Patch vCenter Server Critical Security Bug CVE-2021-22005 Download
Security concerns related to our VMware vSphere environments keep us up at night, and with good reason. Critical security bugs that affect your hypervisor virtualization environment can give an attacker the “keys to the kingdom.” It could potentially allow them to “own” your environment. A new critical vSphere vulnerability that specifically affects vCenter Server is now in the wild, and it is a bad one. It is being tracked as CVE-2021-22005 and it has a CVSS 3.1 severity rating of 9.8/10 – just about as bad as it gets. Let’s take a look at how to Patch vCenter Server critical security bug download. We will also take a look at workarounds to the critical issue.
What is the critical CVE-2021-22005 vCenter Server security bug?
Let’s see what the bug is all about. First, the vulnerability documented in CVE-2021-22005 is a critical vulnerability that allows attackers with only network-level access to upload arbitrary code using the vCenter Server Analytics service. A specially crafted file can allow an attacker to run commands. Again, it only requires access to port 443. as part of the official VMware security advisory, there is an entire bundle of vulnerabilities that are fixed in the latest patch for vCenter Server 6.7 and 7.0.
These include the following CVEs:
- CVE-2021-21991
- CVE-2021-21992
- CVE-2021-21993
- CVE-2021-22006
- CVE-2021-22007
- CVE-2021-22008
- CVE-2021-22009
- CVE-2021-22010
- CVE-2021-22014
- CVE-2021-22015
- CVE-2021-22019
- CVE-2021-22020
The ones in the above list are classified as Important with a CVSS score of 4.3-8.8.
Where can you download the fixed versions?
Follow the links below for the fixed versions of affected products:
vCenter Server 7.0 U2d
Downloads and Documentation:
https://customerconnect.vmware.com/downloads/details?downloadGroup=VC70U2D&productId=974&rPId=74352
