New VMware VMSA-2022-0004 security vulnerability Affects ESXi Workstation Pro and others. Yesterday, VMware released news of high-severity security vulnerabilities that affect core products across the board. The products affected include:
- VMware ESXi
- VMware Workstation Pro / Player (Workstation)
- VMware Fusion Pro / Fusion (Fusion)
- VMware Cloud Foundation (Cloud Foundation)
These include the following vulnerabilities:
- Use-after-free vulnerability in XHCI USB controller (CVE-2021-22040)
- Double-fetch vulnerability in UHCI IUSB controller (CVE-2021-22041)
- ESXi settingsd unauthorized access vulnerability (CVE-2021-22042)
- ESXi settingsd TOCTOU vulnerability (CVE-2021-22043)
- ESXi slow HTTP POST denial of service vulnerability (CVE-2021-22050)
The relevant CVEs are the following:
- CVE-2021-22040
- CVE-2021-22041
- CVE-2021-22042
- CVE-2021-22043
- CVE-2021-22050
New VMware VMSA-2022-0004 security vulnerability Affects ESXi Workstation Pro and others
An attacker with local administrator rights on a virtual machine running in a vulnerable environment can potentially execute code as the virtual machine’s VMX process running on the host. So with the right set of circumstances, this is a very serious set of vulnerabilities that can lead to compromised environments. In and of themselves, the vulnerabilities are important to moderate. However, it is the cumulative nature of the vulnerabilities that can result in higher severity compromise.
Use-after-free vulnerability in XHCI USB controller (CVE-2021-22040)
This vulnerability affects VMware ESXi, VMware Workstation, VMware Fusion. It involves a use-after-free vulnerability in the XHCI USB controller. The score of this individual vulnerability is 8.4. This vulnerability is remediated in the fixed version of the affected products. A malicious actor with local administrative privileges on a virtual machine may exploit this issue to execute code as the virtual machine’s VMX process running on the host.
Double-fetch vulnerability in UHCI IUSB controller (CVE-2021-22041)
This vulnerability affects VMware ESXi, VMware Workstation, VMware Fusion. A malicious actor with local administrative privileges on a virtual machine may exploit this issue to execute code as the virtual machine’s VMX process running on the host. Again this is fixed in the fixed version of the respective VMware solution.
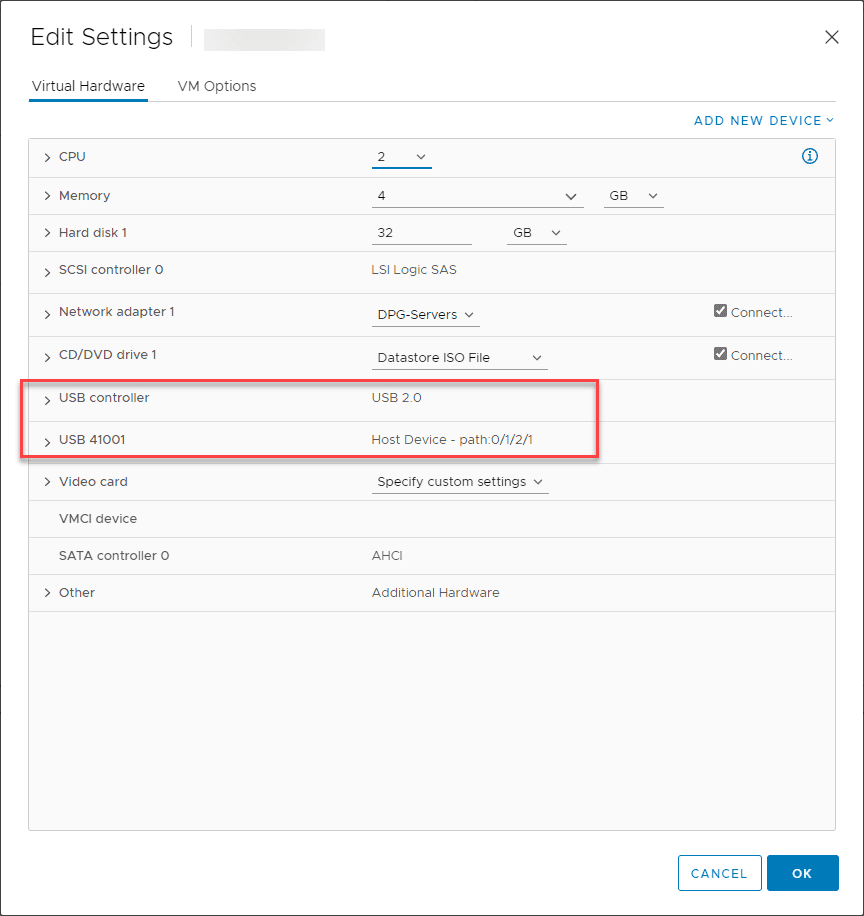
As a note successful exploitation of this issue requires an isochronous USB endpoint to be made available to the virtual machine.
ESXi settingsd unauthorized access vulnerability (CVE-2021-22042)
This vulnerability affects VMware ESXi and contains an unauthorized access vulnerability due to VMX having access to settingsd authorization tickets. If a malicious actor has privileges within the VMX process can access settingsd service running as a high privileged users. The fix for this is to install the fixed version.
ESXi settingsd TOCTOU vulnerability (CVE-2021-22043)
VMware ESXi has another vulnerability known as the TOCTOU (Time-of-check Time-of-use) vulnerability. This vulnerability affects the way temporary files are accessed. To fix, apply the fixed version of VMware ESXi.
ESXi slow HTTP POST denial of service vulnerability (CVE-2021-22050)
This vulnerability is found in VMware ESXi and is known as a slow HTTP POST denial of service (DOS) vulnerability affecting rhttpproxy. An attacker can use this vulnerability to launch a DOS attack that overwhelms the rhttpproxy service with multiple requests.
How were these discovered?
These issues were discovered as part of the Tianfu Cup, a Chinese hacking event. VMware worked with the organizers of this event to review the findings and receive the information privately.
Is there a workaround to the issue as of yet?
In accord with best practices, VMware recommends getting a patched version of affected products installed as soon as possible. However, there is a bit of a workaround that involves identifying virtual machines with a USB controller installed. To do that, you can identify these with a PowerCLI script as follows:
$VMs = Get-VM
$USBHardware = "VirtualUSBController|VirtualUSBXHCIController"
foreach ($VM in $VMs) {
$VMview = Get-VM $VM | Get-View
$VMview.Config.Hardware.Device | Where-Object {$_.GetType().Name -match $USBHardware} | Foreach-Object {
$devname = $_.GetType().Name
Write-Host "$VM`: VM has a $devname device." -ForegroundColor Yellow
}
}To remove the USB controllers from affected virtual machines, you can use the following PowerCLI code. As a note, a hindrance to having this completely automated is the virtual machines need to be powered off before you can remove the USB controller.
$VMs = Get-VM $vmname
$USBHardware = "VirtualUSBController|VirtualUSBXHCIController"
foreach ($VM in $VMs) {
$VMview = Get-VM $VM | Get-View
$VMview.Config.Hardware.Device | Where-Object {$_.GetType().Name -match $USBHardware} | Foreach-Object {
$devname = $_.GetType().Name
Write-Host "$VM`: Removing the $devname device." -ForegroundColor Yellow
$Config = New-Object VMware.Vim.VirtualMachineConfigSpec
$Config.DeviceChange = New-Object VMware.Vim.VirtualDeviceConfigSpec
$Config.DeviceChange[0] = New-Object VMware.Vim.VirtualDeviceConfigSpec
$Config.DeviceChange[0].Operation = "remove"
$Config.DeviceChange[0].Device = $_
# $VM.ExtensionData.ReconfigVM($Config)
}
}On another note, if you are running snapshots in your environment, you will need to keep this in mind as removing the USB controller from a virtual machine. The reason for this is that snapshots contain virtual hardware as part of the VM state. Restoring a snapshot on a virtual machine will bring back the removed USB controller.
Response Matrices and fixed versions
The following response matrix is in regards to the following two of the CVEs of the New VMware VMSA-2022-0004 security vulnerability:
- Use-after-free vulnerability in XHCI USB controller (CVE-2021-22040)
- Double-fetch vulnerability in UHCI IUSB controller (CVE-2021-22041)
| Product | Version | Running On | CVE Identifier | CVSSv3 | Severity | Fixed Version | Workarounds | Additional Documentation |
| ESXi | 7.0 U3 | Any | CVE-2021-22040, CVE-2021-22041 | 8.4 | Important | ESXi70U3c-19193900 | KB87349 | FAQ |
| ESXi | 7.0 U2 | Any | CVE-2021-22040, CVE-2021-22041 | 8.4 | Important | ESXi70U2e-19290878 | KB87349 | FAQ |
| ESXi | 7.0 U1 | Any | CVE-2021-22040, CVE-2021-22041 | 8.4 | Important | ESXi70U1e-19324898 | KB87349 | FAQ |
| ESXi | 6.7 | Any | CVE-2021-22040, CVE-2021-22041 | 8.4 | Important | [1] ESXi670-202111101-SG | KB87349 | FAQ |
| ESXi | 6.5 | Any | CVE-2021-22040, CVE-2021-22041 | 8.4 | Important | ESXi650-202202401-SG | KB87349 | FAQ |
| Fusion | 12.x | OS X | CVE-2021-22040, CVE-2021-22041 | 8.4 | Important | 12.2.1 | KB87349 | FAQ |
| Workstation | 16.x | Any | CVE-2021-22040, CVE-2021-22041 | 8.4 | Important | 16.2.1 | KB87349 | FAQ |
Impacted Product Suites that Deploy Response Matrix of affected products:
| Product | Version | Running On | CVE Identifier | CVSSv3 | Severity | Fixed Version | Workarounds | Additional Documentation |
| Cloud Foundation (ESXi) | 4.x | Any | CVE-2021-22040, CVE-2021-22041 | 8.4 | Important | KB87646 (4.4) | KB87349 | FAQ |
| Cloud Foundation (ESXi) | 3.x | Any | CVE-2021-22040, CVE-2021-22041 | 8.4 | Important | 3.11 | KB87349 | FAQ |
The following response matrix is in regards to the following two of the CVEs in the New VMware VMSA-2022-0004 security vulnerability:
- ESXi settingsd unauthorized access vulnerability (CVE-2021-22042)
- ESXi settingsd TOCTOU vulnerability (CVE-2021-22043)
| Product | Version | Running On | CVE Identifier | CVSSv3 | Severity | Fixed Version | Workarounds | Additional Documentation |
| ESXi | 7.0 U3 | Any | CVE-2021-22042, CVE-2021-22043 | 8.2 | Important | ESXi70U3c-19193900 | None | FAQ |
| ESXi | 7.0 U2 | Any | CVE-2021-22042, CVE-2021-22043 | 8.2 | Important | ESXi70U2e-19290878 | None | FAQ |
| ESXi | 7.0 U1 | Any | CVE-2021-22042, CVE-2021-22043 | 8.2 | Important | ESXi70U1e-19324898 | None | FAQ |
| ESXi | 6.7 | Any | CVE-2021-22042, CVE-2021-22043 | N/A | N/A | Unaffected | N/A | N/A |
| ESXi | 6.5 | Any | CVE-2021-22042, CVE-2021-22043 | N/A | N/A | Unaffected | N/A | N/A |
Impacted Product Suites that Deploy the affected products
| Product | Version | Running On | CVE Identifier | CVSSv3 | Severity | Fixed Version | Workarounds | Additional Documentation |
| Cloud Foundation (ESXi) | 4.x | Any | CVE-2021-22042, CVE-2021-22043 | 8.2 | Important | KB87646 (4.4) | None | FAQ |
| Cloud Foundation (ESXi) | 3.x | Any | CVE-2021-22042, CVE-2021-22043 | N/A | N/A | Unaffected | N/A | N/A |
The following response matrix is in regards to the following two of the CVEs in the New VMware VMSA-2022-0004 security vulnerability:
- ESXi slow HTTP POST denial of service vulnerability (CVE-2021-22050)
| Product | Version | Running On | CVE Identifier | CVSSv3 | Severity | Fixed Version | Workarounds | Additional Documentation |
| ESXi | 7.0 | Any | CVE-2021-22050 | 5.3 | Moderate | ESXi70U3c-19193900 | None | FAQ |
| ESXi | 6.7 | Any | CVE-2021-22050 | 5.3 | Moderate | [1] ESXi670-202111101-SG | None | FAQ |
| ESXi | 6.5 | Any | CVE-2021-22050 | 5.3 | Moderate | ESXi650-202110101-SG | None | FAQ |
Impacted Product Suites that Deploy Response Matrix 3e Components:
| Product | Version | Running On | CVE Identifier | CVSSv3 | Severity | Fixed Version | Workarounds | Additional Documentation |
| Cloud Foundation (ESXi) | 4.x | Any | CVE-2021-22050 | 5.3 | Moderate | KB87646 (4.4) | None | FAQ |
| Cloud Foundation (ESXi) | 3.x | Any | CVE-2021-22050 | 5.3 | Moderate | 3.11 | None | FAQ |
Recommended resources
Take note of the following resources:
Concluding Notes
As bad as we hate to see new security vulnerabilities come down the pipes, it is better to find them this way than after the fact and the attackers have the upper hand. Kudos to VMware for getting this New VMware VMSA-2022-0004 security vulnerability disclosed and patched in a timely manner.
Google is updating how articles are shown. Don’t miss our leading home lab and tech content, written by humans, by setting Virtualization Howto as a preferred source.