Unifi IoT Network Build and Configuration
There has been an explosion of IoT devices on the market. It seems like everything is now connected to the Internet in some form or fashion, including modern appliances. While many devices simply make use of the existing “flat” Internet connection that exists in most home scenarios is a great idea for security and other reasons to create a dedicated home IoT network. I have been using Ubiquiti Unifi gear for a couple of years now after upgrading my existing wireless network to Ubiquiti Unifi at that time. The Ubiquiti hardware and solutions offer many enterprise features for a very modest price which makes them an excellent choice for a wireless upgrade as well as creating a Unifi IoT network for home IoT and other devices. In this post, I will go over a few details of Unifi IoT network build and configuration and some things you will want to consider.
Why Ubiquiti Unifi gear?
Just a brief overview of why I have migrated to Unifi gear and how they have served me thus far. After getting my hands on Ubiquiti Unifi AP Pros, they are awesome little access points. So far, I have not had a single major issue since migrating to the Unifi ecosystem for wireless around two years ago.
They work off the premise of having a wireless network controller that controls the configuration of the wireless APs, upgrades of firmware, etc. You can also get into the wireless APs as well as they run a very light installation of BusyBox Linux.
Are Ubiquiti Unifi APs for everyone? I would answer no on that. If you are not a power user or have experience with networking you will most likely be in over your head with these types of devices. However, for most readers of the blog, they are most likely going to be in the comfort zone for many to most. This is also part of the appeal of the gear for me. I like to geek out on network gear, etc. If you like the thought of running your own network controller, VLANs, firewall rules, and other implements, you will love the Unifi experience.
Unifi IoT Network controller – hardware or software
Another great feature of the Ubiquiti Unifi controller is you can run this as either a hardware device or a software-based controller. You can purchase the “Cloud key” devices on Amazon which are essentially a hardware controller device that sits on your network and serves the purpose of the Ubiquiti controller.
However, if you have a home lab environment and have the ability to run your own VMs, you can also run the Unifi controller inside a Linux VM without issue. I have mine located in a Ubuntu VM that pulls the Unifi updates as part of the regular Ubuntu software updates and this has worked well.
Upgrading firmware on Ubiquiti Unifi APs from the Unifi controller.
Unifi IoT Network Build and Configuration
The Unifi IoT Network Build and Configuration includes creating a new network that is used to house IoT devices. Why is this an important consideration and best practice?
Network Segmentation has been an age-old security best practice in the enterprise. When you segment your large flat network into multiple smaller networks, you are reducing the attack surface for an attacker who may infiltrate one of the smaller networks. Whereas when a large flat network is compromised, the attacker can literally see everything.
Additionally IoT devices are historically less secure than other types of network devices for a number of reasons. These include:
- They are less fully-featured from a security perspective
- They may have more vulnerabilities
- Attackers more often target IoT devices due to the above reasons
All of these things lead to IoT devices being great candidates for living on a segmented network with little or no access to other network segments outside of routing and other network services if needed.
Creating Unifi Networks and Wireless Networks
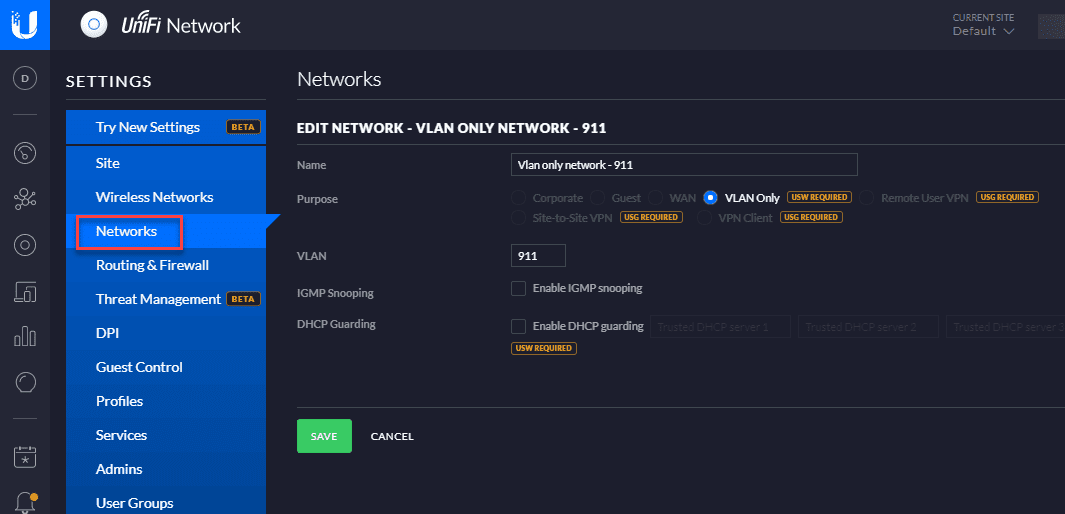
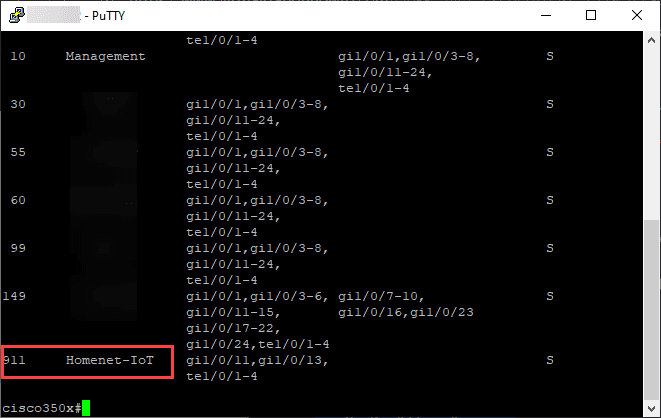
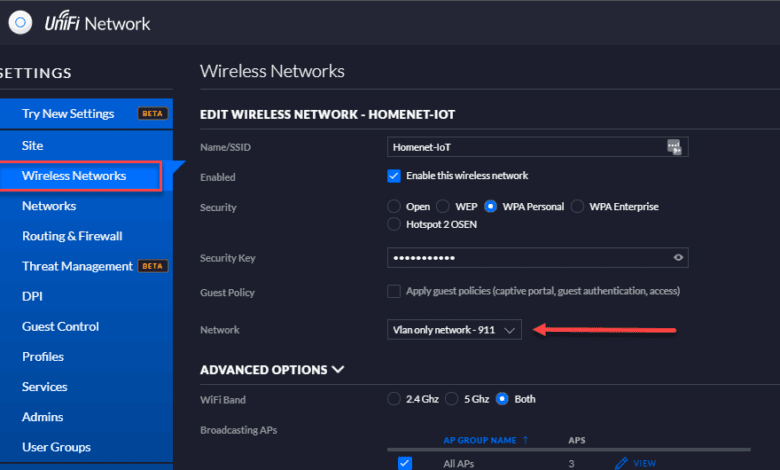
To create the Unifi IoT Network, you need to create what Unifi calls Networks and Wireless Networks. This has changed since the release of Unifi Controller 6.X. However, the Network is the construct that defines the VLAN and the Wireless Network is where you define the SSID for the wireless AP and connect the VLAN to it.
A picture is worth a thousand words so notice below how this is configured. You need to first create the Network that defines the VLAN.
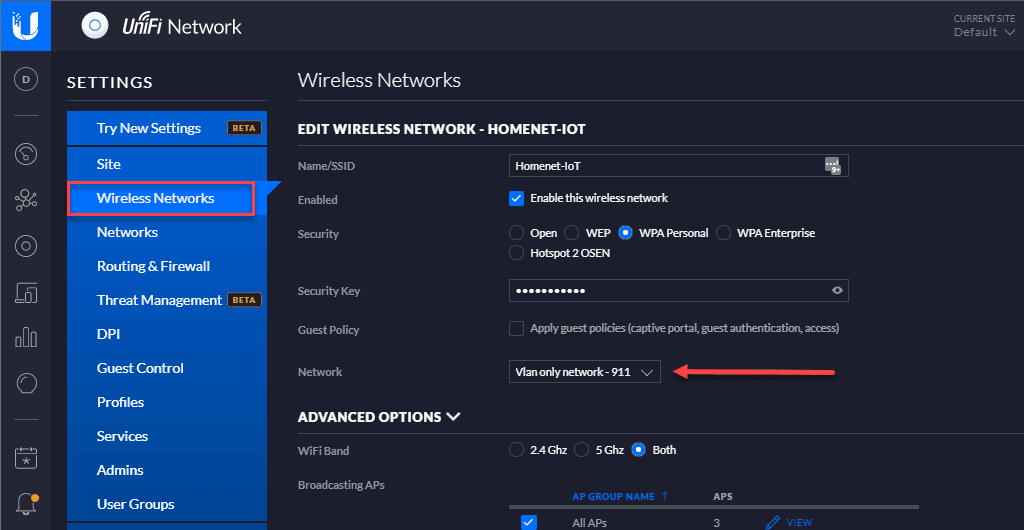
Next, you create the Wireless Network which defines the SSID, security mode, and also the Network you want to use. In this case the VLAN only network is defined.
What this means is clients or IoT devices that connect to this SSID will have frames tagged with the VLAN ID for the IoT network. To pass the traffic across your network, you need to make sure your underlying network switch or switches if you have more than one, have the VLANs created and tagged for all uplink ports where the Unifi APs are uplinked.
For most environments, you will have your uplink ports carrying your Unifi AP traffic configured in Trunk or General mode to allow multiple VLANs to traverse the port. Most will have more than the IoT network presented on a particular AP.
Configuring DHCP – IP Addressing
The last piece of the puzzle you need to include is how your IoT clients will receive a network address. For most, a DHCP server of some sort will need to be introduced into the VLAN to listed for DHCP requests from clients. There is no right or wrong solution for DHCP necessarily and this element depends on each particular environment.
Options may include:
- A Windows DHCP Server with multiple scopes (one of which assigns addresses for IoT devices).
- A Unified Access Gateway handing out IPs
- An non Ubiquiti upstream firewall handing out IPs
Firewall Rules to prevent traffic from crossing VLAN Networks
By default, most firewalls will allow traffic to route between different networks that it knows about. So, for instance, if you have a main LAN network and an IoT network, these devices will most likely be able to communicate, ping each other, and so forth. For securing your Unifi IoT Network, you want to ensure firewall rules are created to filter any traffic between your “trusted” LAN and your IoT network.
***Note*** Trusted networks are a thing of the past and I am here simply using this term to describe security boundaries. The concept of “zero-trust” is much more relevant today which assumes no trust between devices.
There may only be certainly allowances that you may want to allow between the two networks for various network resources such as communicating with your Unifi Controller if it sits on a different network range.
Wrapping Up
Unifi IoT Network Build and Configuration is easy to accomplish with a little bit of network know-how and some basic common sense when it comes to security best practices. The Unifi Controller provides the tools needed to create Networks, Wireless Networks and the VLAN association needed to segment the network. Hopefully this post helps to give a high-level overview of the concepts and how this is accomplished.