Passwords are a basic component of user security. Managing passwords across your infrastructure can be an extremely challenging task, especially in larger environments. There is a specialized account that is generally used in Windows environments known as the service account.
Service accounts are usually special-purpose accounts that are provisioned solely for authenticating a Windows service on a server with Active Directory so the service can start, run, and have access to other resources under the user context of the service account.
There are several security and compliance considerations that need to be addressed with service accounts in general regarding password management. Microsoft introduced Managed Service Accounts to help address some of these issues. However, let’s take a look at another tool that can greatly simplify Windows Server service account password management.
Windows Service Account Password Challenges
Historically, there are many challenges that revolve around service accounts and changing the passwords for these. Especially if an account is being used on a system that is “in scope” as part of a compliance regulation like PCI-DSS, the passwords must be changed on a specified interval for compliance.
Organizations that have many different servers running hundreds, maybe even thousands of service accounts can certainly experience pain when it comes to manual management of service accounts. However, the traditional ways of dealing with service accounts was difficult.
Most organizations, especially SMBs and smaller-sized environments, services accounts in Active Directory are generally created with a password set to “not expire”. This ensures the password will not age out. For those environments due to compliance and other reasons who have to change the Windows service account passwords generally resort to a manual process of changing the password and then rotating through all resources that are using the service account and manually changing the service account passwords that way.
Setting a service account password to never expire in an Active Directory environment can lead to pretty major security concerns, even if the password is long and complex.
Additionally concerning, developers may hard code service account passwords in configuration files and other “plain text” files that are referenced by applications and other code.
Managed Service Accounts (MSAs) and Group Managed Service Accounts (gMSAs)
In case you weren’t aware, Microsoft introduced a feature starting in Windows Server 2008 R2 that helps to provide a security mechanism for non-interactive user acocunts that are used for service accounts. These are called Managed Service Accounts (MSAs).
The power of the MSAs and gMSAs is they are designed to provide Windows service accounts and other entities like IIS application pools the ability to share their own domain accounts and eliminate the need to manage the service account passwords manually.
You can read more about the Managed Service Accounts (MSAs) here:
The managed domain account is an account that handles the password changes for the account automatically. The Group Managed Service Account (gMSA), introduced in Windows Server 2012/Windows 8, extends the capabilities of the MSA even further.
Previously, with only the MSA, the computer account is limited to one domain server and the passwords are managed by the computer. MSAs were limited to one domain server and the passwords are managed by the computer.
This means the limiting factor with MSAs is they could not be shared across multiple systems. This meant the accounts for each service on each system had to be regularly maintained to prevent password expiration.
This particular problem was solved by Microsoft with the gMSA since the accounts are now managed by the domain controllers and can be retrieved by more than one Windows 8/Windows Server 2012 system.
To learn more about creating and getting started with Group Managed Service Accounts, take a look at the whitepaper here from Microsoft:
A Better Way to Manage Service Accounts in Windows Server?
Even with the improvements with Group Managed Service Accounts (gMSAs), getting the accounts configured on the domain as well as correctly deploying it throughout your environment can be a bit challenging.
Additionally, you will note reading through Microsoft’s documentation, it is difficult to find good documentation on how this is audited from a password change perspective and having centralized visibility to these types of configurations and password changes for your Windows Server service accounts.
I would like to introduce you to a feature of Securden Privileged Access Manager (PAM) that makes the process of managing your Windows Server service accounts even easier.
With Securden Privileged Access Manager (PAM) you can easily do the following:
- Discover where the service account is being used
- Change the password of the existing Windows service account
- Synchronize the service account password change to all the remote servers referencing it
- Configure automatic service account password changes on a set schedule
- Have full visibility and auditing of all activities related to the Windows service account password change
Let’s take a look at these and see how Securden provides the above functionality.
1. Discover where the service account is being used
Unlike the MSA and gMSA, you don’t have to create a new service account with Securden. Securden is able to discover the existing service accounts that you have in your environment and all the dependencies that are using that service account.
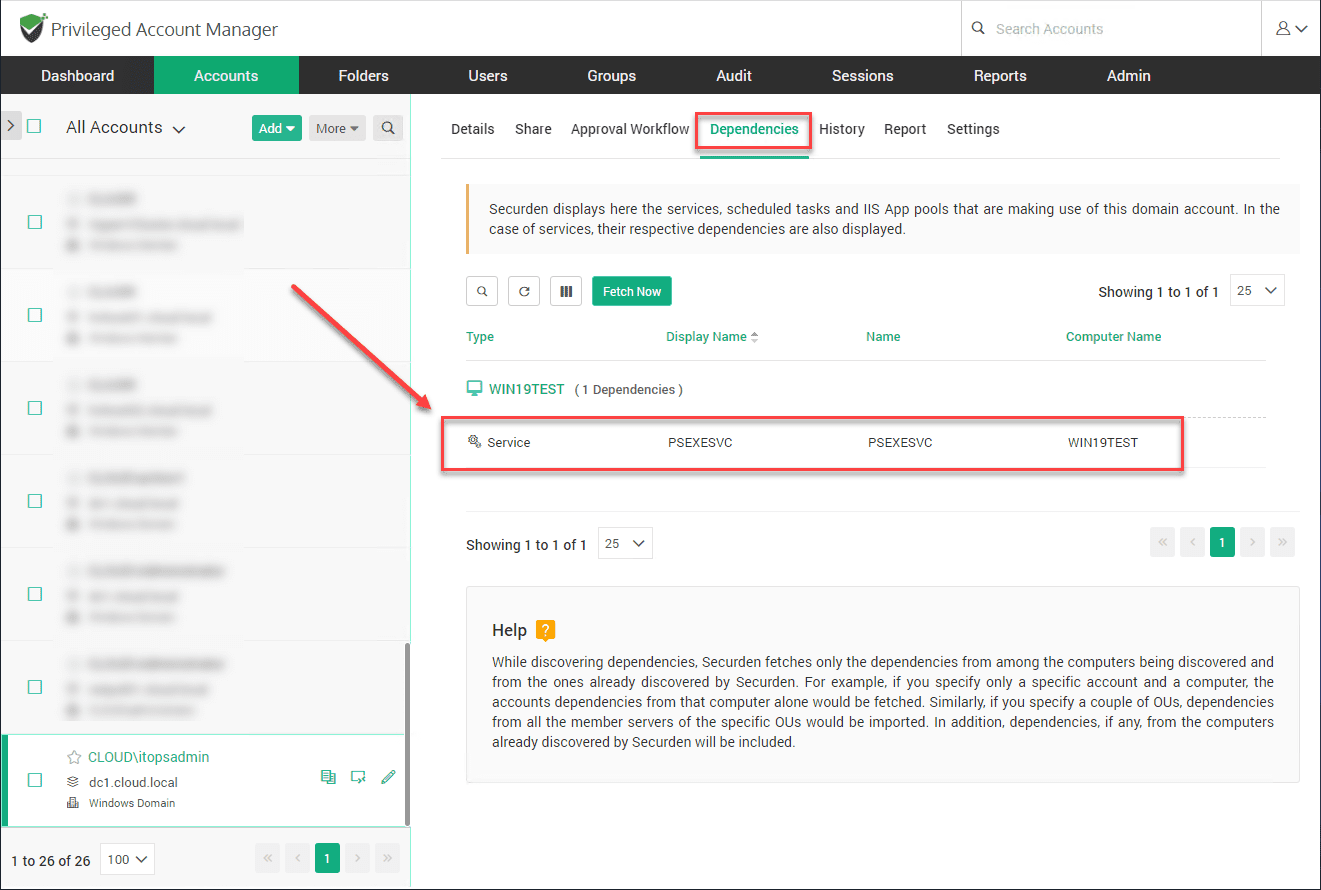
Below, I have already synchronized Securden with my Active Directory environment to pull in all the accounts. Under the Dependencies tab, you will see the dependencies using the service account.
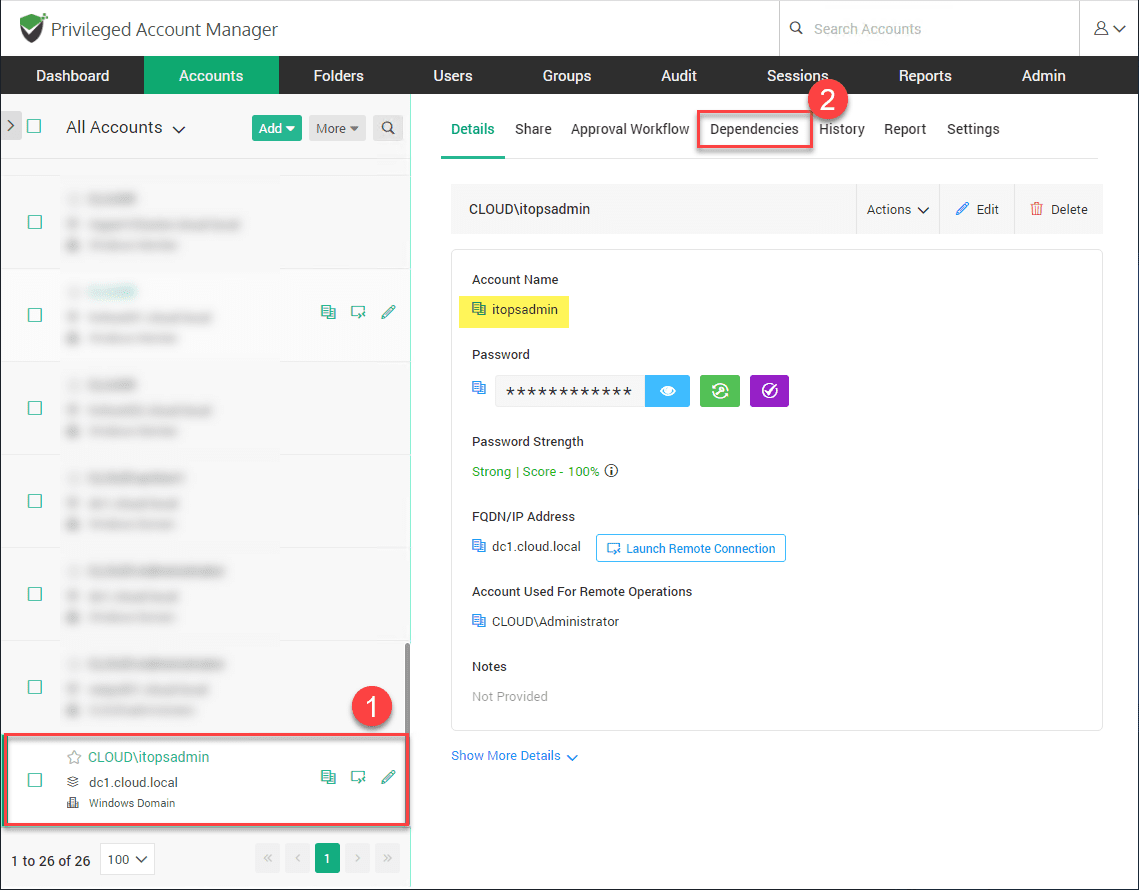
As you can see, under the Dependencies tab, you see where the service account is being used. We see the machine name as well as the service in particular that is using the Windows service account.
You can imagine how powerful this functionality is if you have dozens, even hundreds of machines using a particular account.
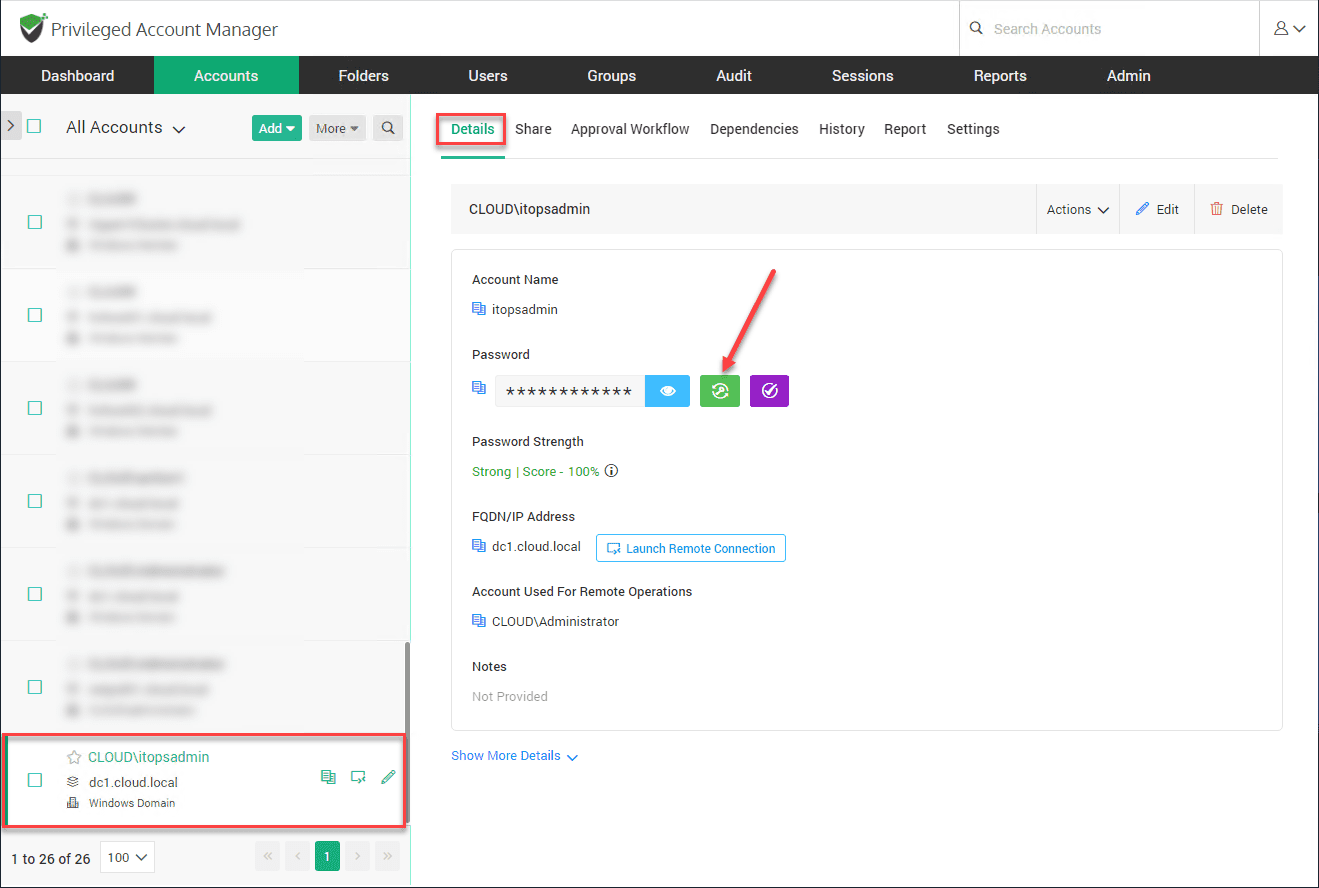
2. Change the password of the existing Windows service account
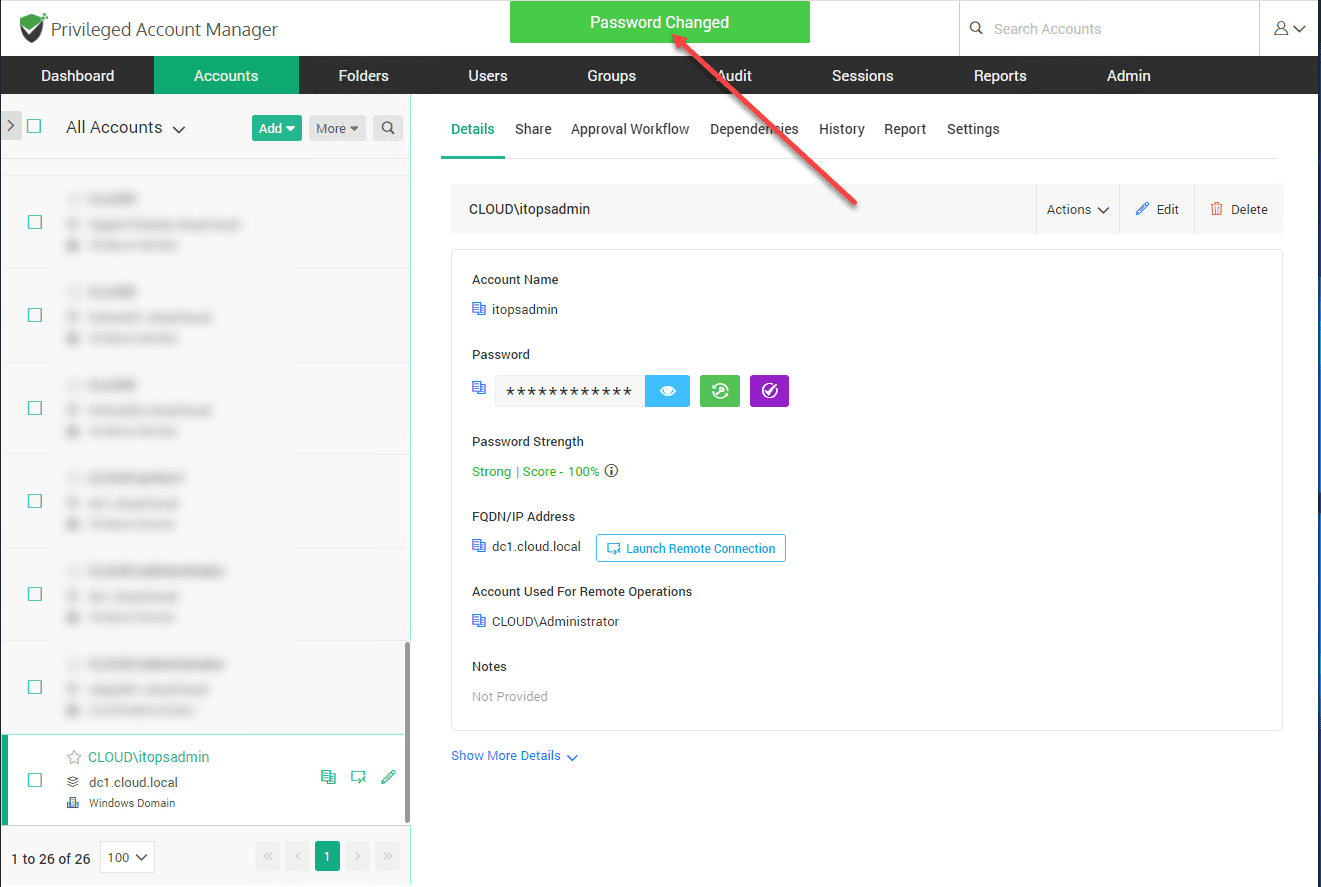
Let’s manually change the password of the existing Windows service account. Next to the password field, the second symbol button is used to change the password.
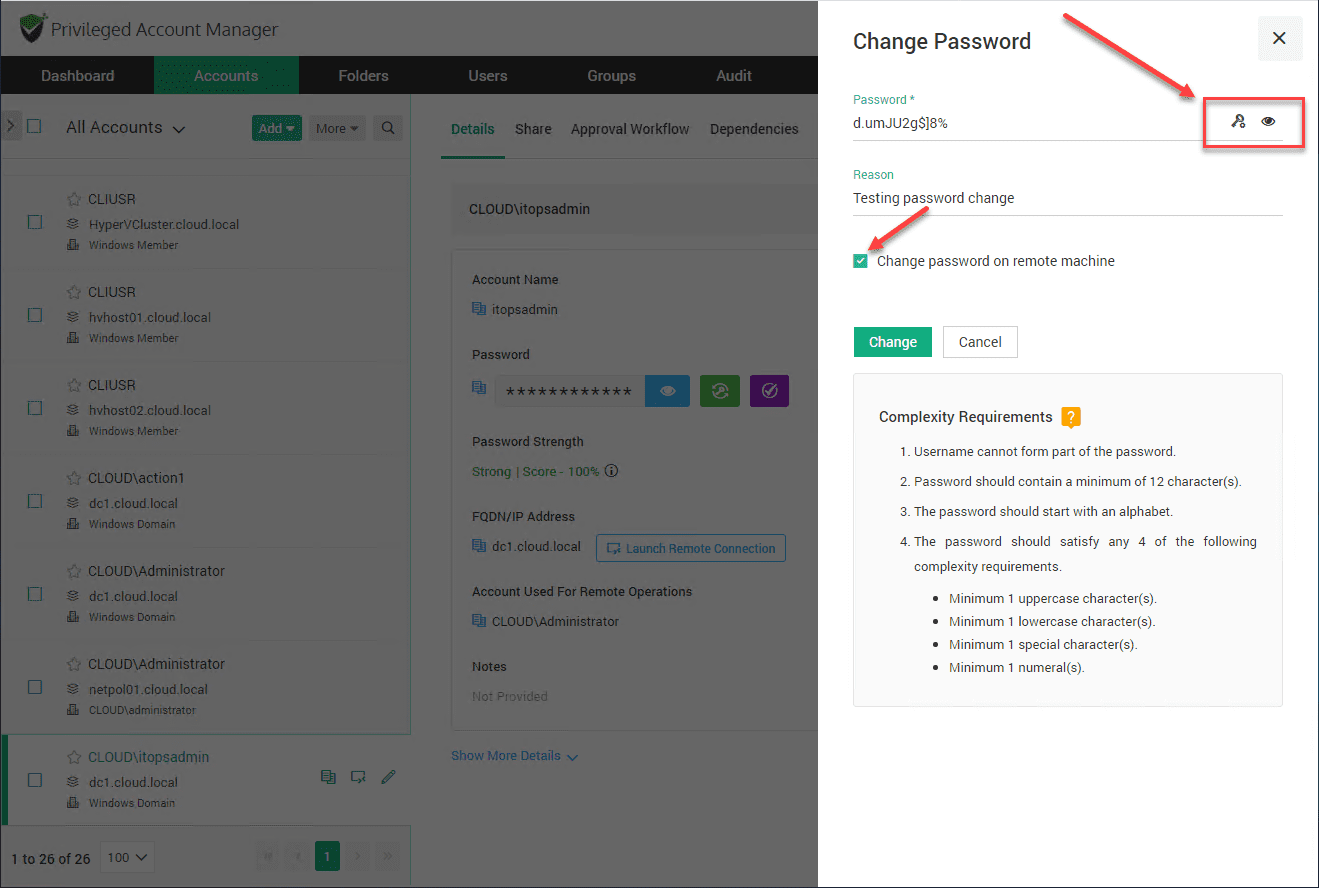
3. Synchronize the service account password change to all the remote servers referencing it
You can now change the password for the service account. Notice the checkbox Change password on remote machine. This allows changing the password on the remote machines referencing the service account.
I have click the “eye/show password” symbol to show the type of auto-generated password that Securden will assign to the account if you allow it to generate the new password. Click Change.
You will see the Password Changed pop up after you submit the password change.
4. Configure automatic service account password changes on a set schedule
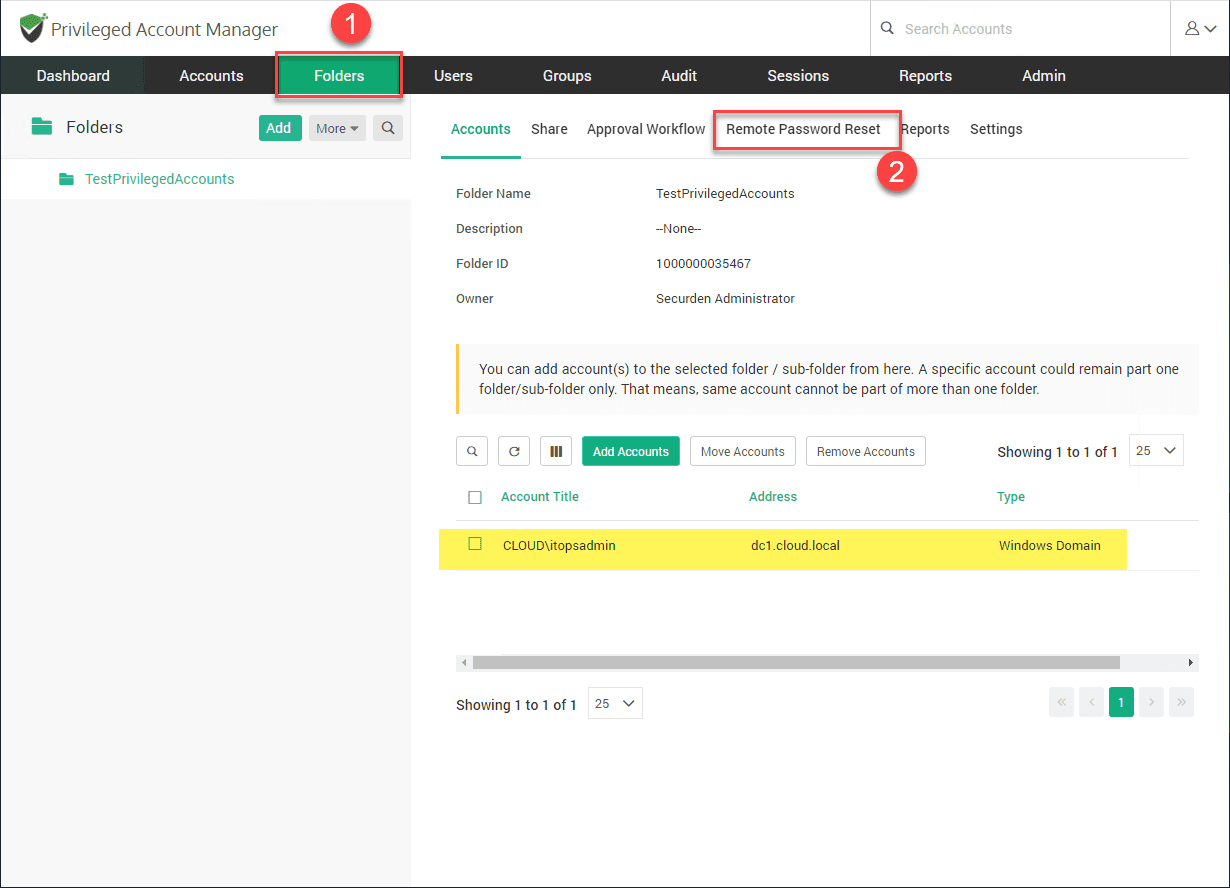
A Folder in Securden is a grouping of accounts. Here I only have one account in the “test” folder. Once you have a specific account or group of accounts in a folder, you can click the Remote Password Reset tab to begin configuring the automatic password reset feature.
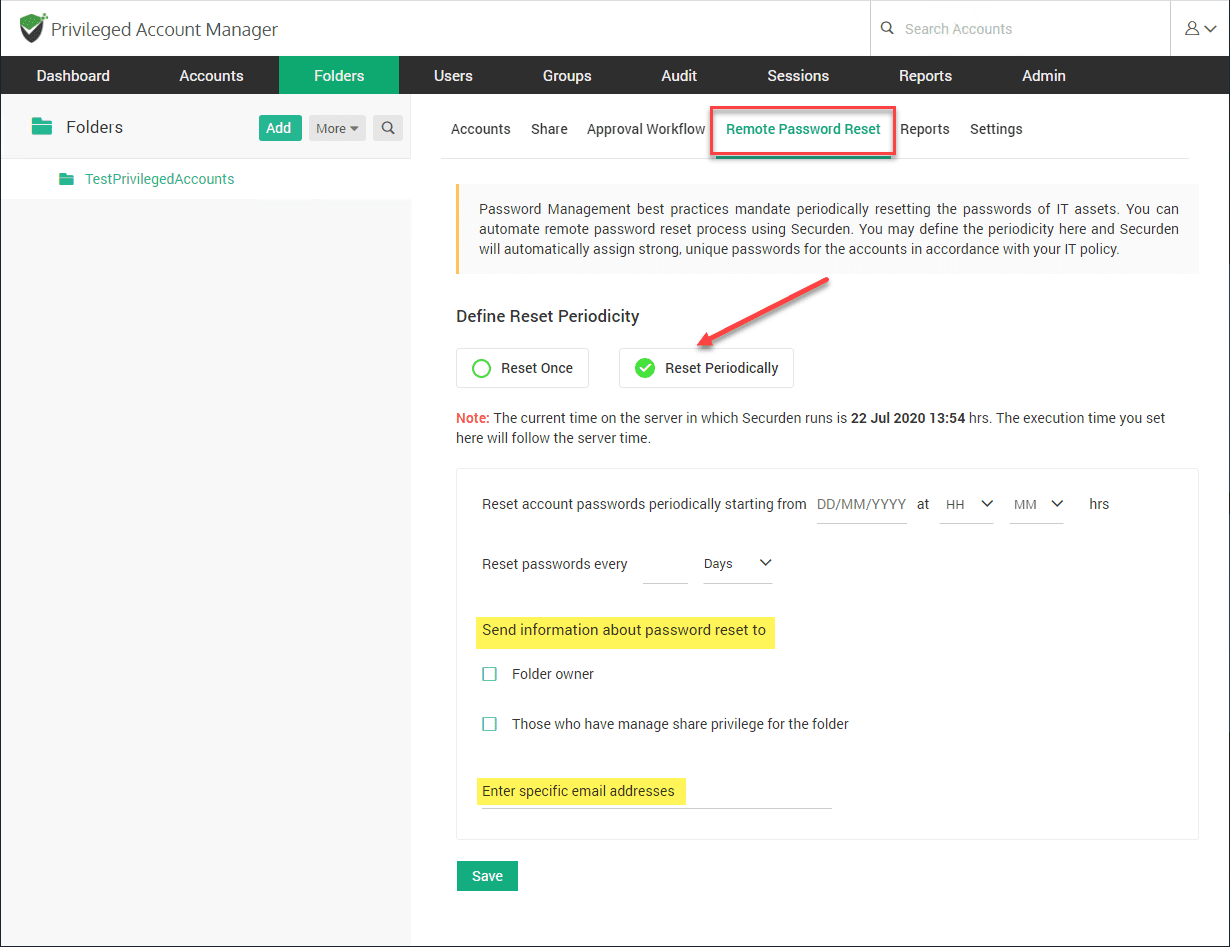
Flag the radio button Reset Periodically. You have options here to reset the password periodically and setting the number of days and even the specific hour. You have several options to be notified of password changes as well, even specifying specific email addresses.
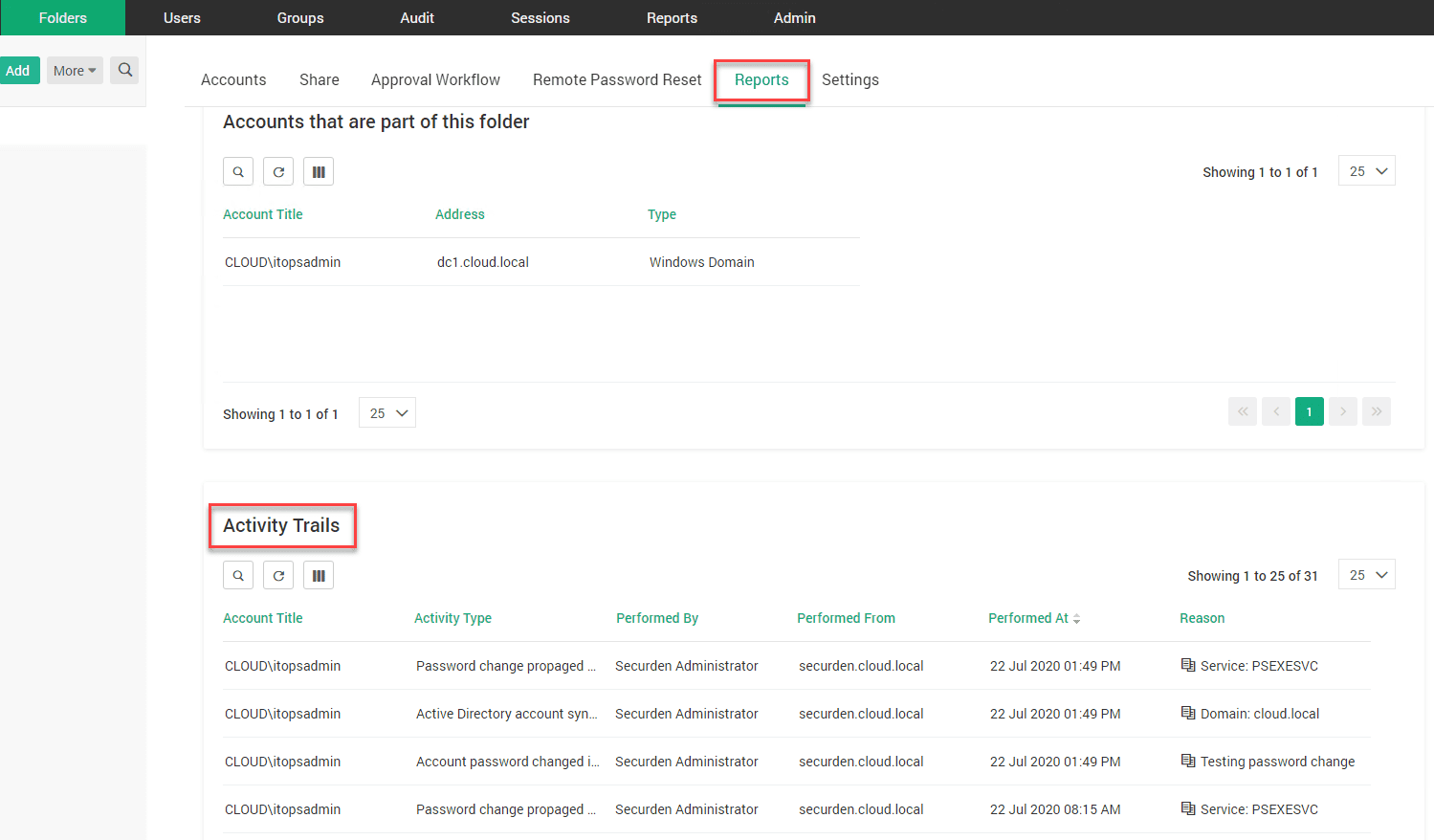
5. Have full visibility and auditing of all activities related to the Windows service account password change
The great thing about Securden managing the automated password resets of your service accounts, you have a full audit trail of all activities associated with the password change.
Wrapping Up
Service accounts can be extremely problematic when it comes to security and compliance as they are typically very cumbersome to change frequently using traditional account management.
Windows Server Managed Service Accounts password changes can be accomplished using the MSA and gMSA functionality since Windows Server 2008 (MSA) and Windows Server 2012 (gMSA) respectively. However, there are drawbacks to using these built-in mechanisms.
Configuring the functionality is rather tedious, relying on PowerShell and other tasks to be accomplished. Securden’s Privileged Account Manager (PAM) solution is a much better way to manage Windows service accounts in your environment.
Securden provides a centralized dashboard that automatically discovers dependencies in your environment for accounts that are defined on Windows services. It allows changing passwords and pushing the change out to the remote machines that utilize it. You can also setup automatic password changes to periodically change passwords on service accounts without any manual intervention.
Additionally, Securden provides a full audit trail of all the Windows service account activities as well as notifications for password changes.
Check out Securden Privileged Account Manager (PAM) solution here.
Google is updating how articles are shown. Don’t miss our leading home lab and tech content, written by humans, by setting Virtualization Howto as a preferred source.