https://docs.vmware.com/en/VMware-vSphere/7.0/rn/vsphere-vcenter-server-70u2d-release-notes.html
vCenter Server 6.7 U3o
Downloads and Documentation:
https://customerconnect.vmware.com/downloads/details?downloadGroup=VC67U3O&productId=742&rPId=73667
https://docs.vmware.com/en/VMware-vSphere/6.7/rn/vsphere-vcenter-server-67u3o-release-notes.html
vCenter Server 6.5 U3q
Downloads and Documentation:
https://customerconnect.vmware.com/downloads/details?downloadGroup=VC65U3Q&productId=614&rPId=74057
https://docs.vmware.com/en/VMware-vSphere/6.5/rn/vsphere-vcenter-server-65u3q-release-notes.html
VMware vCloud Foundation 4.3.1
Downloads and Documentation:
https://docs.vmware.com/en/VMware-Cloud-Foundation/4.3.1/rn/VMware-Cloud-Foundation-431-Release-Notes.html
VMware vCloud Foundation 3.10.2.2
Downloads and Documentation:
https://docs.vmware.com/en/VMware-Cloud-Foundation/3.10.2/rn/VMware-Cloud-Foundation-3102-Release-Notes.html
Patch vCenter Server Critical Security Bug CVE-2021-22005 Download
There are a few options when it comes to patching vCenter Server. The two we will cover are:
- VAMI
- Patch from ISO
VAMI
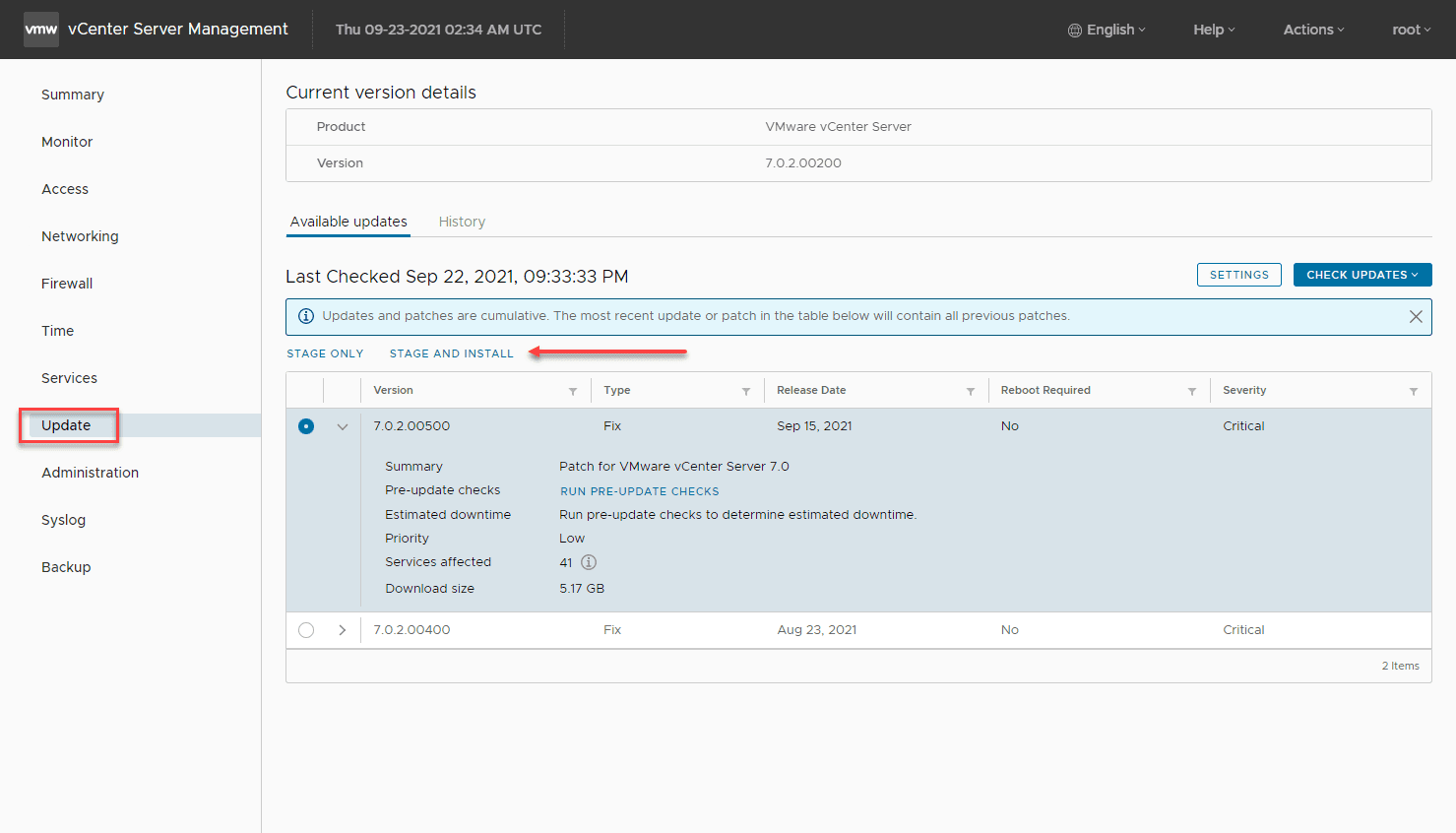
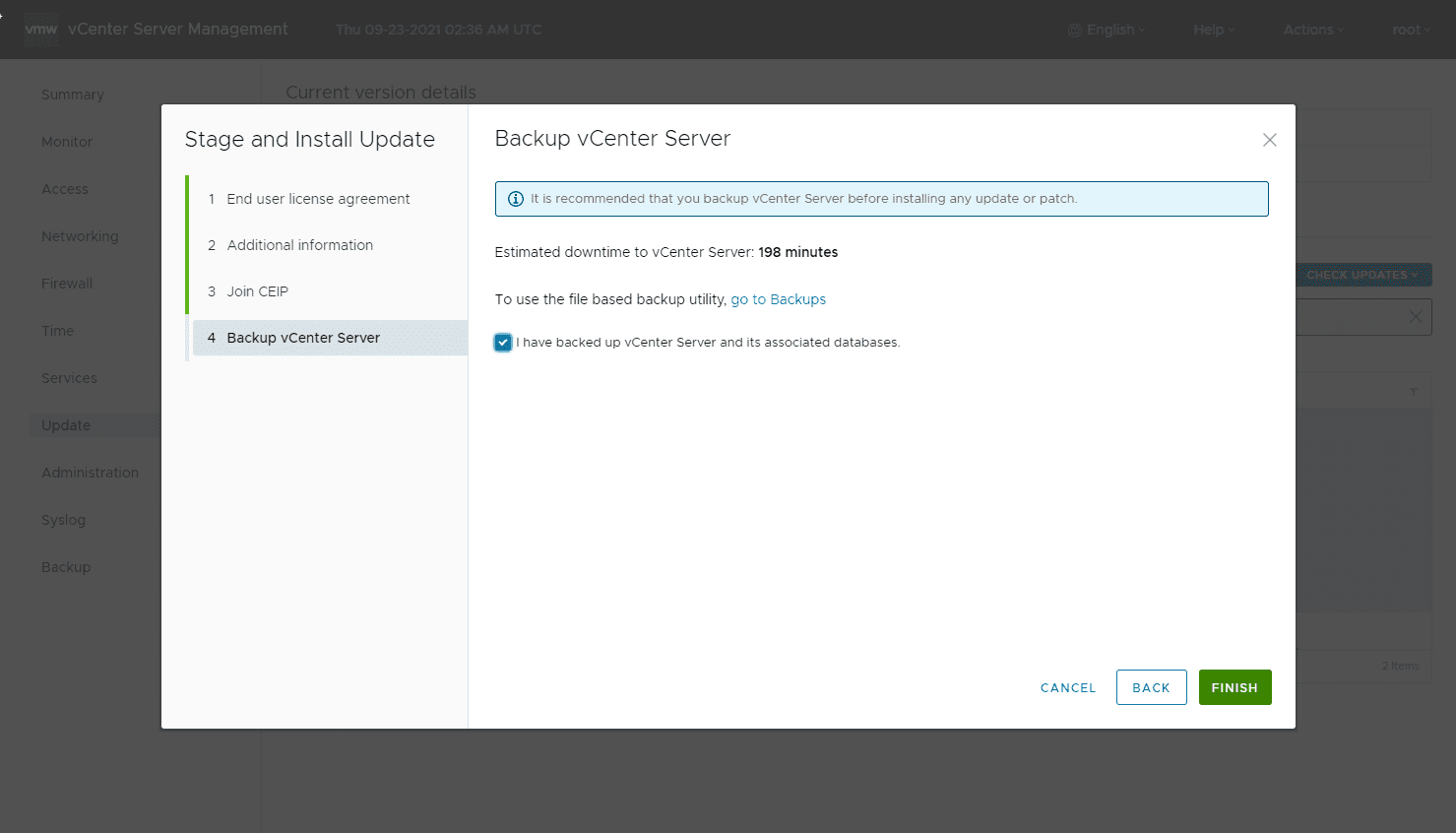
The most obvious choice for patching your vCenter Server is using the VAMI out-of-band administrator interface for your vCenter Server. By simply checking the Update dashboard, you can pull the latest patch from online and upgrade your vCenter Server. After you click the Update dashboard, click the Check Updates from CDROM and URL. Then verify you are seeing the 7.0.2.00500 patch listed. Click Stage and Install.
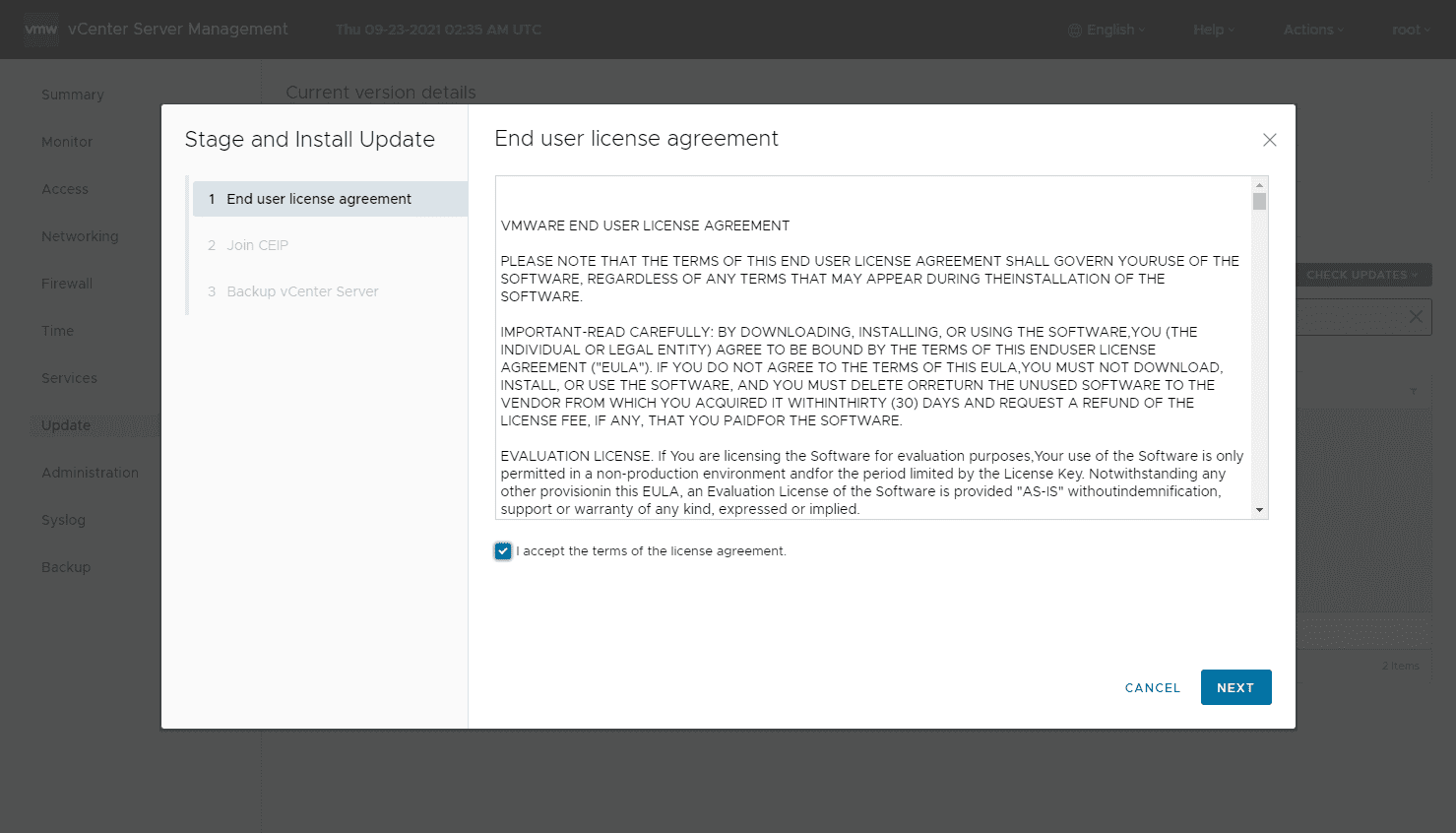
This kicks off the wizard with the EULA first.
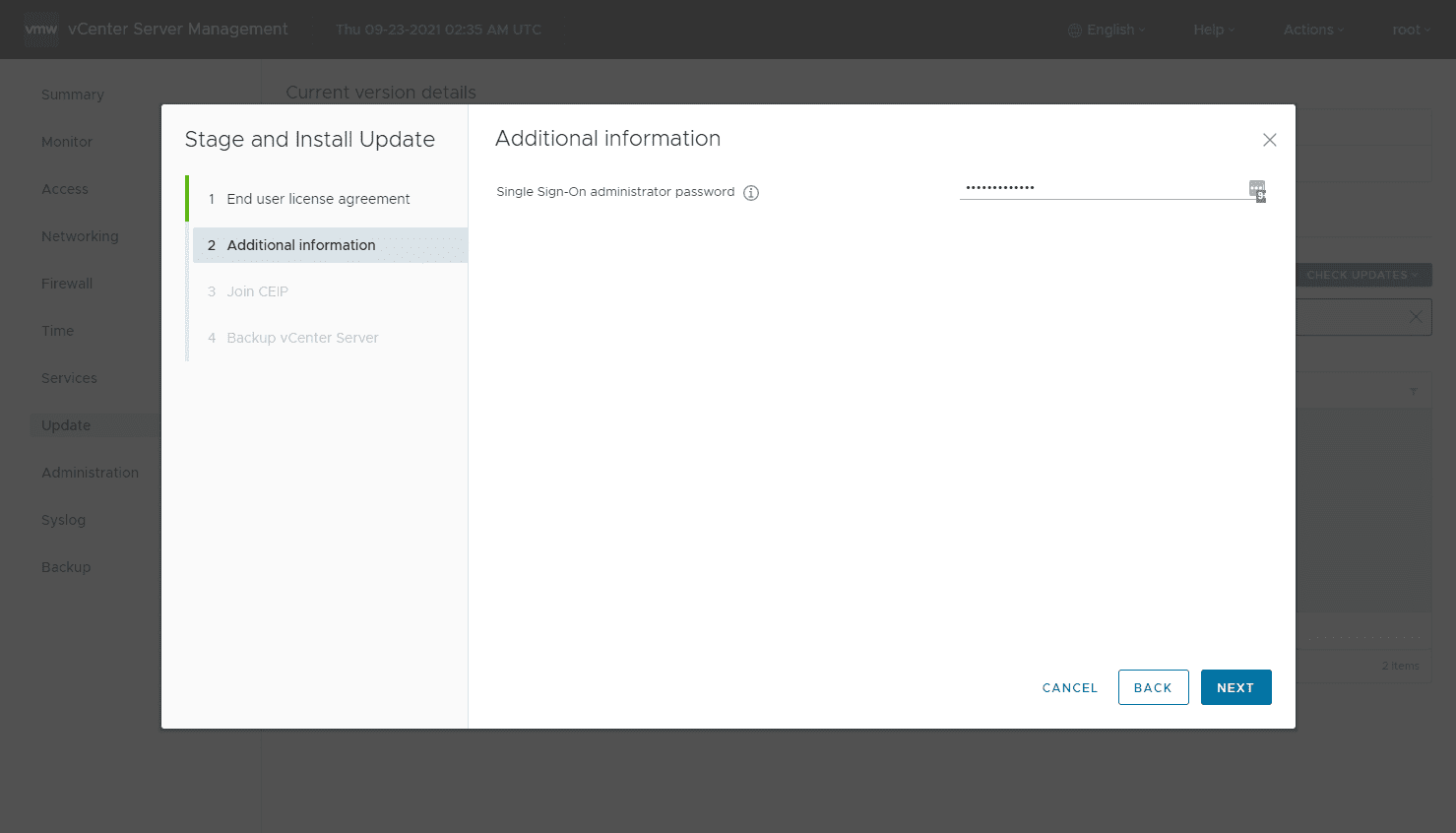
Enter your SSO administrator password to move forward.
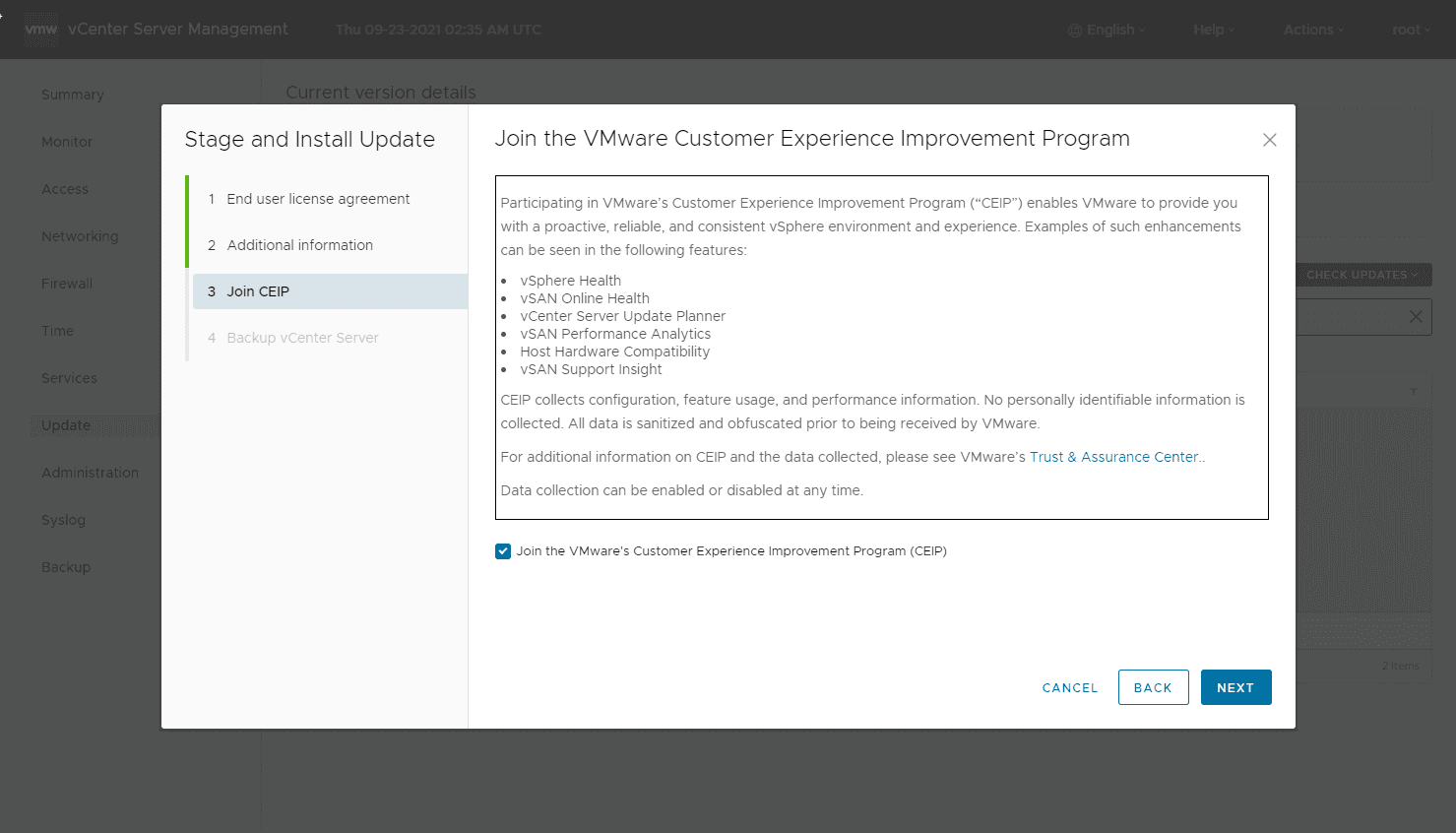
Make your choice on joining the CEIP program.
Verify that you have backed up your vCenter Server. Click Finish.
After this, the patch will download, stage, and install.
Patch from ISO
For the patch from ISO approach, the workflow is the following:
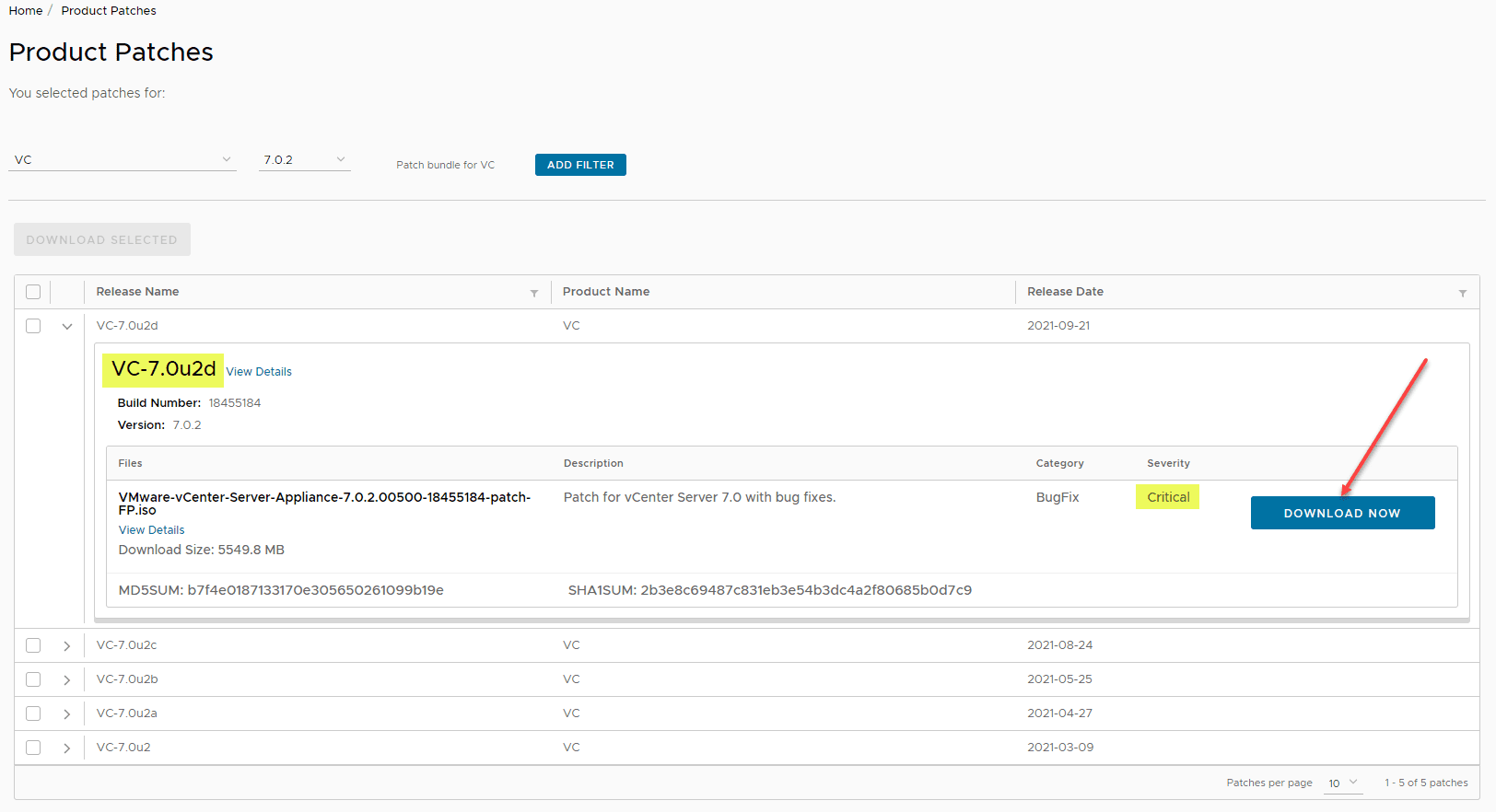
- Download the Appliance patch ISO – https://my.vmware.com/group/vmware/patch
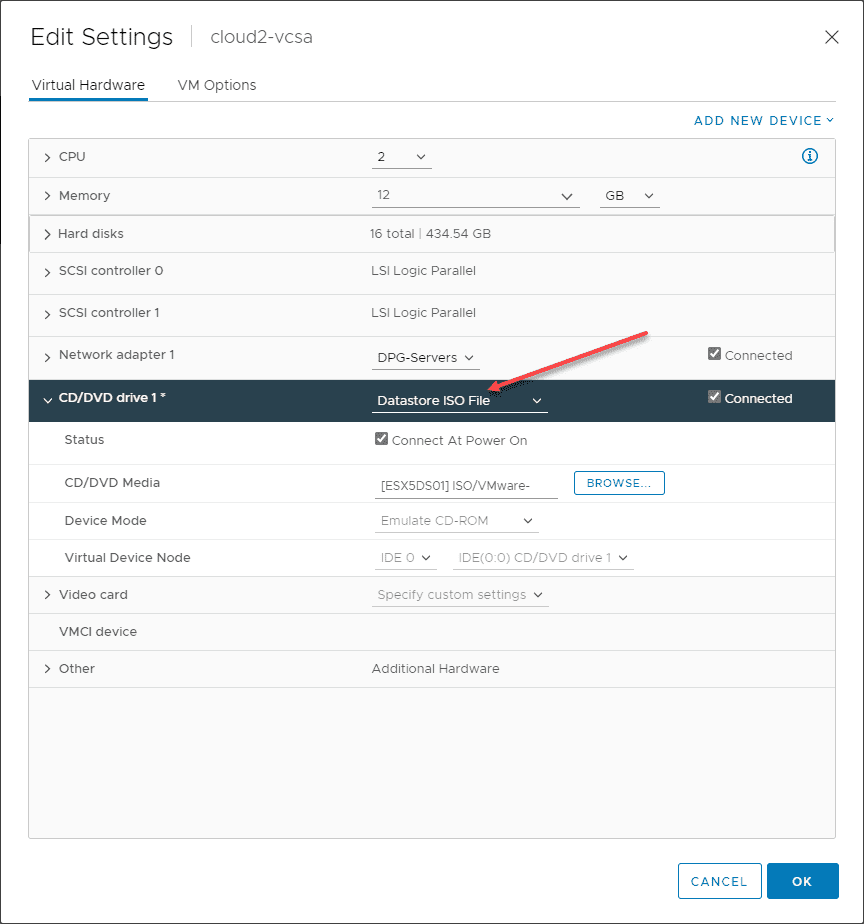
- Copy the ISO to a datastore or content library that you can mount to your VCSA appliance CD-ROM drive via the vSphere Client.
- Once the ISO file is mounted, SSH into the VCSA appliance and run the necessary commands to manually patch VMware vCenter Server VCSA with ISO that was uploaded
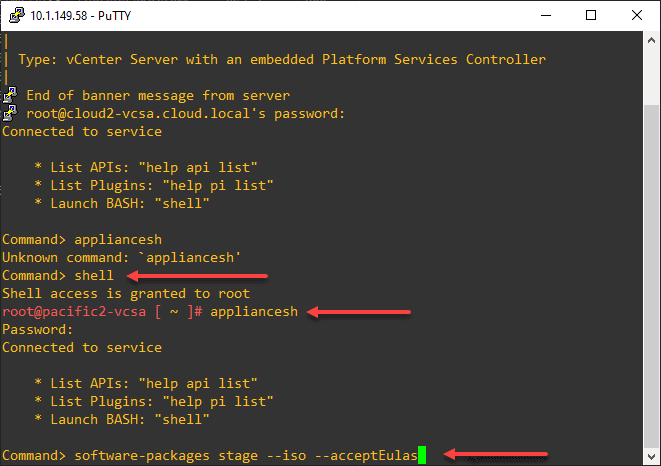
Once you have the ISO downloaded and mounted, SSH into your vCenter Server appliance and run the following commands:
appliancesh
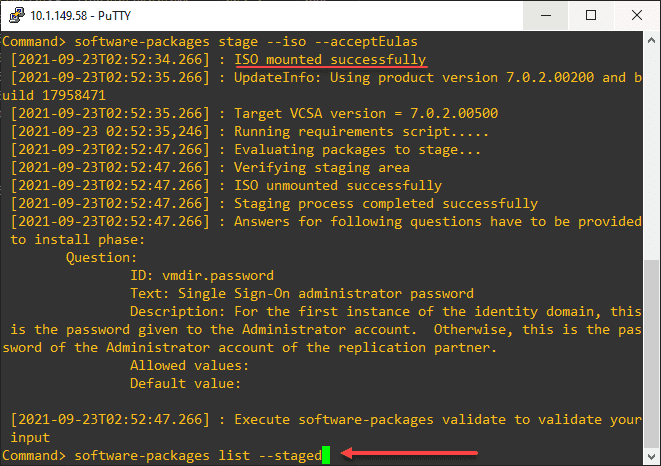
software-packages stage --iso --acceptEulas
software-packages list --staged
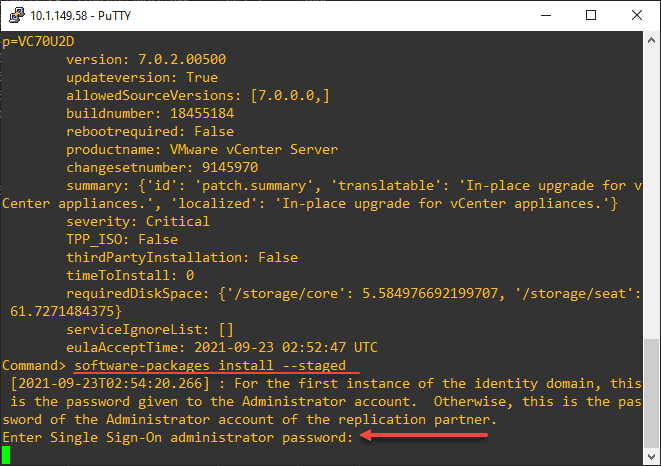
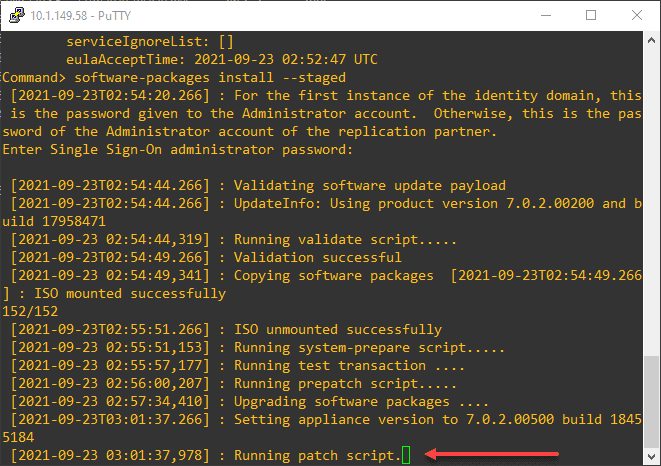
software-packages install --stagedBelow is a view of my running the commands listed above sequentially. First, SSH into the vCenter Server appliance and enter the appliancesh command.
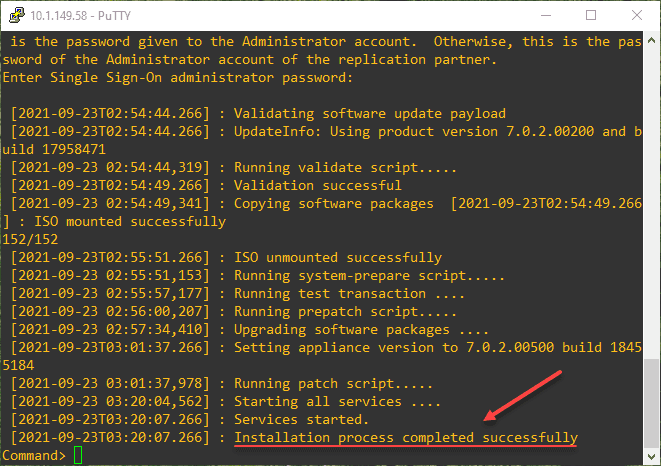
software-packages stage --iso --acceptEulassoftware-packages list --stagedsoftware-packages install --stagedAfter some time, the upgrade process will complete successfully. It will note if a reboot is necessary.
vCenter Server Security Best Practices
Take a look at the video I posted below covering Center Server security best practices.
Workaround to CVE-2021-22005
Take a look at my blog post and video on how to leverage the vCenter Server firewall to remediate vCenter Server security vulnerabilities:
Final thoughts
This is a bad one folks and one that should certainly get your attention as shown in this Patch vCenter Server Critical Security Bug CVE-2021-22005 Download. Keeping your environment patched with security patches and following best practices to segment your network and secure your vCenter Server from a network perspective will help ensure your attack surface is minimal, even if a new vulnerability is discovered.