VMware NSX-T 3.2 Released New Features
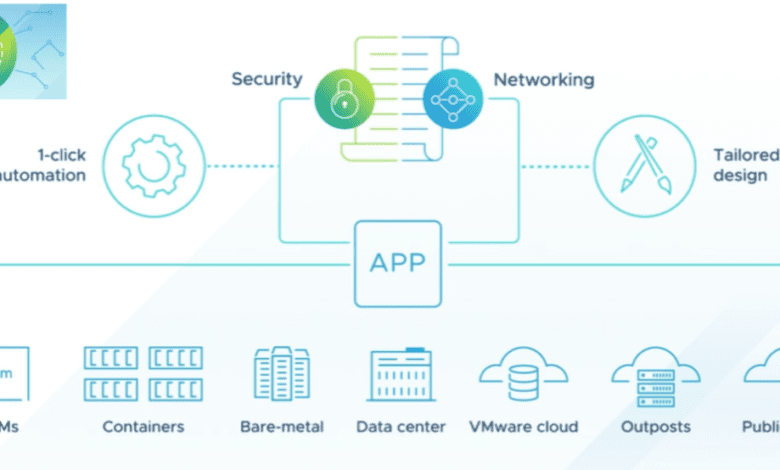
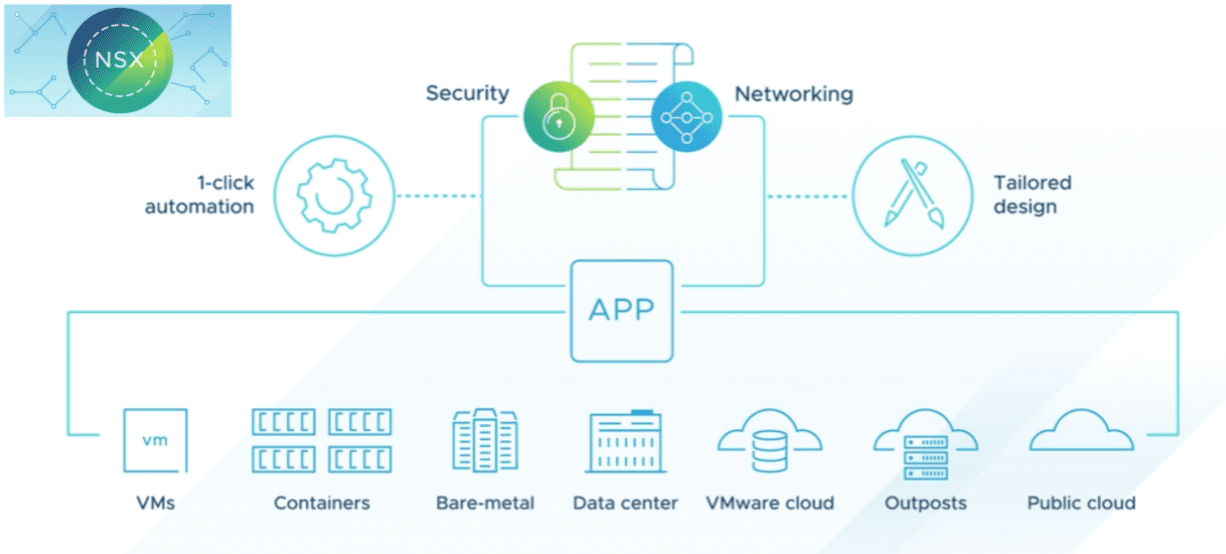
There is arguably not another software-defined networking solution that has had the impact of VMware NSX. It has revolutionized the way organizations can carry out network operations in their environments. NSX-t of course is the way forward from NSX-V since NSX-T is the multi-cloud aware modern NSX solution that will move forward with both vSphere and multi-cloud solutions. Each release of NSX brings more features and functionality for the enterprise datacenter and, importantly, new security features. Let’s take a look at VMware NSX-T 3.2 released new features and see what this version of NSX brings to the table.
VMware NSX-T 3.2 Released New Features
The VMware NSX-T release is massive and brings great new features and capabilities across many different fronts, including:
- Multi-cloud security
- Networking and policy enhancements
- Simplified network provisioning and operations
Multi-cloud security
Most organizations have resources across many different clouds, hybrid cloud, multi-cloud, etc. Having a seamless single-pane-of-glass interface that can secure networking across multiple clouds is hard to come by outside of VMware NSX-T. NSX-T 3.2 makes it easy to enable Zero Trust application access across multi-cloud environments.
It enables securing traffic across applications and individual workloads with security controls that check all the right boxes:
- Consistency
- Automation
- Attached to the workload
- Elastic in scale
One of the cool new features that is integrated directly into the NSX Distributed Firewall (DFW) is Network traffic analysis (NTA) and sandboxing solutions. In classic NSX form, NSX-T 3.2 eliminates network hairpins by distributing the NTA across your ESXi hypervisors in the cluster.
When you combine this with the capabilities of the distributed IDS/IPS that were released a few versions back, SecOps can now have the entire security stack virtualized and eliminate blind spots. It also allows security policies and controls to follow the workflows throughout their lifecycle.
New with NSX-T 3.2 is an enhanced Gateway Firewall that provides software-based gateway services with L2-L7. One of the great new features is Distributed Malware Prevention. NSX-T 3.2 provides the industry’s first distributed malware solution, leveraging the integration with Lastline, a distributed firewall embedded within the hypervisor kernel that can identify known and zero-day attacks.
This includes URL filtering and Advanced Threat Protection (ATP) with malware analysis and sandboxing. It also allows organizations to extend security controls to protect:
- Physical workloads
- Data center perimeter
- Public cloud edge
All traffic directions are covered by the solution, including east-west and north-south while being centrally managed from NSX Intelligence.
With NSX-T 3.2, VMware has now integrated the NSX Network Detection and Response (NDR) solution into NSX Intelligence. This allows signal correlation between IDS/IPS, NTA, and the sandbox to identify intrusions. It now offers other benefits, including:
- Scale-out performance
- Improved firewall rule recommendations
- Simplified and automated network segmentation across application traffic
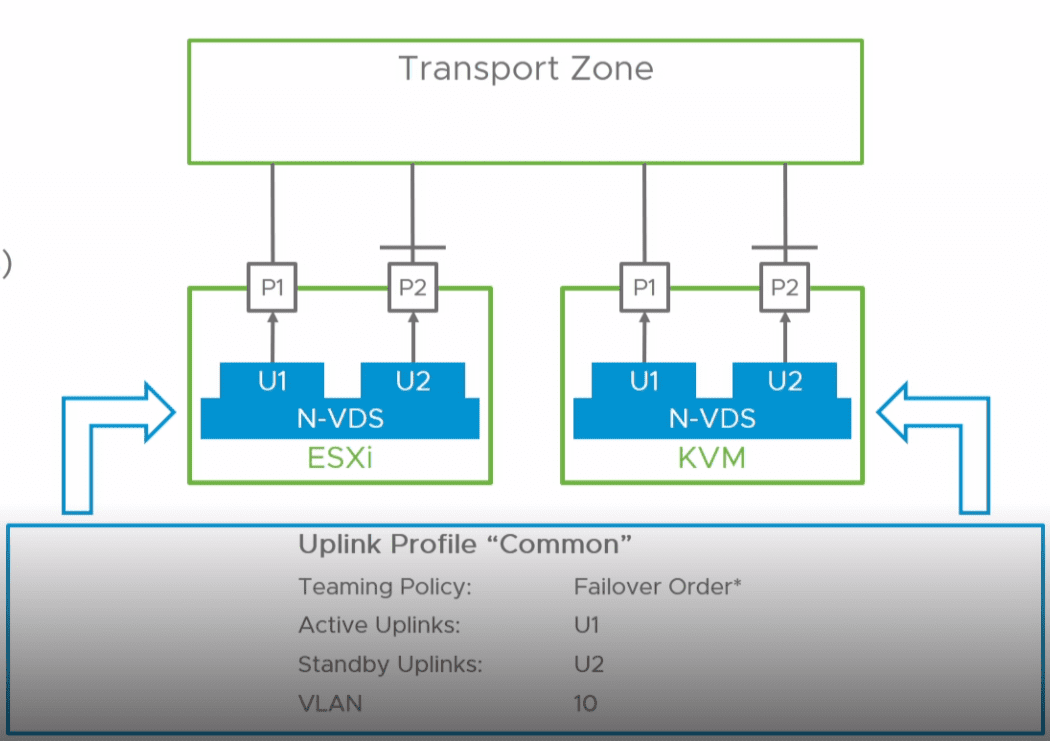
VMware has been collapsing down the once specialized N-VDS switch back down to work with the built-in core networking found in vSphere which is a great move. Further improvements in NSX-T 3.2 include the NSX Distributed Firewall now supporting workloads deployed on Distributed Port Groups on a VDS switch.
