VMware ESXi Passphrase and Account Lockout Configuration
Configuring password requirements is extremely important when it comes to the overall cybersecurity of your environment. VMware vSphere has the configuration capabilities to support most modern password requirements. When it comes to ESXi we can set ESXi passwords and account lockout behavior with several advanced configuration settings. Let’s take a look at VMware ESXi passphrase and account lockout configuration and see which settings can be changed and how this can be done.
VMware ESXi passphrase and account lockout
With VMware ESXi, you can change the predefined requirements in regards to:
- Account lock failure attempts
- Account unlock time
- Password history
- Password max number of days
- Password quality control
- SSH sessions limit
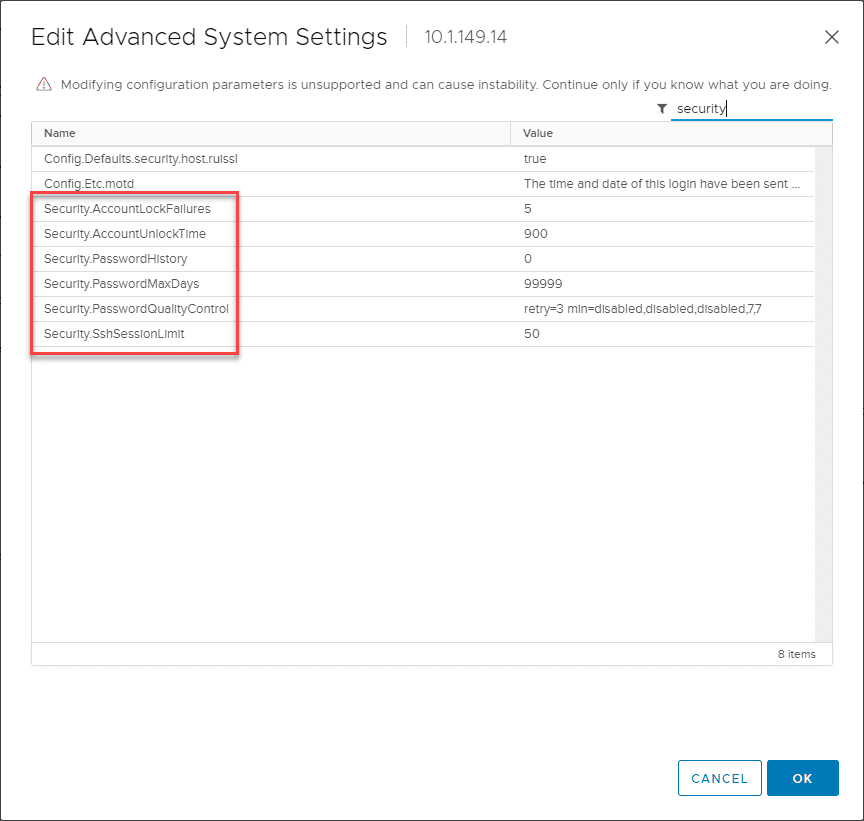
As you can see below, the Advanced System Settings for an ESXi host defines the various security settings that define specific password requirements. Below is a screenshot of the Advanced System Settings for an ESXi host. These are the default settings configured with ESXi. If you are checking these from the vSphere Client with the host connected to vCenter Server, you navigate to Host > Configure > System > Advanced System Settings and perform a search for security.
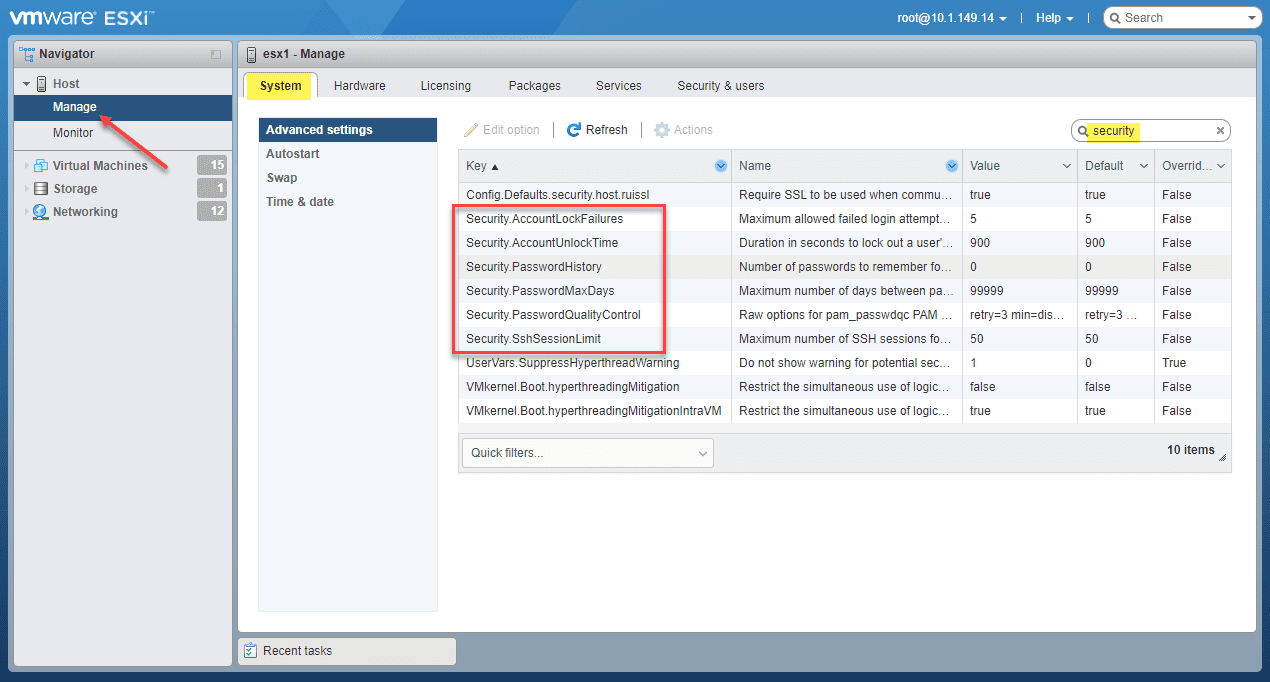
Below is a screenshot of the same host, logged into the VMware Host Client. As you can see, you have the same settings listed from the VMware Host Client.
VMware emphasizes the need to pay attention to the password requirements for ESXi passwords from one release of ESXi to another release. These defaults can change between releases due to further enhanced out-of-the-box security tweaks implemented by VMware between each release.
ESXi passwords and password enforcement
What exactly do the password requirements configured for ESXi apply to? ESXi enforces password requirements for access from the Direct Console User Interface (DCUI), ESXi shell, SSH, and the VMware Host Client. The default settings with the ESXi host require the following:
- A mix of characters from four character classes: uppercase, lowercase, numbers, and special characters
- A password with a length of 7 characters but less than 40
- No dictionary passwords or parts of a dictionary password
- **Note** An uppercase character at the beginning of a password and a number on the end does not count towards the number of character classes required.
- Passphrases are not enabled by default out-of-the-box
The Security.PasswordQulityControl advanced option from the vSphere Client is the attribute that defines the ability to use passphrases. As you noted above in the screenshot the default SEcurity.PasswordQualityControl setting is configured for:
retry=3 min=disabled,disabled,disabled,7,7
What does the above password quality control setting equate to?
- Passwords with one or two character classes and passphrases are not allowed
- Passwords from three and four-character classes require 7 characters in the password
With these settings, the following passwords are allowed:
- xQaTEhb! – Contains eight characters from three character classes.
- xQaT3#A – Contains seven characters from four character classes.
The following passwords are not allowed:
- Xqat3hi – Begins with an uppercase character, reducing the effective number of character classes to two. The minimum number of required character classes is three.
- xQaTEh2 – Ends with a number, reducing the effective number of character classes to two. The minimum number of required character classes is three.
ESXi passphrase configuration
As mentioned above, by default, passphrases are not enabled. Many organizations are migrating towards using passphrases as these are more effective in producing passwords that a human can remember and use effectively. Their strength comes not in their complexity, but in the length of the passphrase. As part of a new alignment of password policies with newer techniques such as passphrases, organizations may choose to enable passphrases as part of the ESXi password security. How are passphrases enabled in ESXi?
Again, this is controlled by the Security.PasswordQualityControl advanced system setting. As an example, you can enable a passphrase which is characterized by:
- 16 characters
- three words
- separated by spaces
Using the following:
retry=3 min=disabled,disabled,16,7,7
How do you change the default password or passphrase settings with the SEcurity.PasswordQualityControl advanced option? The default can be changed in line with the following example:
retry=3 min=disabled,disabled,15,7,7 passphrase=4
ESXi account lockout configuration
Account lockout policy is a great way to improve the security of your VMware ESXi hosts. It prevents the ability of an attacker having no limit to the number of bad passwords attempted against the host. Instead, with account lockout, after the configured number of bad password attempts, the account is “locked out,” meaning the account cannot be logged into, even using the correct password. With VMware ESXi, the account lockout behavior is supported for access through SSH and with the vSphere Web Services SDK. DCUI and the ESXi shell are not controlled by the account lockout policy.
What about the default account lockout configuration with ESXi? How is this controlled?
By default, ESXi is configured with:
- Maximum of 5 bad password attempts
- The account is locked for 15 minutes
To configure the account lockout behavior, configure the following advanced system settings:
- Security.AccountLockFailures – This is the maximum number of failed login attempts against your ESXi host until the account is locked out. A setting of “0” effectively disables the account lockout policy.
- Security.AccountUnlocktime – This setting defines the number of seconds the account is locked out due to hitting the threshold of bad password attempts configured in the Security.AccountLockFailures configuration
- Security.PasswordHistory – If you want to set the password history, this is the number of passwords remembered for each user. Setting this to “0” disables password history.
Wrapping Up
Understanding the VMware ESXi passphrase and account lockout configuration for your VMware ESXi hosts is critical to bolstering the overall security of your vSphere environment. By configuring the Advanced System configuration found for each ESXi host in a vSphere cluster, you can control the types of passwords required, passphrase enablement, password history, and password lockout.