Patch two new Active Directory privilege escalation bugs
If Log4j wasn’t enough, Microsoft has upped the alert on two new Active Directory bugs that now have a PoC tool in the wild. What are the new Active Directory bugs that need attention from enterprise customers? Let’s take a look at the why and how to patch two new Active Directory privilege escalation bugs and see some potential considerations from the patch.
SAM Account Name impersonation vulnerability
As it turns out, these are not zero-day new. The two Active Directory security vulnerabilities were patched in the November 2021 security update cycle. There are two specific CVEs to give attention to. These are CVE-2021-42287 and CVE-2021-42278. Both of the patched CVEs are described as Windows Active Directory domain service privilege escalation vulnerabilities.
The potential criticality of these particular CVEs has now been escalated as there is now a proof-of-concept tool in the wild for these CVEs. It means the bad guys now have public access to a tool to actively exploit the vulnerability.
The alarming thing about the two CVEs is they can be combined to provide an attacker a straight path to escalating privileges to a Domain Admin. It only requires the attacker to compromise an underprivileged, regular user. So, it increases the likelihood of a successful attack using the vulnerabilities, since compromising a normal user account isn’t that difficult.
The first part of the compromise is possible due to the way an unpatched domain controller allows a normal user to change the sAMAccountName attribute. By default, a normal user has permissions to modify a machine account for up to 10 machines coming from the ability for a normal user to add machines to the domain.
Active Directory SAM Account Name attack steps
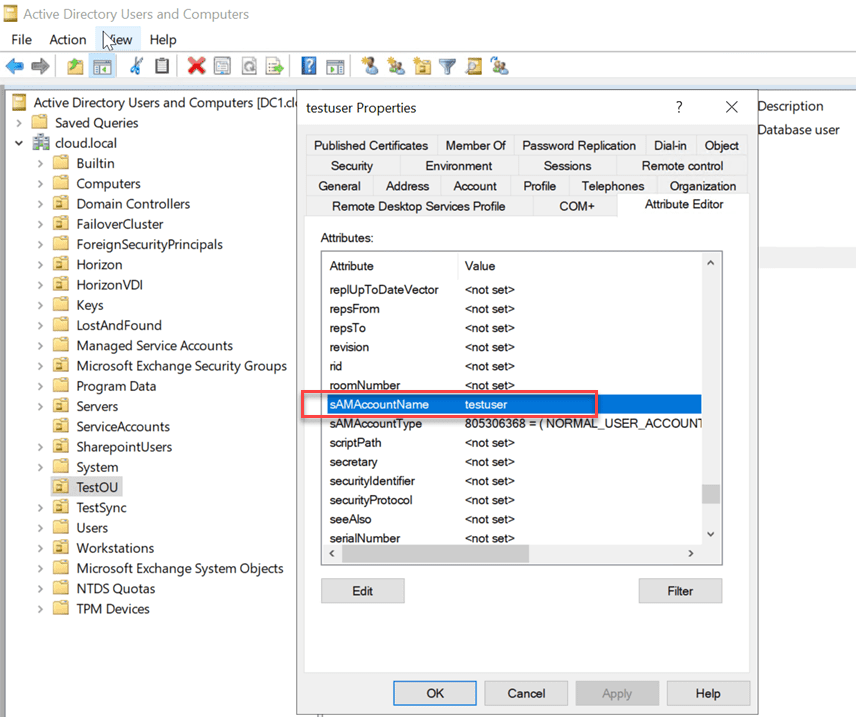
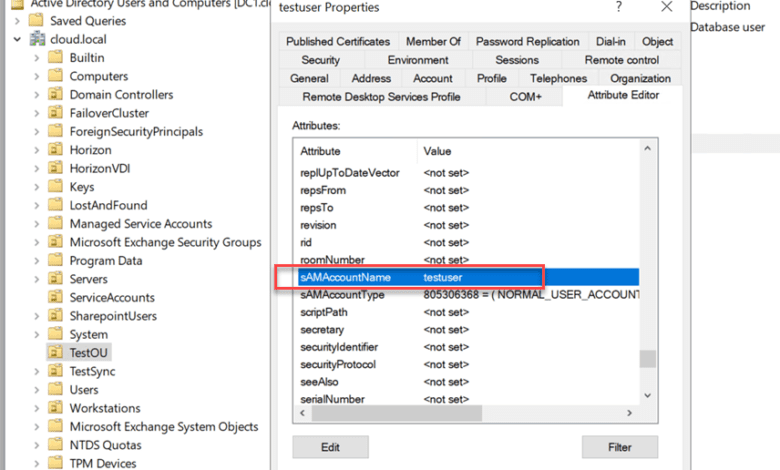
Microsoft notes that sAMAccountName attributes usually end with a “$” sign. This was historically used to differentiate between user and computer objects. With unpatched systems, there are no restrictions of validations for changing the attribute. Below is a look at where you can find the sAMAccountName in Active Directory Users and Computers. You have to turn on Advanced Features in ADUC under the View menu. Then, you will see an additional tab called Attributed Editor. In this tab, you can view the AD attributes assigned to objects.