It means customers can deploy the NSX firewall without reworking their vSphere Distributed Switch infrastructure. Now, you can also leverage the Distributed Firewall capabilities with VDS-based VLAN networks without having to convert switch ports to N-VDS, or deploy overlays. All of the changes mean simplified architectures which is exponentially beneficial.
Networking and Policy Enhancements
There are several new advancements in the NSX-T 3.2 release that help to simplify network configuration and management across cloud environments, private or public.
Now, with NSX-T 3.2, administrators can define Antrea networking and security policies for containers from NSX-T Manager. Policies can be applied to Kubernetes clusters running Antrea 1.3.1-1.2.2 using the interworking controller. NSX automatically gathers Kubernetes objects like pods, namespaces, and services. It tags these so they can be selected in Distributed Firewall policies.
For troubleshooting purposes, NSX-T 3.2 can manage Antrea Traceflow and also collect log bundles from Kubernetes clusters using Antrea.
The NSX Migration Coordinator continues to become more polished to support customer-defined NSX topologies, larger scale, and new features such as VMware Integrated OpenStack (VIO), OSPF fixed topologies, guest introspection for supported partners, and other identity-based firewalls (IDFW/RDSH) configurations.
NSX Federation is a great new feature introduced with NSX-T 3.0 that brings the seamless cloud operating model to NSX. It allows operators to manage a multi-site network as a single entity while synchronizing the operational state across locations. This has been enhanced with NSX-T 3.2. Now it supports VM tag replication so VMs replicated and restarted in the process of a Disaster Recovery event retain their security policies.
Streamlined network provisioning and operations
When you look at how far things have come since the early days of deploying NSX, wow, they have come a long way. Now with NSX-T 3.2, admins can deploy NSX-T manager, and network security configurations directly from the vSphere Client. This greatly simplifies NSX operations.
Another streamlined area with NSX-T 3.2 is installing and configuring the NSX Advanced Load Balancer (ALB). It now has much tighter integration with the NSX Manager. The NSX Manager UI can be used to install and configure NSX Advanced Load Balancer controllers. The Migration Coordinator can now handle migrating load blanacing solutions from NSX for vSphere to the VMware NSX Advanced Load Balancer.
There is now much tighter integration between vRealize Network Insight (vRNI) 6.4 and NSX-T Federation. This integration provides network visibility across multiple NSX-T data centers at global, regional, and local site levels.
There are new capabilities to optimize application performance and traffic flows. The vRNI 6.4 solution now supports NSX-T Distributed Firewall (DFW) on Distributed Port Groups. It allows easily seeing unprotected flows, Name Space (NS) groups, and distributed firewall rules on existing VLAN DVPGs in a topology. There is also new licensing terms available for vRNI 6.4 for 1 & 3 years.
New Edge and L3 time-series monitoring allows seeing a time-series view of Edge and L3 metrics, including:
- CPU
- Memory
- Disk usage
- Packets per second
- Bytes per second
- Pack drop rate
- others
This helps to gather KPIs for your software-defined network environment. There are several new events and alarms to enhance troubleshooting across the environment.
Wrapping Up
This is another landmark NSX-T release, providing modern features for modern workloads and helping organizations solve the ever-evolving security challenges in the enterprise datacenter and across clouds. The new features will definitely give businesses the tools needed to make it much more difficult for the bad guys to compromise an environment.
Take a look at the official press releases for NSX-T 3.2 here: