Airmon-ng VMware Kali Linux Hacking Wireless

You can do many cool things with Kali Linux, including testing the security of a wireless network. This post will look at airmon-ng VMware Kali VM configuration and what you can do with airmon-ng and aircrack-ng once installed in VMware Workstation.
Table of contents
- What is Kali Linux?
- What is Airmon-ng?
- Is Airmon-ng Pre-installed In Kali Linux?
- Install Kali Linux
- Start using Docker-Kali Image
- Now install tools into your Kali Linux
- How To Install Aircrack-ng
- Installing VMware Tools on Kali Linux VMware VM
- Which wireless card
- How To Enable Wifi Adapter In Kali Linux In Vmware
- How To Use Aircrack-ng And Airodump-ng In Kali Linux To Crack Wi-fi Passwords
- How to Keep Your Wireless Network Safe
- Wrapping up
What is Kali Linux?
Kali is well-known as a “hacking” Linux distro. It provides all of the tools in one place for cracking, hacking, and penetration testing. The Kali Linux distro is free to download as well and can be run as a virtual machine, container, inside VMware Workstation, etc.
What is Airmon-ng?
Airmon-ng is a command-line tool that is part of the tool suite known as the Aircrack-ng suite. These are a collection or bundle of tools for testing wireless network security.
With Airmon-ng you can configure your wireless network adapter for “monitor mode” and this allows them to capture raw 802.11 frames. This then can allow a skilled security pro to “listen in” on wireless networks, and collect data of the traffic captured. Then this traffic capture can be analyzed.
Security pros can use this to identify weak points in the network and possible attack vectors that hackers can use to compromise the wireless network.
Is Airmon-ng Pre-installed In Kali Linux?
Yes, it is part of the Aircrack-ng suite that is included with Kali LInux. It means you don’t have any additional installations to take care of when you download Kali Linux, the tools are already there for you to use.
Install Kali Linux
First you will want to download Kali Linux. You can find that website here: Get Kali | Kali Linux.
Download Kali Linux for your virtualization technology from the website for Kali and choose the right platform for moving forward with the installation.
If you are using VMware Workstation like I am, you can extract the downloaded files to the folder of your choosing.
From here, In VMware Workstation, we will Open the new virtual machine from the files extracted from the download:
Boot Kali Linux in VMware Workstation.
Start using Docker-Kali Image
Using a Kali Linux Docker container is also an easy way to get started using Kali Linux. To get started, pull the official Kali Linux Docker image by running the following command:
docker pull kalilinux/kaliThen run a new container with the Kali Linux image:
docker run -it --name kali-container kalilinux/kaliNow install tools into your Kali Linux
Even though Kali Linux comes with most all of the tools you may want to use and work with, you can also install other tools that are not included by default. You can use the “apt-get” package manager to update the package list that is available and then and then install the tools you want. As an example, you can install the Metasploit framework, run the following commands (note in recent versions of Kali, this is already installed)
sudo apt-get update sudo apt-get install metasploit-frameworkHow To Install Aircrack-ng
Aircrack-ng, as mentioned earlier, comes pre-installed with Kali Linux. But if there is a need or reason that you need to install or reinstall it, you can use the commands below:
sudo apt-get update sudo apt-get install aircrack-ngInstalling VMware Tools on Kali Linux VMware VM
You will want to install VMware tools in your Kali Linux distro. However, recent versions should have this preinstalled and ready to go. But, if you need to install VMware Tools on your Kali Linux virtual machine or have problems, run the commands:
sudo apt-get update sudo apt-get install open-vm-tools-desktop fuseAfter the install, reboot.
Which wireless card
The built-in cards that come in laptops and other devices may not allow the device to be put into monitor mode. This is a required mode to use tools like airmon-ng.
To overcome this issue, you can find an external USB Wi-Fi adapter on Amazon or another online vendor that is compatible with Kali Linux and supports both monitor mode and packet injection.
How To Enable Wifi Adapter In Kali Linux In Vmware
To enable a Wi-Fi adapter in Kali Linux running in a VMware virtual machine, follow these steps:
connect the adapter to the host machine’s USB port
Configure VMware workstation to allow USB connections from the host to be connected to the VM,
Launch Kali and connect the Wi-Fi adapter to the virtual machine
You can then open Kali and terminal and then run the following command to enable the Wi-Fi adapter:
sudo ifconfig wlan0 upYou can see if the adapter is available and you can make sure it is enabled:
sudo iwconfig
The Wi-Fi adapter should now be enabled and ready for use within your Kali Linux virtual machine.
