the details of each of these by visiting the documentation here: Installation – Semaphore Docs (ansible-semaphore.com).
Implementing Ansible Playbooks
Your Ansible playbooks serve as a roadmap for what tasks the remote machines will execute. Creating an inventory file is crucial for running Ansible playbooks, as it defines which hosts to run tasks on. Semaphore provides a convenient way to create and access inventory files during playbook execution.
Running playbooks in Semaphore is quite straightforward. Navigate to the “Playbook Repositories” section and create a new repository. Semaphore allows playbook repositories to be linked with GitHub, offering an easy way to manage your Ansible playbooks.
Leveraging Job Templates and Access Control in Semaphore
Job templates simplify the execution of recurring tasks. Create a job template and specify the playbook, inventory, and SSH private key. The SSH private key will enable a secure connection to the remote machine.
In Semaphore, keys are stored in the “Key Store”. SSH private keys usually allow Semaphore to access your hosts securely. Users can be assigned various tasks and projects, providing a fine-grained access control system.
Semaphore Installation Process
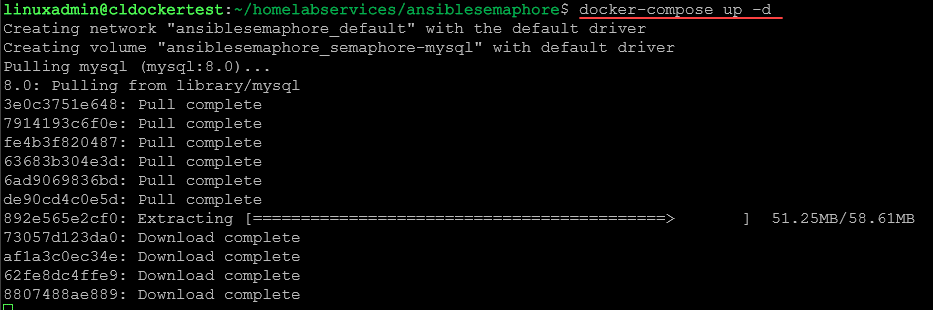
For this walkthrough, we will be using the Ansible Semaphore Docker installation method for installing Ansible Semaphore. Frankly, it is the easiest method to use since you don’t have to worry about any prerequisites aside from Docker and Docker Compose.
Firstly, install Docker and Docker Compose on your system. Run the following command: sudo apt install docker docker-compose. Verify the installation by checking your command line’s Docker and Docker Compose versions.
Below is my Docker Compose file for installing Ansible Semaphore. You will need to replace passwords throughout to customize for your environment.
To generate a password for the SEMAPHORE_ACCESS_KEY_ENCRYPTION stanza, use the command: head -c32 /dev/urandom | base64.
services:
# uncomment this section and comment out the mysql section to use postgres instead of mysql
#postgres:
#restart: unless-stopped
#ports:
#- 5432:5432
#image: postgres:14
#hostname: postgres
#volumes:
# - semaphore-postgres:/var/lib/postgresql/data
#environment:
# POSTGRES_USER: semaphore
# POSTGRES_PASSWORD: semaphore
# POSTGRES_DB: semaphore
# if you wish to use postgres, comment the mysql service section below
mysql:
restart: unless-stopped
ports:
- 3306:3306
image: mysql:8.0
hostname: mysql
volumes:
- semaphore-mysql:/var/lib/mysql
environment:
MYSQL_RANDOM_ROOT_PASSWORD: 'yes'
MYSQL_DATABASE: semaphore
MYSQL_USER: semaphore
MYSQL_PASSWORD: 'semaphore'
semaphore:
restart: unless-stopped
ports:
- 3000:3000
image: semaphoreui/semaphore:latest
environment:
SEMAPHORE_DB_USER: semaphore
SEMAPHORE_DB_PASS: 'semaphore'
SEMAPHORE_DB_HOST: mysql # for postgres, change to: postgres
SEMAPHORE_DB_PORT: 3306 # change to 5432 for postgres
SEMAPHORE_DB_DIALECT: mysql
SEMAPHORE_DB: semaphore
SEMAPHORE_PLAYBOOK_PATH: /tmp/semaphore/
SEMAPHORE_ADMIN_PASSWORD: changeme
SEMAPHORE_ADMIN_NAME: admin
SEMAPHORE_ADMIN_EMAIL: [email protected]
SEMAPHORE_ADMIN: admin
SEMAPHORE_ACCESS_KEY_ENCRYPTION: gs72mPntFATGJs9qK0pQ0rKtfidlexiMjYCH9gWKhTU=
SEMAPHORE_LDAP_ACTIVATED: 'no' # if you wish to use ldap, set to: 'yes'
SEMAPHORE_LDAP_HOST: dc01.local.example.com
SEMAPHORE_LDAP_PORT: '636'
SEMAPHORE_LDAP_NEEDTLS: 'yes'
SEMAPHORE_LDAP_DN_BIND: 'uid=bind_user,cn=users,cn=accounts,dc=local,dc=shiftsystems,dc=net'
SEMAPHORE_LDAP_PASSWORD: 'ldap_bind_account_password'
SEMAPHORE_LDAP_DN_SEARCH: 'dc=local,dc=example,dc=com'
SEMAPHORE_LDAP_SEARCH_FILTER: "(u0026(uid=%s)(memberOf=cn=ipausers,cn=groups,cn=accounts,dc=local,dc=example,dc=com))"
depends_on:
- mysql # for postgres, change to: postgres
volumes:
semaphore-mysql: # to use postgres, switch to: semaphore-postgresThen, run a docker-compose up -d.
