VMware NSX-T 3.0 Released with New Features
You can’t think about network virtualization without thinking about VMware NSX. VMware NSX has evolved greatly over the past few years. The NSX-V product has slowly been getting deprecated in favor of the NSX-T release. NSX-T is the way forward with VMware network virtualization. VMware NSX-T 2.4 and then 2.5 were pivotal releases for NSX-T. With version 2.4, VMware achieved relative feature parity with NSX-V. At this point though, NSX-T contains more functionality than NSX-V. In this post, we will take a look at VMware NSX-T 3.0 released with new features including federated multi-site as well as distributed IDS/IPS.
VMware NSX-T 3.0 Released with New Features
On the heels of the release of vSphere 7.0, VMware today is releasing NSX-T 3.0. NSX-T 3.0 represents the latest and greatest features for network virtualization, not only in an on-premises environment, but also VMware Cloud on AWS, native AWS EC2 environments as well as Azure.
There are a load of new features contained in NSX-T 3.0 that include many highly anticipated features. These include:
- Federation support
- Distributed IDS
- LB/VPN enhancements
- Containers support with vSphere 7
- L3 Multicast, L3 EVPN and VRF Lite
- Converged VDS in vSphere 7
- NSX-T UI enhancements
- New automation support
Let’s take a look at these new features and see how they will provide great new features for the enterprise, both on-premises and in the cloud.
Federation Support
This is a big one. This feature has long been requested of VMware customers making use of NSX-T. It provides centralized, conssitent policy framework across large scale NSX deployments.
This allows for:
- Operational simplicity for NSX-T data center and NSX cloud
- Consistent policy configuration and enforcement
- Simplified DR
- Supports NSX DC and NSX cloud in NSX-T 3.0 with support for VMC on AWS in the future
NSX-T Federation positioning:
- Simplified management
- Security use cases
- Network use cases
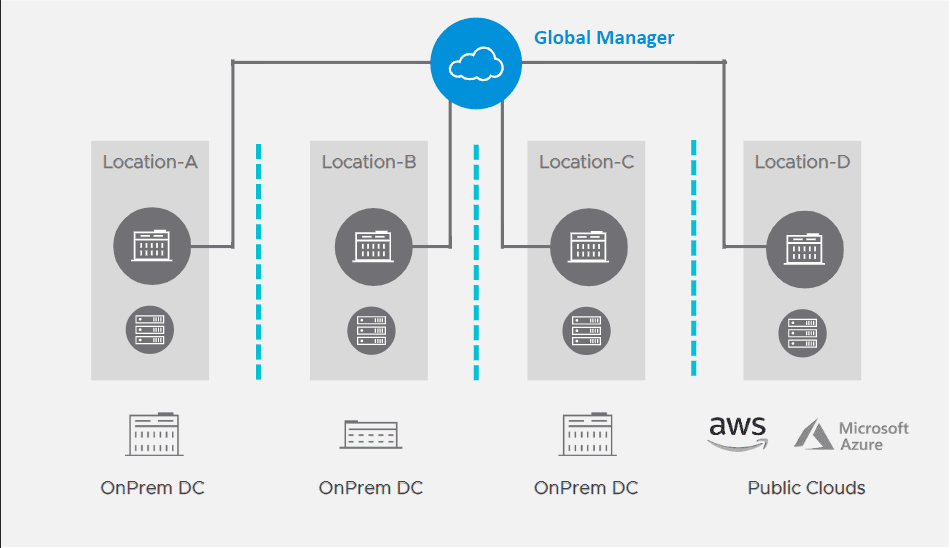
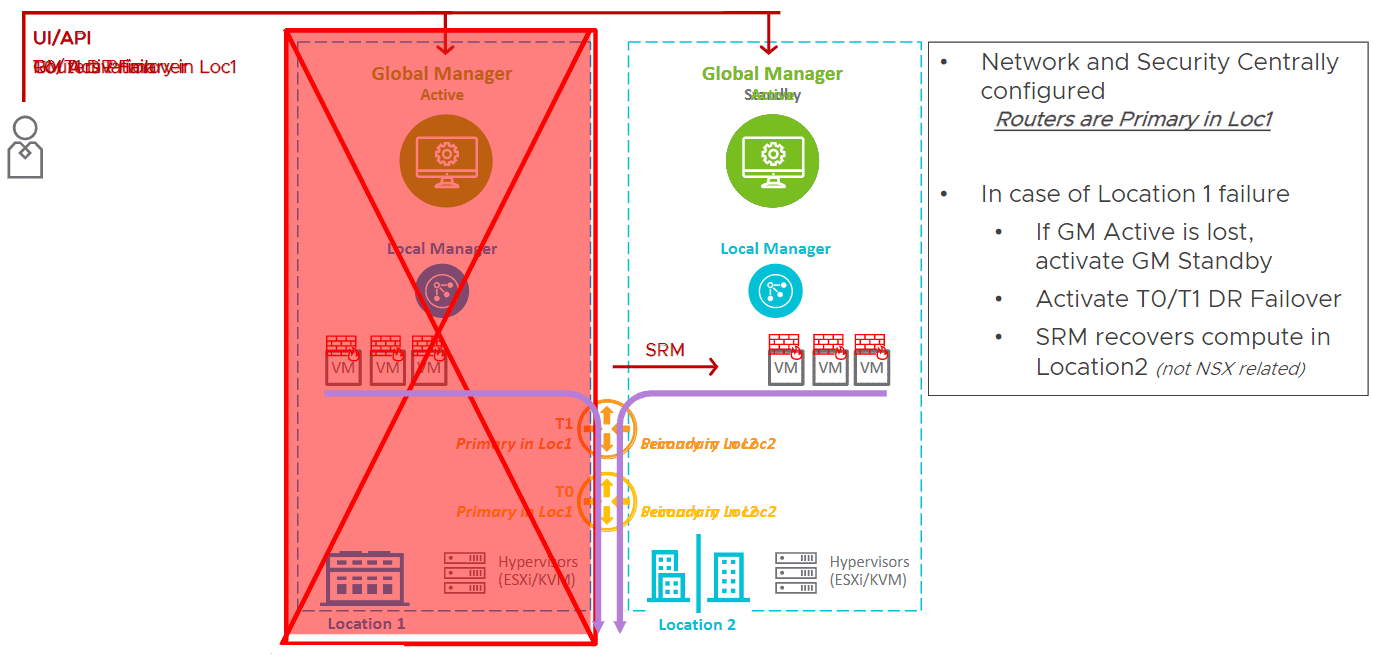
NSX-T 3.0 federation support is made possible by the new NSX-T Global Manager. The Global Manager, is a “manager of managers” if you will. It allows managing multiple NSX-T environments in a single pane of glass interface.
NSX-T 3.0 federation allows a solution to federate multiple NSX-T deployments over different locations. It can be on-prem, public clouds, native AWS, Azure. Benefits are threefold.
- Operational simplicity. Configure everything from single pane of glass called the Global Manager. Network and security objects are shared.
- Simplified DR – With federation this is made much simpler. If you have a DR scenario. Workloads are in one locaiton. You create the network and security objects in that location. A single logical router can be stretched between locations. In the pure DR use case, you can define primary location and secondary location.
- If you lose location 1, you lose everything in your primary location, you can recover quickly by means of the Global Manager standby. It takes one click to make it active. ActivateT0/T1 DR failover. Using this you have fully recovered your network and security to the secondary, DR location.
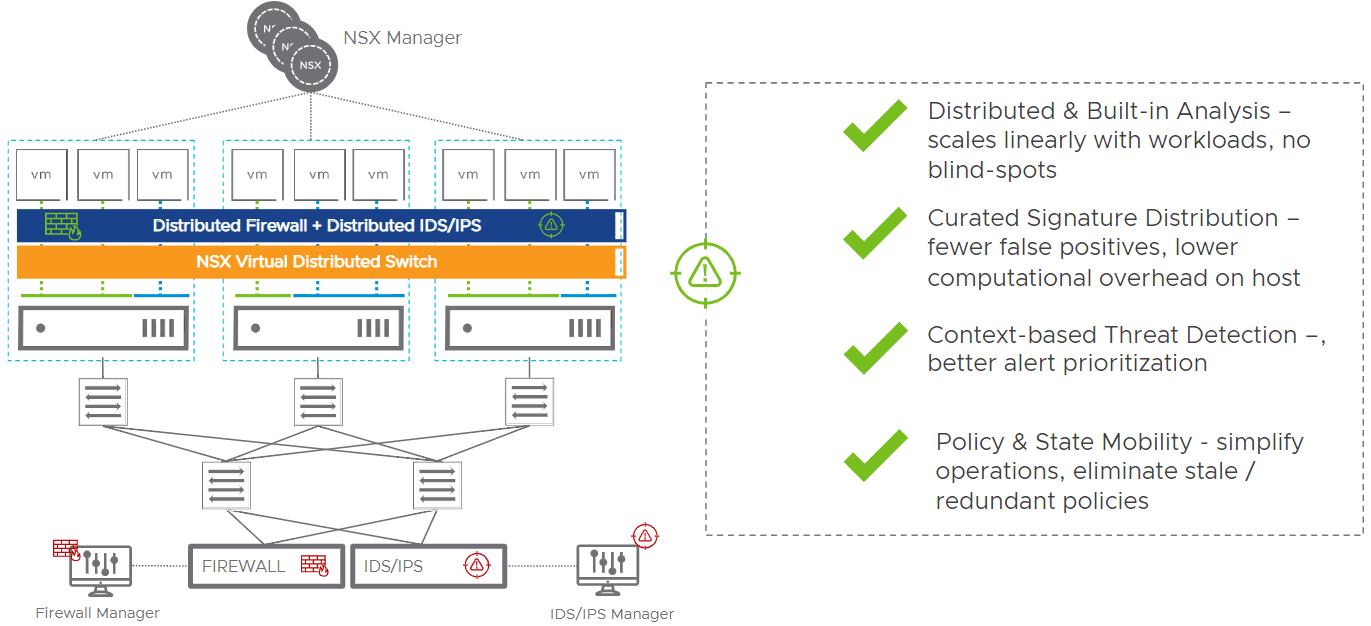
Distributed IDS/IPS
NSX Distributed IDS/IPS is extending the intrinsic security paradigm for internal firewall.
Traditionally in the datacenter, most customers deploy physical appliances to do IDS/IPS. You have to hairpin traffic to the physical network which creates network choke points. This doesn’t really scale very well, requires network rearchitecture and planning. It is often an inadequate and inflexible model for granular policy definition for lateral movement. Adding more applications means scaling up the physical IDS/IPS and lacks any application context or service awareness.
NSX Distributed IDS/IPS moves this functionality into the hypervisor. The distributed IDS/IPS functionality in NSX-T 3.0 is distributed and scales linearly with workloads, has no blind-spots, fewer false positives, and lower computation overhead on host.
In terms of efficiency, the IDS/IPS rules only get programmed to the vNic where it is relevant. This means that alert overhead is greatly reduced. IDS/IPS are basically regular expressions.
In traditional physical IDS/IPS implementations, since there is no context, all traffic gets examined for all signatures. However, with context-based threat detection, signatures can be mapped to VMs that are running specific services. For instance, you don’t have to map IDS/IPS rules for Linux to Windows VMs, which is a much more effective and efficient approach.
Use cases:
- Regulatory compliance
- Virtual zones – create zones in software without cost /complexity of air-gapped networks or physical separation, secure vendor-partner, provider-tenant traffic.
- Discrete appliance consolidation – replace discrete centralized appliances, leverage native IDS/IPS implementation in NSX – simply “turn it on”.
- Detect lateral movement – prevent lateral movement of attackers by blocking vulnerabilities, combine signature-based detection, anomaly detection, protocol conformance checks.
What are the benefits of the distributed IDS/IPS solution in NSX-T 3.0?
- Elastic throughput
- Simplified network architecture
- Operational simplicity
- Utilize stranded compute capacity
LB/VPN enhancements
There are quite a number of load balancer and VPN enhancements with NSX-T 3.0 including the following:
- Extra Large advanced load balancer and IPv6 for load balancer support – VMware is incorporating the Avi Networks LB technology in these new advanced load balancers as well as IPv6
- JSON Web Token, SSL pass-thru and dynamic SSL termination base on SNI
- L2 VPN on T1 and local egress
- Stateful VPN failover
- Intel QAT for IPsec
- TCP MSS / PMTU support
Containers Support with vSphere 7
NSX-T 3.0 supports the new vSphere 7.0 and the technology and capabilities that it provides in regards to containers support. The containers support with NSX-T 3.0 includes:
- Support for Project Pacific (included in vSphere 7)
- DLB support for Project Pacific containers
- Container inventory and monitoring
- IPv6 and ENS for containers
- NCP 3.01 Telco – Multus, LB, FW logging enhancements
- Scale – 50,000 pods
L3 Multicast, L3 EVPN and VRF Lite
There has been a lot of improvement in the L3 functionality with NSX-T 3.0. Highly anticipated features such as multicast. The following are improvements in this area:
- L3 multicast
- L3 EVPN and VRF Lite
- NAT64, DHCPv6 server
- Rate-limit on T1 uplink
- SRIOV support
- Edge VM XL Form Factor
- AMD Support for Edges
- Faster BFD timers
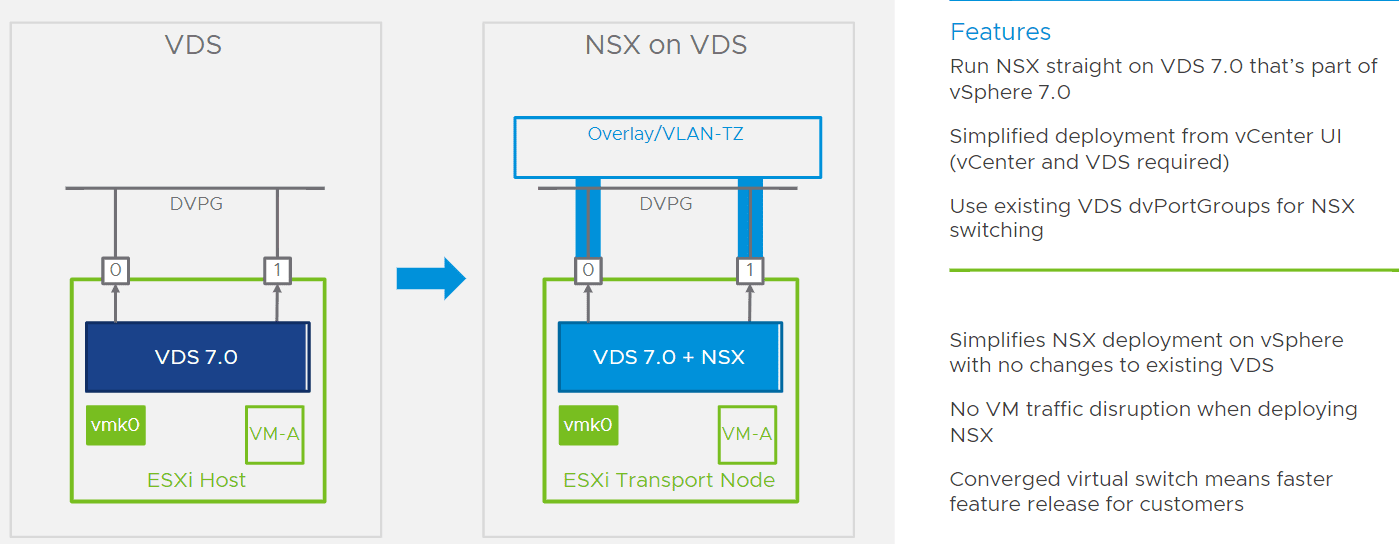
Converged VDS
A really great feature released with NSX-T 3.0 is the converged VDS. What is this? With the converged VDS, as soon as you install NSX-T 3.0, the existing VDS will be transitioned to a converged VDS. This means that port groups that already exist will continue to function as prior. Any new NVDS switches that are created will be imposed on the converged VDS.
This will help to serve to simplify the implementation of the NVDS switch and will also help to require fewer dedicated physical connections to the server.
This is an awesome new feature if you ask me. There is one caveat to this new functionality. Your hosts have to be running vSphere 7 to take advantage of the new converged VDS.
NSX-T 3.0 UI Enhancements
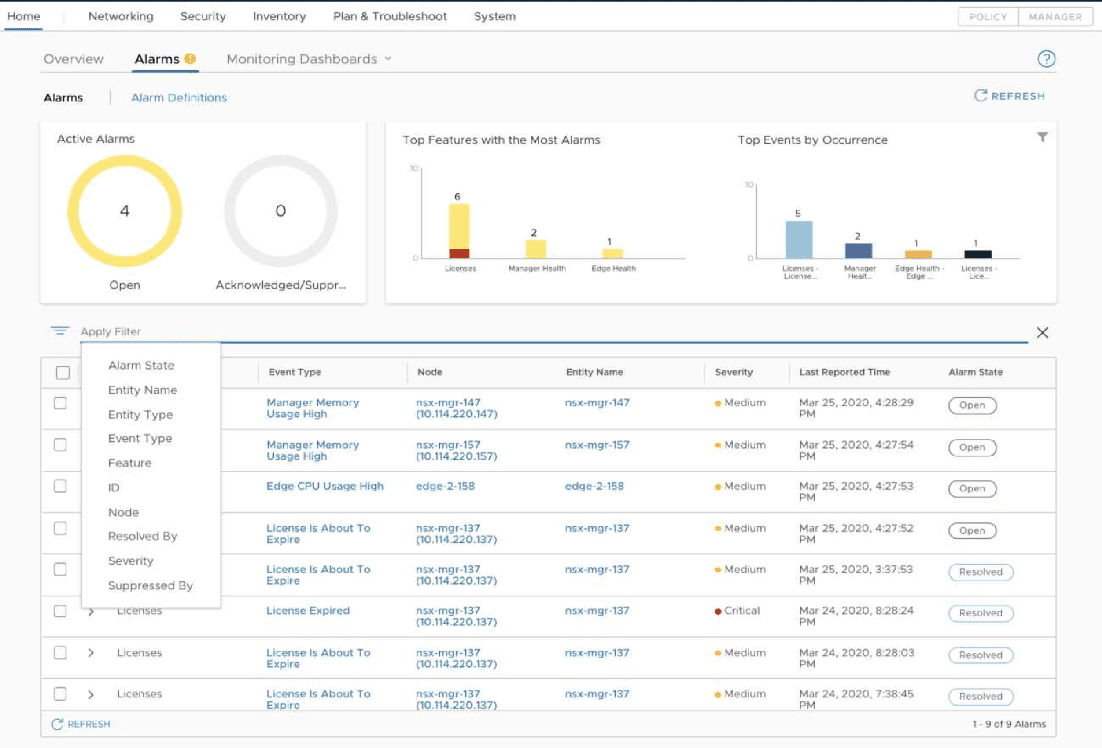
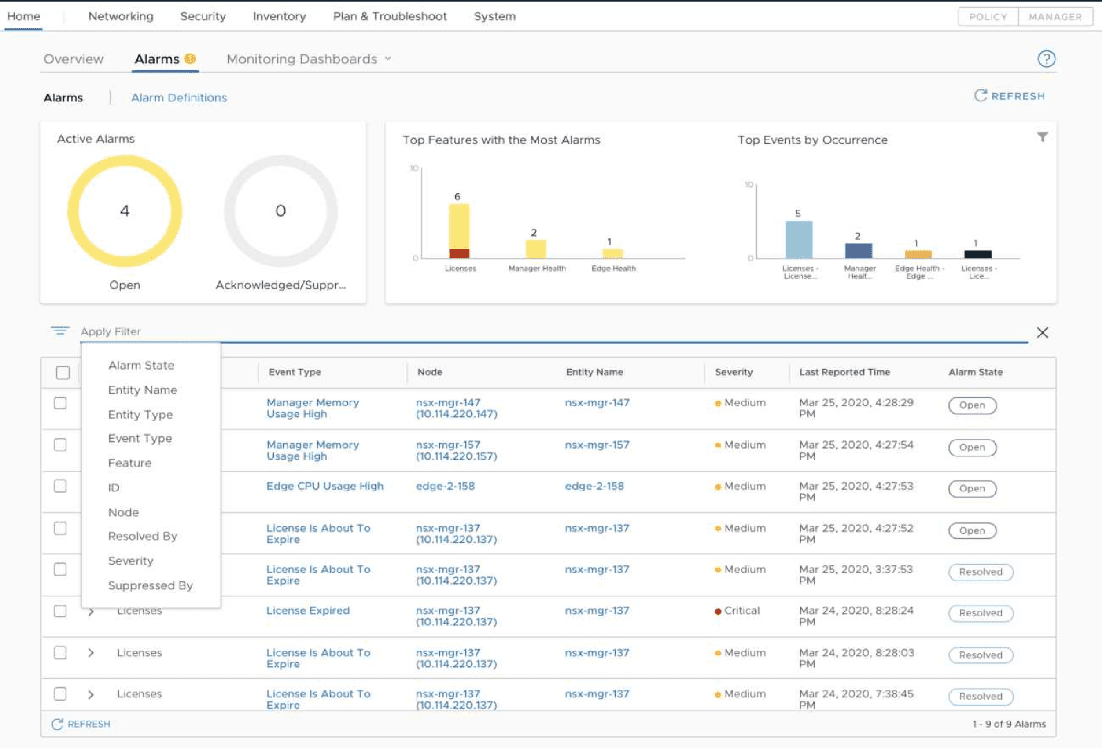
There are many great new additions to the NSX-T 3.0 UI. These include a brand new Alarms dashboard as well as Network Topology Visualizations.
With the alarms dashboard, you have a brand new consolidated view of all alarms in the environment that allows having visibility to and managing these much more easily. Besides numerous in-the-box alarms, you can even create your own customized alarms as well.
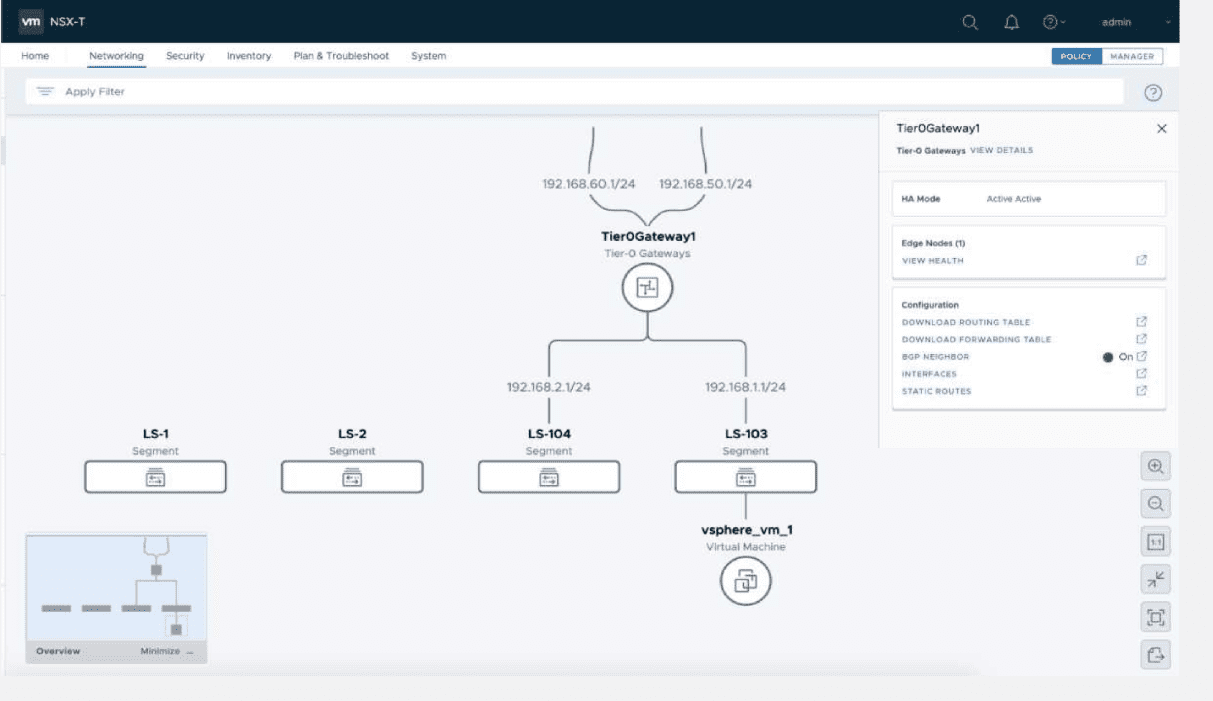
Another great new visual UI tool is the Network Topology Visualizations dashboard. This provides a graphical visualization of the network infrastructure, the ability to export the topology to PDF, and a search and filter to customize the topology view.
New Automation Support
VMware is always on the forefront of providing automation tools within the various products and solutions. NSX-T is no different here. It is great to see that with NSX-T 3.0, a terraform provider and Ansible module for NSX-T policy is being included. There is also Ansible Module support for NSX-T upgrades. Good stuff for sure!
Wrapping Up
Definitely exciting news with VMware NSX-T 3.0 Released with New Features today. This is certainly the premiere software-defined networking stack on the market today. The functionality and interaction with NSX-T is unrivaled by other offerings on the market.
The new features and capabilities with this release allow customers to truly have a solution that spans on-premises and public cloud environments as well as multiple NSX-T environments with the new federation capabilities.