As organizations have transitioned to supported their remote workforce, these have been tasked with delivering the technology tools needed by the remote workforce to carry out business-critical operations. Many businesses may be using Windows Server 2019 Remote Desktop Services for both desktop session virtualization and virtual application delivery. To minimize the issues that come from end-users accessing the RemoteApps published from your Windows Server 2019 server, you want to make the experience as seamless as possible. Let’s look at how to make sure the credentials are passed from client workstations accessing RemoteApps and configure Windows Server RDS 2019 SSO.
What is Single Sign-On (SSO)
Single sign-on (SSO) for end-users ensures that they have the most seamless experience possible when working with published RemoteApps. This means the user they are logged in with on their workstation is passed over to the remote desktop connection backing the published RemoteApps.
This provides the best experience for the end-user as they get the seamless experience of simply clicking the icon for the published app. It launches without any additional entering of username or password.
What is RemoteApp?
RemoteApps are a feature of RDS that allows essentially “streaming” an application over an RDP connection. This means the end-user experience is virtually the same as working with a locally installed application and provides many benefits.
Benefits of RemoteApp
What are the benefits of Windows Server RDS RemoteApp? RemoteApp provides a number of benefits to organizations compared to full desktop sessions presented in RDS. First of all, many end-users only need access to applications and not full desktops. For many end-users who may have access to a full desktop session, all they really do with that desktop session is launch an application. If this is the case, why not simply publish a RemoteApp application?
RemoteApp publishes require far fewer resources than a full desktop session. This means you can host many more users using RemoteApp as opposed to a full desktop session. The end result is the ability to have a much smaller hardware and overall infrastructure footprint using RemoteApp.
RemoteApp can also help to narrow in the scope of application resources. By streaming an application from a Remote Desktop Session Host, the only resource that needs to directly connect from a network perspective to application resources is the RDSH server. This can greatly help from a security perspective.
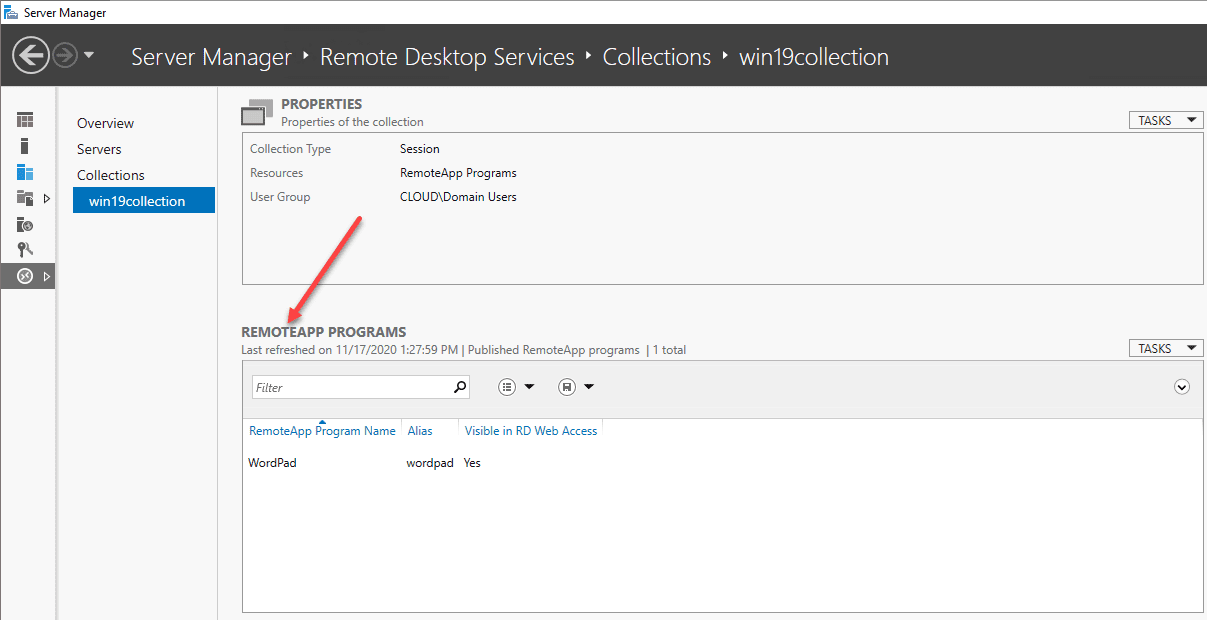
Configure Windows Server RDS 2019 SSO
The process to configure Windows Server RDS 2019 SSO is fairly straightforward. However, there is a tweak I had to make with the RDP file that is created from the RemoteApp publish. More on that a bit later.
Let’s look and see how you configure single sign-on (SSO) for desktop sessions and RemoteApp. This is made possible by means of a group policy setting on the client side. This means this is a setting you configure on the Windows 10 client that is initiating the RDS or RemoteApp connection.
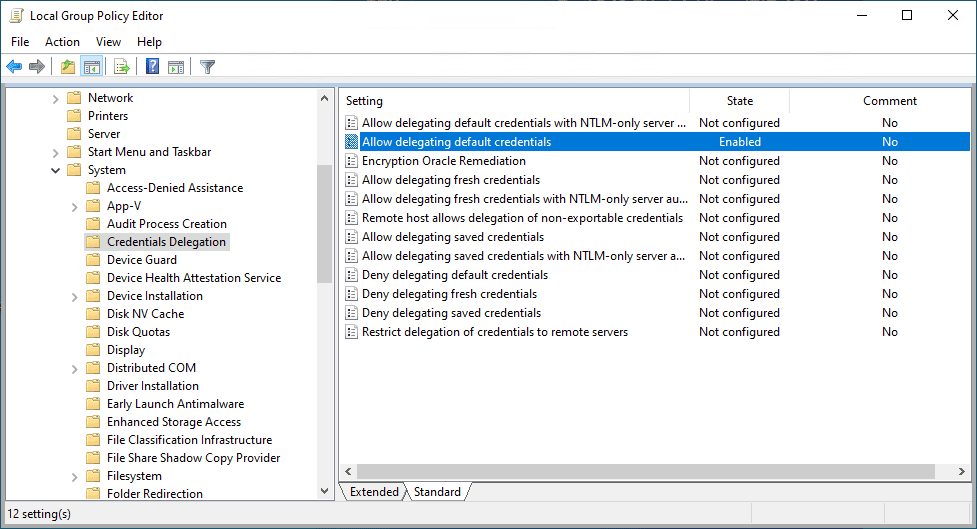
In Windows 10, navigate to Computer Configuration > Administrative Templates > System > Credentials Delegation > Allow delegating default credentials.