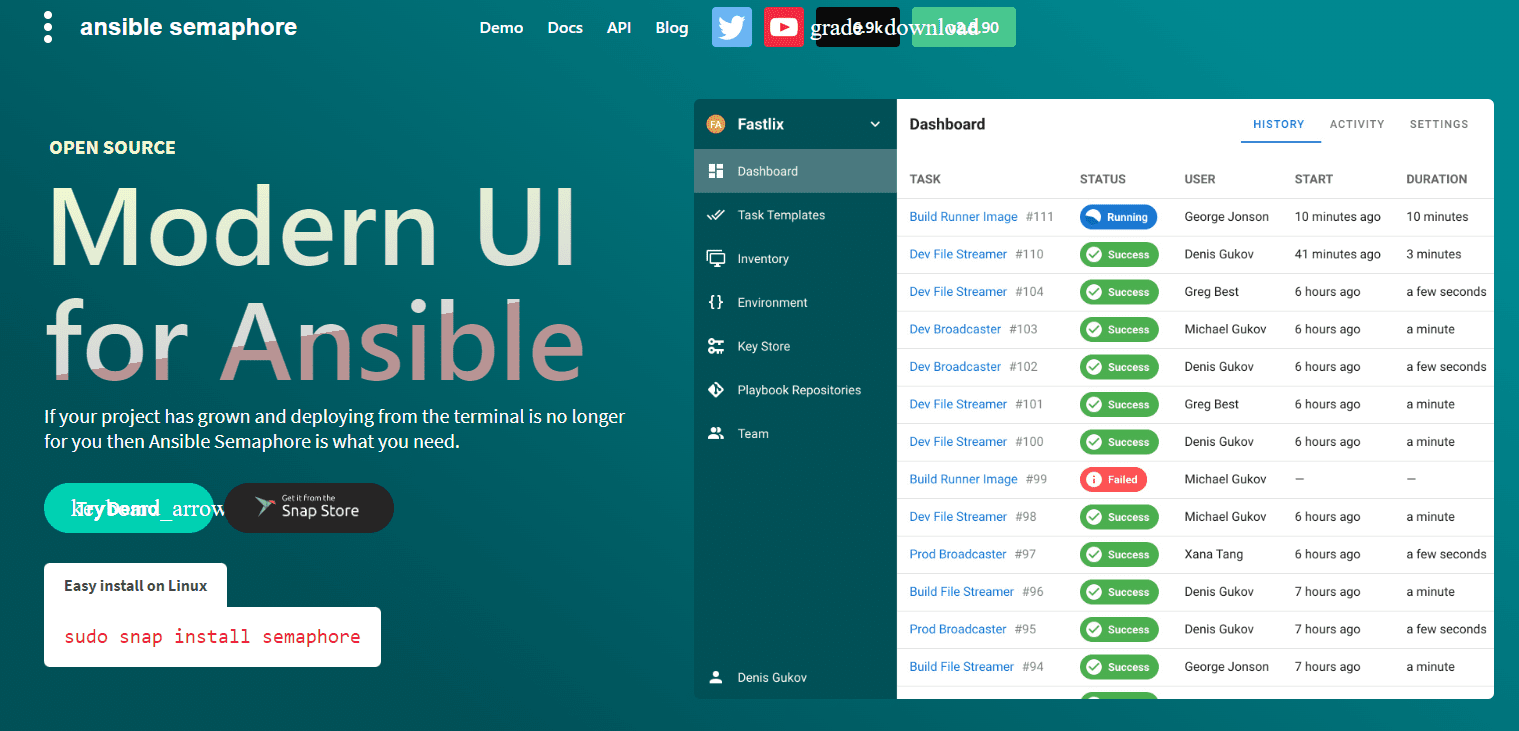
Ansible Semaphore UI
The UI is amazing, has a very modern feel, and is intuitive. Even though I hadn’t used the solution before, I felt at home with the menus and could easily find my way around.
You will see the menus on the left-hand side:
Task Templates – This is where you setup simple task template you want to run playbooks
Inventory – Configure your inventory. This is the list of machines against which you want to run the Ansible tasks
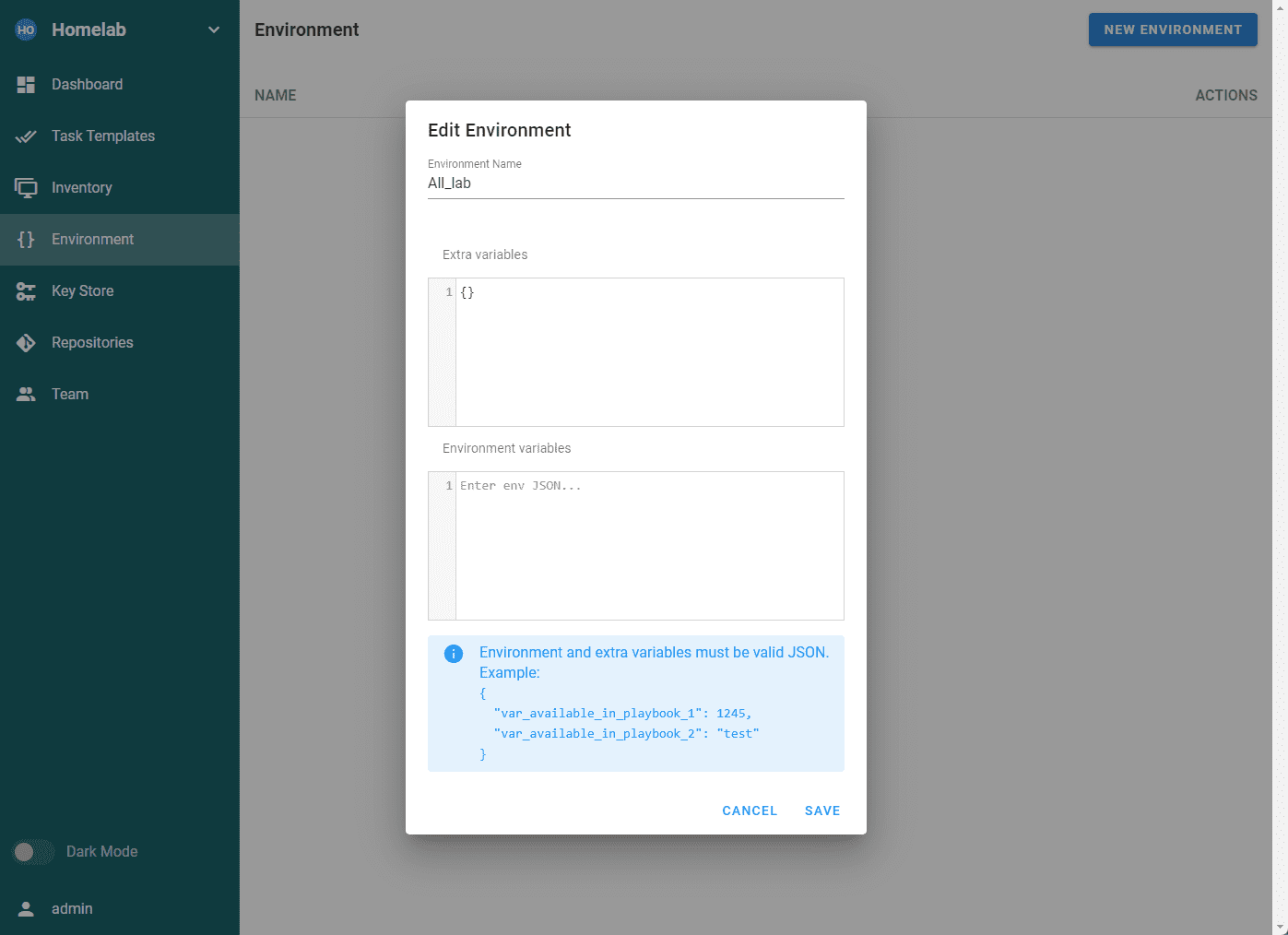
Environment – This is specific to Semaphore. It is a place to store additional environment variables for an inventory, stored in JSON format. All task templates require an environment to be defined, even if it is empty.