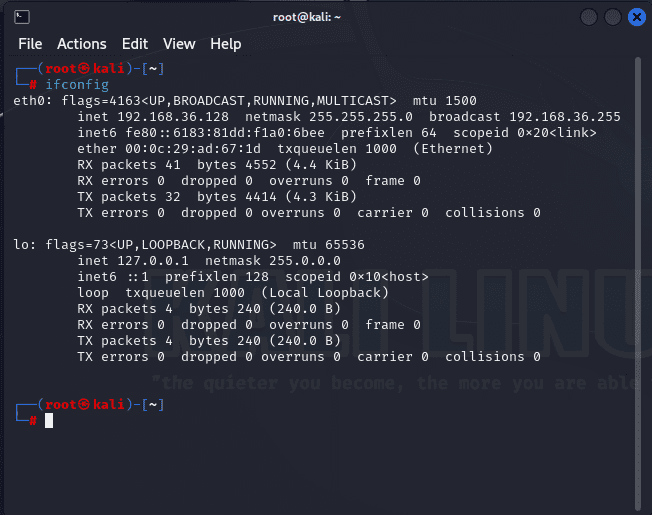
You can use ifconfig, as shown below. If you have added your wireless adapter, it should display the IP address here.
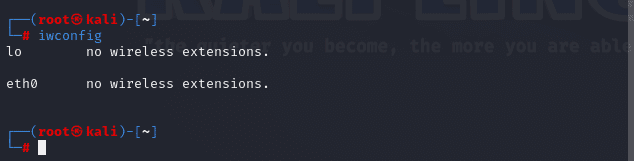
If you have no wireless connections, you will see the following with an iwconfig output.
How To Use Aircrack-ng And Airodump-ng In Kali Linux To Crack Wi-fi Passwords
Aircrack-ng and Airodump-ng are tools that enable an experienced security pro or an attacker to crack Wi-Fi encryption keys. To crack passwords:
Put your Wi-Fi adapter into monitor mode using Airmon-ng:
sudo airmon-ng start wlan0You can identify the target wireless network by running Airodump-ng:
sudo airodump-ng wlan0monYou can capture the “handshake” between the access point and a client by running Airodump-ng with the target network’s BSSID and channel:
sudo airodump-ng -c [channel] --bssid [BSSID] -w [output-file] wlan0monWait for a handshake to be captured, indicated by the “WPA handshake” message in the Airodump-ng output.
Use Aircrack-ng to crack the captured handshake and retrieve the Wi-Fi password:
sudo aircrack-ng -a2 -b [BSSID] -w [wordlist] [output-file-01.cap]Replace [wordlist] with the path to a wordlist file containing your password file passwords. Keep in mind that this process should be used responsibly and only for ethical hacking purposes.
How to Keep Your Wireless Network Safe
Use strong encryption: Enable WPA3 encryption on your Wi-Fi router if available. If WPA3 is not supported, use WPA2 instead of the outdated and insecure WEP or WPA.
Set a strong password: Use a complex and unique password for your Wi-Fi network. Make sure it should be at least 12 characters long, including uppercase and lowercase letters, numbers, and special symbols.
Change the default SSID: Change the default Service Set Identifier (SSID) or network name if your wi-fi or router access point comes with something default configured
Disable WPS: Wi-Fi Protected Setup (WPS) can be vulnerable to brute-force attacks. Disable this feature on your router to improve security.
Enable router firewall: Make sure that your built-in firewall on your router is enabled and it has the settings configured that need to be to block malicious traffic
Keep router firmware updated: Update your router, always
Disable remote management: Turn off your router’s remote management features
Use MAC address filtering: Limit access to your Wi-Fi network by allowing only specific devices based on their MAC addresses. Make sure you know though that MAC addresses can be spoofed
Create a separate guest network: Set up a separate guest Wi-Fi network
Turn off the network when not in use: If you don’t need your Wi-Fi network for extended periods, turn it off
Wrapping up
Kali Linux is a great “hacking” linux distribution that provides all of the tools preloaded for use for penetration and other security testing. Airmon-ng is one of those tools you can make use of to test the strength and security of wireless networks. You will most likely need an external USB wireless network adapter for testing out and capturing packets with airmon-ng. Let me know in the comments if this is a tool you have used? Any tips or tricks you have gathered to share?