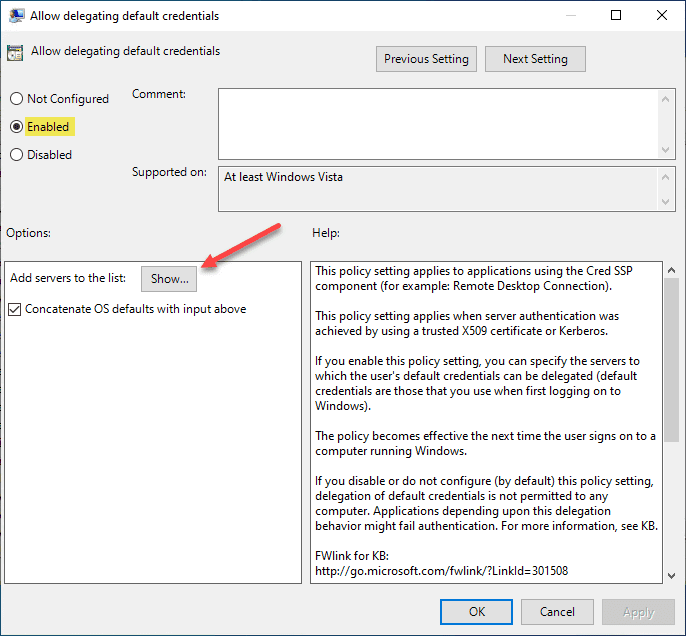
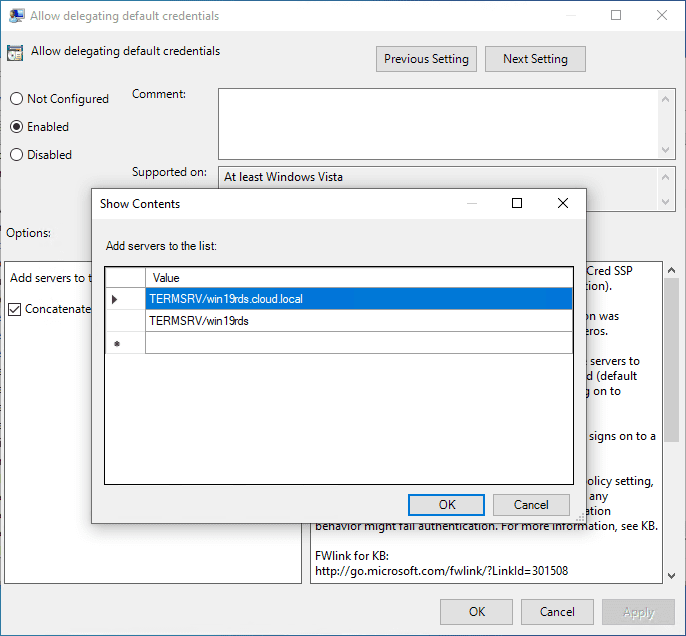
On the Allow delegating default credentials policy dialog box, click the Show button next to Add servers to the list.
This opens a Show Contents dialog box. In the dialog box add the names of your Windows Server 2019 RDS servers in the format below. Note the TERMSRV/ in front of the server name.
TERMSRV/win19rds.cloud.local TERMSRV/win19rds
After you enable the server names for credential delegation, you should be able to launch RDS 2019 SSO connections without being prompted for your credentials. The same is true of RemoteApps. However, I did run into an issue with RemoteApp below.
Username format issue for SSO
You may find that after you enable the SSO entries for delegated permissions to target your Windows Server 2019 RDSH box, your plain RDP connection to the RDSH server work as expected, but not the RemoteApp connection.
I found this to be the case as well. However, what I noticed was that by default, when you publish a RemoteApp from Windows Server 2019, the RD Gateway Server expects the username in the UPN format. As a quick refresher, usernames can be formatted in a couple of different ways.
- DOMAINusername – This is known as the NetBIOS domain format with a separator and then the username.
- [email protected] – This is known as the UPN format or user principal name.
You can read more about user name formats in the Microsoft KB here:
I had to tweak the RDP file that I downloaded from the Windows Server 2019 RDS server for it to correctly pass the credentials. I am still trying to flush out if this is specific to my lab environment. In case you run into this in your own environment, this is what I had to do.
- Edit your RDP file in notepad.
- Change the value gatewaycredentialssource:i:0 to
- gatewaycredentialssource:i:2
This denotes that it uses the same logged in user for your gateway server connection.
Concluding Thoughts
To configure Windows Server RDS 2019 SSO this is basically a setting in group policy applied to your client workstation that will be running the RDS session or RemoteApp connection. Once you configure the setting to delegate your credentials, you will be able to simply launch an RDP session or RemoteApp session to the RDS server and not reenter your credentials.
Google is updating how articles are shown. Don’t miss our leading home lab and tech content, written by humans, by setting Virtualization Howto as a preferred source.


i did this GPO but still get prompted. I am using the RDP file downloaded from RDWeb access.