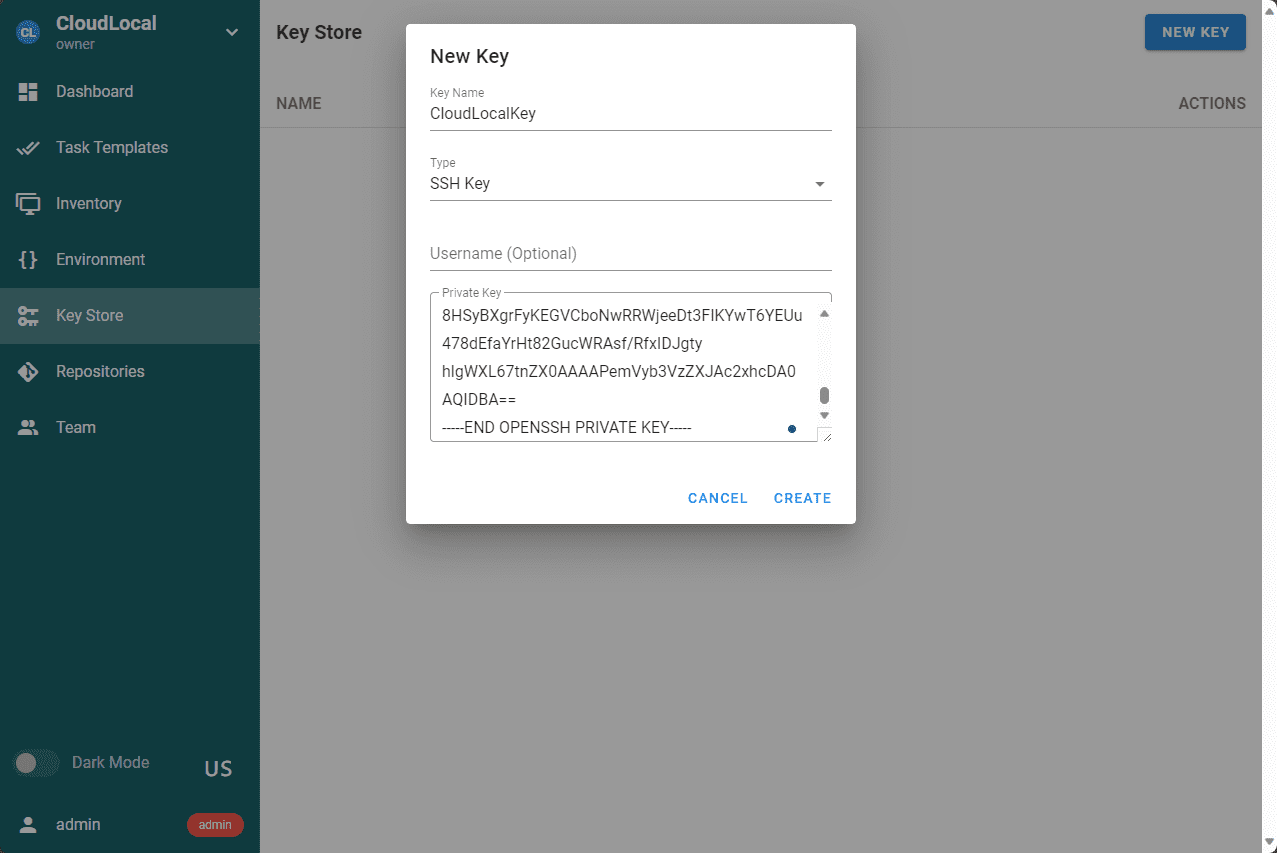
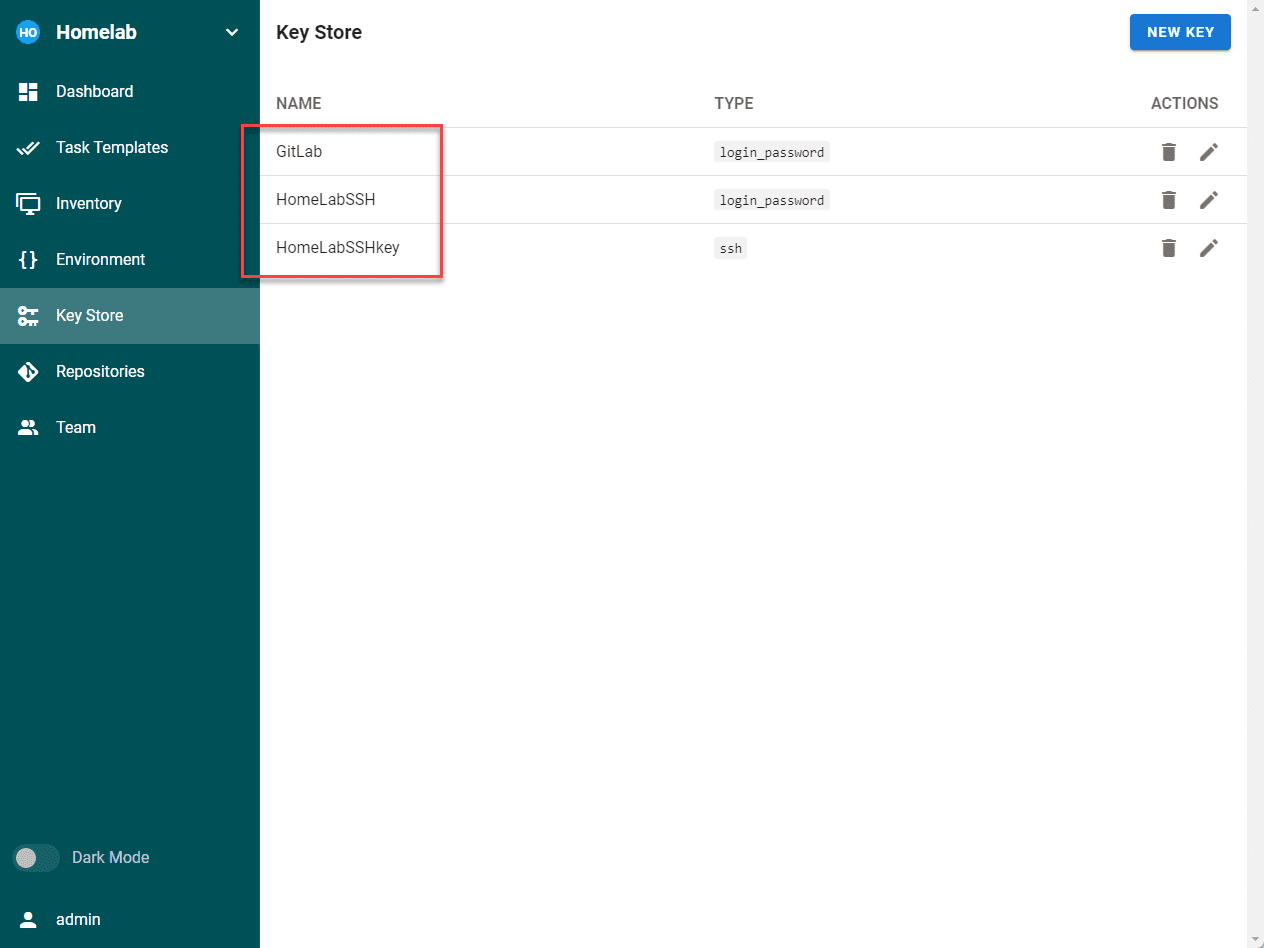
Key Store – The Key Store in Semaphore stores credentials for accessing remote Repositories, remote hosts, sudo credentials, and Ansible vault passwords.
