VMware vRealize Network Insight vRNI Assessment
VMware vRealize Network Insight (vRNI) clarifies network flows in and out of your virtual environment and how this network traffic intersects your physical infrastructure. With VMware vRNI, you have a solution that allows gathering the information needed for effectively deploying micro-segmentation in your environment and the analytical data to understand how firewall rules can be used to secure your network flows. VMware vRNI has become much more aware of “applications” as these are the real point of interest in network security. This post will overview running a VMware vRealize Network Insight vRNI assessment and the tools that vRNI offers to understand your network traffic effectively.
How network security has changed
To understand the extremely powerful role of vRNI in your environment, it is important to understand how networks and network security have changed in recent years. Organizations today are more focused on applications than ever before. Applications are becoming more decentralized and spread out across many different network resources. With the shift to modern applications that use microservices, applications no longer fit the traditional 3-tier architecture of days gone by. Developers are making use of containers and other technologies to house microservice architectures as opposed to monolithic applications.
With that being said, it is no longer as easy to secure and have visibility to an application simply based on a single physical machine or VM. Understanding network flows of all components across all the different architecture components is extremely important. This is where vRNI comes into play as it allows easily classifying applications and analyzing network flows to better understand and provide security to your applications.
VMware vRealize Network Insight vRNI
Using vRNI, you can understand network traffic to a much more detailed degree to understand how traffic needs to be micro-segmented, security groups, and firewall rules that need to be created. You can collect your vRNI data from VMware vCenter Server, NSX-T, and your physical network infrastructure. This can include your switches, routers, NLBs, and firewall devices.
With vRNI, all of the information is aggregated in the vRNI database and can be used to provide a centralized configuration management database (CMDB) for your infrastructure and your applications. This can be a difficult source of information to build using manual means. VMware vRNI makes this much easier.
VMware vRealize Network Insight vRNI Assessment
VMware vRNI provides a VMware network assessment of your vSphere environment that allows mapping out your applications and network flow data. Using this VMware virtualization assessment, your organization can better understand where your network stands – both physical and virtual.
VMware vRNI provides various types of planning and assessment tools that allow classifying network flows and traffic. You can use the following assessment tools in vRNI:
- Security planning
- Applications
- PCI compliance
Security planning
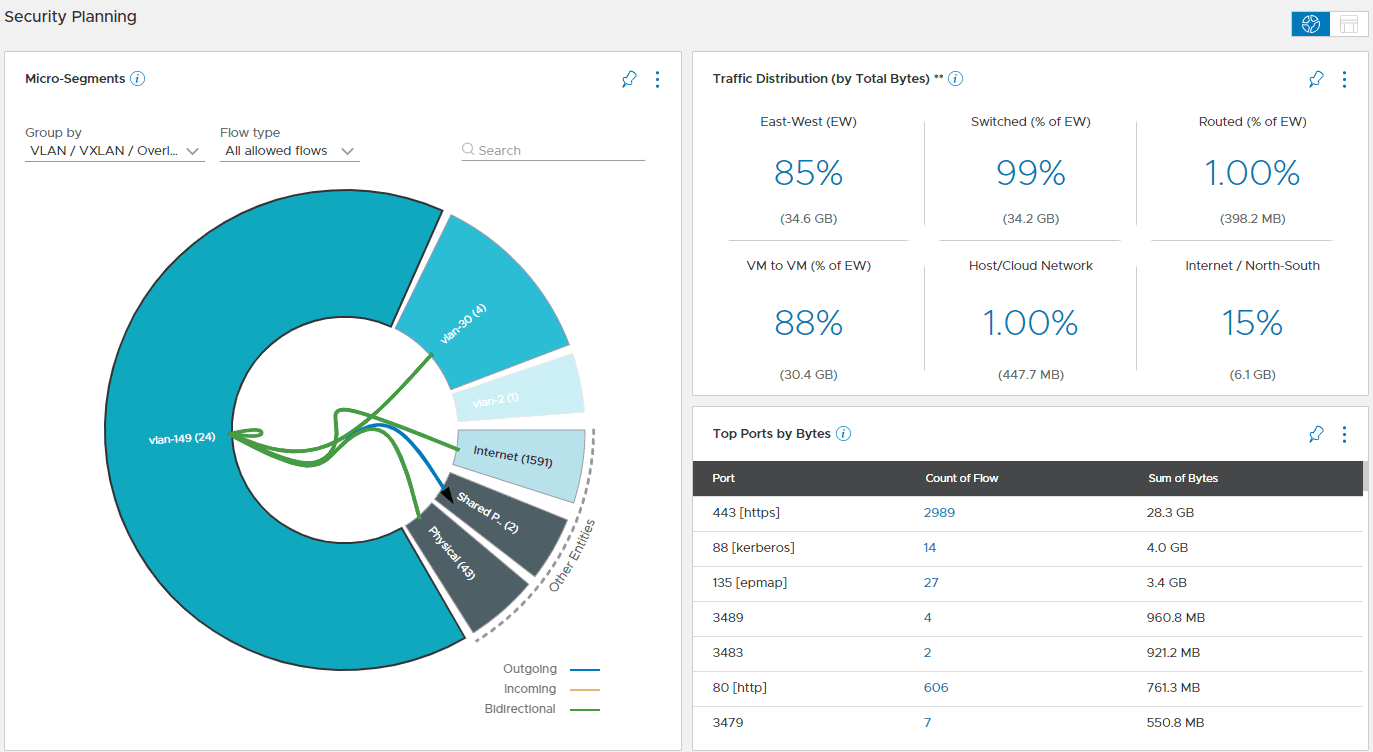
Using the security planning assessment, you get a powerful view of overall network traffic flows in your vSphere environment. This is especially useful for planning your micro-segmentation initiative. It includes:
- Internet/North-South traffic
- East-west traffic
- Switch traffic
- Routed traffic
- VM to VM
- Host/Cloud network
You can group the traffic flows by VLAN/VXLAN/Overlay, application, tier, subnet, folder, cluster, VM, port, security tag, security group, IPSet, AWS VPC, Azure VNet, or Kubernetes cluster.
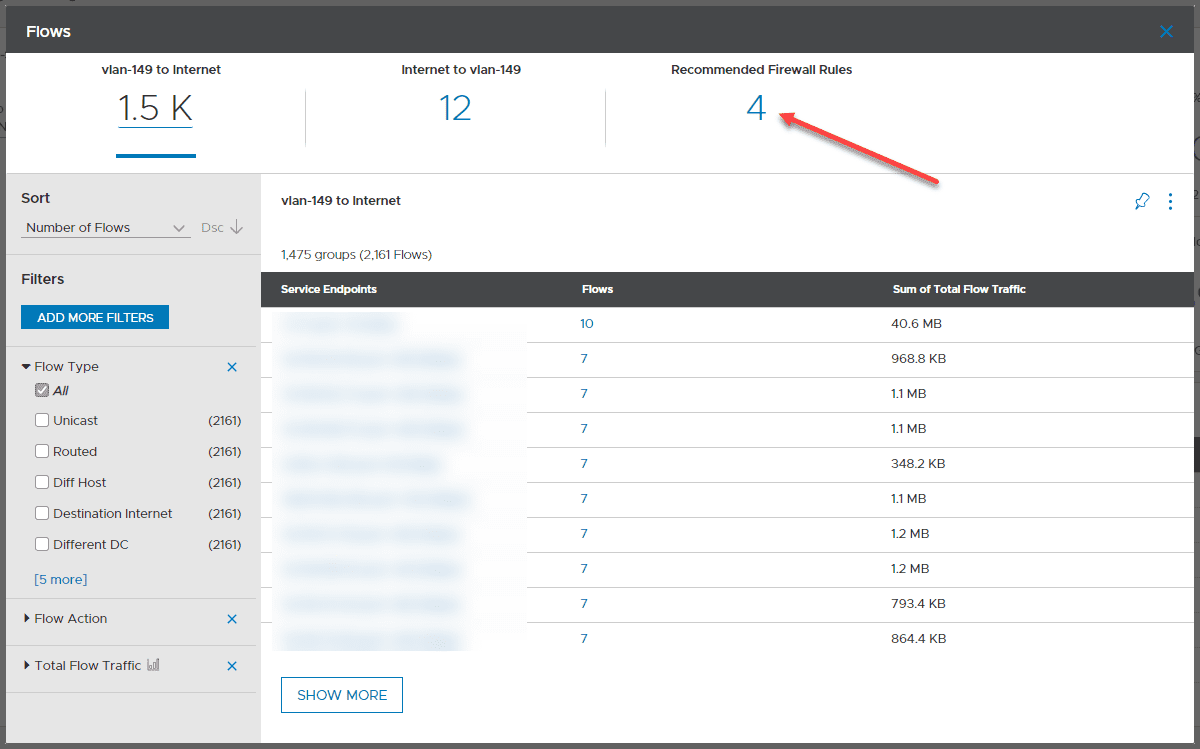
The amount of visibility that vRNI gives you regarding your network flows in the environment is incredible. It provides extremely detailed and granular views of all the traffic flows in your environment and the source/destination. It also correlates this into real data in context, including the virtual networks, VMs, VLANs, and other constructs involved.
One of the instrumental sections of the security assessment is the Recommended Firewall Rules. VMware vRNI uses the services information and external services that are accessed to provide a list of recommended firewall rules to implement effective micro-segmentation in your environment. Using these recommendations, these can be exported out of vRNI and into an NSX environment or another security solution. This provides much of the heavy-lifting required to implement micro-segmentation in your environment effectively.
Applications
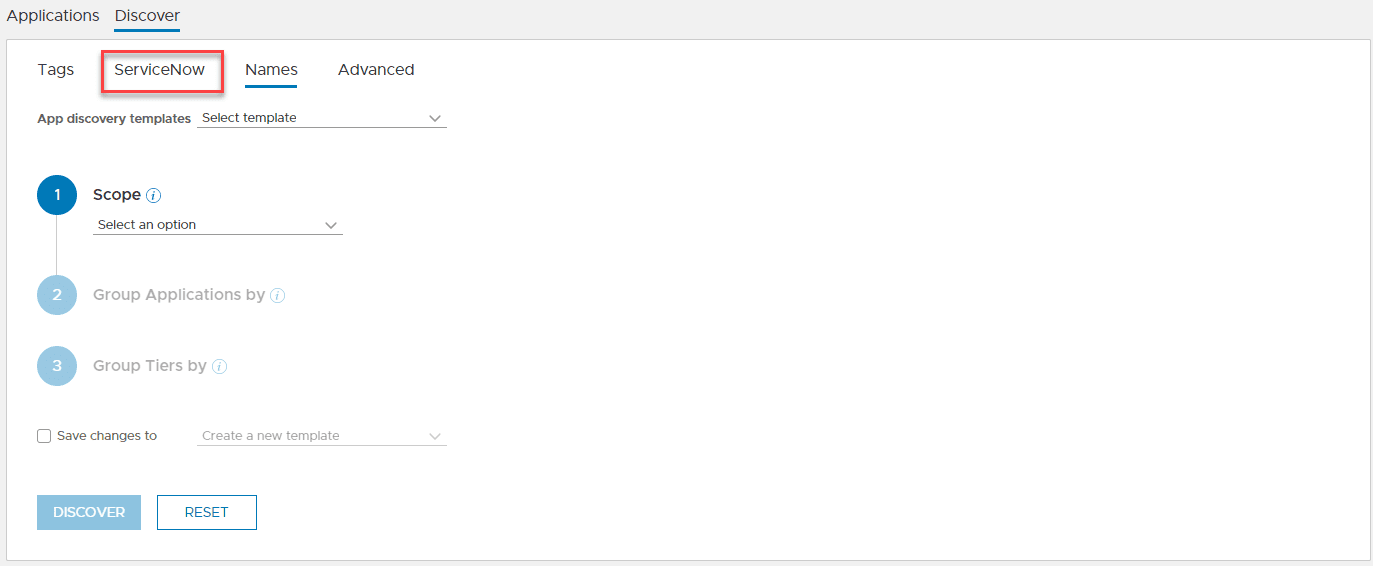
With vRNI, you can create applications that you can use to define types of traffic and categorize these. The application you create inside of vRNI is a logical container that holds objects associated with the application. This allows you to put application context around the network flow data that you collect in vRNI.
This is where a CMDB solution like ServiceNow comes in handy. Using ServiceNow or another custom CMDB, you can automatically pull the CMDB applications and synchronize these with the data found in vRNI.
PCI Compliance
Another very powerful capability provided by vRNI is the ability to audit for PCI compliance. Using vRNI, you can easily audit all communications between your VMs, physical network, traffic flows between VMs that may be in scope, various networks traversed, and many other features.
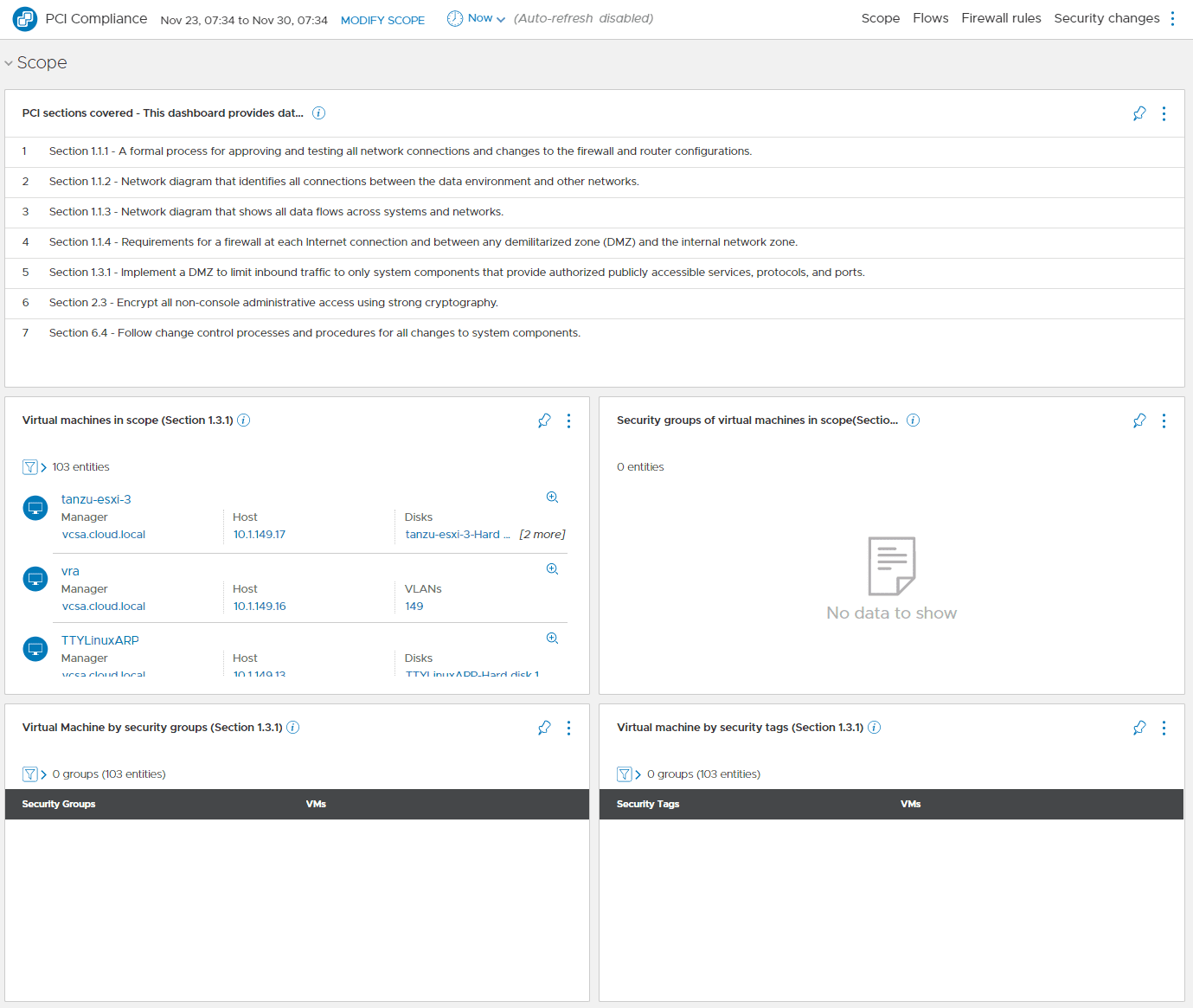
It also breaks down the various PCI sections that relate to your network infrastructure, displays these in a very consumable dashboard, and documents resources that apply.
Below, I have simply copied and pasted the PCI sections displayed in vRNI 6 under the PCI compliance assessment.
- Section 1.1.1 – A formal process for approving and testing all network connections and changes to the firewall and router configurations.
- Section 1.1.2 – Network diagram that identifies all connections between the data environment and other networks.
- Section 1.1.3 – Network diagram that shows all data flows across systems and networks.
- Section 1.1.4 – Requirements for a firewall at each Internet connection and between any demilitarized zone (DMZ) and the internal network zone.
- Section 1.3.1 – Implement a DMZ to limit inbound traffic to only system components that provide authorized publicly accessible services, protocols, and ports.
- Section 2.3 – Encrypt all non-console administrative access using strong cryptography.
- Section 6.4 – Follow change control processes and procedures for all changes to system components.
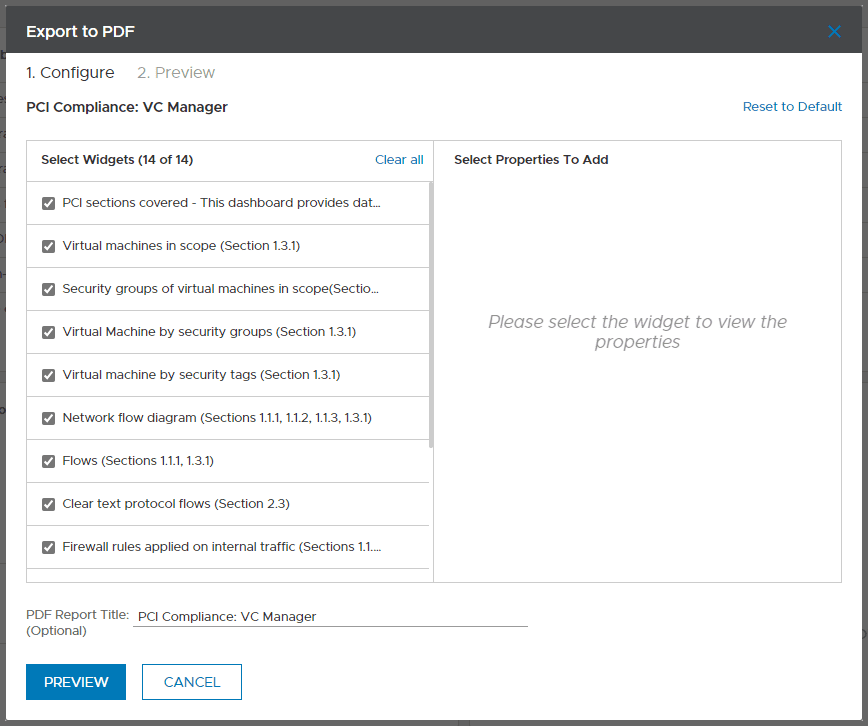
Hugely beneficial also is that the vRealize Network Insight assessment dashboards allow you to easily export the findings and outputs to a PDF, which can be used, in the case of PCI, as documentation for auditors and other business stakeholders.
Wrapping Up
The VMware vRealize Network Insight vRNI assessment capabilities are powerful and provide an easy way to have visibility into your environment and map out network flows across today’s modern applications. It allows easily planning out micro-segmentation initiatives, mapping applications, and also PCI compliance assessments.
The vRealize Network Insight assessment tools are intuitive and easy to access through very “wizardized” dashboards found in the interface. In just a few minutes, you can start delving into very detailed traffic flow analyses and starting to make business, and technical decisions to further document, assess, and secure your environment.
Check out more about VMware vRealize Network Insight here.