With this capability, an attacker has the potential to impersonate domain controllers directly. The scenario laid out by Microsoft goes this way:
- A domain controller in the environment has the SAM account name of DC1$
- An attacker can create a new machine account and rename its SAM account name to DC1
- a Ticket Granting Ticket (TGT) is requested
- It is renamed to a different name
- A Ticket Granting Service ticket is requested
- The TGT in hand is used for the request
- The KDC will fail the lookup when processing the TGS request
- The KDC will perform another lookup appending a trailing $
- The lookup succeeds
- The KDC will issue the ticket using the privileges of DC1$
By using both CVEs, it is easy to see how an attacker can gain domain admin user permissions in just a few steps and with little effort.
Patch two new Active Directory privilege escalation bugs
Take note of the following links containing the relevant patch information for the specific vulnerabilities:
- KB5008102—Active Directory Security Accounts Manager hardening changes (CVE-2021-42278)
- KB5008380—Authentication updates (CVE-2021-42287)
- KB5008602(OS Build 17763.2305) Out-of-band
Be aware of Active Directory changes with November 2021 patches
While the patches for these two vulnerabilities are absolutely critical and necessary for administrators to give attention to, there are also things to be aware of with the newly introduced domain controller patches in the November 2021 security cycle. What are these?
The fixes introduced in the November 2021 patch release will effectively break any unpatched domain controllers from July 2022 onward. By break, it means that domain controllers with the latest patches after July 2022 will not be able to communicate with domain controllers that do not have at least the November 2021 patch in place.
Note the following taken from the Microsoft KB: KB5008380—Authentication updates (CVE-2021-42287) (microsoft.com)
The July 12, 2022 release will transition all Active Directory domain controllers into the Enforcement phase. The Enforcement phase will also remove the PacRequestorEnforcement registry key completely. As a result, Windows domain controllers that have installed the July 12, 2022 update will no longer be compatible with:
- Domain controllers that did not install the November 9, 2021 or later updates.
- Domain controllers that installed the November 9, 2021 or later updates but have not yet installed the April 12, 2022 update AND who have a PacRequestorEnforcement registry value of 0.
However, Windows domain controllers that have installed the July 12, 2022 update will remain compatible with:
- Windows domain controllers that have installed the July 12, 2022 or later updates
- Window domain controllers that have installed the November 9th, 2021 or later updates and have a PacRequestorEnforcement value or either 1 or 2
Wrapping Up
It seems like we are saying this a lot lately, but these two Microsoft Active Directory Domain Services bugs are bad. They are not too difficult to exploit by an attacker and provide an easy path for malicious threat actors to totally take control of your ADDS domain. The priority to patch two new Active Directory privilege escalation bugs need to be remediated quickly.
However, as mentioned, there is due consideration that needs to be given to the November patches for Active Directory as these set in motion settings that will lead to interoperability issues mid-2022 if patches have not been consistently applied across your Active Directory landscape.