Repositories – Connect to your Git repository. This is required as it pulls your playbooks and roles from your repo
Team – Configuration for access control
Configuring Semaphore for Your First Project
To configure Semaphore, access its UI in your browser and set up the system. Create a new user and set up a secure solution with a password. Use this to log into Semaphore’s dashboard. From the user interface, initiate your first project.
Create your User Credentials
Navitage to Key Store and create your user credentials as you will need these in the other configurations. Add your credentials to the keystone. I have added my Git credentials and SSH password and SSH key.
Below, i have added a few credentials I will need to configure Semaphore.
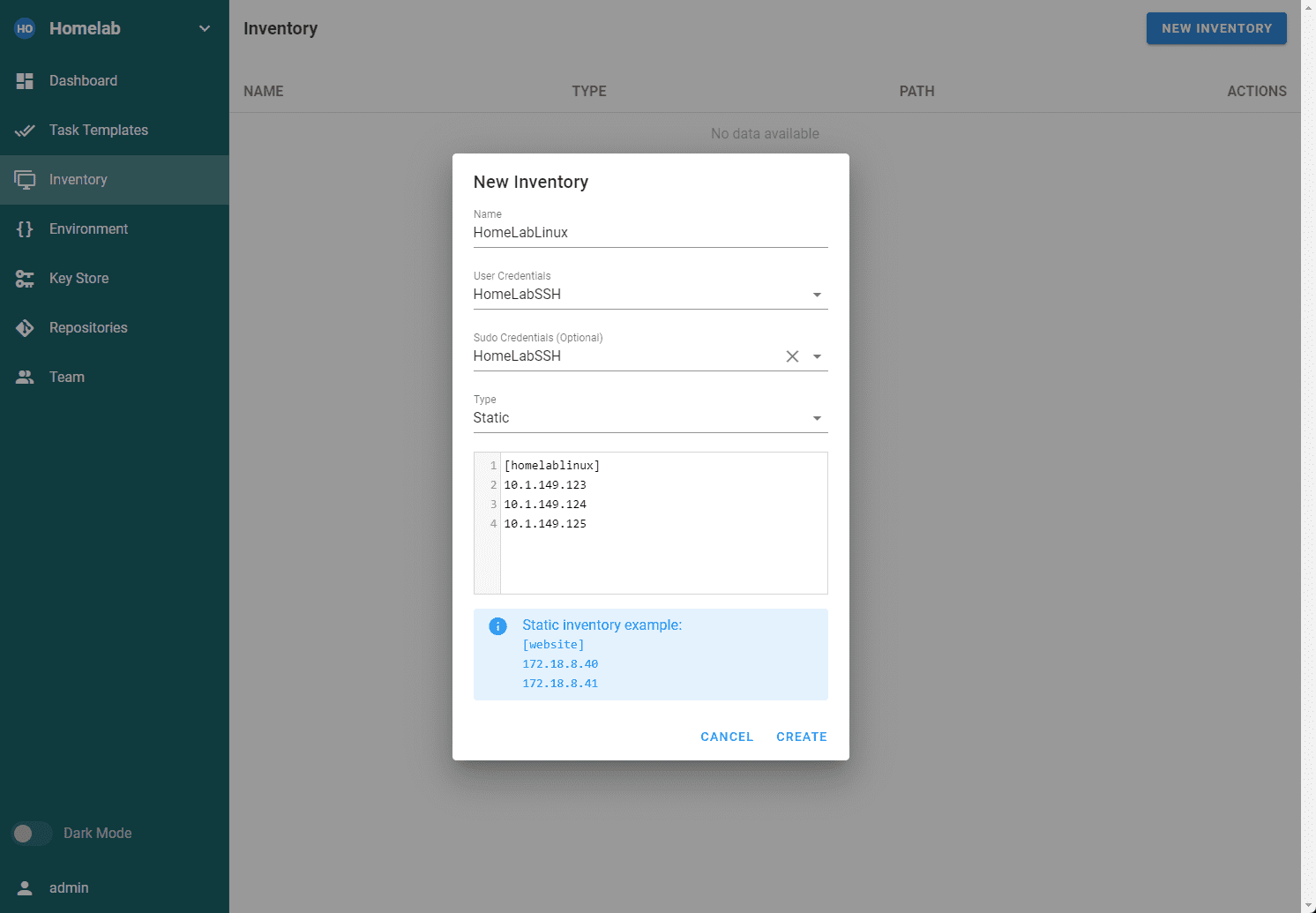
Create your inventory
Navigate to Inventory > New Inventory. Ansible Semaphore makes it easy to start configuring your Ansible inventory. You have three choices here:
Static
Static YAML
File
The Static option is super easy and allows you to store the inventory right in the configuration window, as shown below.
Create a new environment
Create the environment. If you don’t want to add any additional environment variables, you can just enter the following:
{}Add a Git repository
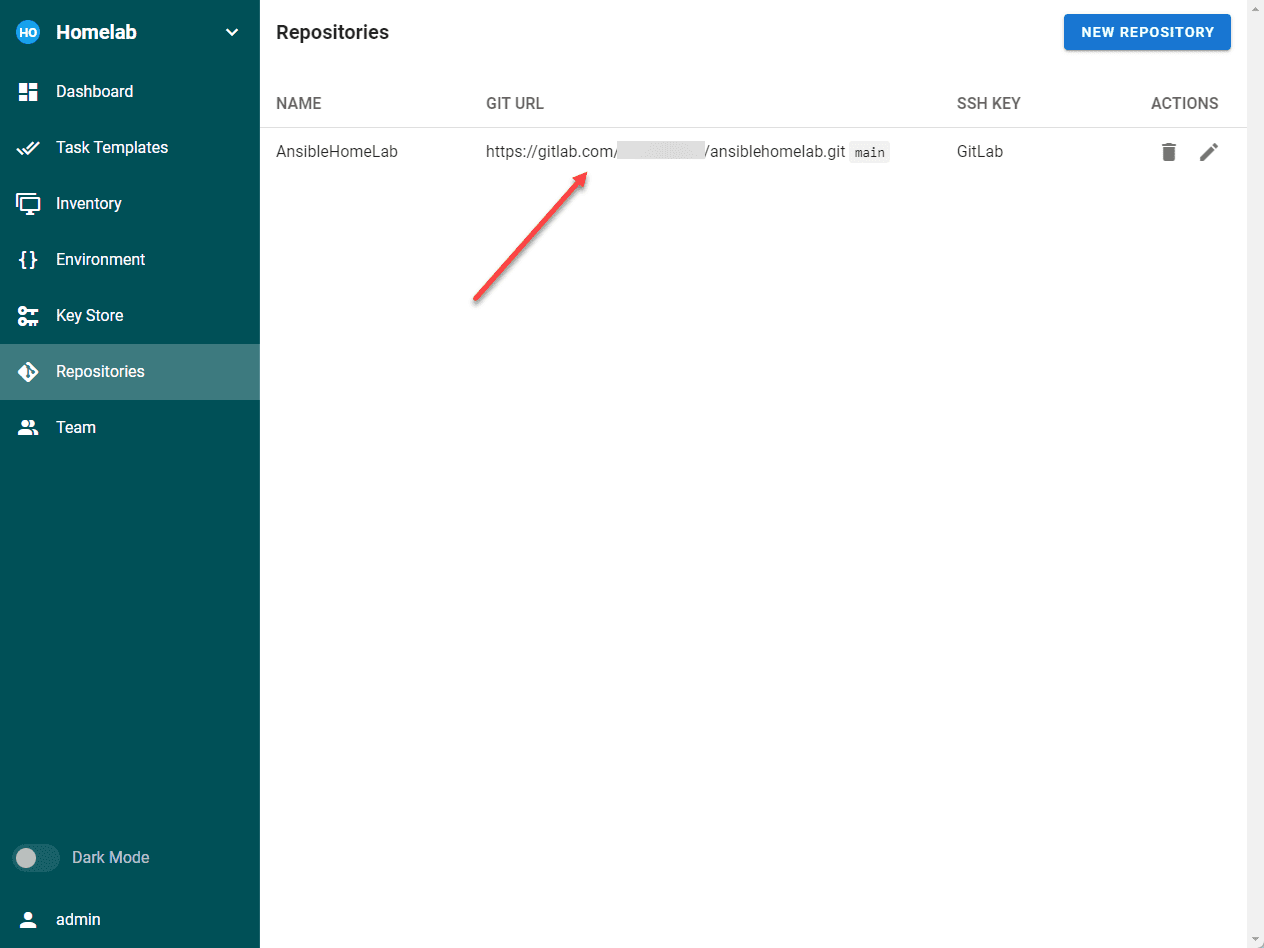
Add your Git repository.
Create your playbooks and sync these with your Git repo
Before creating the Task Template, we need to create playbooks for the task templates. Create a new repository in your Git repository of choice. I am using Gitlab, so I have created a new AnsibleHomeLab repo.
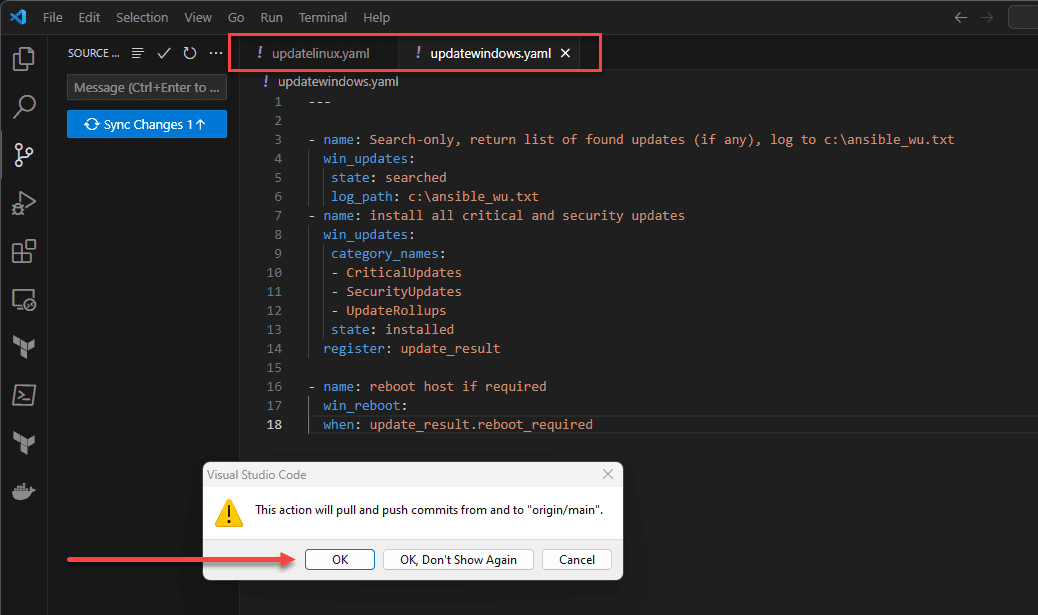
Clone down your repo and create your new playbooks in VS Code or your favorite code editor. Commit and synchronize your changes to your repo. This is where Ansible Semaphore will pull the playbooks and any roles you have configured.
A simple Linux Update Ansible Playbook may look like this:
---
- hosts: all
vars:
ansible_host_key_checking: false ##If you get an error about hosts not trusted
become: true
tasks:
- name: Update and upgrade apt packages
apt:
update_cache: yes
upgrade: yesBelow is a Windows playbook as well that I am synchronizing with Gitlab.
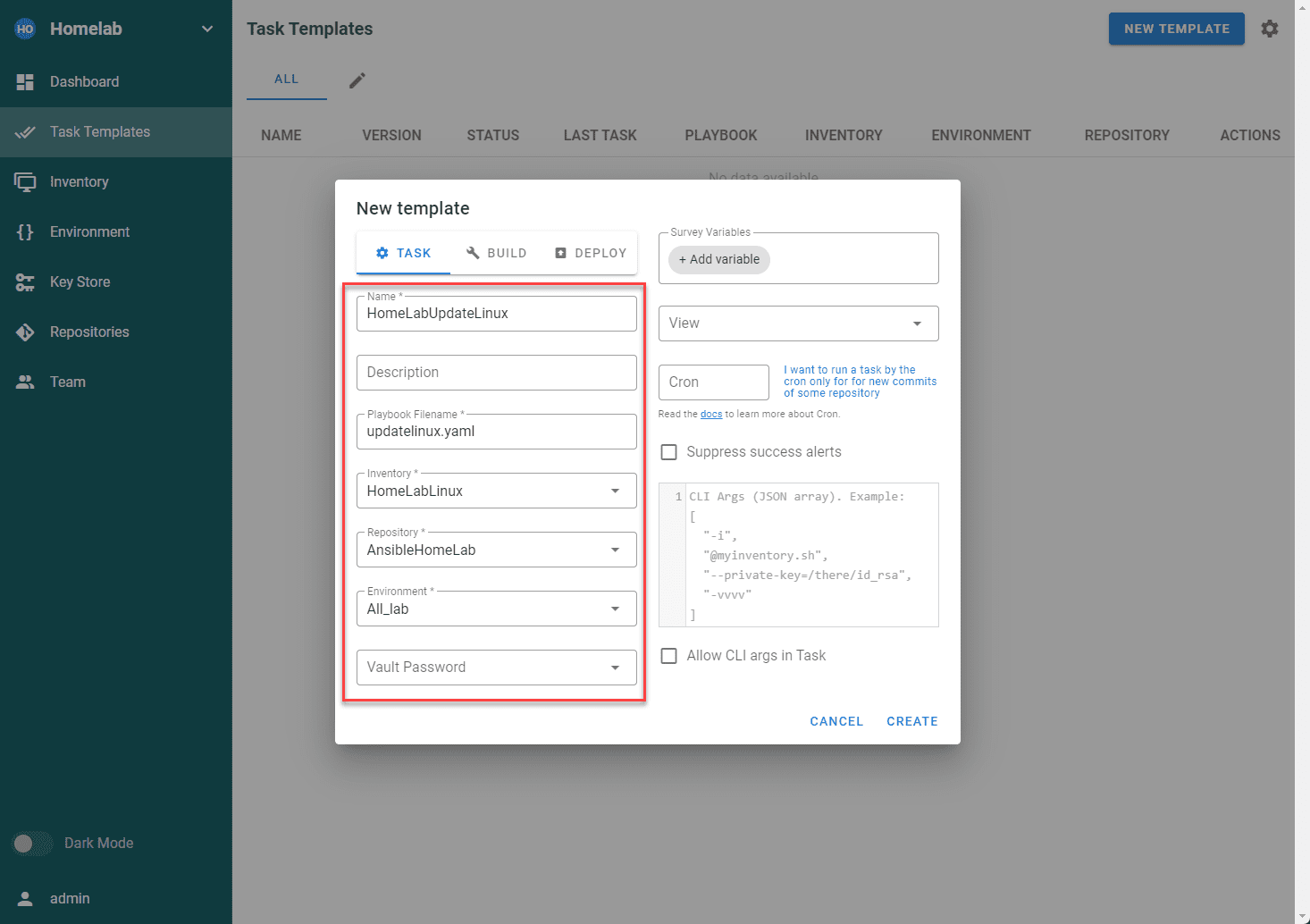
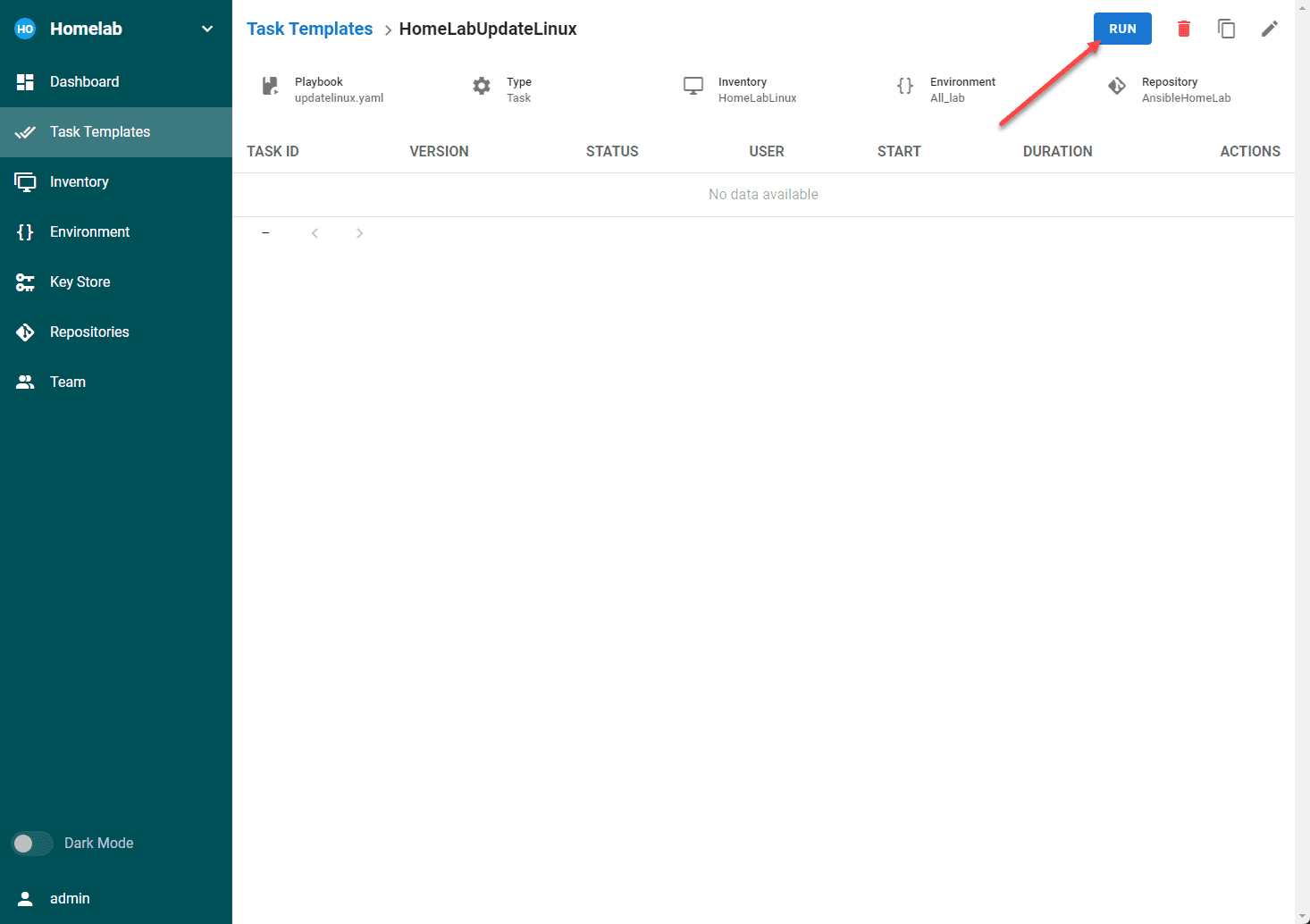
Now, we can configure our new Task Template. We can populate all the other areas configured in the template as we have configured these already. The Vault configuration is not mandatory.
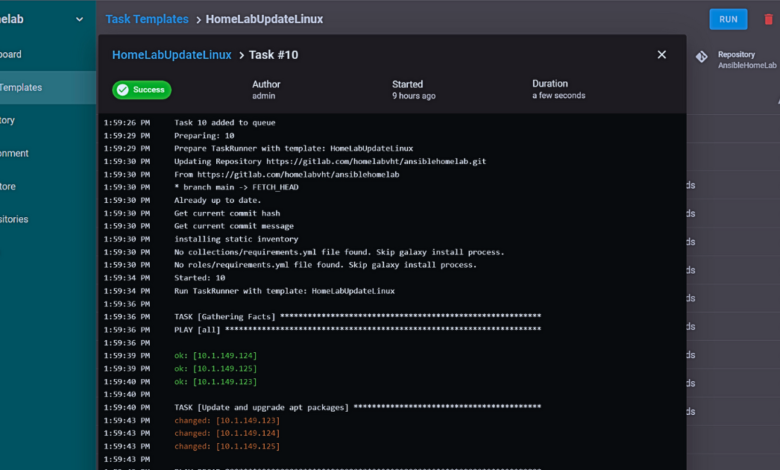
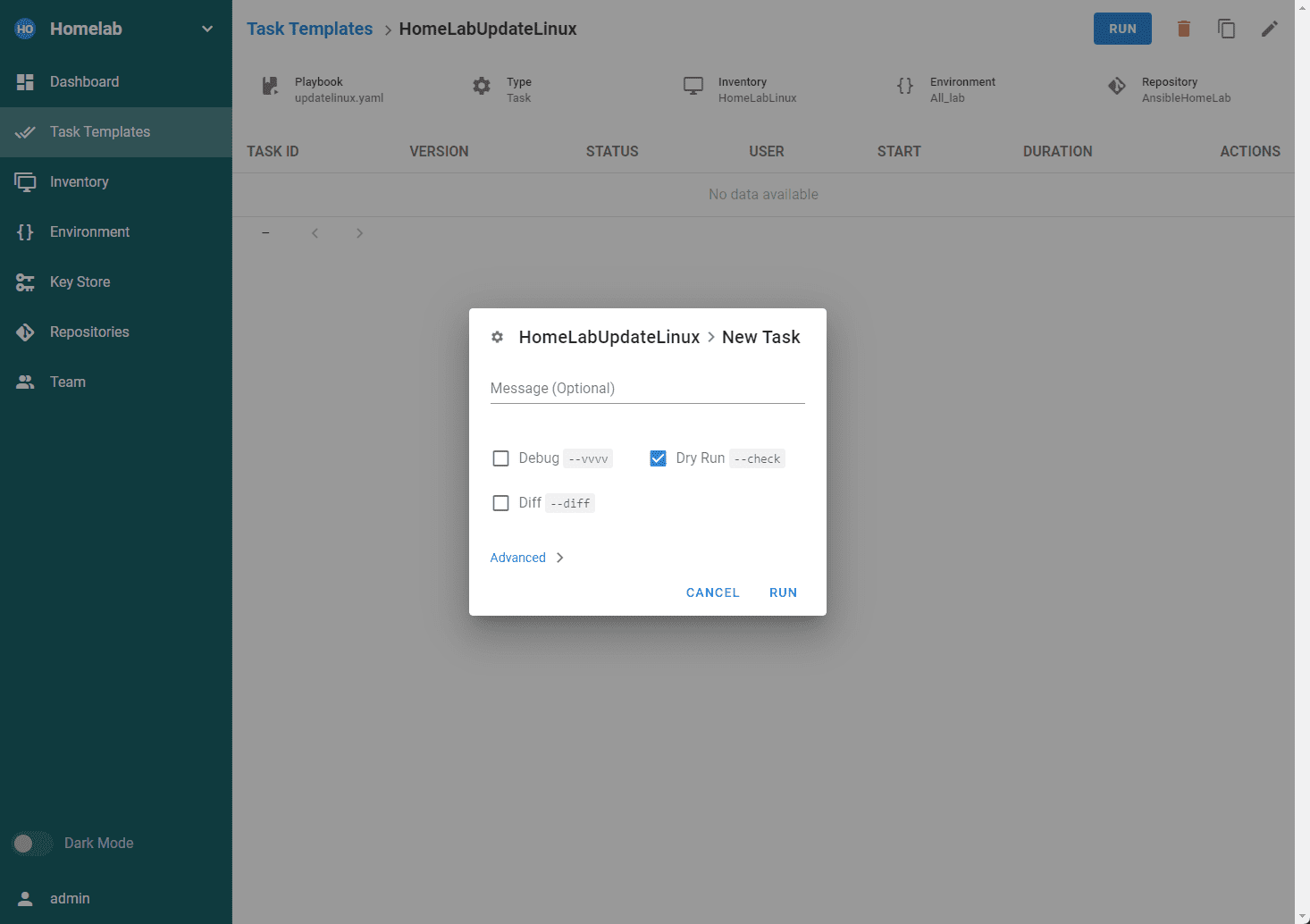
Once your task template is created, click the Run button.
