There are many who are looking at ways to automate the process to apply the currently recommended remediation using a script. With Windows, PowerShell is the obvious choice here as it is easy to use and works well on the client operating systems affected – Windows 10. In this quick post, let’s take a look at a PowerShell script workaround for SeriousSAM and HiveNightmare vulnerability.
Importance to get your machines patched
This is an extremely bad vulnerability that provides the means for an attacker to get access to sensitive data, install programs, and create high-level user accounts. Until Microsoft releases an official patch for the vulnerability, the workaround needs to be applied.
You can find the official CVE information from Microsoft here:
PowerShell Script fix for SeriousSAM and HiveNightmare Vulnerability
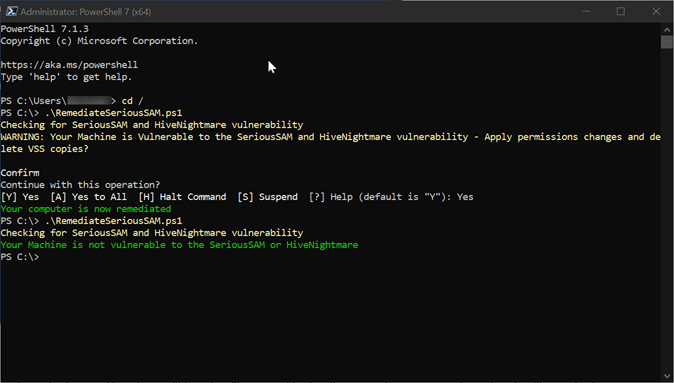
The SeriousSAM and HiveNightmare vulnerability remediation include a combination of changing permissions on a folder in the system directory and also deleting Volume Shadow Copies (VSS). The script checks the permissions on the folder for the BUILTIN\Users inherited permissions. If the permissions that make the Windows 10 machine vulnerable are present, it prompts to apply the remediation.
The script will create a temporary file where the output from the Get-ACL command is stored. It will then be deleted as the script is run. Also, there will be a log file created in the directory where you run the script. It will contain the output from the permissions change operation and the vssadmin delete command. Below is the script in full.
You can download or clone the script from my repo here:
#PowerShell script to check for the SeriousSAM/HiveNightmare vulnerability and remediate
#Use at your own risk!
#Author: Brandon Lee - Virtualizationhowto.com
$placeholder = "check.txt"
$log = "SeriousSAM.log"
try {
Write-Host "Checking for SeriousSAM and HiveNightmare vulnerability" -ForegroundColor Yellow
Get-Acl $env:windir\system32\config\SAM | fl | out-file $placeholder
$check = Get-Content $placeholder | Where-Object { $_.Contains("BUILTIN\Users") }
if ($check -ne $null) {
try {
Write-Warning "Your Machine is Vulnerable to the SeriousSAM and HiveNightmare vulnerability - Apply permissions changes and delete VSS copies?" -WarningAction Inquire
icacls c:\windows\system32\config\*.* /inheritance:e > $log
vssadmin delete shadows /All /Quiet >> $log
Remove-Item $placeholder
Write-Host "Your computer is now remediated" -ForegroundColor Green
}
catch {
Write-Host "You chose not to remediate your host" -ForegroundColor Red
}
}
else {
Remove-Item $placeholder
Write-Host "Your Machine is not vulnerable to the SeriousSAM or HiveNightmare" -ForegroundColor Green
}
}
catch {
Write-Host "Error running the script" -ForegroundColor Red
}Wrapping Up
Hopefully, this PowerShell Script workaround for SeriousSAM and HiveNightmare vulnerability will help to provide an automated workaround for implementing the currently recommended remediations for the vulnerability. I will keep the post updated and code if there are additional items found to be affected.
Google is updating how articles are shown. Don’t miss our leading home lab and tech content, written by humans, by setting Virtualization Howto as a preferred source.