As you migrate your workloads to a Microsoft IaaS environment, you will want to give due attention to your security posture in Microsoft Azure. There are many considerations you will want to make when looking at your Azure VM security and how to protect your workloads from potential attack or data breach. In this post, we will take a look at Azure VM security best practices to look at a few basic best practices you will want to make sure you are doing with your Azure IaaS VMs.
Azure VM Security Best Practices
What are the basic Azure VM best practices that you will want to make sure you are doing to make VMs in Azure IaaS more secure? We will take a look at the following:
- Secure Identity Authentication & Authorization
- Protect Against Malware and Attacks
- Update Management
- Virtual Machine Security Posture
- Control Networking
Secure Identity Authentication & Authorization
There are a few basic things to give attention to with secure identity authentication & authorization in the realm of Azure VM security.
This includes:
- Enabling Multi-factor Authentication (MFA)
- Ensure least privilege access using role-based access control (RBAC)
- Use Privileged Identity Management (PIM)
Multi-Factor Authentication (MFA)
Using MFA is one of the most basic ways to secure your Azure VMs from attack. MFA will help to block somewhere in the neighborhood of 99% of attacks. In line with best practices, ALL accounts should be using MFA for access.
Ensure Least Privilege Access Using Role-Based Access Control (RBAC)
You want to always enforce least privilege if at all possible in Azure IaaS. This ensures that if an account is compromised, attackers will have the least amount of rights possible with the compromised account. It also helps to ensure that admin accounts don’t have permanent access and an approval process is enforced for user permissions.
Use the Azure Security Secure Score
The Azure Security Secure Score allows you to have an automatically generated analysis of the overall security score of your Azure environment. Additionally, Azure Security Center breaks down what makes up the overall score so that you can remediate the security risks presented in each area of your Azure environment.

Audit External Account Access
Be sure to audit and examine external account access. Azure Security Center provides automatic examination of your external account access in Azure which allows you to have visibility on external accounts that were granted access and that may still have access long after the need has expired.
Protect Against Malware and Attacks
Protecting Azure VM security against malware and attacks is an extremely important task that you want to give attention to. This includes the following:
- Using Atimalware and monitoring with Azure Security Center
- Use Azure Security Center Standard for Adaptive Application Control
Use Antimalware and Monitor with Azure Security Center
Using Antimalware you are able to cover the bases with many of the basic attacks that your Azure VMs may experience like viruses and spyware. This is still a basic area of concern that exists in the wild.
Use ASC Standard for Adaptive Application Control
This is the next level of Azure VM security that helps to prevent malware. This basically involves “whitelisting”. The whole principle behind whitelisting is you get a baseline of what your good applications look like and allow these applications to run with the adaptive application control found in Azure Security Center. This can be done in what ASC calls audit mode where blocks are not actually enforced. However, this still allows the adapting control to learn the environment.
Once you have the baseline tweaked, you can turn on the enforce mode which allows ASC to start blocking applications that are outside of the whitelist.
You can also whitelist applications based on certificate, path rules, and hash rules to enable an application to run.
Update Management
Applying updates to your systems is a key best practice with Azure VM security. Updates are often very difficult to keep up with manually. Microsoft Azure Update Management can automate the process of applying patches in your environment.
A really nice point to make with Azure Update Management is that it not only can patch Windows systems, but also Linux. Two more key points to make with Update Management are:
- Use the latest operating system images
- Plan for BC/DR
Use the Latest Operating System Images
Using the latest OS images helps to ensure new VMs provisioned are as current as possible with patches and underlying security enhancements.
Plan for BC/DR
Another consideration to make is if your VM is compromised with some type of malware, how are you going to quickly recover? Are you going to restore from backup? Or, are you going to deploy a new resource and patch it up as quickly as possible? This is an important consideration to make with Azure VM security.
VM Security Posture
Aside from the items already mentioned with Azure VM security, there are a few other details you want to consider related to your Azure IaaS VM security posture. These include:
- Review missing OS updates
- Use disk encryption
- Assess and remediate vulnerabilities
- Detect Threats with Azure Security Center and MDATP for servers
- Use Azure Vulnerability Assessment
Review Missing OS Updates
We have already touched on this under the Update Management section, however, your Azure VM security posture will be greatly determined by missing OS updates. Review these often, use Update Management, make use of desired-state configuration, and deploy custom VM images with policy built in.
Use Disk Encryption
By using disk encryption you are protecting your data at rest. Azure disk encryption makes use of BitLocker to protect your data. Be sure to take advantage of this feature.
Assess and Remediate Vulnerabilities
Be sure to assess not just the VMs themselves, but the applications they run. Vulnerable applications provide a target for hackers.
Detect Threats with ASC Standard and MDATP for Servers
Azure Security Center is a great resource along with MDATP for servers for Azure VM security.
Use Azure Vulnerability Assessment
Microsoft announced Azure Vulnerability Assessment at Ignite 2019 which makes use of a Qualys agent running in your Azure VMs. Azure Security Center scrapes the logs of the Qualys cloud environment and presents this information to you in your Azure portal.
Control Networking
Control Networking for Azure VM security so that you can restrict who has access via the network to your Azure IaaS environment. There are three points to consider with this:
- Review VM traffic patterns and restrict with multi-dimensional segmentation
- Limit Access to Management Ports
- Use Adaptive Network Hardening
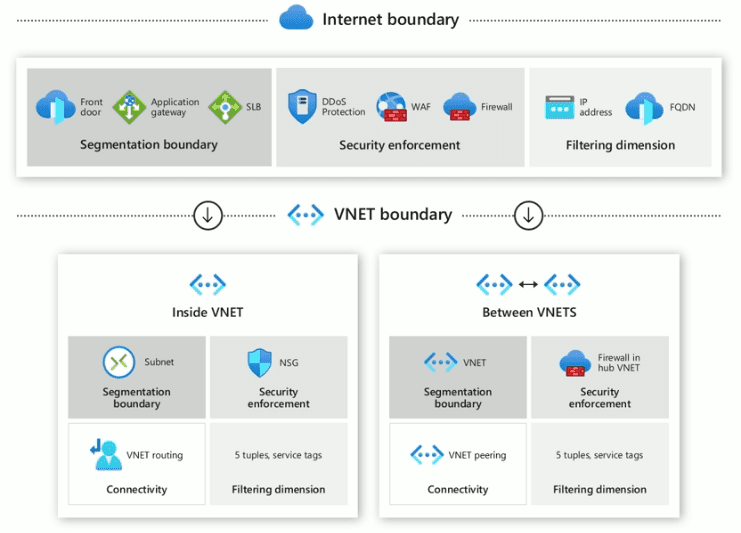
Review VM traffic patterns and restrict with multi-dimensional segmentation
Knowing what resources your VMs need to hit and what traffic should be allowed is key. Implement segmentation to prevent unauthorized network access.
Limit Access to Management Ports
Use “Just In Time” (JIT) management policies integrated with Azure Firewall and NSG or use Azure Bastion.
Use Adaptive Network Hardening
Azure makes use of ML to make your job of securing the network much easier.
Wrapping Up
Microsoft has introduced some really great tools to help with ensuring Azure VM Security Best Practices. With the Azure Security Center, you have a great tool that automatically watches your environment for you and points out potential security issues that need to be resolved. This goes a long way in helping to secure your Azure IaaS environment.
Be sure to check out the official Ignite 2019 session by Nicholas DiCola found here: https://ignite.microsoft.com/en-US/home
Google is updating how articles are shown. Don’t miss our leading home lab and tech content, written by humans, by setting Virtualization Howto as a preferred source.