Office 365 Ransomware protection with SpinOne New Features
Companies are moving to the cloud in drove for housing many business-critical processes, including employee collaboration and productivity tools. The pandemic has taught us many things about how employees can work effectively. They don’t have to be located on-premises if they have the tools that allow them to carry out their business productivity tasks effectively. Moving to the cloud has been accelerated by the need for employees to work from anywhere in highly distributed teams. Microsoft 365 has been the target of many cloud migrations with Microsoft Teams seeing huge adoption in the enterprise for the reasons mentioned. Cybersecurity in these cloud SaaS environments has come into clear focus. As ransomware and other extremely dangerous threats are targeting businesses, organizations need to be keenly focused on tightening the security of their cloud SaaS environments.
SpinOne is a great solution that provides arguably some of the best all-around features for protecting and securing your data in cloud SaaS environments like Google Workspace and Microsoft 365. Focusing on Microsoft 365, Spin has released new features that allow businesses to further simplify and strengthen their cybersecurity. Note how you can implement Office 365 Ransomware protection with SpinOne new features.
Ransomware encryption in the cloud?
Yes, ransomware can infect cloud-housed data. While many ransomware gangs are presently focused on on-premises data as they can often more quickly proliferate ransomware across on-premises servers, ransomware is no doubt going to begin targeting cloud SaaS data. Criminals know businesses are moving their critical data and apps to cloud SaaS and other solutions. So, to remain lucrative and extort money from businesses, cybercriminals will be following suit with this trend.
A ransomware attack in the cloud can happen due to various attack vectors. These include:
- Phishing emails
- File synchronization
- Malicious cloud applications
Phishing emails
Phishing emails are one of the most common ways that cybercriminals attempt to deliver ransomware to business environments. Hackers send emails to end-users that often masquerade as from a legitimate sender containing malicious attachments.
Note the following posted recently by ZDNet:
Cybersecurity researchers at Coveware analysed ransomware attacks during the second quarter of this year and have detailed how phishing attacks and RDP attacks are the most popular entry points for starting ransomware attacks. Part of the appeal for cyber criminals is that these are low-cost to carry out while also being effective.
Phishing attacks – where cyber criminals send emails containing a malicious attachment or direct victims towards a compromised website which delivers ransomware – have slightly grown in popularity over the last quarter, accounting for 42 percent of attacks.
File synchronization
File synchronization is generally not as prolific as the other ways in modern cloud environments. However, it can still be a path to files in OneDrive and other cloud environments becoming encrypted. This attack happens when an end-user who has a cloud synchronization app running like Google Drive or Microsoft OneDrive for Business gets infected with ransomware. When the local files get encrypted by the ransomware, this triggers a synchronization of the data to the cloud. Then the cloud copy is encrypted.
Malicious cloud applications
Malicious cloud applications are an increasingly popular way that ransomware infects cloud environments. Similar to phishing attacks, cybercriminals create malicious cloud applications that pose as legitimate applications. These trick end-users into granting OAuth permissions to the application which then has the ability to encrypt cloud data. OAuth access is dangerous as it bypasses two-factor authentication by default and must be manually revoked.
Other Cloud Cybersecurity Challenges
One of the dangers of ransomware is that it can encrypt files, without administrator visibility. IT and SecOps on-premises can be challenged to have the visibility needed. This problem often grows when organizations migrate to the cloud. A lack of visibility to cybersecurity issues in the cloud is a definite challenge.
Also, like on-premises environments, businesses often use multiple solutions with various overlapping features and numerous dashboards to administer and maintain. With this being said, simplifying the approach with a more robust solution that provides visibility in a single-pane-of-glass view is much more effective.
On top of the lack of visibility and overlapping tools, businesses today are also challenged from the standpoint of a lack of automated responses to cybersecurity events. Cybersecurity automation is absolutely essential to combat the plethora of cybersecurity threats facing enterprise cloud and hybrid cloud SaaS environments.
File Versioning is Limited
Cloud SaaS environments contain file versioning in the cloud that allows seeing a version history of files contained in cloud storage. Admins and users can then recover files and other Microsoft 365 data. However, file versioning has limitations in the protection it provides. The point in time versions can easily be deleted by any user who has write access to files. They can simply delete the entire version history.
In addition, file versioning is limited in the amount of time they are valid. The retention is mainly controlled by Microsoft and may not align with each individual business SLA.
SpinOne Accelerating Cloud SaaS Cybersecurity
There is a solution that caught my attention a few years back, called SpinBackup. It wasn’t just the average cloud SaaS backup, of which, now there are many cloud backup solutions. SpinOne, the evolution of SpinBackup, combines effective cloud backups with powerful cybersecurity features, as these go hand-in-hand. SpinOne stands alone in this space with the features and capabilities provided to organizations moving to the cloud.
It has been great to see how the product has continued to improve in the past couple of years. In 2021, Spin has already introduced several new features in Q2, with three more new capabilities to note. Let’s look at the following:
• Cloud monitor
• Data audit
• Security policies
• Add-ons
Cloud monitor
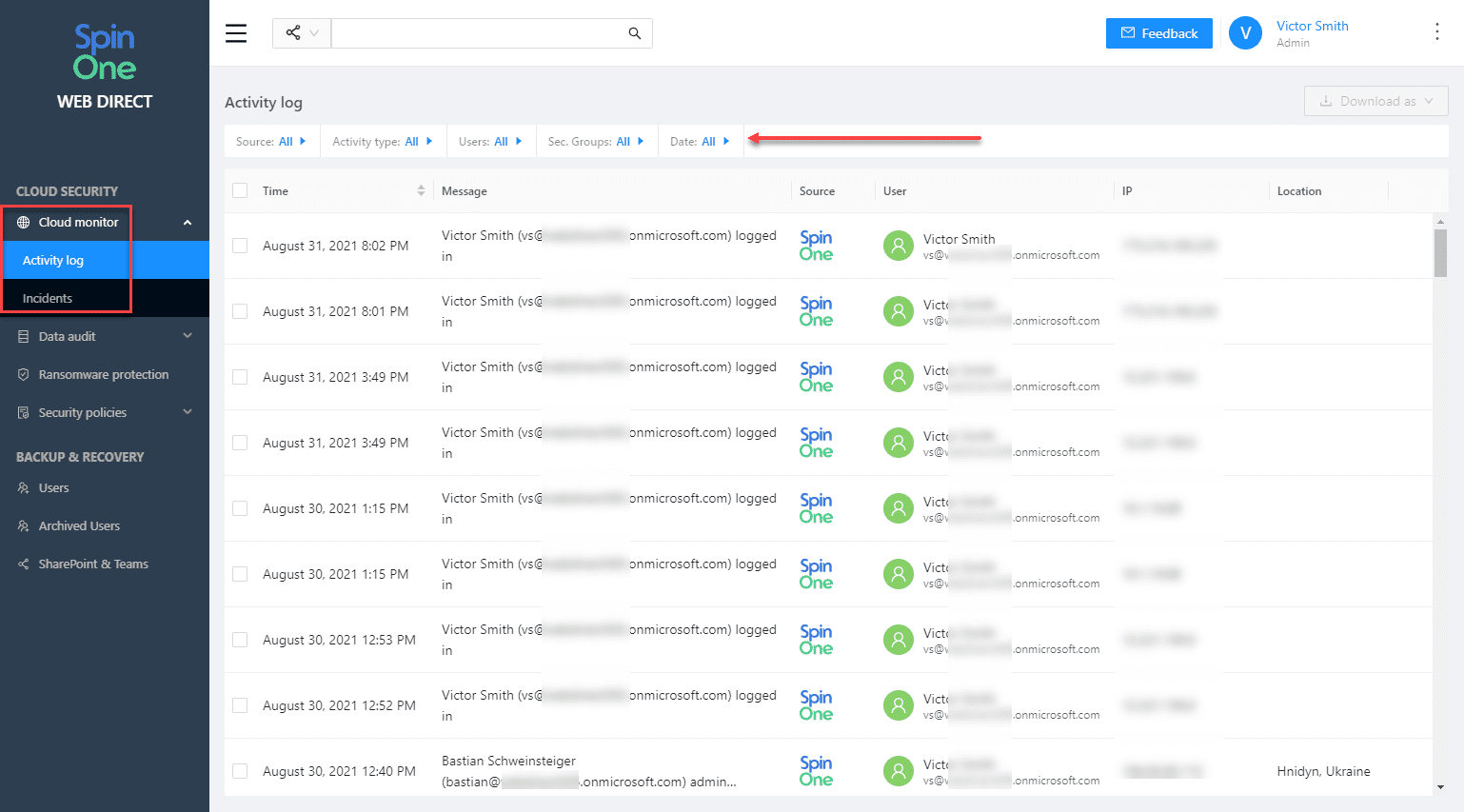
Cloud Monitor’s two child dashboards provide the following:
- Activity log – All monitored activity captured by Spin
- Incidents – Cybersecurity events captured by Spin
Cloud Monitor Activity log provides a view of activity across your Microsoft 365 organization. You can see:
- timestamps
- activity recorded
- source, user
- IP address
- IP geolocation information.
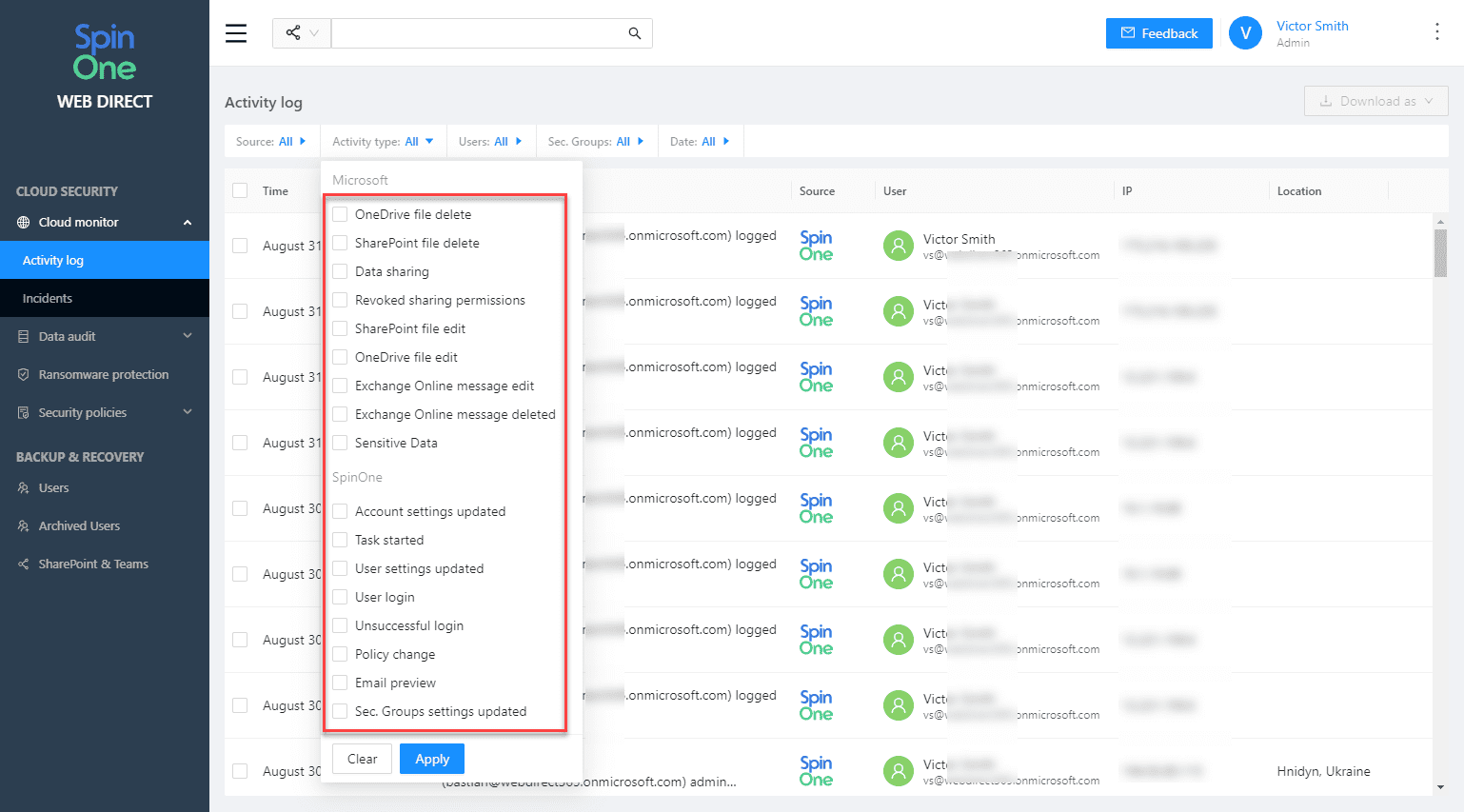
Also, note the filter menus at the top of the screen. You can look for specific data this way.
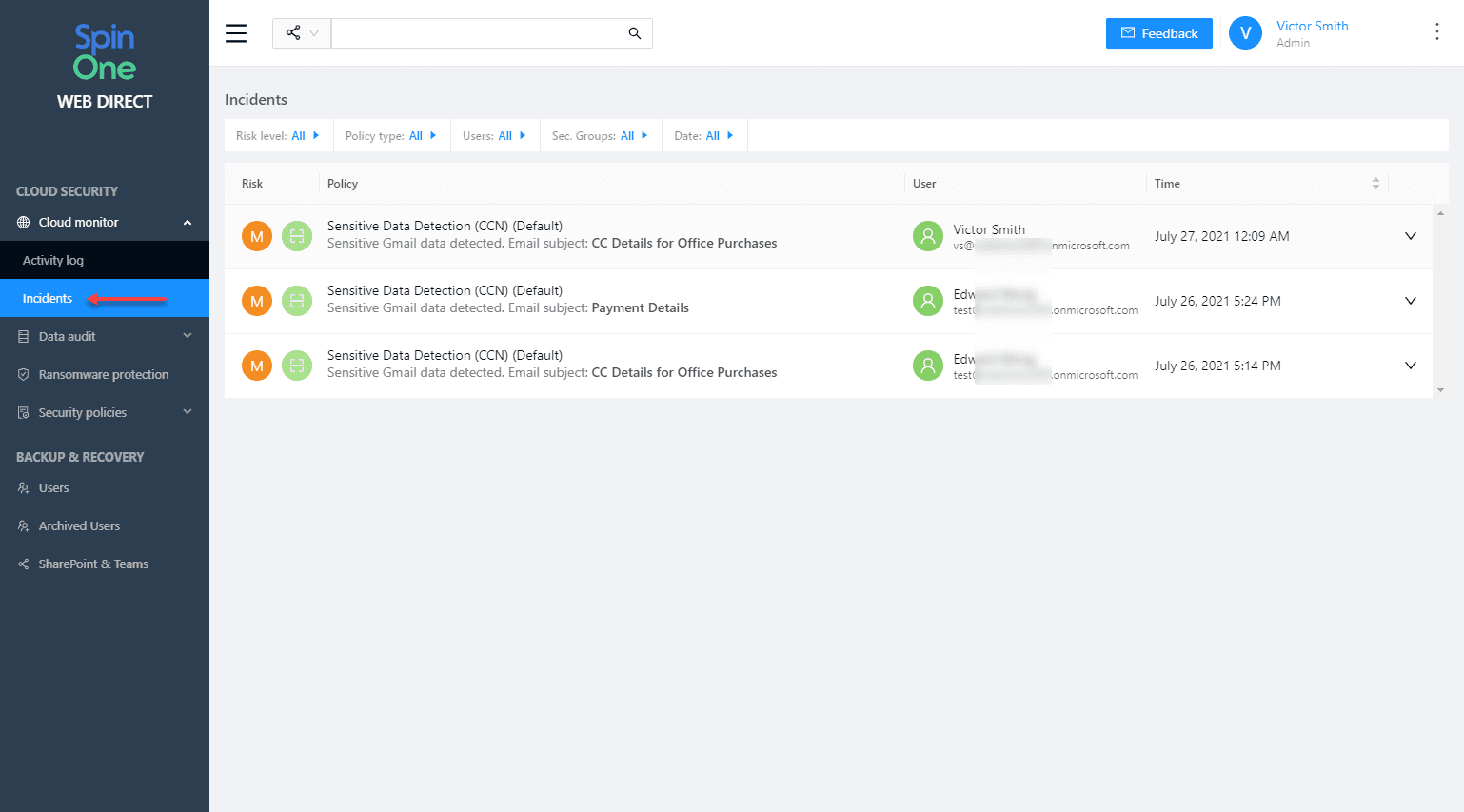
The Incidents dashboard includes the following incident types:
- Ransomware protection
- Shared items control
- Sensitive data detection
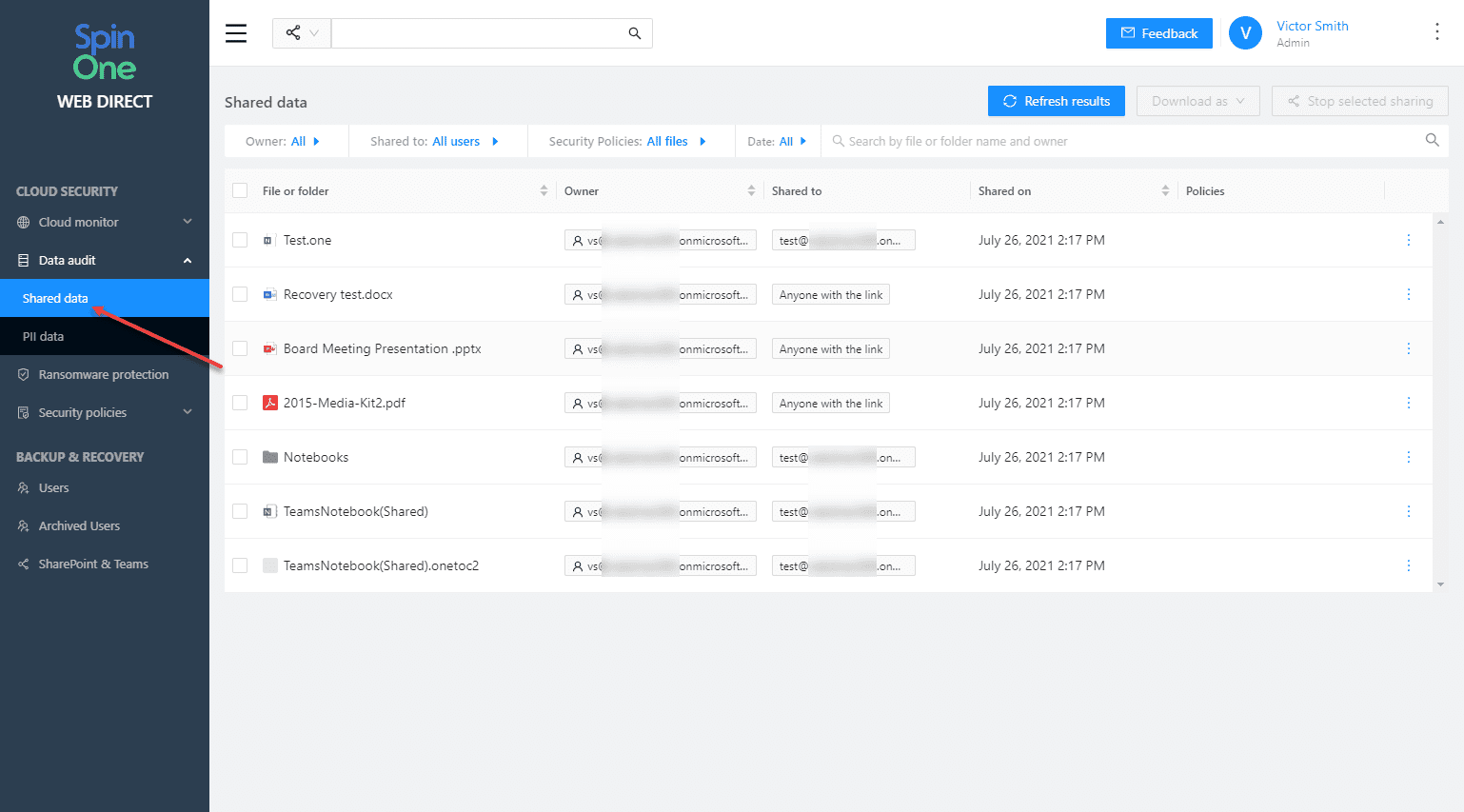
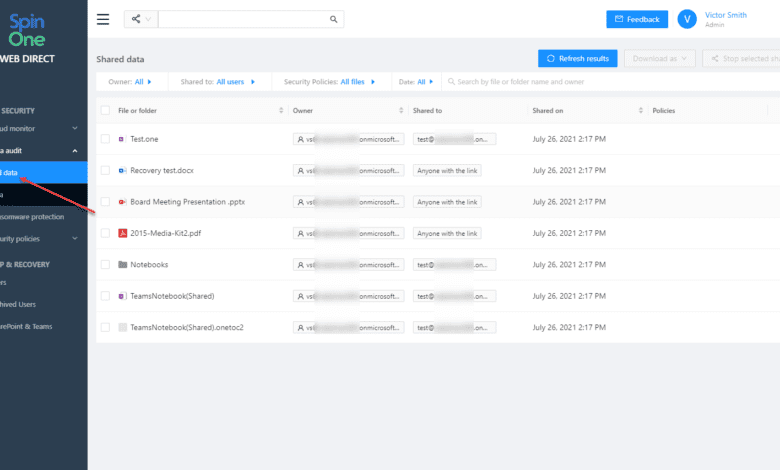
Data audit
Businesses today must keep a check on who data is shared with, by whom, when, and what type of data it is. SpinOne makes keeping an eye on data leakage with the Data Audit dashboard. Data Audit displays OneDrive information that is shared (files or folders) with others. You can see:
- Owner
- Who data is shared with
- When they were shared
- Policies
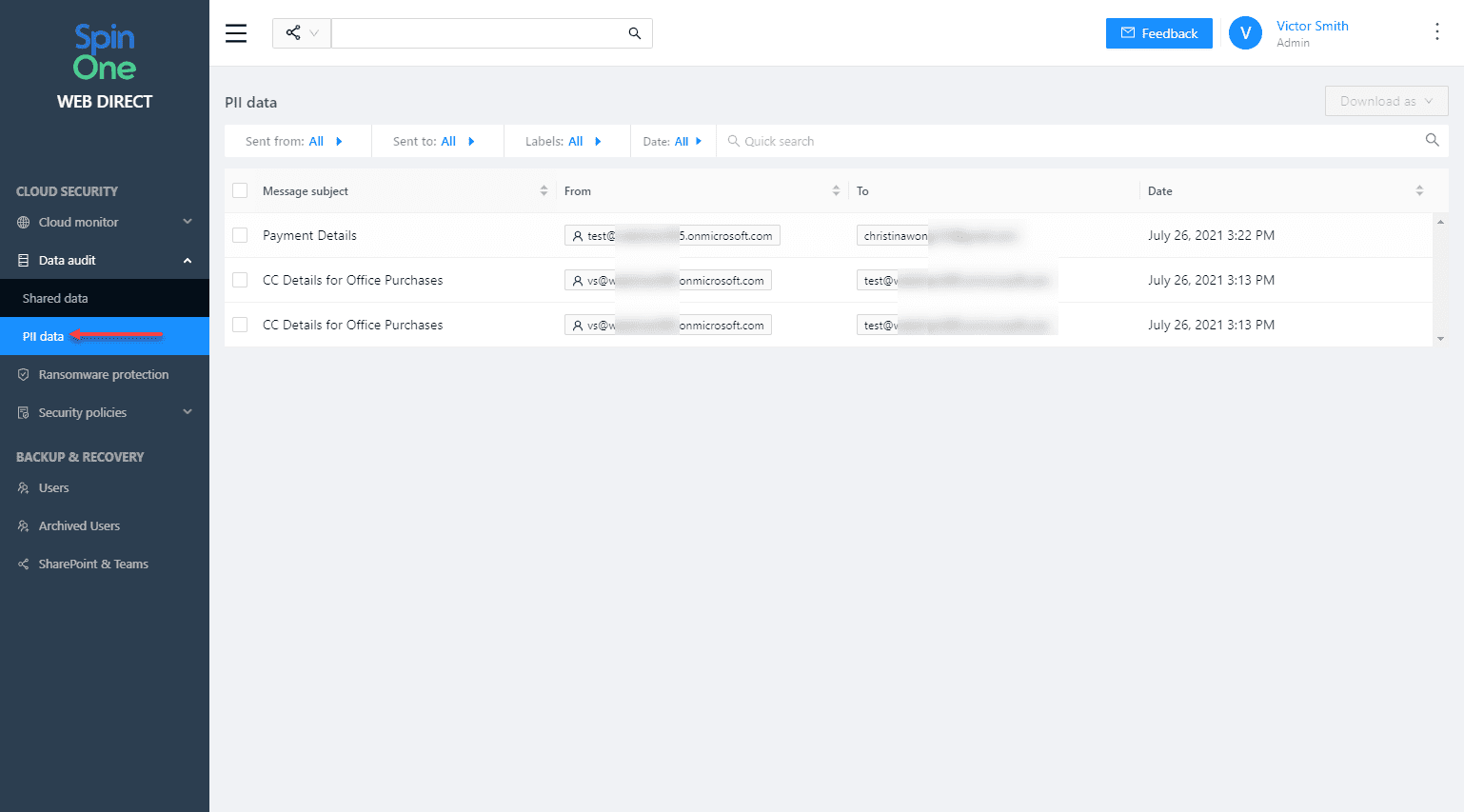
Using the PII dashboard you can have visibility to PII data contained in emails sent or received. SpinOne captures the information in redacted form.
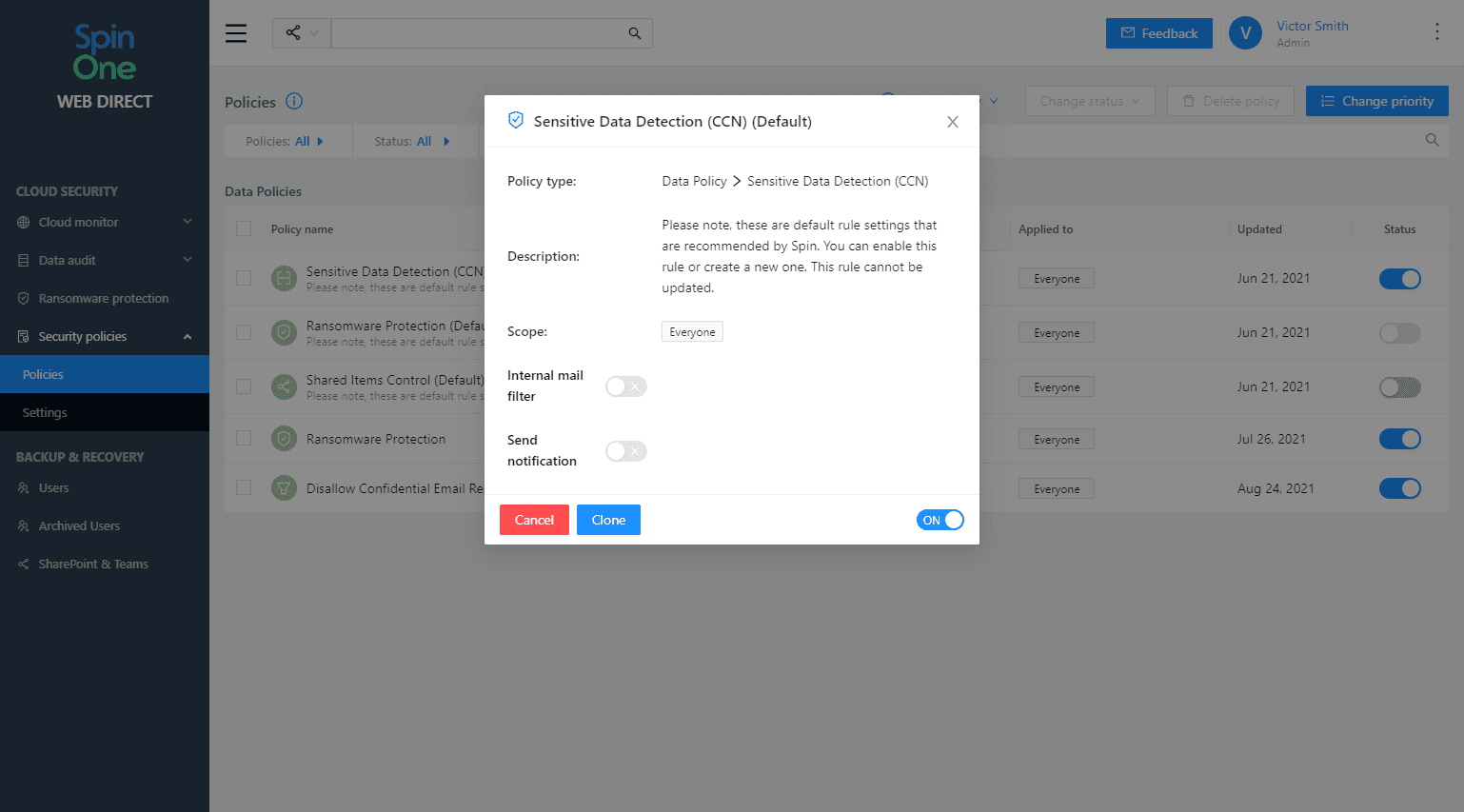
Security Policies
SpinOne provides the ability to create security policies that control security processes included with SpinOne:
- Ransomware protection
- OneDrive Sharing Visibility and Control
- Sensitive Data Detection
- Restore Filtration
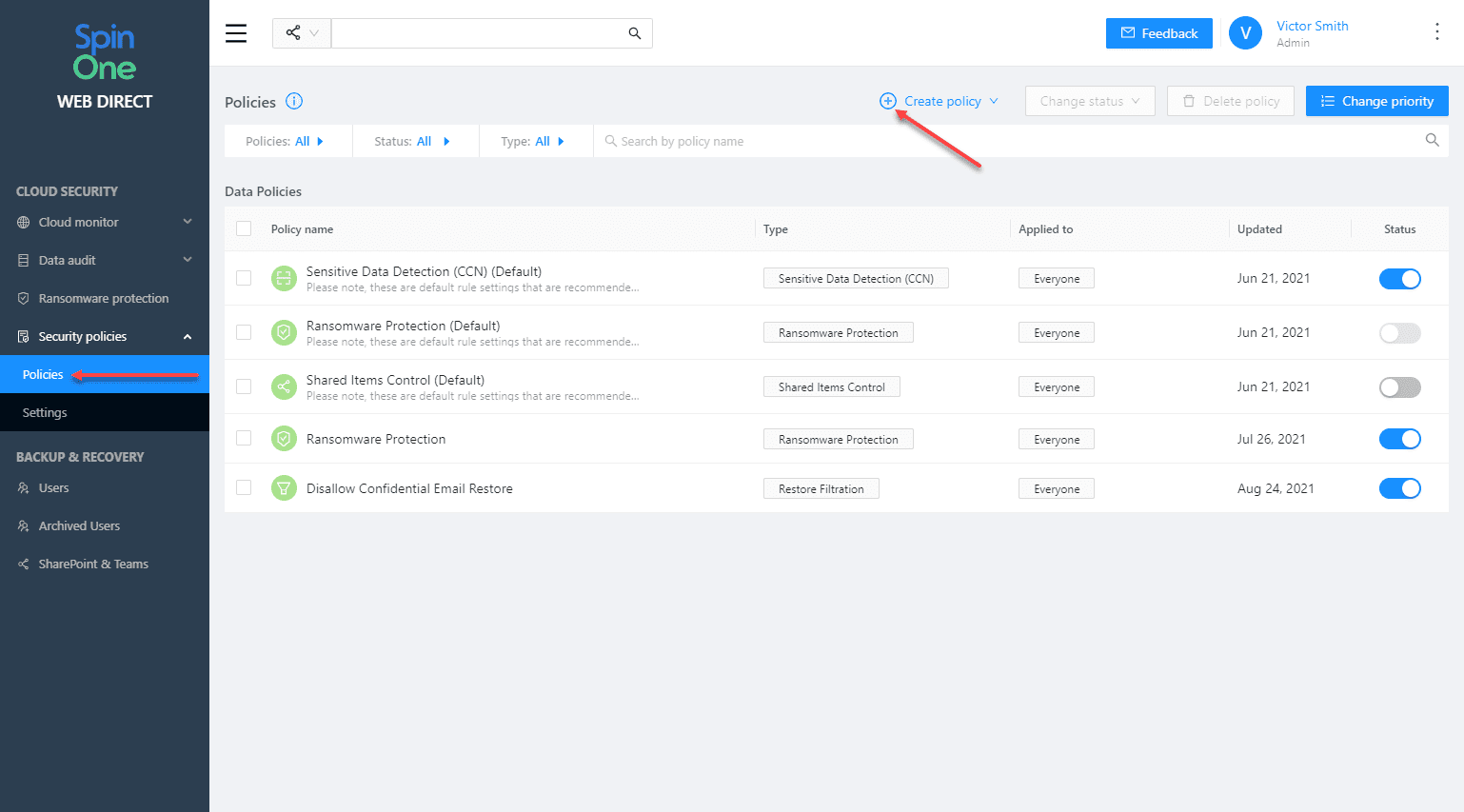
Below is a look at the properties of a security policy.
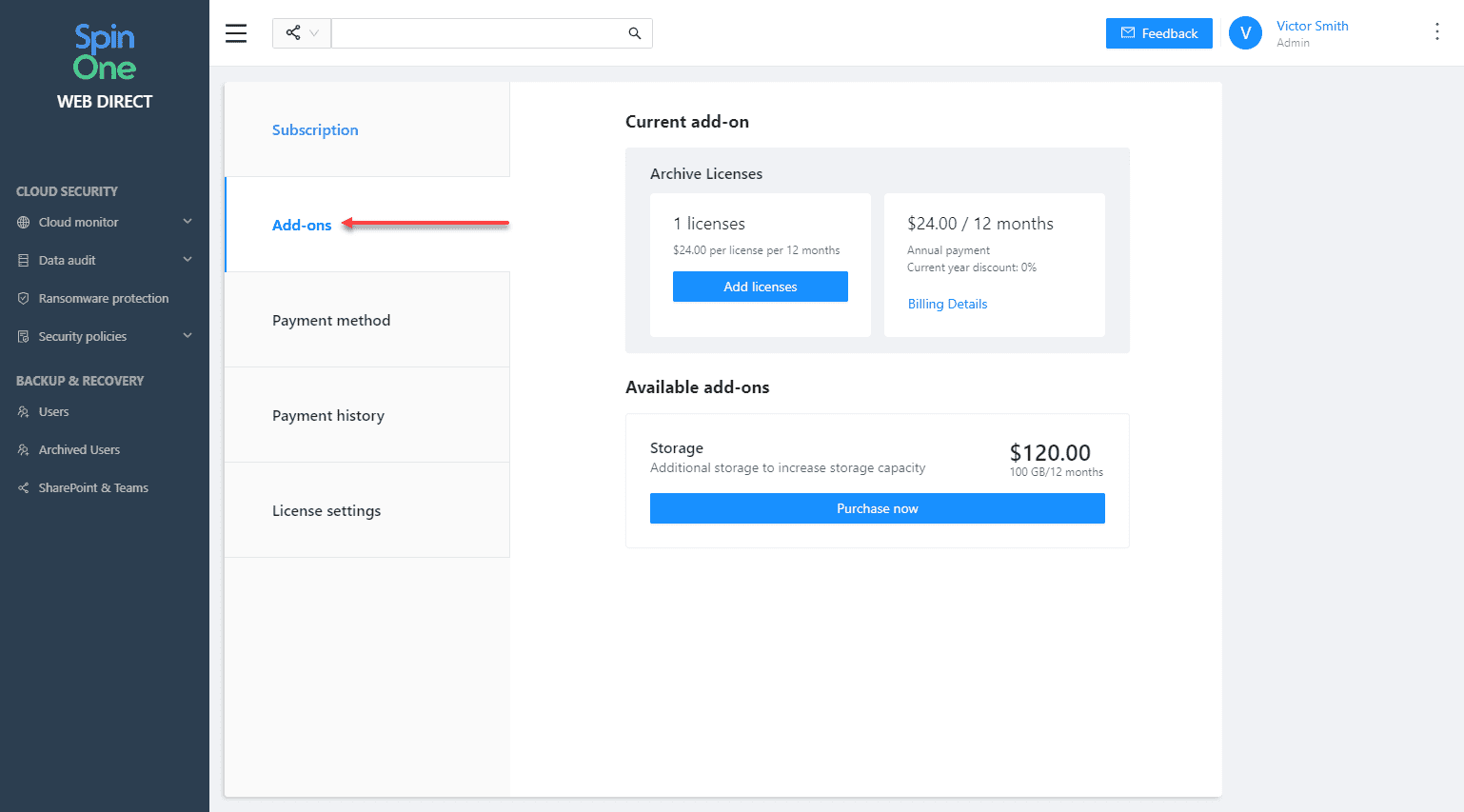
Add-ons
SpinOne has added an easy way to interact with and upgrade backend archive and storage licenses.
These include:
- Archive licenses– A cost-effective license that allows retaining terminated employee data
- One Automated Backup
- Unlimited Manual Backups
- Unlimited Download
- Unlimited Restore
- Unlimited Storage
- Access to the latest Snapshot
Storage – With the storage add-on, you can increase your overall account storage capacity. Businesses can upgrade their storage capacity at any time to avoid exceeding storage limits.
Recent New Features introduced by SpinOne
Spin has recently introduced the following new features:
- OneDrive folder structure browsing during recovery
- Export Exchange Online mailboxes and emails to PST
- Increased storage from 30GB to 50GB
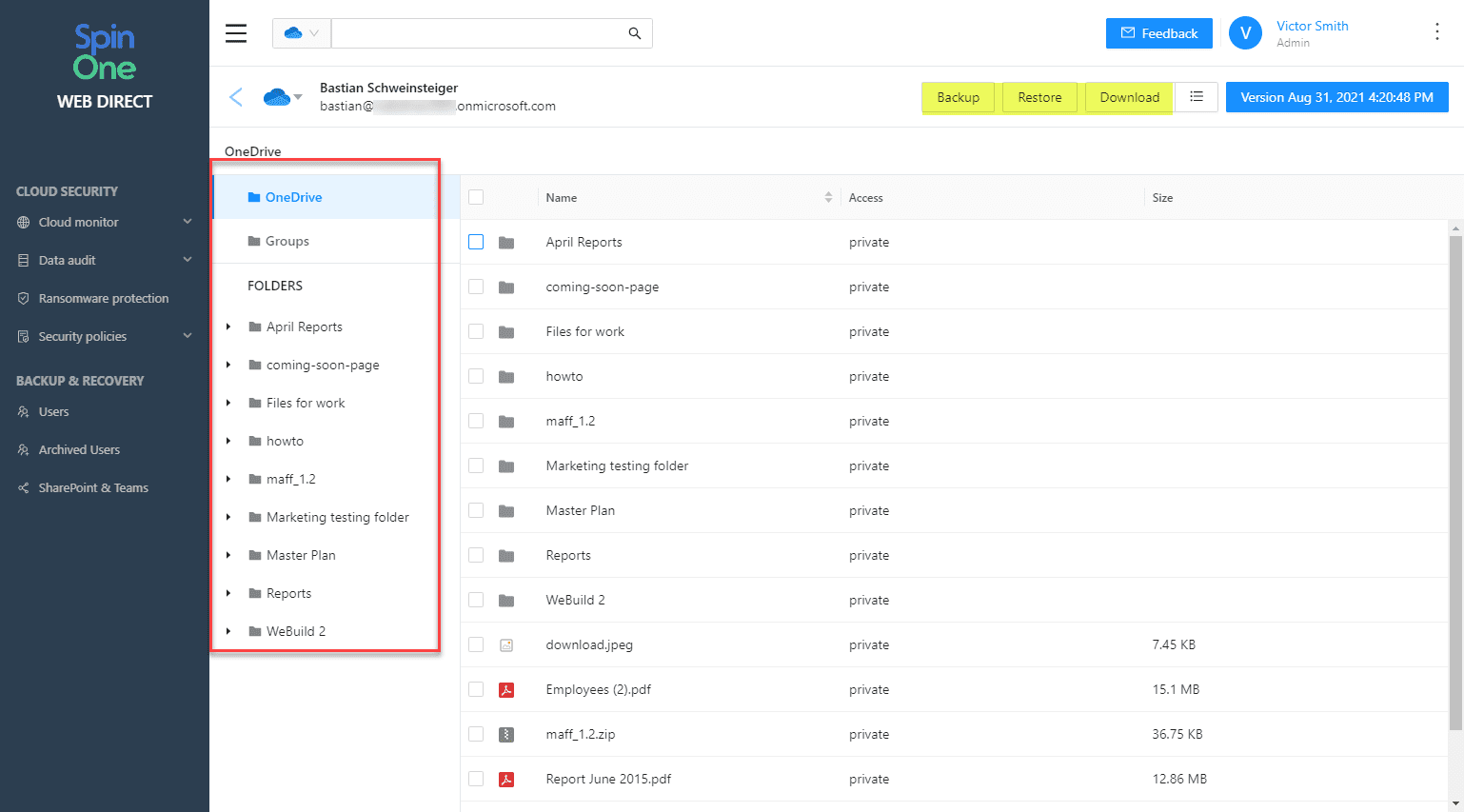
OneDrive folder structure browsing during recovery
With the new feature, cloud administrators can browse the folder structure of user’s OneDrives. This helps to locate and restore information. This new feature leads to simplified operations, quicker restores, and less downtime.
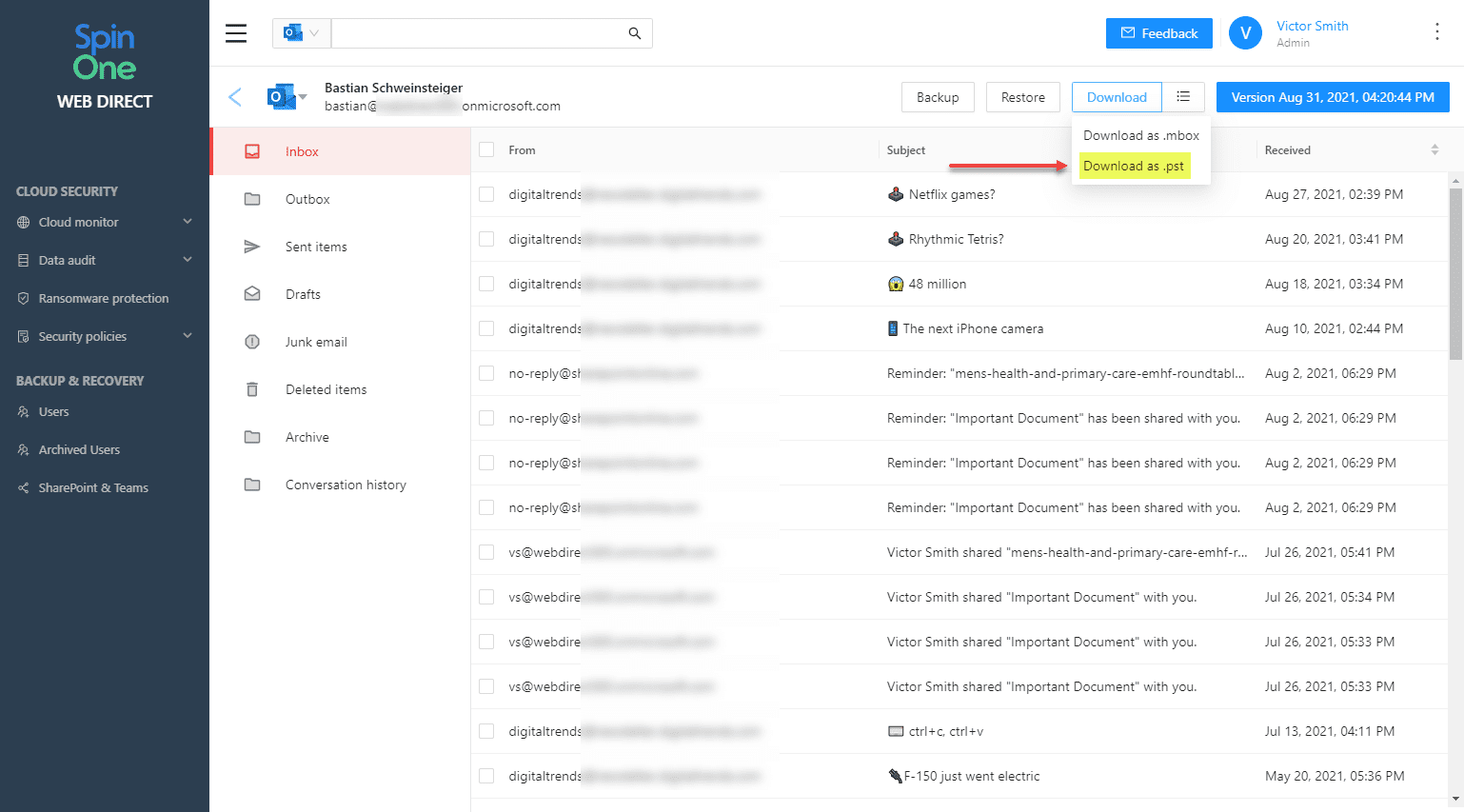
Export Exchange Online mailboxes and emails to PST
SpinOne makes it easy to export Exchange Online mailbox data to a PST file. PSTs are a standard file type used to export mailbox data as an archive, local storage, and other use cases.
Increased storage from 30GB to 50GB
New SpinOne licenses now provide 50 GB of storage. This is an upgrade from the previous 30 GB capacity, but only for those who are on the current $9 user/month SpinOne subscription plan. With this increase, Spin is providing even better value to customers and those who are looking to protect business-critical data in the cloud.
Wrapping Up
Office 365 Ransomware protection with SpinOne new features provides the ability to have greater visibility in the environment, simplified SecOps operations, and other really robust features for organizations migrating to the cloud. Ransomware will only continue to threaten data, wherever it is located. Tools like SpinOne help organizations leverage the cloud with the cybersecurity needed.
Learn more about SpinOne and sign up for a free trial version here.
More Spinone articles here: