When it comes to setting up a safe way for your kids to access the Internet, it is becoming more difficult. Especially if you have small children, you want to set up many safeguards to be able to protect them from the types of content that can easily be stumbled upon. Also, having a way to have more lenient web browsing for the adults in the house can present a challenge to have a happy medium between the two. No matter how good your web filtering is, there are generally sites that can be stumbled upon that are not filtered. Web filtering is an inexact science. It is a constant cat and mouse game of updating filtering technologies to properly categorize sites and allow these to be filtered properly. I wanted to go through what I settled upon that allows completely locking down Internet connectivity for small kids and allowing them to go to only the sites you want them to visit. Let’s take a look at how to configure safe Internet browsing for kids.
Safe Internet browsing technologies
Some may read this post and say, wow this seems very complicated and I could probably do that with pay for third-party control app of some sort. I agree with you. There are some solutions out there. I have bought into a couple for testing and tinkering.
However, there is just usually things about that approach that you can’t control, traffic-wise, for devices. This is especially true for IOS devices. These types of apps are a bit hamstrung for Apple devices.
Plus, I like tinkering and have a home lab environment with VMware vSphere infrastructure that I can make use of for various things. This is part of the reason I am going the route of the following:
- Creating a separate network
- Using a dedicated virtual firewall for kids network
- Using a dedicated web filter for filtering web traffic
- Using a “whitelist” approach for URLs instead of allowing free surfing across the board
Currently, my main home lab firewall is a Palo Alto PA-220 that I use all ingress and egress traffic from multiple VLANs. I also have a Ubiquiti wireless setup with controller and AP-Pros that I will be using to present the new SSID.
Technologies to Implement:
- New VLAN for Kids-only network
- New static route for Kid network
- New virtual NGFW appliance for Filtering kids traffic – Using Untangle 16 with HomePro license ($50) – See here: https://www.untangle.com/shop/ng-firewall-homepro/
- The Untangle appliance is NAT’ing traffic for internal clients. To do that, I have it handing out DHCP addresses. Then these are presented as a single IP on the other side. This is the address seen traversing to the public Internet through the other firewall.
Network Topology
Below is a very simplified view of the network topology that helps to give an idea of how the network traffic flows between the kids network and the Internet.
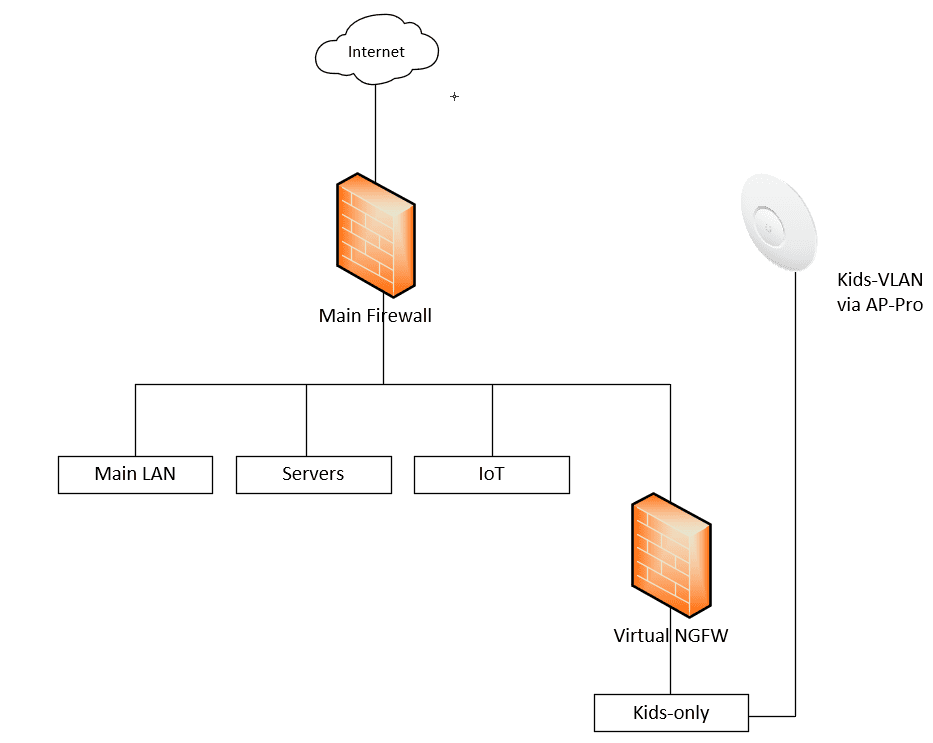
This allows completely segmenting the kids network and controlling Internet independently of the main firewall. While in the Palo I can create different web filtering policies, it is easier to have the separation and do all of the filtering in the separate web appliance and leave the Palo for the additional filtering and main filtering and protection for the other networks.
Also, this helps to make it easy to pinpoint any issues or connectivity issues since all of the “kid traffic” will come from a single IP address presented on the “public” side of the Untangle interface.
To create the denied list of URLs that the kids can get to, you can block everything. I checked all categories here. This way, everything essentially is blocked as the miscellaneous group captures anything that really doesn’t have a particular category.
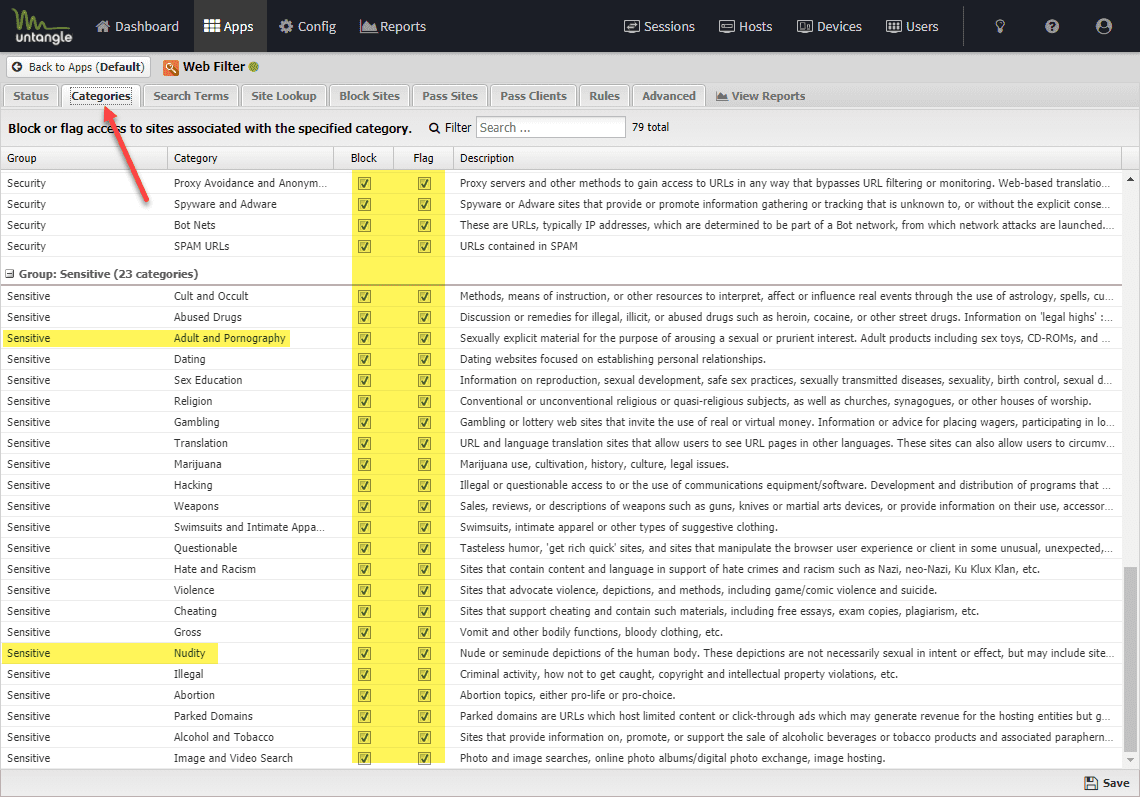
Now for the Pass Sites, you can explicitly define websites that are allowed. This allows basically allowing on specific URLs that you want the kids to be able to browse to.

Using this approach works quite well. The kids are able to hit the access point, be handed over to the internal VLAN. This allows the Untangle box to hand out an IP and handle web filtering which is basically blocking everything besides a handful of allowed URLs that can be hit from the inside.
Other use cases for locked-down Internet access
While I have presented a use case for safe Internet surfing for kids, this same approach can be used for a number of different use cases. If you have a specific number of machines such as with a kiosk or other use case that you want to only be able to visit a certain number of sites, you can use this same approach.
Using virtual firewalls allows for a great deal of flexibility in how traffic is funneled through your virtual infrastructure. Even if you don’t have a full-blown virtual environment at your disposal, this same approach can be used with a hardware firewall using Untangle, loaded on a white-box appliance.
Concluding Thoughts
Creating safe Internet surfing for kids is easy to accomplish with the Untangle NGFW and a little bit of networking. This allows creating a network that is safe for kids, locked down to only a handful of websites, and with the ability to easily add and remove sites.
Google is updating how articles are shown. Don’t miss our leading home lab and tech content, written by humans, by setting Virtualization Howto as a preferred source.