VMware Unified Access Gateway UAG 3.8 Installation and Configuration
Considering the security of your end user computing environment that is accessed via remote connections is extremely important. When building out how your clients are going to access a VMware Horizon environment, you want to enable secure access. VMware has provided a way to do this with the Unified Access Gateway (UAG). The UAG is the replacement for the legacy Horizon Security Server and has many advantages to the older technology. In this post, we will take a look at VMware Unified Access Gateway UAG 3.8 installation and configuration to see how to stand up this security appliance in front of your VMware Horizon infrastructure.
What is the Unified Access Gateway (UAG)?
The UAG is an appliance that directs authentication requests to the appropriate server and discards unauthenticated requests. When directed through the UAG, users can access only the resources they have been given access to use.
The UAG appliance also bolsters security from the standpoint the user is only directed to desktops and applications to which they are entitled to use. It inspects the desktop protocols being used and coordinates access based on the policies and network addresses used for access.
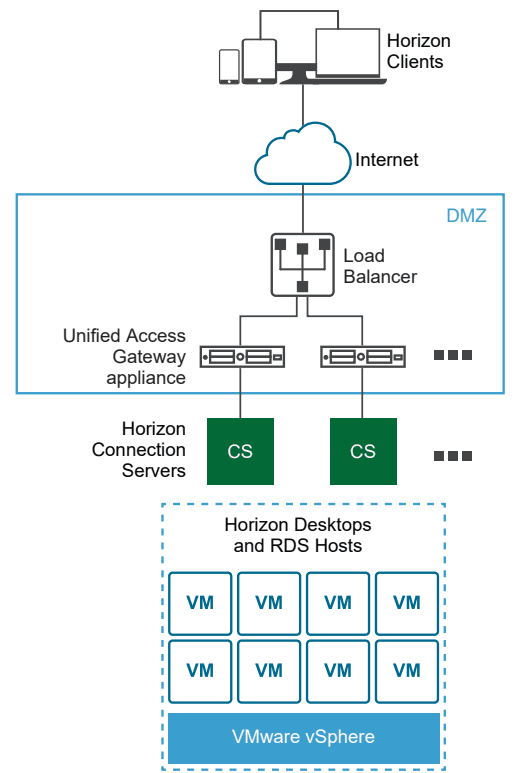
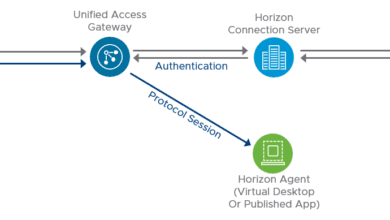
Think of the UAG appliance as a proxy to your Horizon Connection Server which resides inside your company’s network. By designing access to your Horizon environment using the Unified Access Gateway (UAG), you are able to provide an extra layer of security for your end user computing environment which can include virtual machines, application hosts, and even physical workloads.
In addition to the extra layer of security from an access perspective to the Horizon environment provided by UAG, it is also a hardened platform itself. It provides the following hardening settings from an appliance perspective:
- Up-to-date Linux Kernel and software patches
- Multiple NIC support for Internet and intranet traffic
- Disabled SSH
- Disabled FTP, Telnet, Rlogin, or Rsh services
- Disabled unwanted services
Unified Access Gateway (UAG) Architecture
The UAG appliance is generally deployed and configured inside the DMZ network layer. It helps to bolster security from the standpoint that it inspects access requests to the internal EUC environment and makes sure the user is what VMware calls strongly authenticated.
The UAG directs authentication requests to the appropriate server and discards the requests that are not valid.
Horizon Protocols Used in Accessing
Horizon access is comprised of primary and secondary protocols for accessing the Horizon environment.
The primary protocol details are as follows:
- XML-API over HTTPS
- This is used during the authentication phase of the connection process
The secondary protocol details are as follows after an authentication attempt is successful:
- HTTPS Tunnel used for encapsulating TCP protocols such as RDP, MMR/CDR and the client framework channel. (TCP 443)
- Blast Extreme display protocol (TCP 443, TCP 8443, UDP 443, and UDP 8443)
- PCoIP display protocol (TCP 4172, UDP 4172)
Why Use Unified Access Gateway Instead of VPN?
There are several advantages of using UAG over using the traditional VPN way of connecting to the network.
- Much Simpler Access Control – While you can configure network connection rules for individual users using traditional VPN using firewalls, etc, the administrative overhead with this is extensive. UAG Access Control Manager recognizes entitlements of users and allows connections to be made only to those resources.
- User Interface – Using the Horizon UAG environment, users are placed into the Horizon environment as expected. With VPN, the users first have to connect using VPN and then connect to their Horizon environment.
- Performance – Using UAG along with PCoIP and HTML access, security is applied without any additional encapsulation. Depending on the VPN technology used, it can lead to significant performance degradation when compared to connections made through the UAG.
VMware Unified Access Gateway UAG 3.8 Installation and Configuration
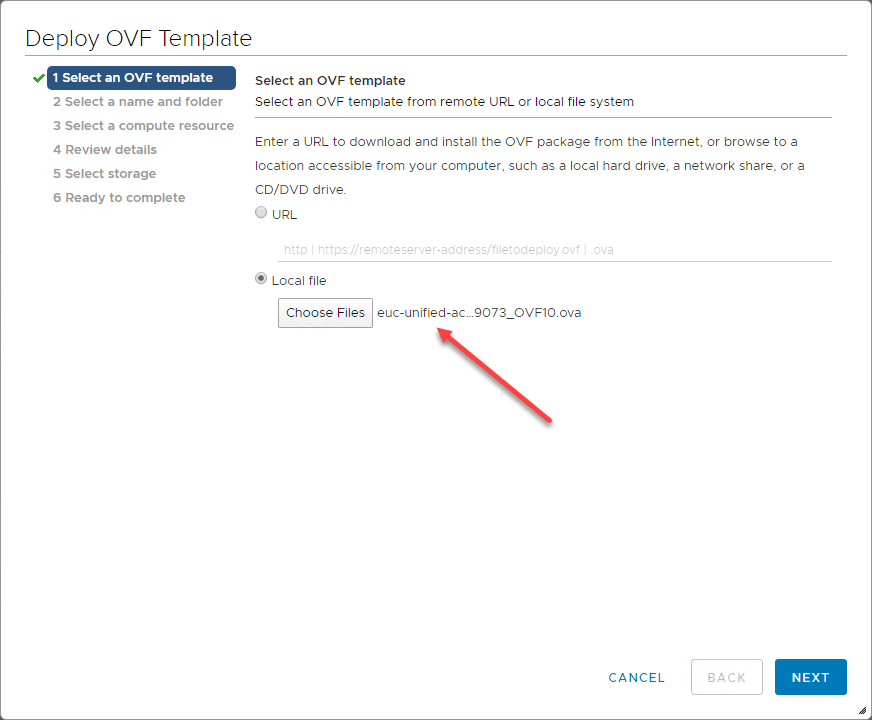
First things first, grab a copy of the UAG appliance from My VMware here. In case you haven’t seen yet, you can now deploy the UAG using a set of PowerShell scripts. Look for a post showing this method coming soon. For the walk through below, we will look at the OVA deployment of the appliance.
The file I downloaded (at the time of this writing) is the following:
- Unified Access Gateway (UAG) 3.8 for vSphere and Amazon AWS (Non-FIPS) – File name: euc-unified-access-gateway-3.8.0.0-15239073_OVF10.ova
Deploying the OVA file is pretty straightforward as you would expect.
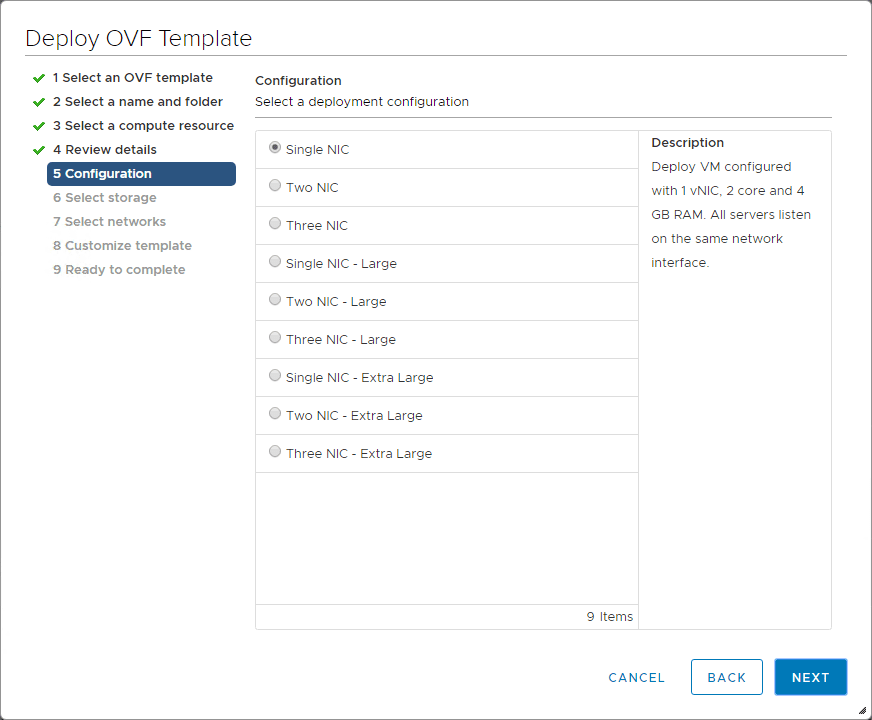
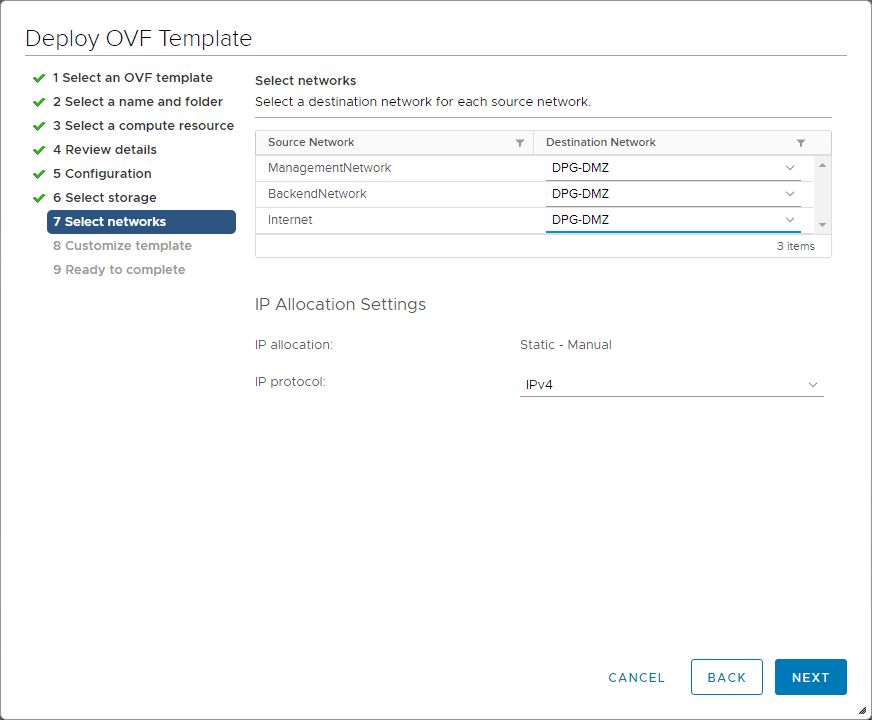
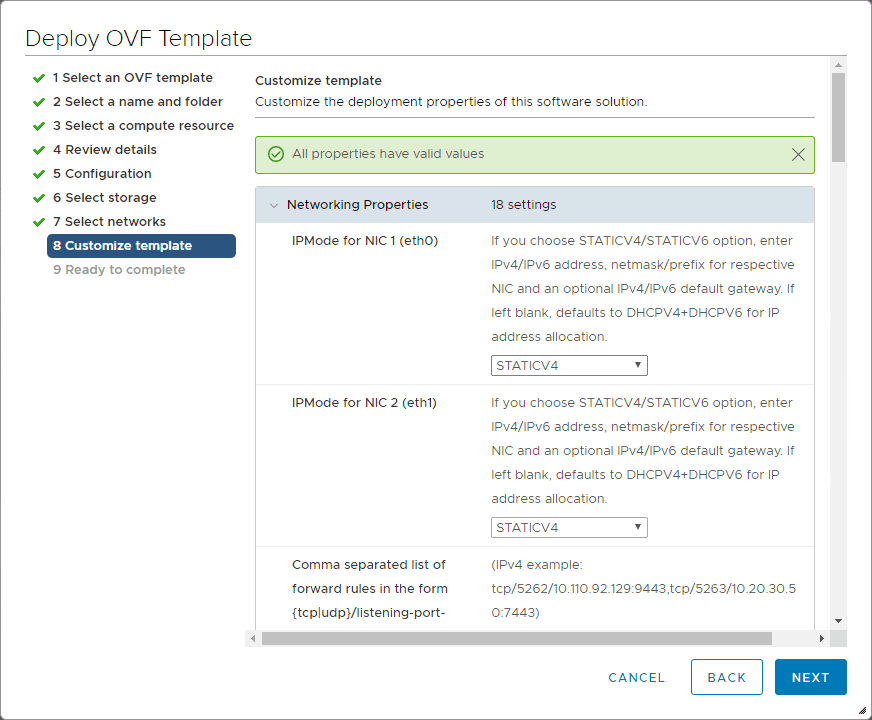
This is the screen you want to pay attention to as here is where you will configure your network address settings for your network configurations which may be more than one adapter depending on what you chose as well as passwords.
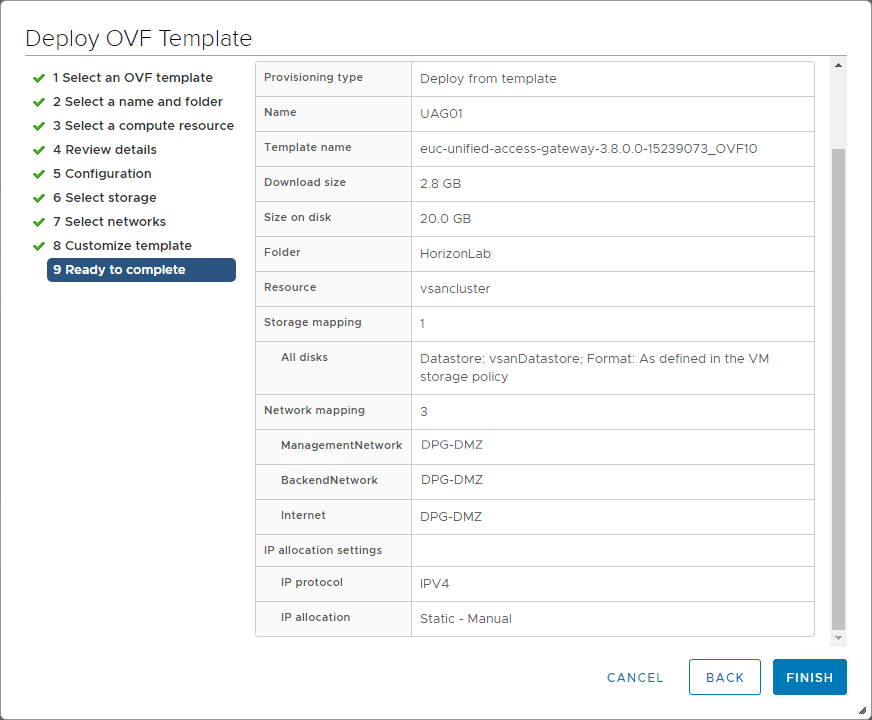
Finish out the deployment of the appliance.
Configuring VMware Unified Access Gateway 3.8
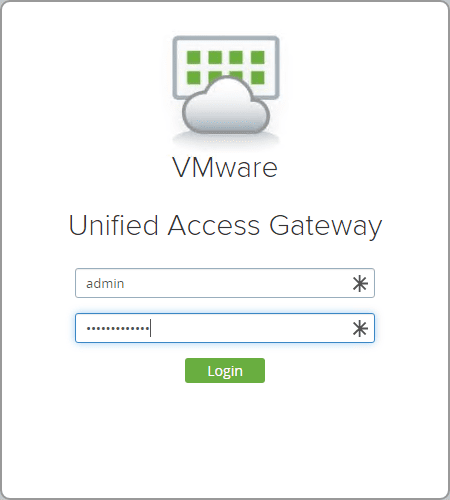
After deploying the UAG 3.8 OVA appliance, power on the VM and then login using the credentials you setup during the customization step of the UAG appliance.
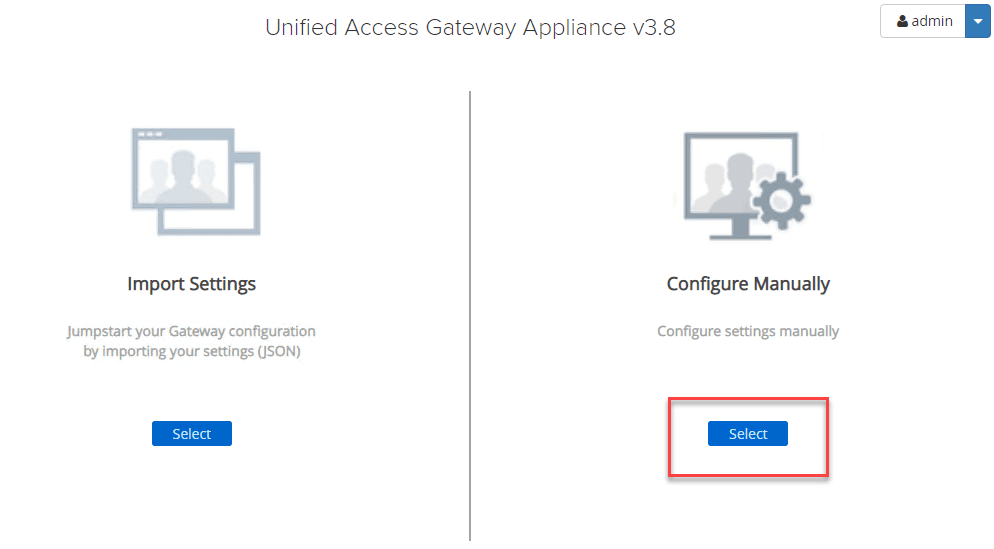
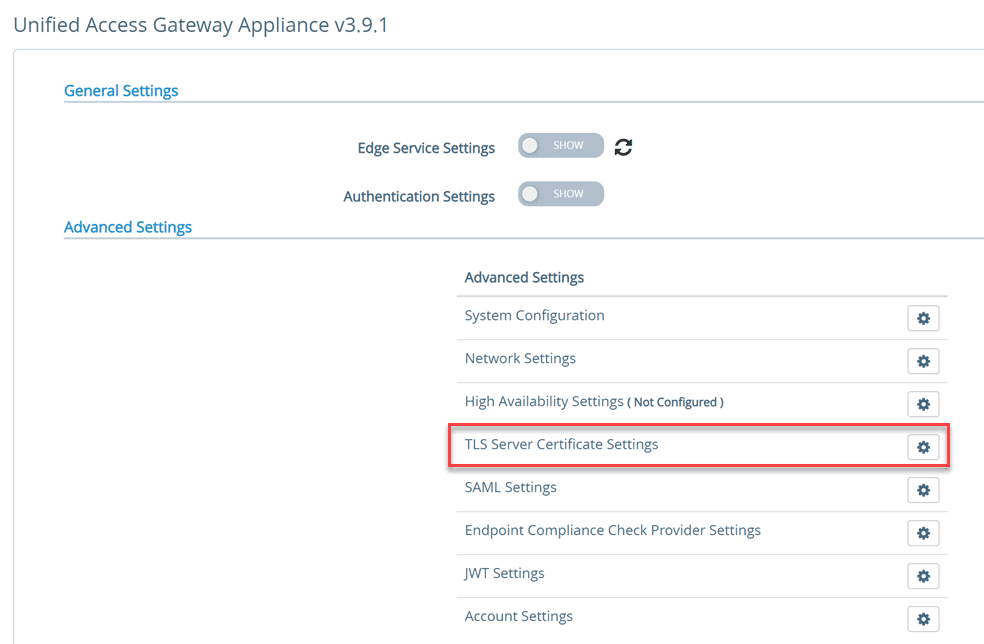
Connect to the web interface of the UAG appliance on port 9443. You will be prompted on how you want to configure the settings for the UAG appliance. Here I am choosing to configure these manually. If you have exported the settings from another UAG appliance, you can import the settings into another UAG using the import settings option.
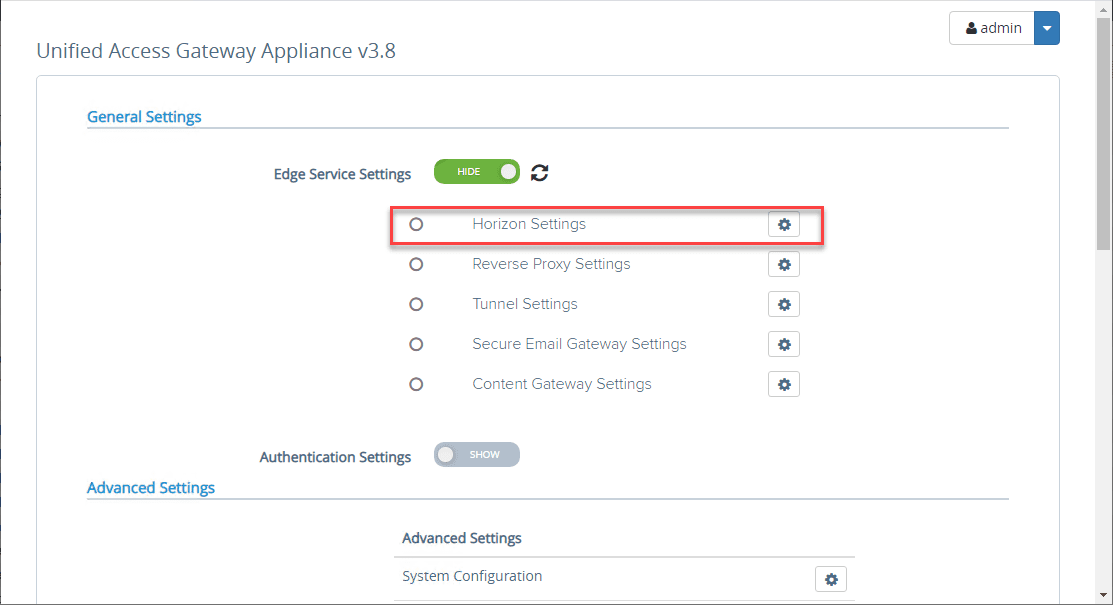
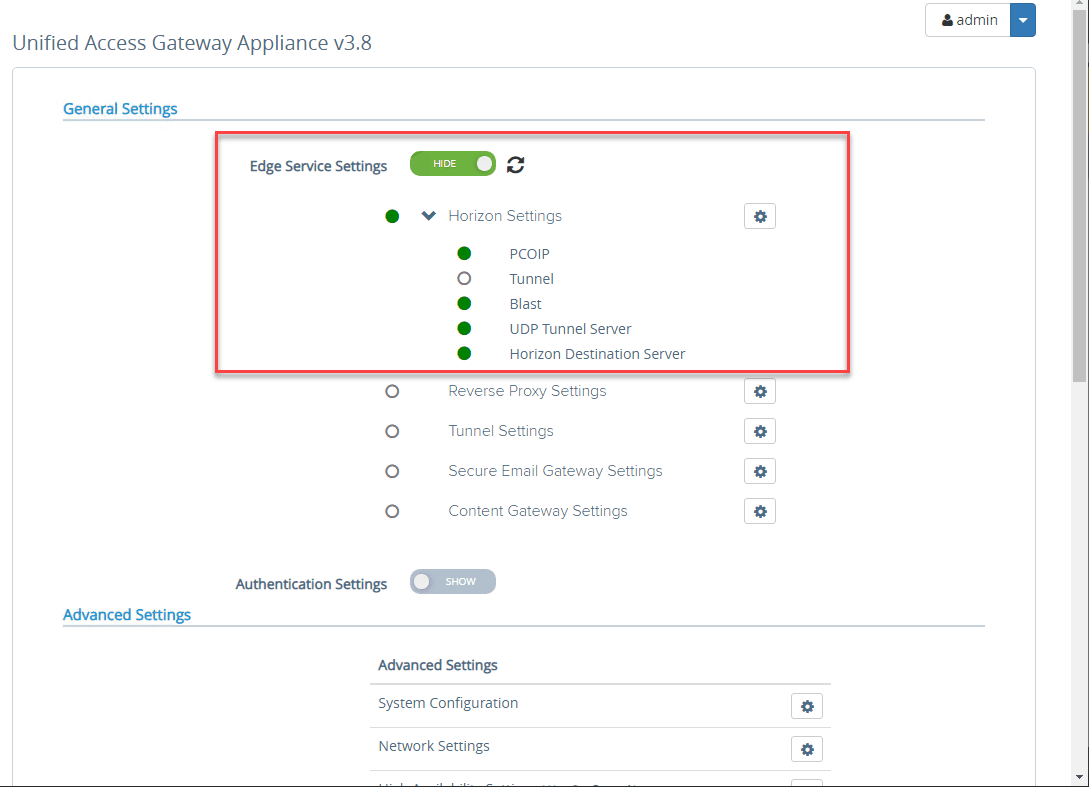
To connect to the Horizon Connection Server internally, you need to configure the General Settings > Edge Service Settings. Toggle the switch.
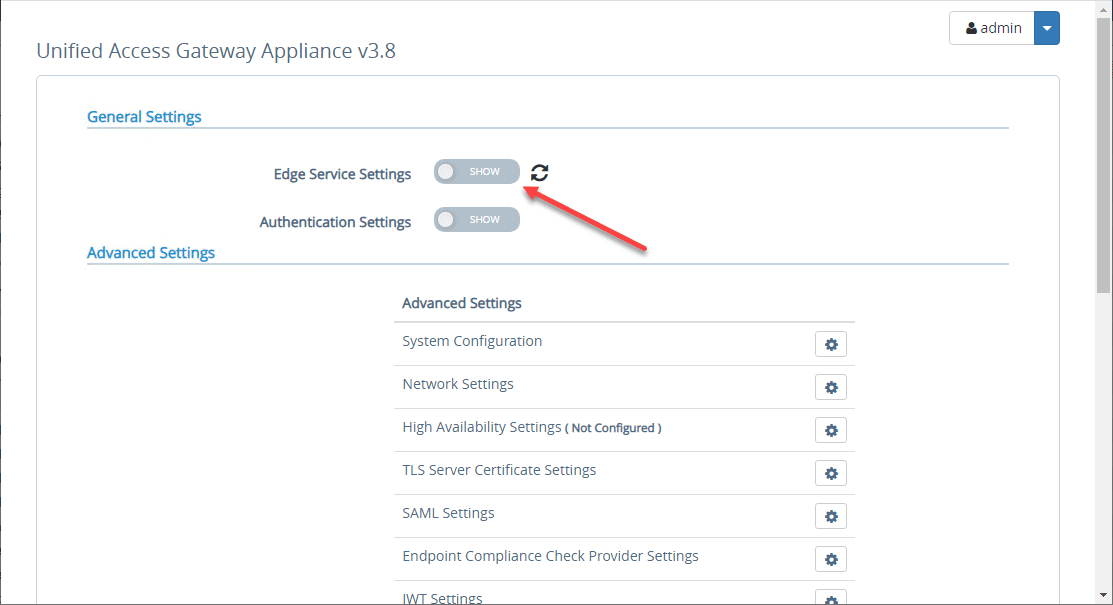
Click the settings “cog” next to Horizon Settings.
Here, you fill in the necessary information to connect to your Horizon Connection Server. The interface here does a good job when you click the information bubble next to each field of explaining the correct format, etc.
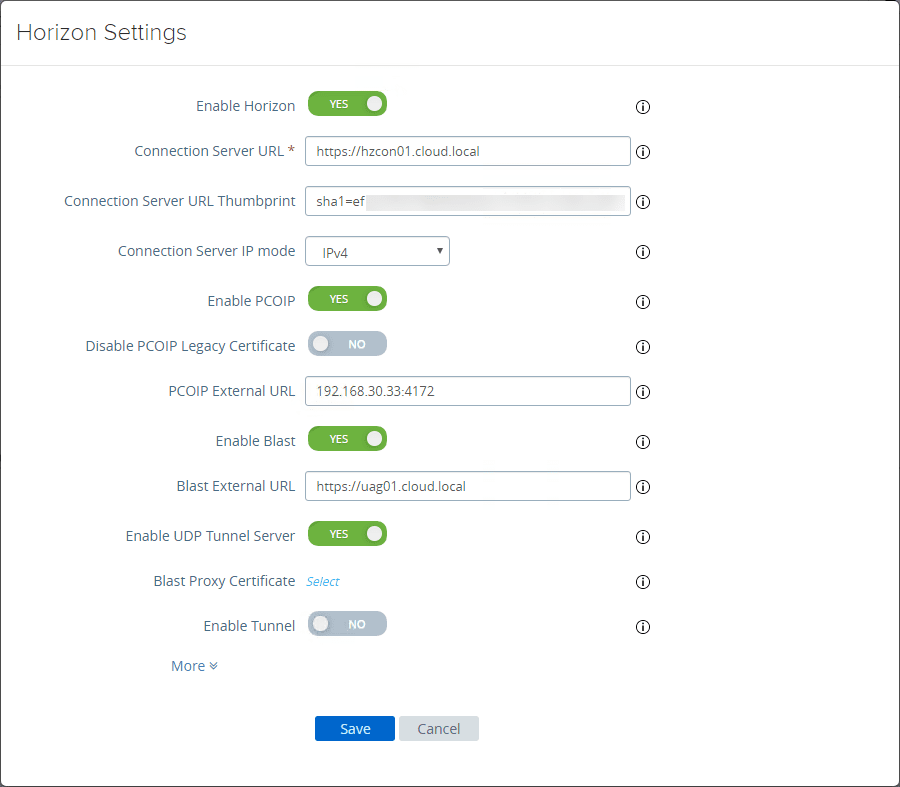
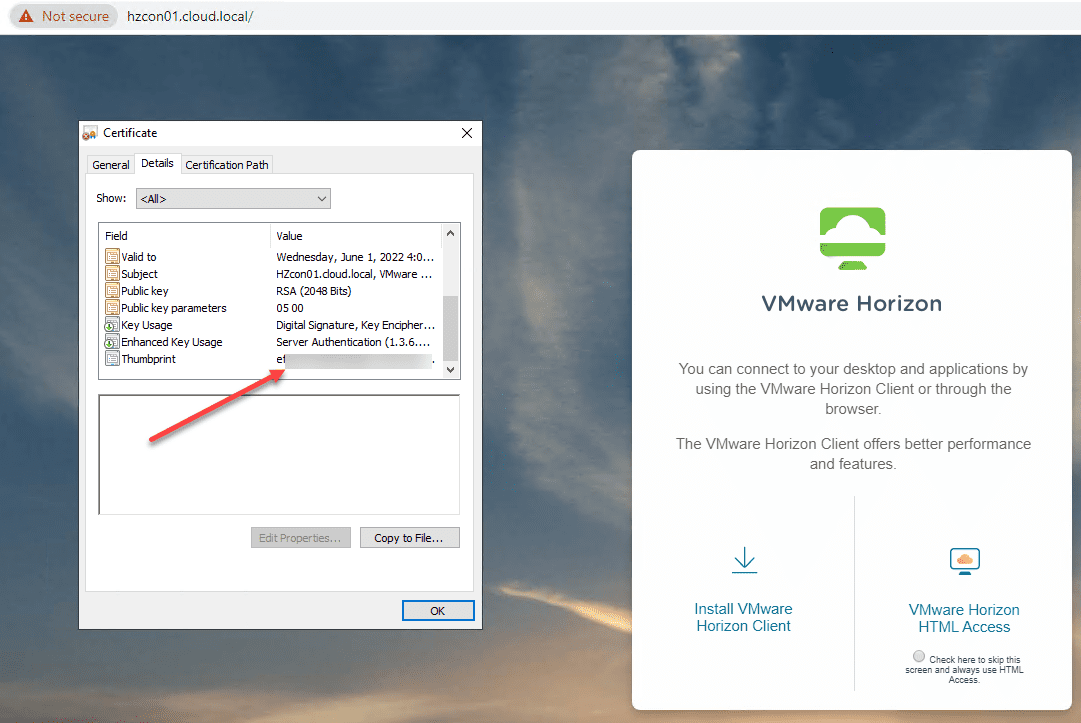
To get the certificate thumbprint of your Horizon Connection Server in the screenshot above, you need to browse out to the web interface of your Horizon Connection Server, view the certificate, and then look at the properties of the Thumbprint. Copy this value to a notepad document or some other text editor.
You will need to add the following in front of your thumprint:
- sha1=ee xx xx xx…….etc
After entering the information, you can hit the refresh button and you should see green bubbles all the way down. If you don’t start troubleshooting the steps or components that are failing according to the bubble indicators.
Wrapping Up
In this VMware Unified Access Gateway UAG 3.8 Installation and Configuration primer, we have looked at what Unified Access Gateway UAG is, the architecture, protocols, etc. Also, we looked at a basic deployment of the solution along with configuring the connection to the Horizon Connection Server.
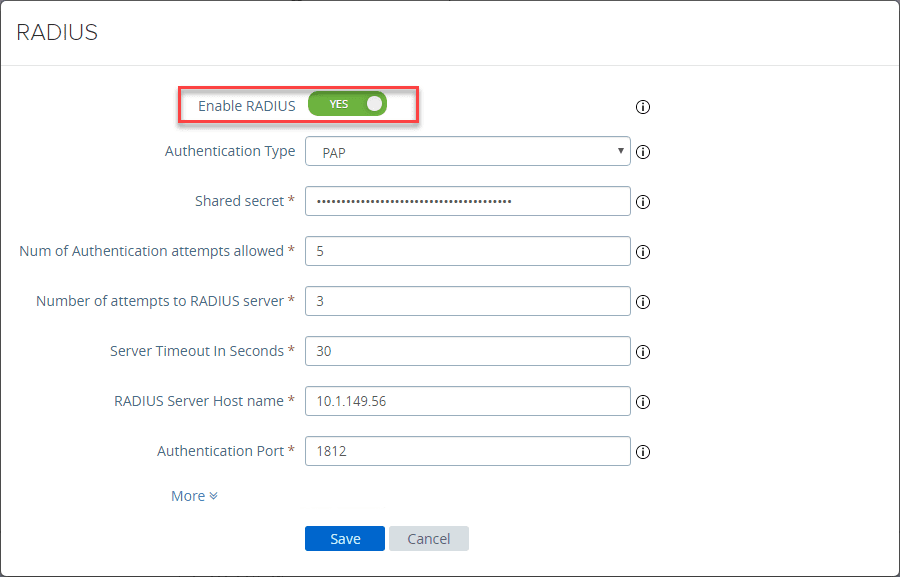
Next, we will look at the authentication protocols and how you can setup various authentication models such as RADIUS server as well as 2FA.