Ansible Manage Windows Servers Examples Guide
Managing your Windows Servers from the GUI in mass is not fun or efficient. While the GUI has its place for one-off and ad-hoc configuration, managing your Windows servers in an automated way is a much better option than using the GUI. This allows for much more efficient management at scale. Ansible is a great automation platform that you can get up and running quickly and use to interact with your Windows Servers to perform all sorts of tasks across your Windows landscape. This includes patch management, configuration management, provisioning, software installation, and many others. In this Ansible manage Windows Servers examples guide, we will detail a few examples of how you can use Ansible to manage Windows Servers in your environment.
Why Ansible?
Why should you use Ansible in your environment? I like Ansible for a number of reasons. First and foremost, for me, the time to value is very quick. Ansible skills are rather easy to pick up since it is a very human readable automation platform based on YAML files. Ansible is also agentless. This means that you do not have to install any agents on your Windows Servers to manage them.
It makes use of the WinRM connection to your Windows Server environment which means you already have a built-in way to manage Windows with Ansible without any additional software installation besides loading Ansible on a server to run your playbooks.
Ansible is a free tool as well. You can purchase Ansible Tower for the Enterprise, however, this is not required. Tower is a great tool that makes working in large environments much easier and provides a graphical interface to your Ansible environment. This makes some things much easier to do or see than working with Ansible from the command line.
However, for most, Ansible is easy enough to work with from the command line, and can be quickly setup on your favorite Linux distro of choice with minimal resources.
Installing and setting up Ansible for managing Windows Server
Installing and setting up Ansible for managing Windows Server is fairly simple. All I have setup in my environment is a simple Ubuntu 18.04 Linux VM with very few resources as it does not need much from a resources perspective.
Outside of the normal Ansible installation, to work with Windows Servers, Ansible relies on a specialized Python module called pywinrm. This will need to be installed for Windows Server connectivity and management.
In Ubuntu, you can run the following commands to get Ansible installed along with pywinrm.
sudo apt-get install python-pip sudo pip install --upgrade pip sudo pip install --upgrade virtualenv sudo pip install pywinrm sudo pip install ansible
Once you have Ansible installed, you can begin testing connectivity to your Windows Servers with Ansible. I mentioned earlier about Ansible making use of WinRM for connectivity to Windows. If you have tried to configure and use WinRM previously, you know that it can potentially be a bear to setup and ensure it is configured correctly for remote access from an authorized user.
Thankfully, Ansible has provided a ConfigureRemotingForAnsible.ps1 script that can be ran on a target Windows Server. The script configures WinRM for connectivity from Ansible.
You can download the script here:
Testing Ansible Connectivity to Windows Servers
After you have setup Ansible along with the pywinrm module and also have ensured your servers are configured correctly for connectivity to WinRM, you can start testing connectivity to your Windows Servers.
Ansible has a special module for Windows called the win_ping module. This module allows testing that Ansible can connect to your Windows Server using WinRM and has access using the credentials specified. It is a great place to start when looking to use Ansible to manage Windows Servers.
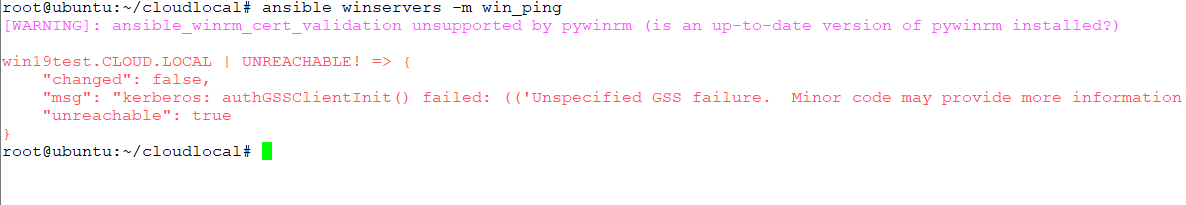
Below are examples of an unsuccessful connection and one that was successful. Below, I had not established connectivity and signed into the domain on my Ansible box.
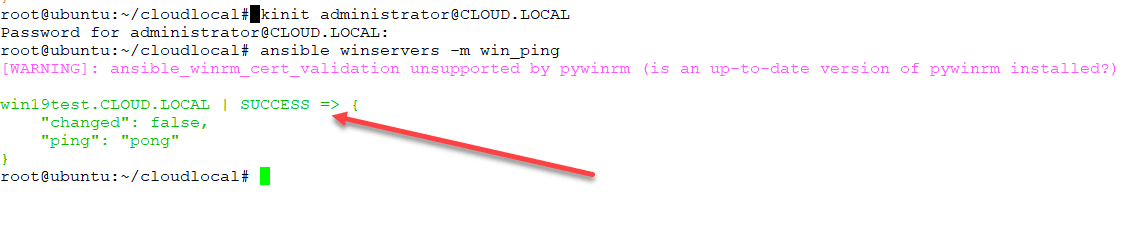
Below is the same server after signing in with domain credentials.
Manage Windows Servers with Domain Kerberos authentication
On the subject of authentication for Windows Servers based on domain credentials, I have a write up that I had put out some time ago, walking users through how to correctly setup Kerberos authentication for Ansible on a Linux box.
Check out the post for that content here:
Running Ansible Playbooks on Windows Servers
The next step after verifying you have a successful Ansible connection to your Windows Server is actually running a playbook. There are many great resources out there on how to run Ansible playbooks, so I am not going to reinvent the wheel.
Ansible playbooks work the same on Windows as they do with any other OS that Ansible is interacting with. So, often, you simply need to find the module you need for the operating system you are working with. There are good resources on general automation tips ad processes with Ansible here:
However, there are a few basics. To run an Ansible playbook in general, you simply can run the command:
ansible-playbook mywindowsplaybook.yml
As simple as that, you can run your first Windows playbook to perform any number of tasks on your Windows Servers. Adding the -v or -vv or -vvvvv switch after the end, ups the level of logging verbosity for your playbook run. This can be helpful if something fails.
Ansible Manage Windows Playbooks
Below are a few examples of Ansible playbooks that I have used for various things in the past.
What about Windows updates? Ansible can easily do that in a playbook:
- name: Search-only, return list of found updates (if any), log to c:ansible_wu.txt win_updates: state: searched log_path: c:ansible_wu.txt - name: install all critical and security updates win_updates: category_names: - CriticalUpdates - SecurityUpdates - UpdateRollups state: installed register: update_result - name: reboot host if required win_reboot: when: update_result.reboot_required
Installing applications in Windows is made easy with Ansible. Check out how easy it is to install applications like Chrome:
- name: Install Chrome
win_chocolatey:
name: googlechrome
state: present
Setting network properties such as DNS values:
# Set DNS addresses - win_dns_client: adapter_names: '*' ipv4_addresses: - 10.1.149.10 - 9.9.9.9
Joining Windows server to a domain:
- win_domain_membership: dns_domain_name: cloud.local hostname: win2016test domain_admin_user: [email protected] domain_admin_password: domain_ou_path: "OU=Servers,DC=cloud,DC=local" state: domain register: domain_state
Running command line commands in an Ansible playbook:
- name: Disable Firewall win_command: 'netsh advfirewall set allprofiles state off'
Creating a directory and copying files to it:
- name: Create directory structure and copy files to a directory
win_file:
path: C:windowstools
state: directory
- win_copy:
src: /root/test/resources/testfile
dest: 'C:windowstools'
remote_src: no
These are just a few of the little snippets that you can use in Ansible playbooks. If you can Google for something you would like to be able to do in your playbook, most likely you will find someone who has written exactly what you need.
Generally, there are Ansible modules that are already written to do many of the common tasks that you may need to do on a Windows Server.
Final Words
Using Ansible to manage Windows is a great way to be much more efficient and consistent in your efforts to automate and streamline Windows resources in your environment.
It is an easy automation framework to learn and can bring quick time to value in your environment, especially for repetitive tasks and configuration management. Hopefully the examples shown help to demonstrate quick and easy tasks that can be accomplished using Ansible to manage Windows.