Choose Dry Run for testing.
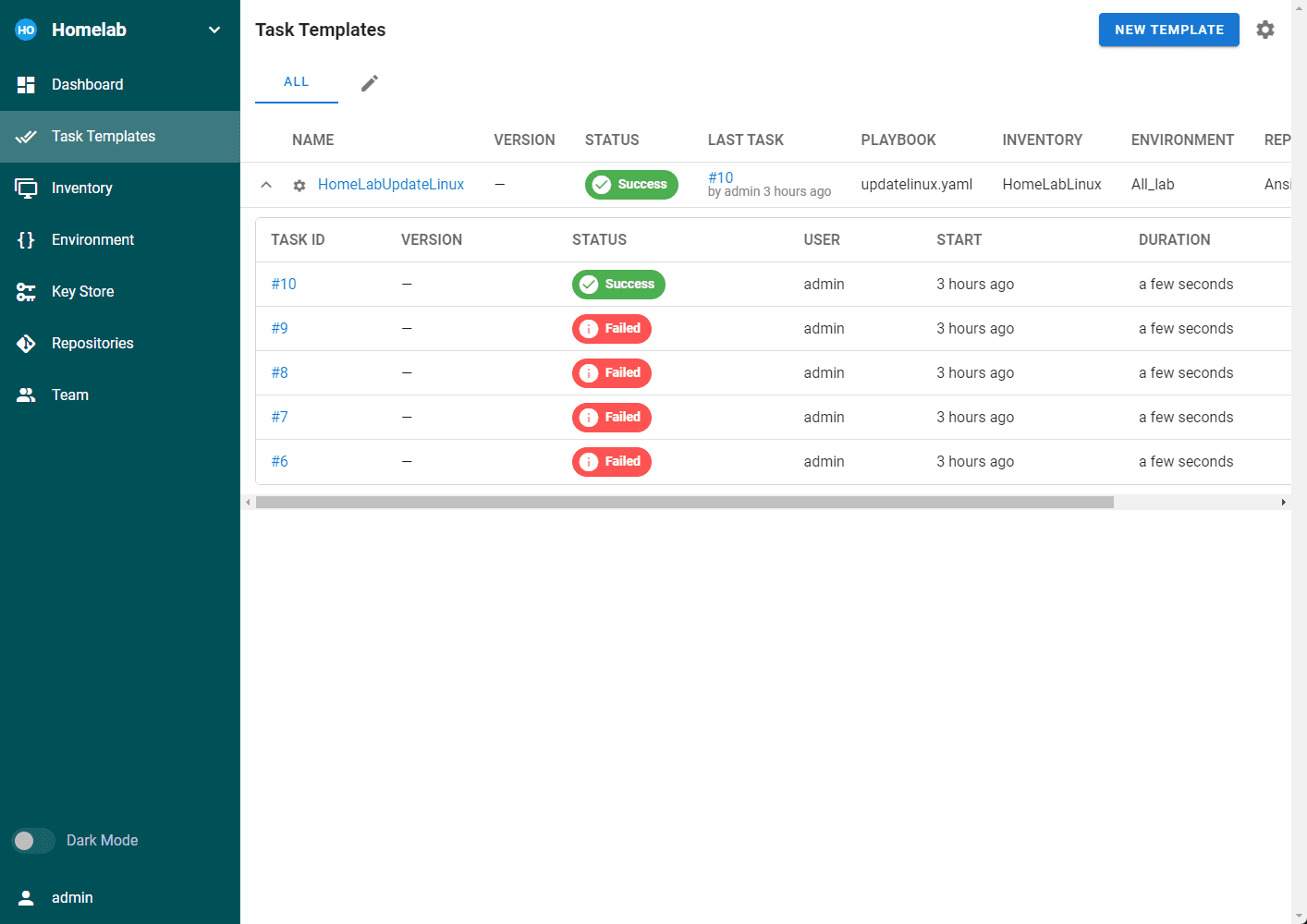
Below, you can see Semaphore keeps a history of all your runs. The failed attempts were me trying to get my credentials figured out.
Frequently Asked Questions
1. Is there a cost associated with using Ansible Semaphore?
No, Ansible Semaphore is an open-source solution available to all users free of charge. It offers a budget-friendly alternative to Ansible Tower for teams requiring a web-based interface for their automation tasks.
2. Can I use Ansible Semaphore on Windows?
Ansible Semaphore can run on Windows, but it requires Docker and Docker Compose, which must be installed on your system. Running Ansible Semaphore within Docker allows it to function across different operating systems, including Windows.
3. Can Ansible Semaphore support multiple users?
Yes, Ansible Semaphore has built-in user management. You can create multiple users, assign them to projects, and control their access levels. This makes Semaphore suitable for team environments, where multiple people may be managing your Ansible playbooks.
4. How does Ansible Semaphore compare to Ansible Tower as an Ansible GUI?
Ansible Tower is Ansible’s enterprise product offering a web-based UI, role-based access control, and job scheduling. However, it comes with licensing costs.
On the other hand, Ansible Semaphore offers a significant portion of the features found in Ansible Tower but is open-source and free. It’s a great choice for smaller teams or projects that can’t justify the cost of Ansible Tower but still require a web-based interface.
5. How secure is Ansible Semaphore?
Ansible Semaphore is designed with security in mind. All sensitive information, like SSH keys and passwords, is stored encrypted in the MySQL database. Additionally, by using Semaphore, you can restrict which playbooks can be run and by whom, further enhancing your security posture.
Automation tools for Home lab
Wrapping up
Using Ansible Semaphore, you can run your Ansible playbook or playbooks with an Ansible GUI, create inventory files, manage access to tasks, and more. All this while benefiting from a modern UI and an efficient system to organize your Ansible projects. Truly, Ansible Semaphore makes Ansible automation a breeze. So, install Semaphore, configure it, and let the power of Ansible automation simplify your IT management tasks.










Hello, I’ve encountered a situation where elevated privileges are not being applied to the commands, even though both user credentials and sudo credentials are specified in the inventory.
which kind is ssh connection do you use? piping?
did you use -vvvv mode to check issue?