I have been playing around lately in my DevOps learning adventures with Traefik. Traefik is a great ingress controller that you will find used just about everywhere in Kubernetes deployments. However, it can be a bit challenging to deploy. There is no better way than to get Traefik into your lab environment and start playing around. Let’s take a look at a Traefik ingress example YAML and setup in K3s
What is a Kubernetes Ingress controller?
First of all, what is a Kubernetes ingress controller? By design, pods running in a Kubernetes cluster can communicate freely between themselves, but they are not exposed by default to the outside world. A Kubernetes ingress controller is in itself an API object that defines how traffic from outside the Kubernetes cluster can reach the internal Kubernetes cluster services that communicate with pods. It defines how the external clients and traffic are routed to a cluster’s internal services. The ingress controller listens for the request and adjusts its configuration to do what the user is requesting.
You can think of the ingress controller as an abstraction layer that makes it, so the user does not need to know which ingress controller is in a cluster, and it routes layer 7 traffic for HTTP/HTTPS requests. Ingress controllers can also define how TLS is configured.
There are many reasons to use an ingress and ingress controller over a load balancer, NodePort, or other ways to expose Kubernetes services. Ingress controllers collect resources behind a common IP and are less technically expensive than other ways to expose services. They can also provide automatic certificate management, middleware, and load balancing themselves.
While they have many great features, there are also limitations to note with an ingress controller. They only handle and route L7 traffic, such as HTTP and HTTPS. You cannot route lower-level traffic types such as TCP and UDP. They are also only relevant for a specific Kubernetes namespace, meaning you can only reference a service inside the same namespace as the ingress controller.
Traefik ingress controller
Why use Traefik ingress example YAML? Traefik is a very popular and fully featured ingress controller with huge adoption. It provides a robust solution that includes ingress but contains many other features and capabilities, such as a modern load balancer, API gateway, Kubernetes ingress controller, and service mesh.
A really cool part of K3s clusters and deploying these with K3D is it comes with Traefik as the ingress controller. So, you can literally spin up a Kubernetes cluster in a few seconds with Traefik installed, etc. Read my walkthrough here on how to spin up K3s with Traefik and expose the Traefik dashboard:
Learn more about Traefik here:
Traefik Ingress Example YAML and setup in K3s
The example Traefik Ingress example YAML we will use comes from the example K3D documentation here:
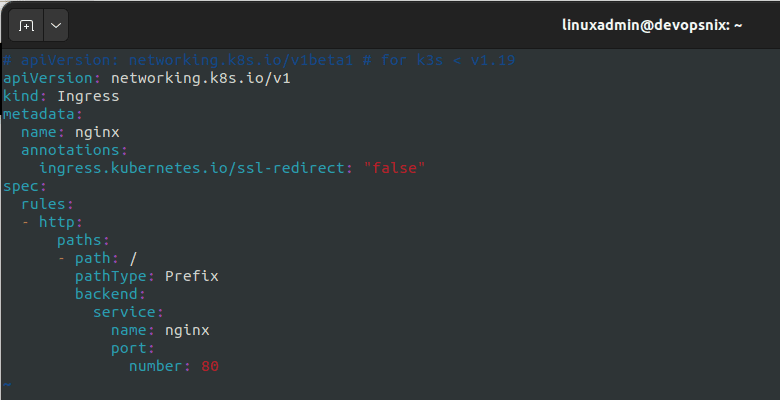
# apiVersion: networking.k8s.io/v1beta1 # for k3s < v1.19
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: nginx
annotations:
ingress.kubernetes.io/ssl-redirect: "false"
spec:
rules:
- http:
paths:
- path: /
pathType: Prefix
backend:
service:
name: nginx
port:
number: 80Now, let’s step through this. First, spin up a new K3s cluster.
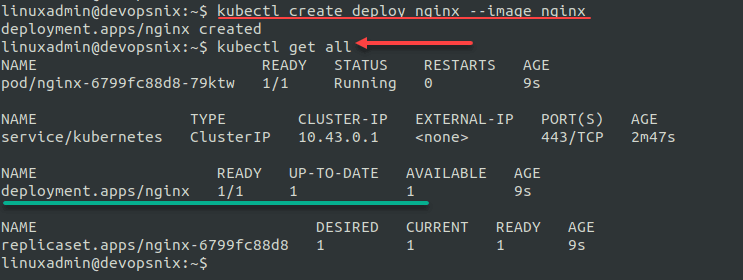
Create a new Nginx deployment:
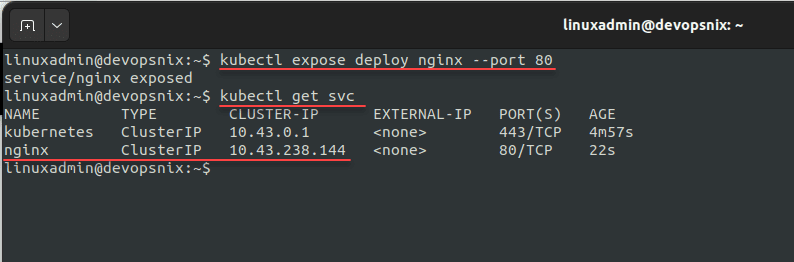
kubectl create deploy nginx --image nginxNext, expose the Nginx deployment:
kubectl expose deploy nginx --port 80You can also view the service by running the kubectl get svc command to view the new nginx service.
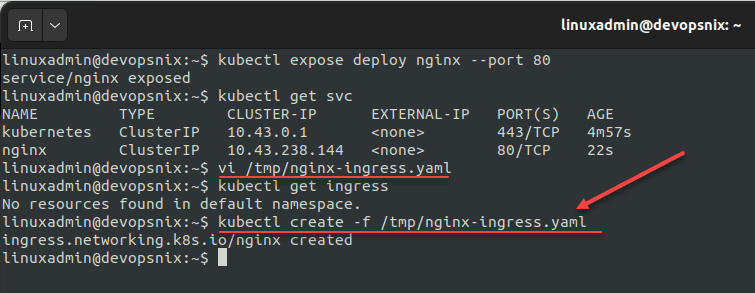
Create a new YAML file, naming it whatever you want in a location you can reference to deploy the ingress. This is the code linked above.
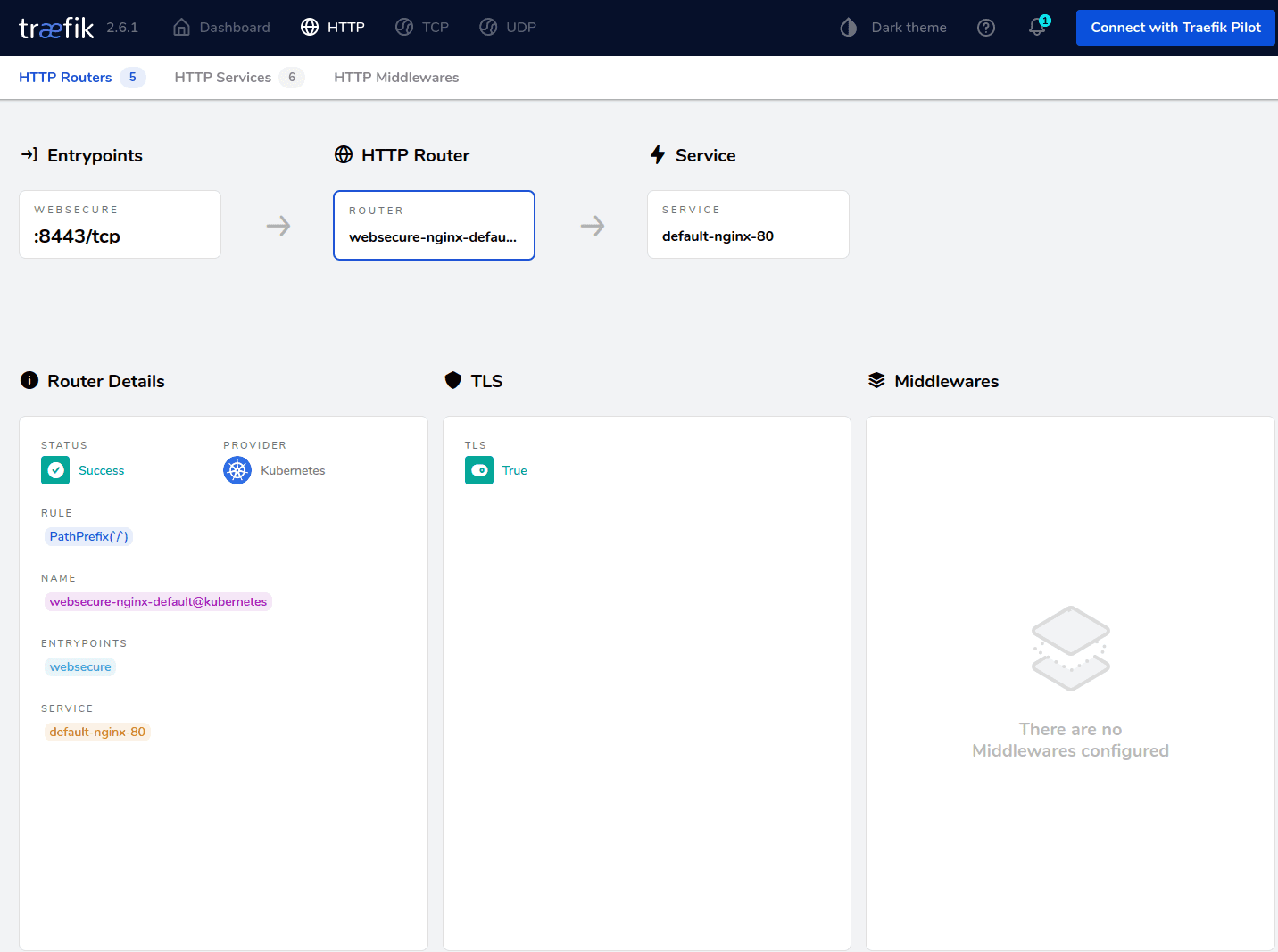
Create the ingress using the command:
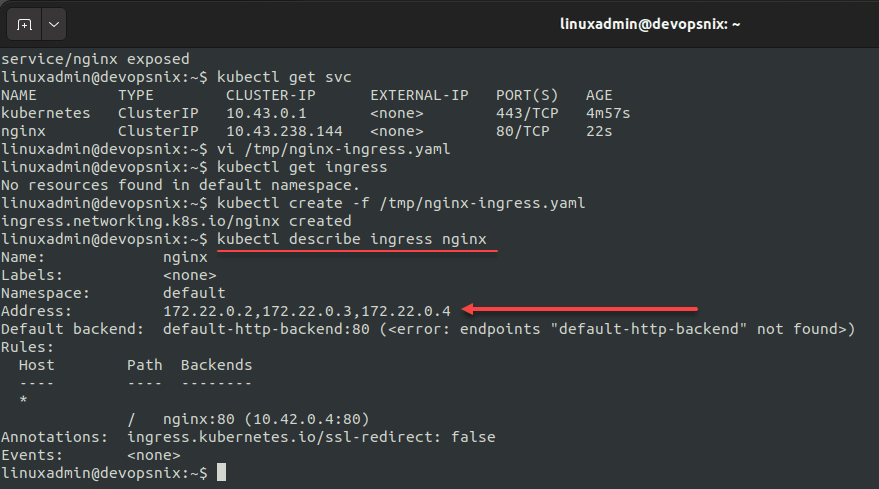
kubectl create -f <your file path.yaml>You can now describe your ingress using the command:
kubectl describe ingress nginxYou can now navigate to your node IP, port 80, and get to the Nginx page. You should be able to do this for the IP of each Kubernetes node, showing the ingress is working correctly.
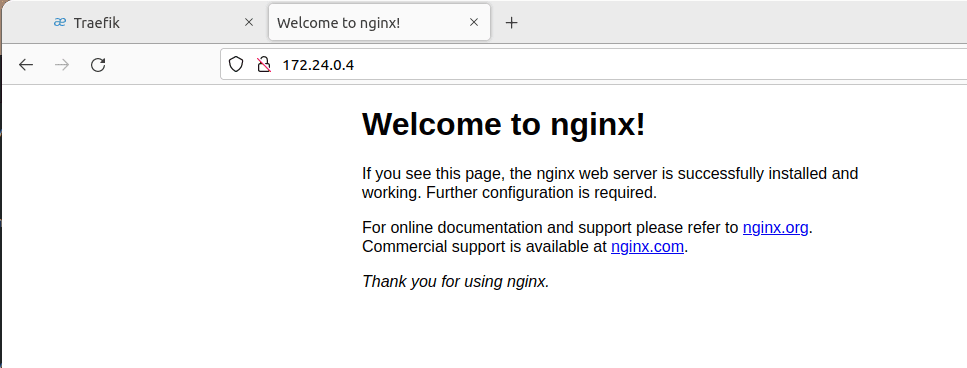
Traefik Ingress Example YAML FAQs
- What is an ingress controller? An ingress controller is an API interface allowing the routing of layer 7 traffic such as HTTP and HTTPS. You can use an ingress controller to expose services running in a Kubernetes cluster easily. It is view as the de facto way to expose production services over other means such as ClusterIP and NodePort. The ingress controller is used in conjunction with an external load balancer to provide resilient and highly available connectivity to your pods.
- What is Traefik? Traefik is a very popular ingress controller that provides many robust features and capabilities for ingress to a Kubernetes cluster
- How do you expose services in Kubernetes? Using an ingress controller, NodePort, ClusterIP, or LoadBalancer configuration, you can expose services in Kubernetes. The Ingress controller is typically seen in production environments.
Wrapping Up
Hopefully, this Traefik Ingress Example YAML will help you to lab and learn with Traefik by creating a play environment using K3s to explore and use Traefik. You can easily create ingress to services with the Traefik ingress controller.
Google is updating how articles are shown. Don’t miss our leading home lab and tech content, written by humans, by setting Virtualization Howto as a preferred source.


This is nginx not traefik. wtf ?!
Interesting that you didn’t bother to read the article. How you considered a non-technical career?
:))))))))))))))))))))))