Windows Server 2022 Security Hardening best practices
Hardening your Windows Servers is a great way, along with other security measures, that you have a strong security posture. What are the best ways to harden your Windows Servers in your environment? There are a few things you can do to harden your Windows Servers per Microsoft best practices. In this post, we will specifically look at hardening Windows Server 2022. Note Windows Server 2022 security hardening best practices.
Windows Server 2022 security hardening best practices
What best practices help to ensure your Windows Server 2022 and legacy Windows Servers are hardened appropriately? Let’s consider the following:
- Use Secured Core Server
- Use LAPs
- Configure a Privileged Access Workstation
- Secure your domain controllers
- Analyze security configuration with the Security Compliance Toolkit
- Secure SMB traffic
1. Use Secured Core Server
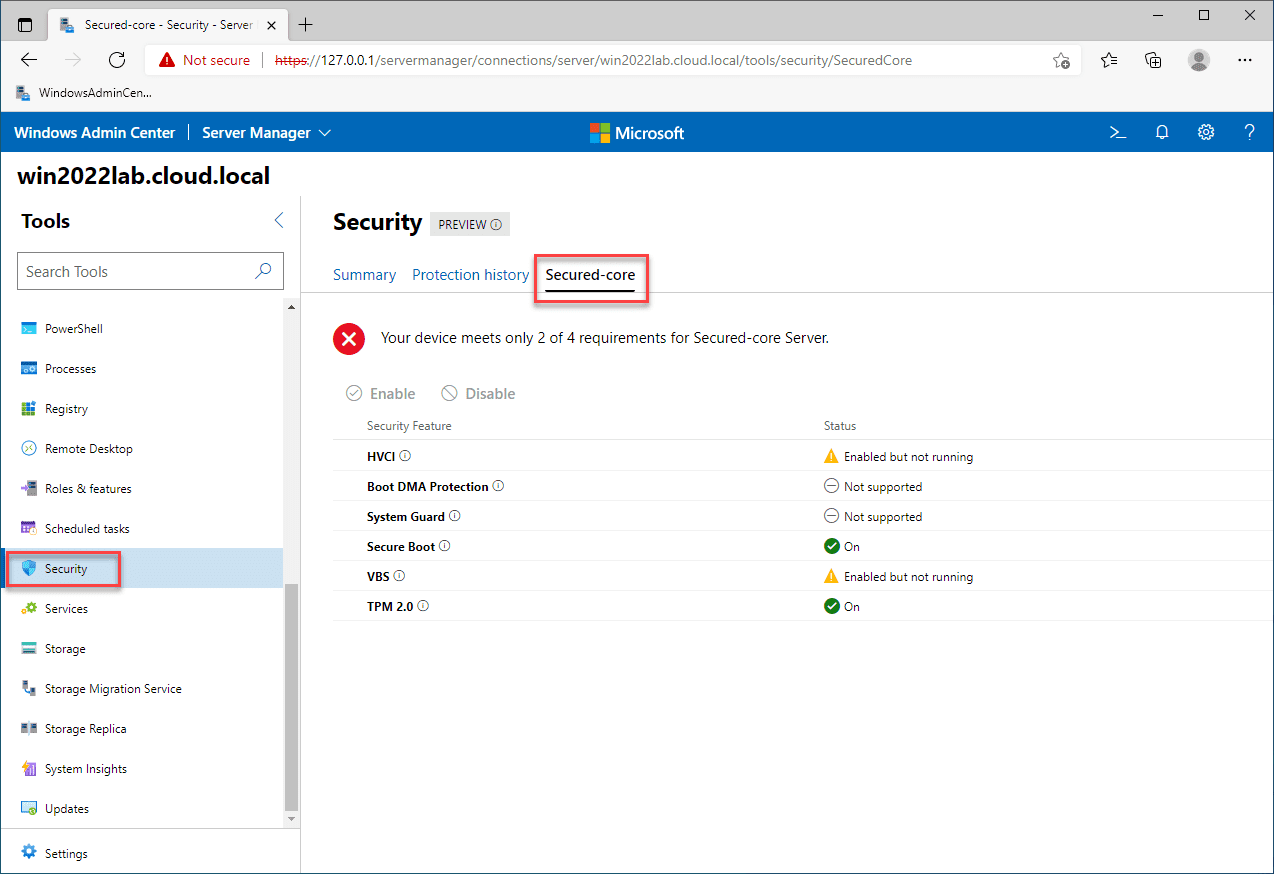
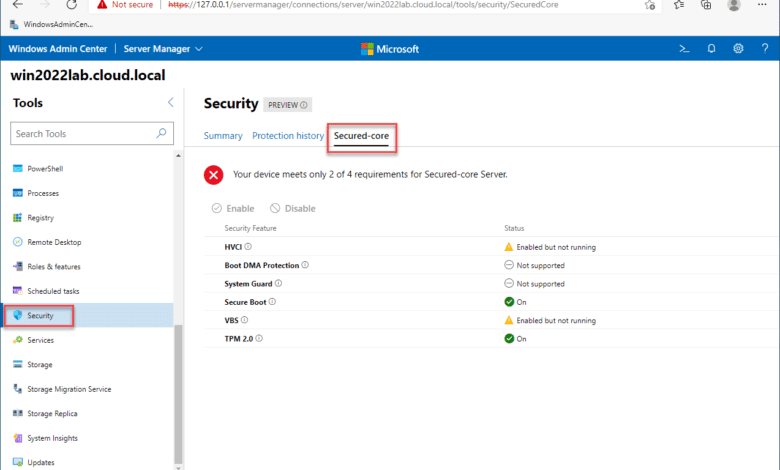
Windows Server 2022 represents the most secure Windows Server platform to date. Much of this newly improved security stance for Windows Server 2022 is a result of Secured Core Server. The Secured Core Server solution is a new security framework from Microsoft that includes several security solutions making up the overall secured core server solution.
Secured core server is not a single solution, but a bundle of security solutions into the secured core solution. Secured Core Server is exposed using Windows Admin Center (WAC). It contains the following security technologies:
- HVCI
- Boot DMA Protection
- System Guard
- Secure Boot
- Virtualization-based Security (VBS)
- TPM 2.0
Read my walkthrough here on setting up Windows Server 2022 Trusted Platform Module:
2. Use Local Administrator Password Solution (LAPS)
This is a technology that is not specific to Windows Server 2022, but rather all workstations and servers on a corporate network. Windows clients and Windows Server require a local administrator account to initially provision a machine on the network. They are also required if for some reason the connection to the Active Directory domain is broken. However, from a security perspective, the local administrator accounts can be dangerous.
If you have tens, hundreds, or even thousands of Windows clients on the network, it can be difficult to provision and manage unique administrator accounts on thousands of nodes. The other side of the coin is provisioning the same local administrator account for all clients on the network. This is a dangerous strategy, as one compromised machine and exposed administrator credentials effectively compromise the entire network of clients with the same password.
Local Administrator Password Solution (LAPS) is a solution that provides organizations with a centralized way to control local administrator passwords for domain-joined computers. It provides:
- Unique local administrator passwords
- Randomized passwords that are automatically changed on an interval
- Local administrator passwords and secrets are stored securely within AD DS
- Configurable permissions control access to passwords in AD DS
- Passwords that LAPS retrieves are transmitted to the client using a secure, encrypted channel of communication
You can download LAPS here:
3. Configure a privileged access workstation (PAW)
It is an often-neglected part of securing an environment. The workstations that connect to business-critical and sensitive servers in the environment should themselves also be secure. Secure servers are only as a secure as the workstations used to connect to them.
Routine tasks such as receiving and reading emails or browsing the Internet should not be mixed with administrative tasks. This introduces increased risk if the machine used for the administrative tasks is compromised, the servers in the environment that have been accessed are also at risk.
A skilled attacker can easily harvest credentials from workstations, especially if these are not using Credential Guard, and the compromised workstation has a mix of daily use credentials and privileged access credentials.
Using a Privileged Access Workstation (PAW) for accessing sensitive environments and privileged access helps to make sure that external attacks can’t infect the devices only access from the PAW. What are PAW best practices?
- Only authorized users should be able to sign into the PAW
- Use Windows Defender Credential Guard on the PAW to protect against credential theft
- Enable BitLocker Drive encryption to protect the boot environment and the hard disk drives from tampering
- Use Windows Defender Device Guard to ensure only trusted applications are allowed to run to perform administrative tasks
- Don’t allow PAWs to access the Internet
- Install all tools in the PAWs that are needed so for convenience an admin doesn’t use a non privileged workstation to perform privileged tasks
- Limit physical access to the PAW
- Block RDP, PowerShell, and other management tools coming from computers that aren’t configured as a PAW
- Restrict administrator accounts to only be able to sign into a PAW
- If you host a daily use workstation and PAW together, make sure you put the daily use machine in the virtual machine on the same physical client and not the other way around. If the daily drive is compromised in the VM, it doesn’t compromised the PAW. However, if the host machine is a daily use workstation and the PAW is a VM, it is much more likely the PAW will be compromised.
4. Secure your domain controllers
Domain controllers are a prime target for attackers since it holds the sensitive account information used in the majority of enterprise organizations today. There are several steps you can take to at least increase the security of your domain controllers. These include:
- Apply security updates and patches to your domain controllers
- Use the Server Core installation option instead of using the Desktop Experience for domain controllers
- If you are using physical domain controllers, keep these secure and separate from the rest of your physical infrastructure (separate racks, etc).
- Use a TPM devie and BitLocker Drive Encryption for your domain controllers
- Use read only domain controllers (RODCs) at a ROBO location where you can’t guarantee the physical security of your DCs
- If you run DCs as VMs, run these on separate virtualized hosts
- Use virtualization security technologies such as the Hyper-V shielded VM running on guarded fabric
- Use Windows Defender Device Guard
- Limit RDP connections so these are limited to Privileged Access Workstations, described above
- Block Internet access from domain controllers
5. Analyze security configuration with the Security Compliance Toolkit
The Microsoft Security Compliance Toolkit (SCT) is a set of tools for downloading and implementing security configuration baselines. it also allows comparing your current GPOs to the recommended GPO security baselines. It also provides Policy Analyzer and Local Group Policy Object (LGPO) tools to manage GPO settings.
Download the Microsoft Security Compliance Toolkit here:
6. Secure SMB traffic
Encryption is important whenever sensitive information is moved by using the SMB protocol. Windows Server 2022 supports the highest levels of encryption for the most secure file transfers using SMB available.
Windows Server 2022 now supports AES-256-GCM and AES-256-CCM cryptographic suites for SMB encryption. It will automatically negotiate this more advanced cipher method when connecting to another computer that also supports it (Windows 11), and it can also be mandated through Group Policy. For down-level compatibility, Windows Server still supports AES-128. AES-128-GMAC signing now also accelerates signing performance.
Wrapping Up
Hopefully, this Windows Server 2022 Security Hardening best practices will help make your environment more secure. Security is about the “layers of an onion” effect. It takes more than one layer of security to be effective. Implementing the recommended security best practices goes a long way in helping to secure environments from modern threats such as ransomware and others.
Take a look at the official Microsoft Windows Server Hardening guide here: