Remote access technologies widely used today were originally built for remote access in a different time – prev-COVID, pre-ransomware, pre-security concerns that exist today. There has been a massive paradigm shift in how businesses today are empowering employees. Since the onset of the global pandemic, businesses have hd to reimagine the entire work experience, not only from the workflow perspective but also from the technical challenges. Attackers have been quick to capitalize on the major security risks associated with and realized with the shift to remote connectivity and productivity. Cameyo’s application virtualization platform provides a major advantage for businesses making the shift to the hybrid or distributed workforce. The platform is built around security. Today, Cameyo has released Secure Cloud Tunneling, which takes the security of the Cameyo solution to the next level.
What are the risks of traditional remote connectivity solutions?
There is no end to the risks associated with traditional remote access platforms, including Remote Desktop Services. RDP has long been a target of ransomware and was recently noted in a recent report by cybersecurity researchers at Coveware as one of the top two ways that attackers infiltrate environments with ransomware.
Traditional remote access technologies were not engineered for the security challenges in the modern world. They were instead engineered to overcome the technical hurdles to provide access to end-users.
What is Cameyo Secure Cloud Tunneling?
Secure Cloud Tunneling is a new technology introduced by Cameyo that provides greater protections for remote workers and internal resources they are accessing. Secure Cloud Tunneling eliminates the need to open firewall ports for connectivity to end-users.
Opening firewall ports is like introducing “chinks in the armor” that attackers can exploit. Cameyo’s solution is already steps ahead of other solutions in the industry with the way they handle the network traffic for authenticated or unauthenticated users. Before Secure Cloud Tunneling, they had a solution called Port Shield that only allowed the RDP port to open for authenticated users. This helps to eliminate the threat of brute force attacks and minimize zero-day vulnerabilities.
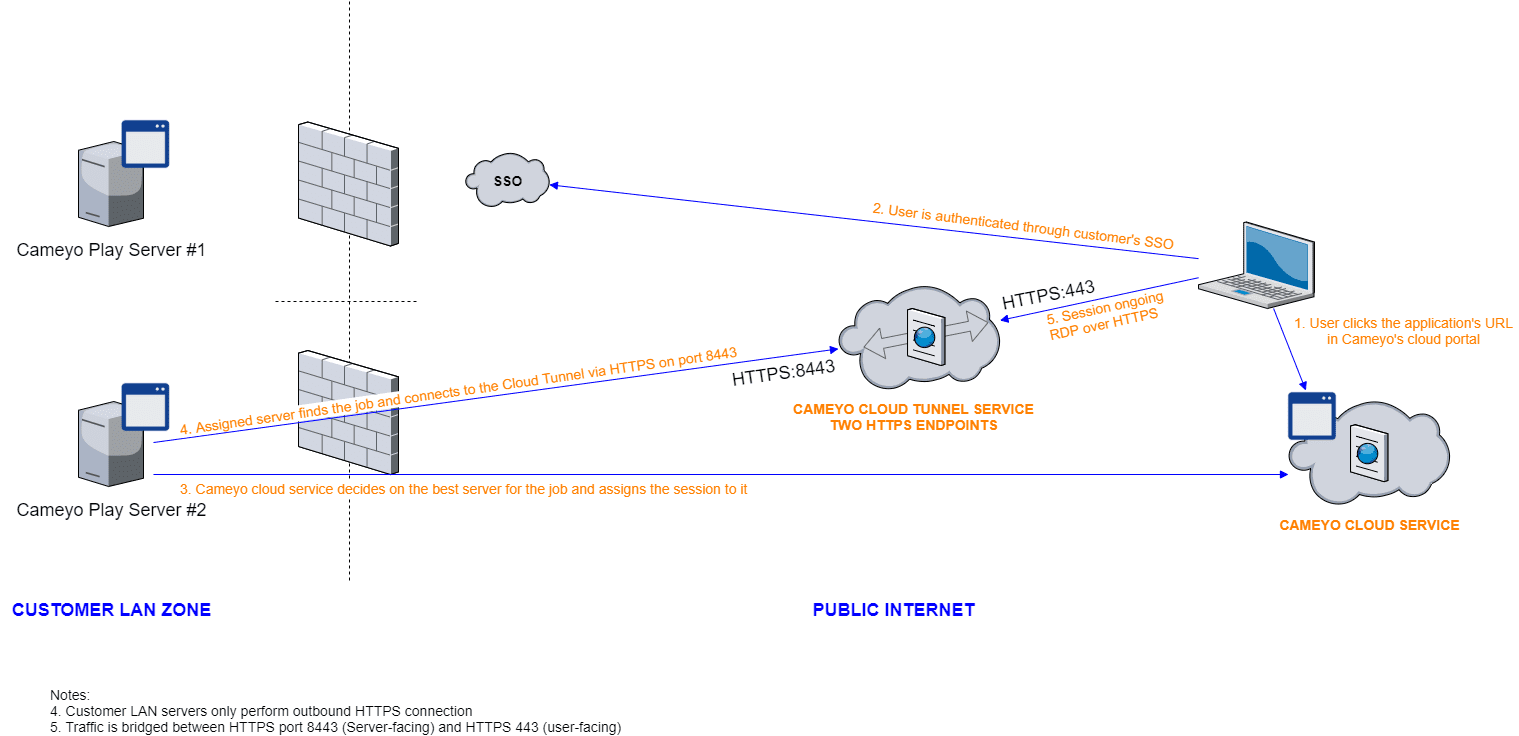
Now, the Cameyo security solution has evolved even further. The Cameyo Secure Cloud Tunneling solution provides secure access in five steps. These are:
- User clicks the application’s URL in Cameyo’s cloud portal
- User is authenticated through customer’s SSO
- Cameyo cloud service decides on the best server for the job and assigns the session to it
- Assigned server finds the job and connects to the Cloud Tunnel via HTTPS on port 8443
- Session ongoing RDP over HTTPS
As you can see from above, the Cameyo server initiates the connection and not an end-user or an attacker attempting to compromise the network. Also, as you can see from the above, the whole process relies on the user authenticating. This helps organizations get to a zero-trust security model based on identity.
In addition to the new Secure Cloud Tunnel feature, Cameyo has also recently been certified with the most prestigious Information Security Management System – ISO 27001. I really like what Cameyo is doing with their architecture, building security in from the ground up. It is great to see a company who is focused on security as intrinsic to their offering.
Note the other security features of Cameyo:
- Device Access Control – A device is never trusted with Cameyo (even managed devices) because those devices can be compromised. Users get secure access to business-critical applications for productivity while providing complete isolation between devices and the data and network they are accessing.
- Segmentation – Cameyo also incorporates intrinsic segmentation to the offering, ensuring the customers session is segmented from customers’ networks and data to ensure ongoing separation.
- Prevention of Lateral Movement – Even in the case where a device has ransomware or malware, that malware cannot reach the customer organization’s network/data, nor can malware on their systems reach the Cameyo system.
- Always-On Monitoring & Validation – Cameyo utilizes non-persistent servers, so all customer user data is wiped from the Cameyo server every time the user logs out.
- Least Privilege – With Cameyo all traffic is encrypted and apps are delivered from a secure HTML5 browser, separating the user’s device from the corporate network and eliminating the need for VPNs. Cameyo also utilizes Windows Terminal Services and temporary user profiles, ensuring users are unable to access admin privileges, settings, and files.
- Identity & Access Management – Cameyo integrates with the customer’s Single Sign-On (SSO) provider of choice, and the Multi-Factor Authentication (MFA) they have set up with their SSO applies to Cameyo.
Eyal Dotan, Founder and CTO of Cameyo explains: “For a solution to provide true Zero Trust security, Zero Trust must be foundational and systemic. Cameyo was designed from day one as a native Zero Trust system where all security capabilities are baked into the core of the platform, never treated as an additional or optional layer.”
More about Cameyo
Cameyo provides Virtual Application Deliver (VAD) to empower customers to easily build their digital workspace for the future. Core to the solution is simplicity, security, and flexibility. The solution is cost-effective and provides the ability for customers to not only use modern applications in a cloud-driven way but also legacy applications, straight from a web browser. As of August 2021, Cameyo has a Net Promoter Score (NPS) of 70 with zero detractors – 100% of responding customers would recommend Cameyo to their peers. To learn more, visit cameyo.com.
Also, see more Virtualizationhowto articles covering the Cameyo solution below:
- Cameyo Launches Artificial Intelligence AI Platform for Virtual Application Delivery
- Cameyo Expands Remote Worker Security with HTTP Port Shield
- Cameyo’s Digital Workspace Platform Now Available on Microsoft Azure
- Cameyo – Easy Digital Workspace for Remote Workers
Google is updating how articles are shown. Don’t miss our leading home lab and tech content, written by humans, by setting Virtualization Howto as a preferred source.