Let’s face it, keeping your VMs and environments updated is a necessary evil that we all realize we need to do for security, stability, and enhancements. Especially from a security perspective, updates are essential. We often hear focus on Windows systems and keeping them updated. However, this is equally important for Linux-based systems also. Automation is key when it comes to keeping systems updated. In this post, let’s take a look at how to use Ansible AWX to automate Linux Updates and patches and see how this can be easily accomplished.
Background to Using Ansible AWX
I am a big fan of Ansible and using it in the home lab quite often to keep configuring drift in check as well as provisioning and performing other mundane tasks that are labor intensive to accomplish manually. After having played around with Ansible Tower in the lab some time ago in the “10 node trim”, I decided to get Ansible AWX up and running to have a totally free version of the Ansible Tower commercial variant to play around with and not be bound by the 10 node limit for free.
In case you are not aware, Ansible AWX is the open source project that Ansible Tower was born from. They look basically identical when comparing the interfaces. After spinning up Ansible AWX, I had a task in mind that I wanted to knock out quickly. After having amassed a large quantity of Ubuntu Linux servers in the home lab, I was in need of getting those updated and keeping them updated on a schedule. This is a perfect first task to get scheduled in the Ansible AWX install.
This is not a “how to install Ansible AWX” post as there are plenty of those already on the net. However, I found a really good post here describing how to get Ansible AWX up and running with NGINX acting as a reverse proxy.
In this post, we will pick up after the point of getting Ansible AWX and see how we can create a simple Inventory, group, and task to automate updating a group of Linux servers.
Use Ansible AWX to Automate Linux Updates and Patches
Ok, so let’s get down to the few simple configuration pieces in Ansible AWX to Automate Linux updates and patches. First, below is a capture of the Ansible AWX interface dashboard. As you can see it is much more pleasing to look at than the Ansible command line. It looks basically just like Ansible Tower, which isn’t surprising.
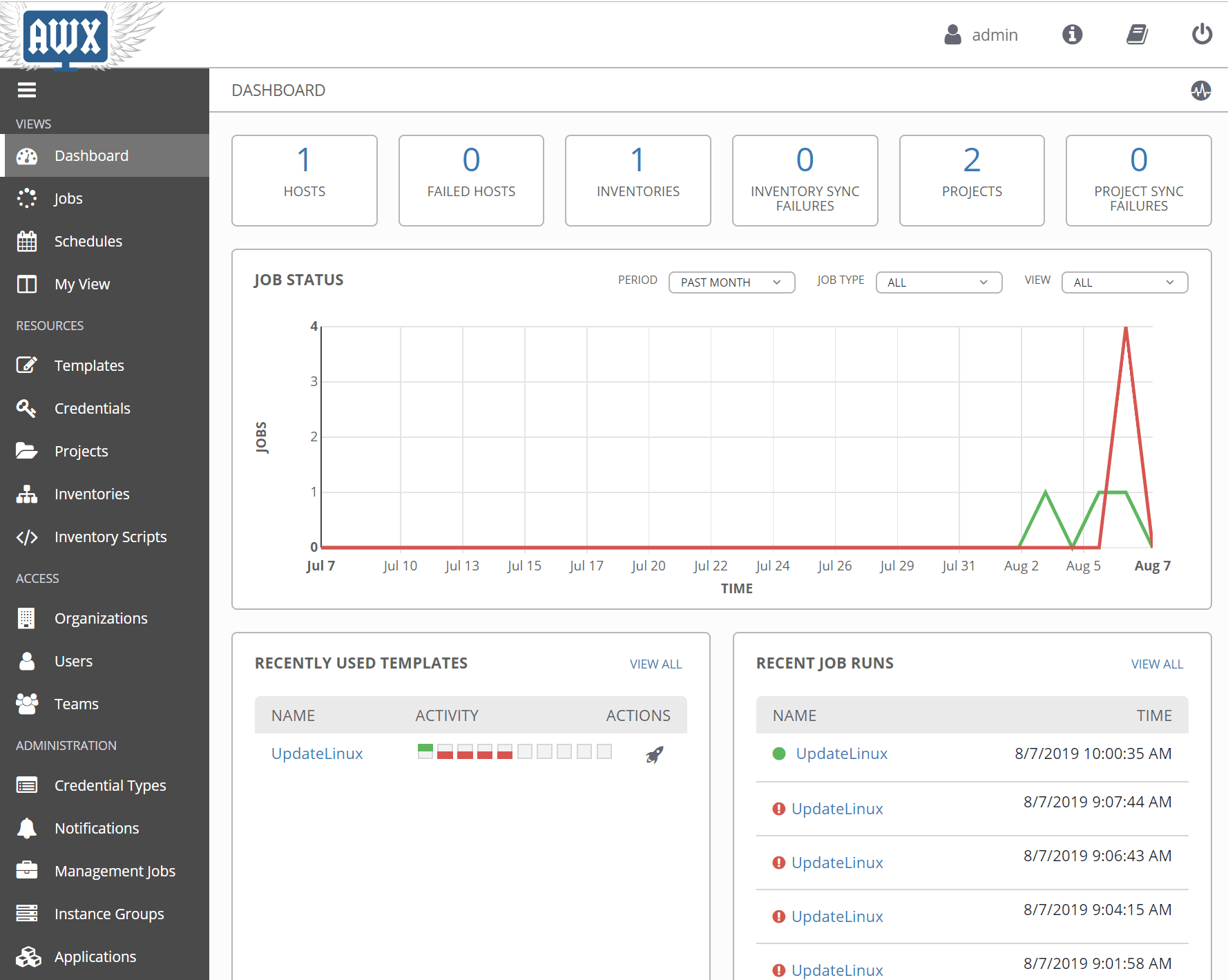
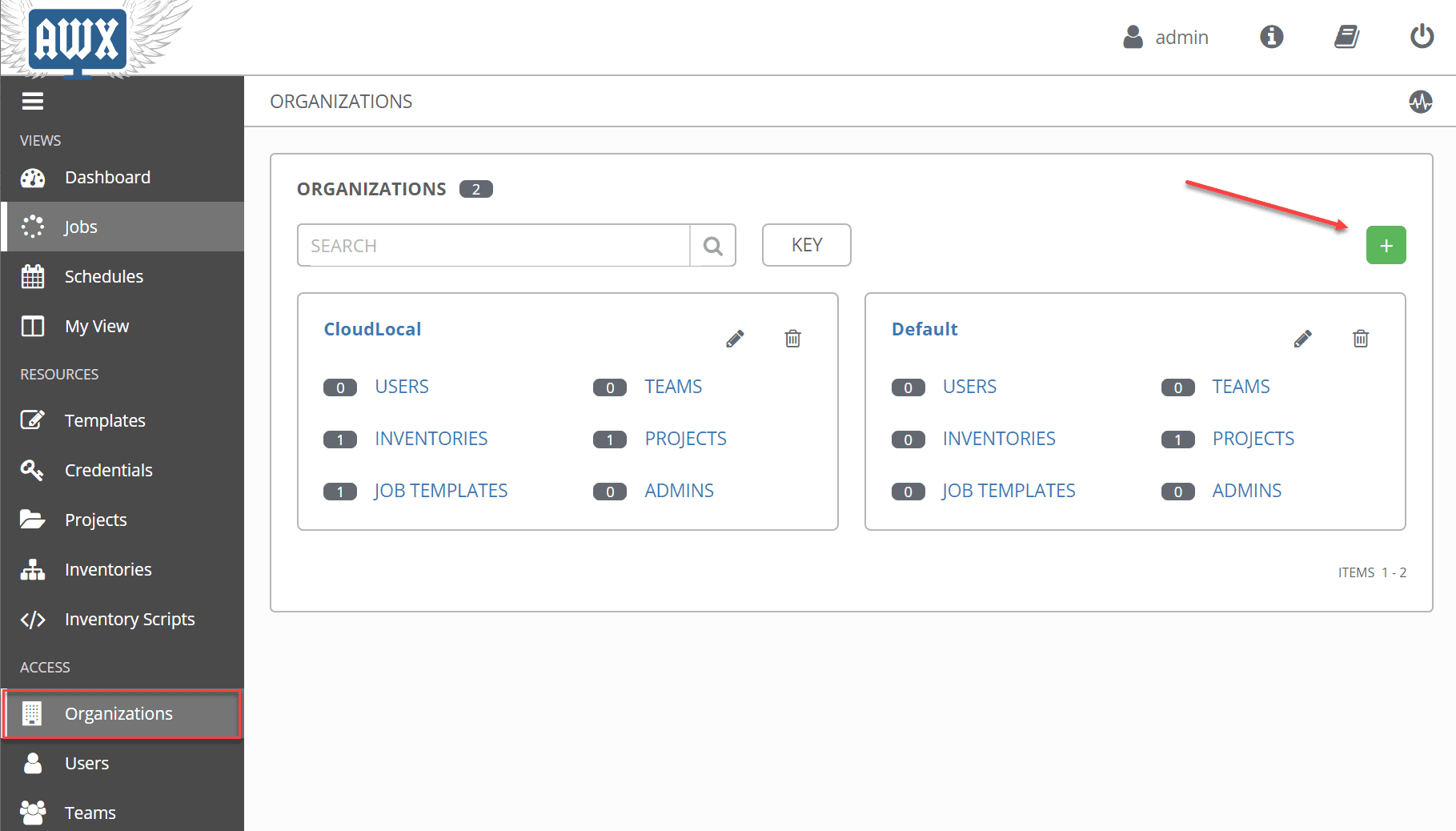
The first few steps is simply getting the “pieces” in place that will be required when creating a new Job template in Ansible AWX. First things first, let’s create a new organization. What is an organization in Ansible Tower/AWX?
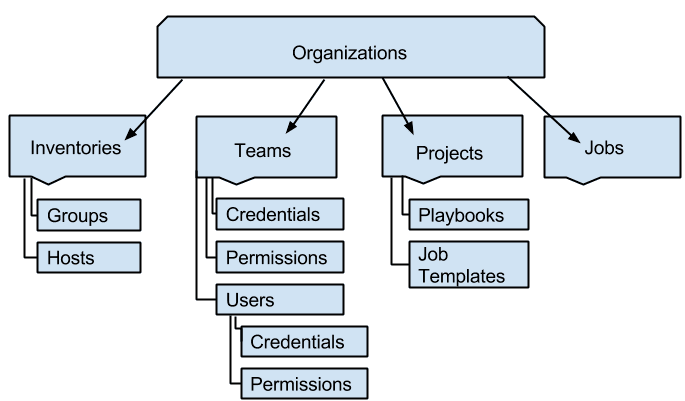
It is a logical collection of Users, Teams, Projects, and Inventories, and is the highest level in the Tower object hierarchy as shown in the diagram.
Navigate to the Organizations node under Access and click the green plus sign to create a new organization.
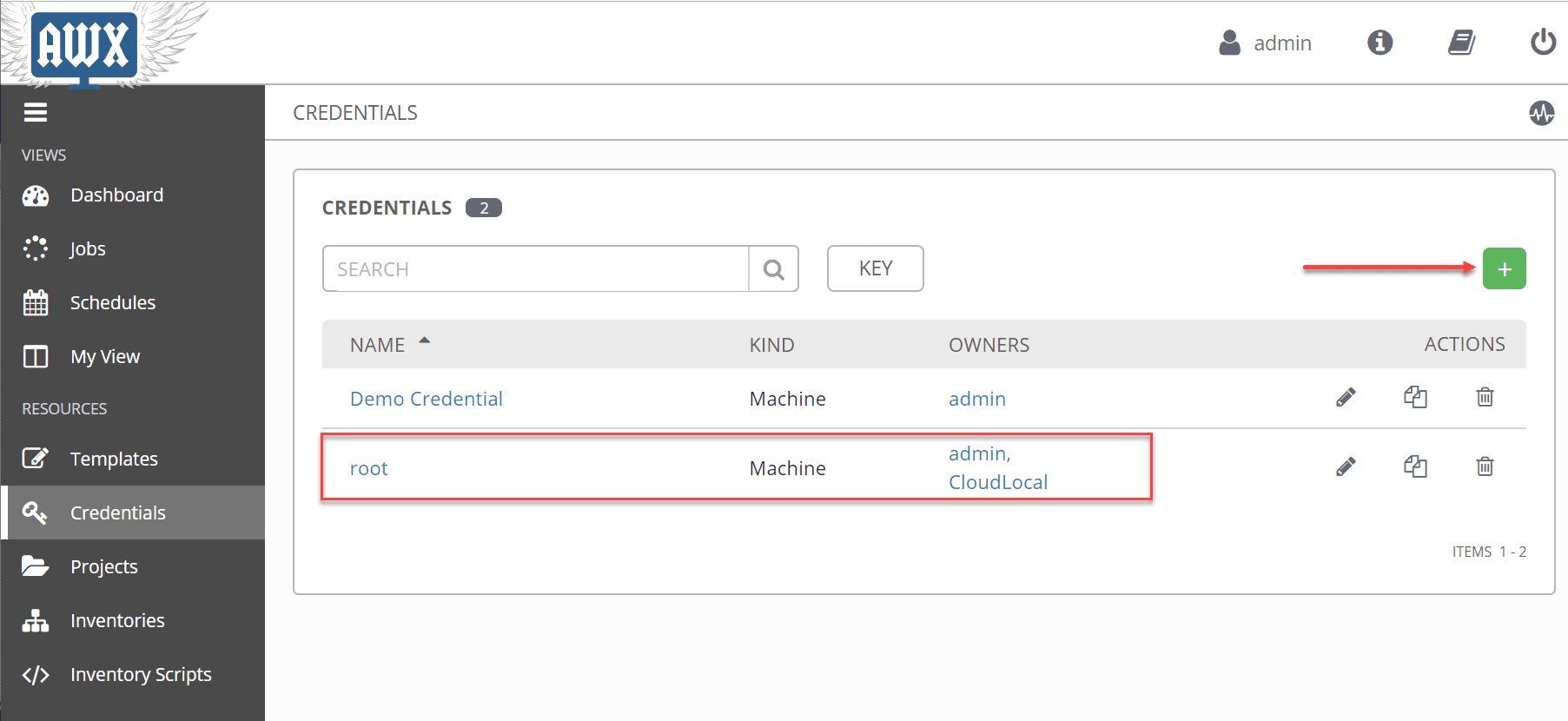
To connect to our Linux servers and run our job template, you will need to have credentials for doing so. Credentials are also utilized by Tower/AWX for authentication when launching jobs against machines, synchronizing with inventory sources, and importing project content from a version control system. Click the Credentials node underneath the Resources node and then click the green plus sign to add a new credential to Ansible AWX. As you can see, I have added a new machine credential for root.
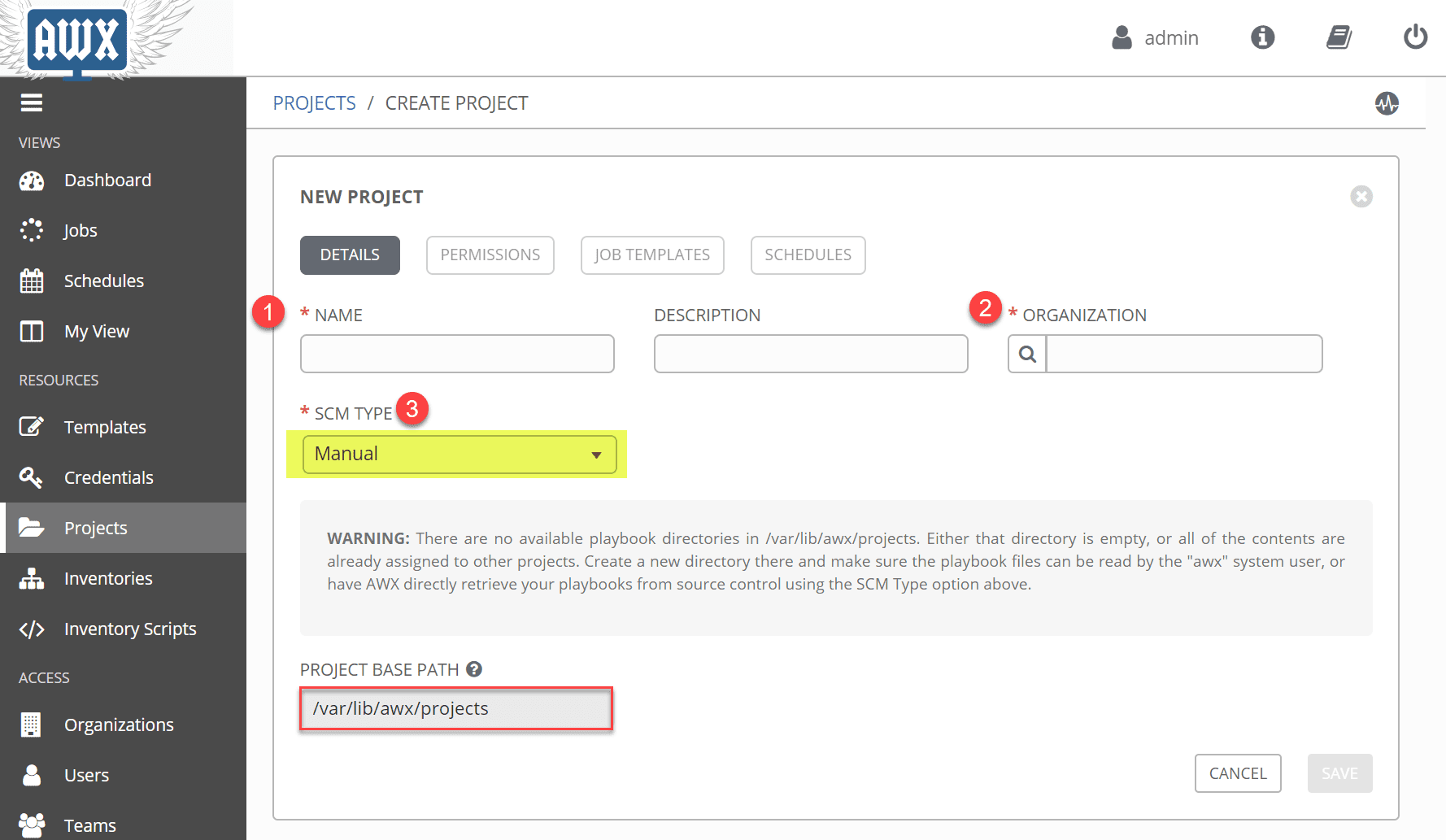
Next, we create a Project. What is a project in Tower/AWX? A Project is a logical collection of Ansible playbooks, represented in Tower. Click the Project node underneath Resources. Also, note how AWX gives you the Project Base Path. You need to make sure you have a folder underneath the base path to match your project name as this doesn’t get created automatically.
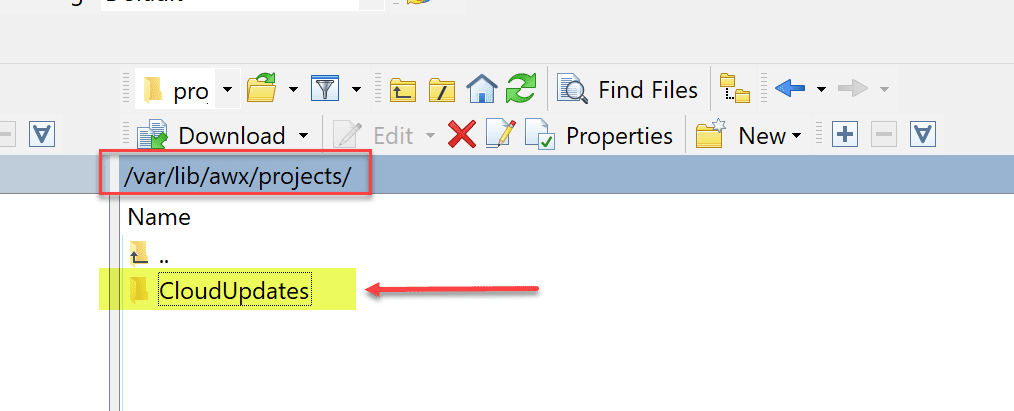
I navigated to this folder on my Ansible AWX server and created the folder for the project.
Underneath the CloudUpdates folder, I created a new YAML file called CloudUpdates.yml that contained the following:
---
- name: Upgrade all packages to the latest version
hosts: all
tasks:
- name: Upgrade all packages to the latest version
apt:
update_cache: yes
upgrade: yes
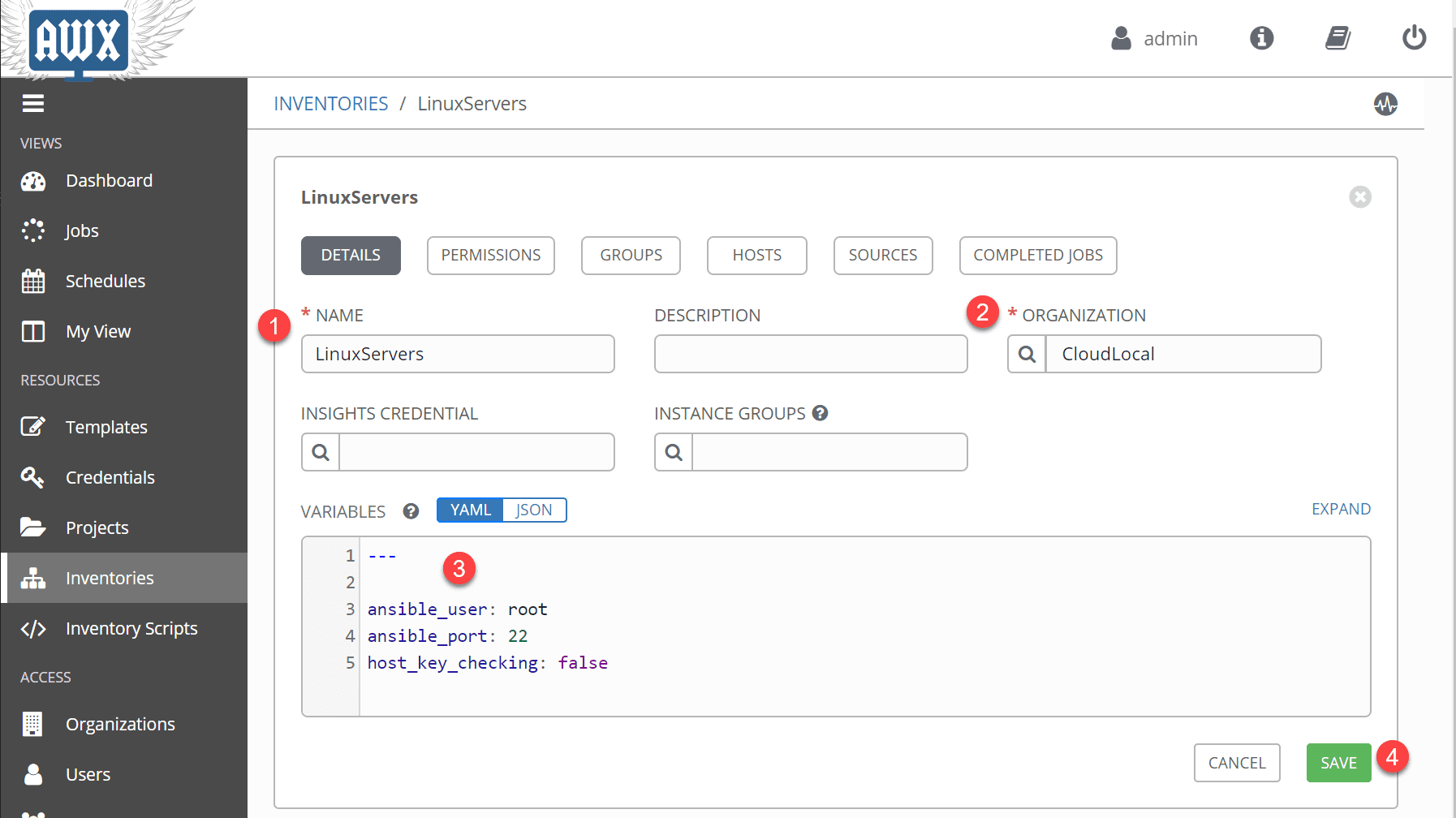
Now, moving on to the Inventories. An inventory is a collection of hosts against which jobs may be launched. Inventories are divided into groups and these groups contain the actual hosts. Groups may be sourced manually, by entering host names into Tower/AWX, or from one of Ansible Tower’s supported cloud providers. Note in the YAML field, I have provided the connection information for how Ansible will connect to the hosts.
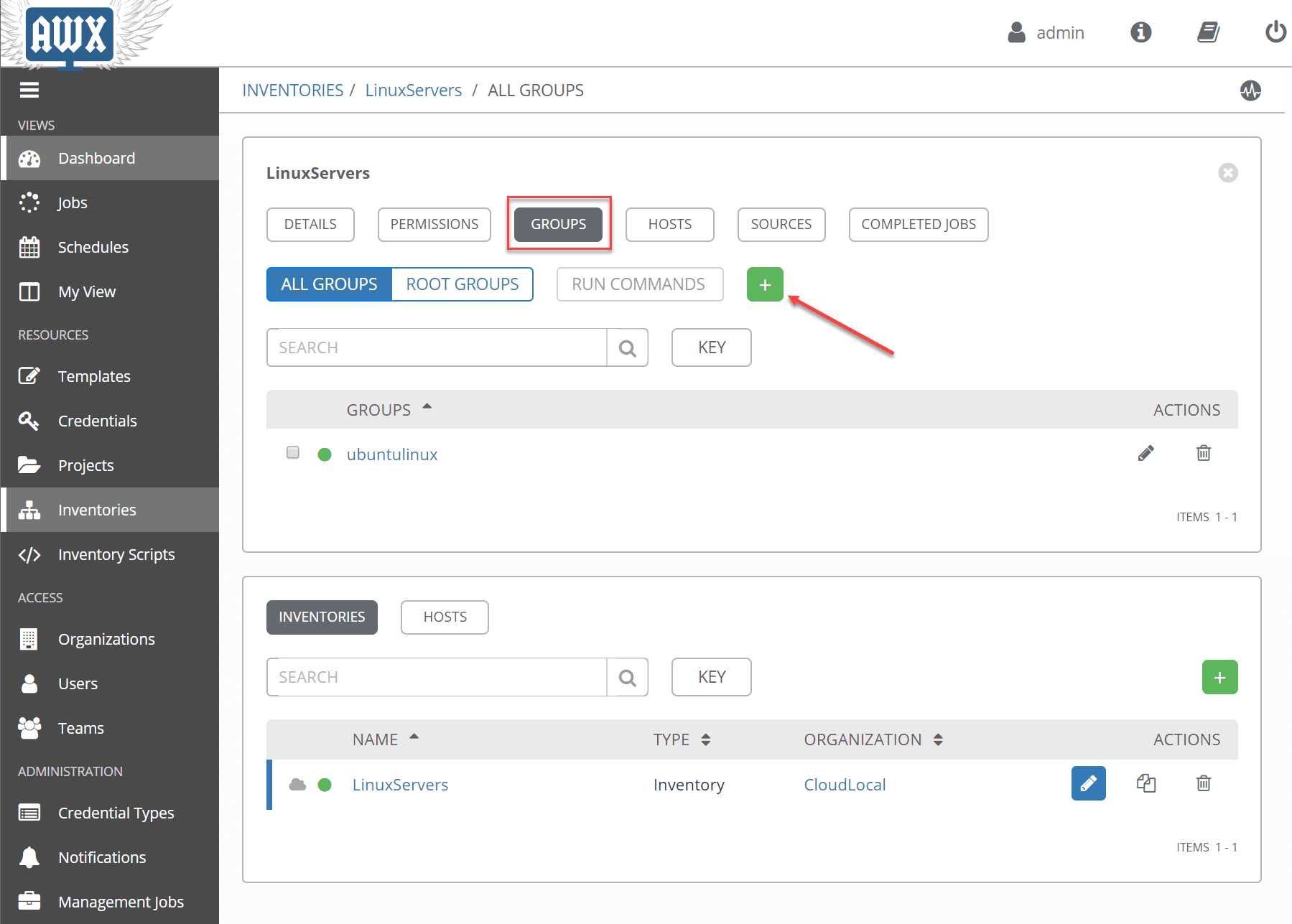
As mentioned, we need to create groups as part of the inventory configuration. These are what actually contain the hosts we want to interact with. Click the Groups button and the green plus sign to add a new group.
Adding the new group in the Ansible AWX inventory.
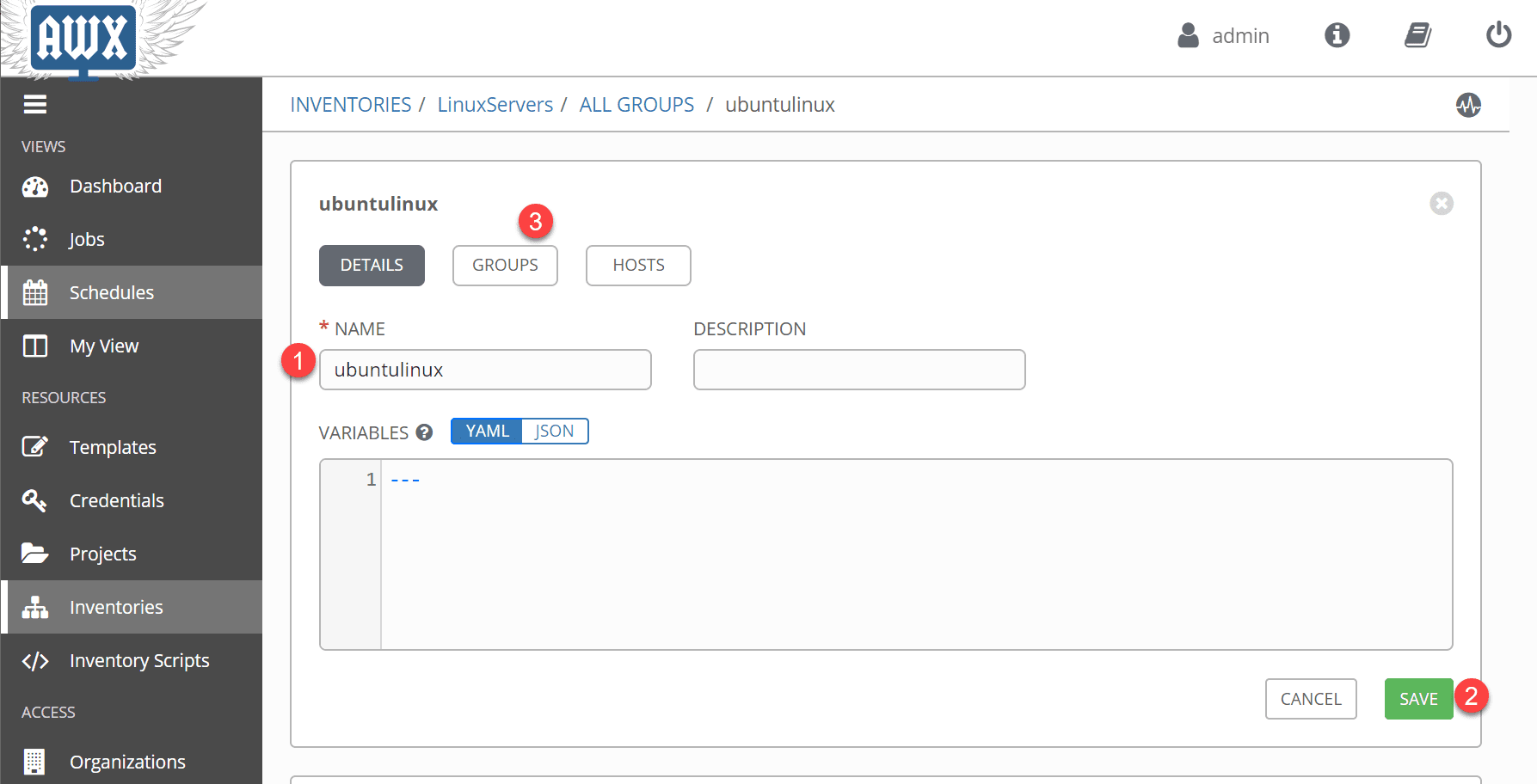
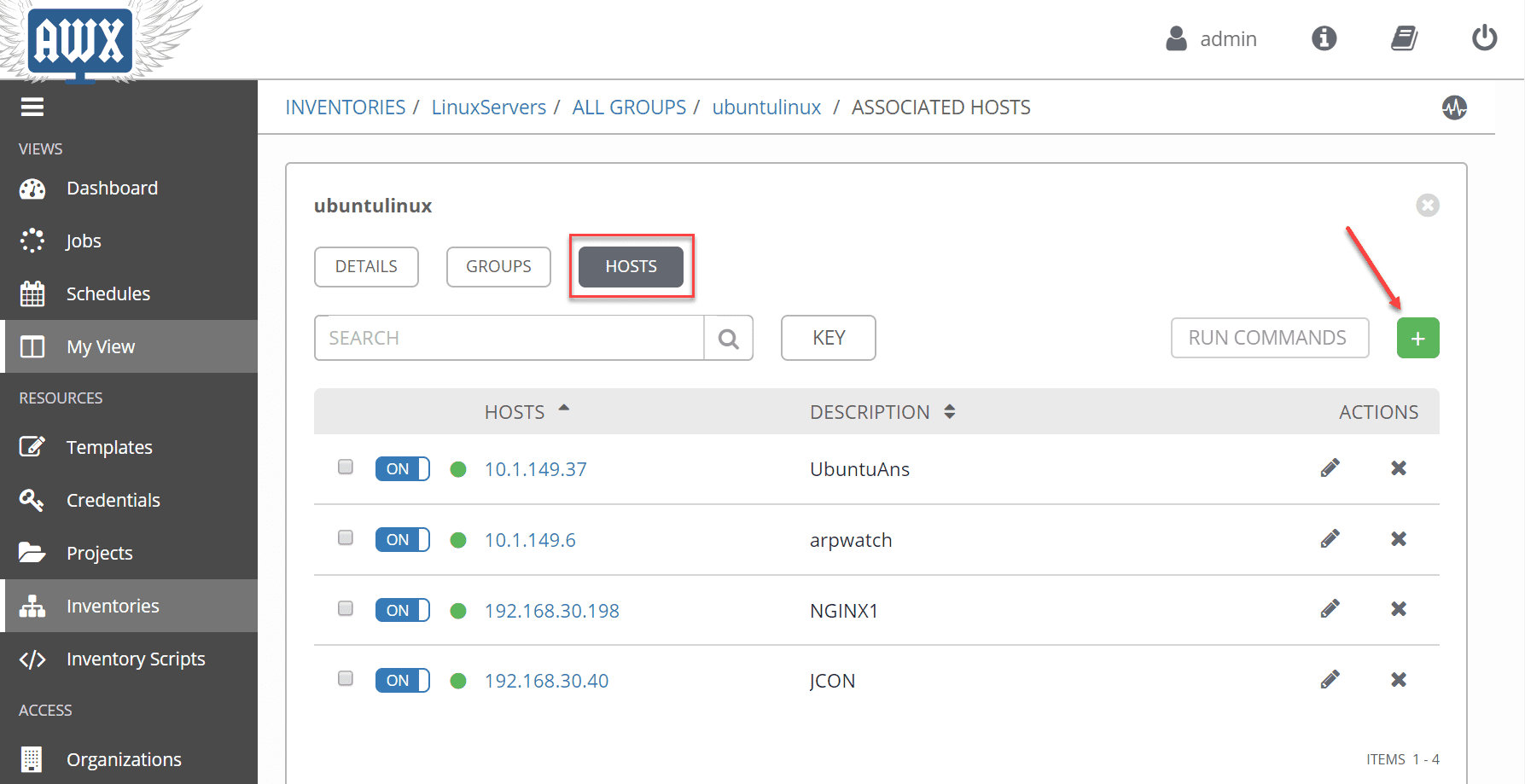
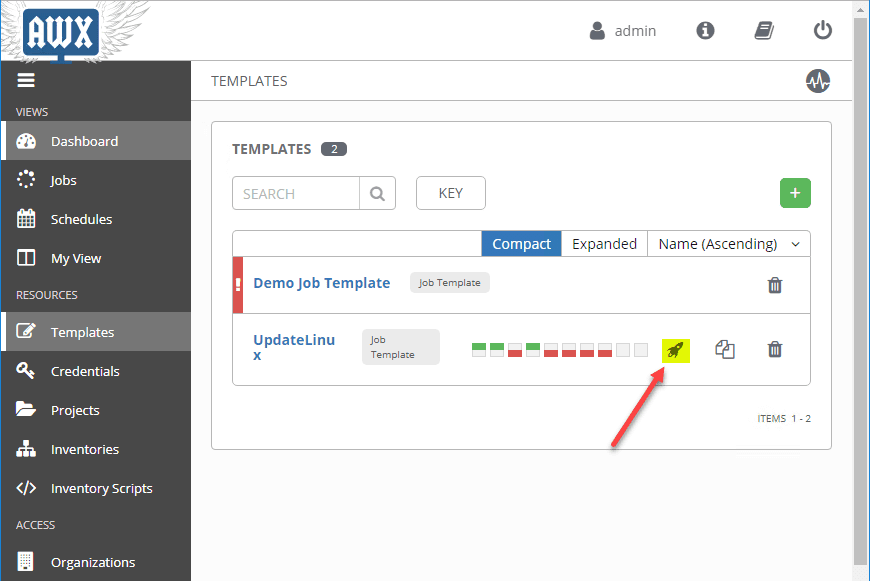
Now, underneath the group, click the Hosts button and using the green plus sign, add the hosts you want to connect to. In my case, since I want to Use Ansible AWX to Automate Linux Updates and Patches, I am adding the Linux hosts here.
Creating the Ansible AWX Job Template to Update and Patch Linux Servers
Once all of the above is completed, we have the minimum in place to actually create a new job template and begin interacting with our servers.
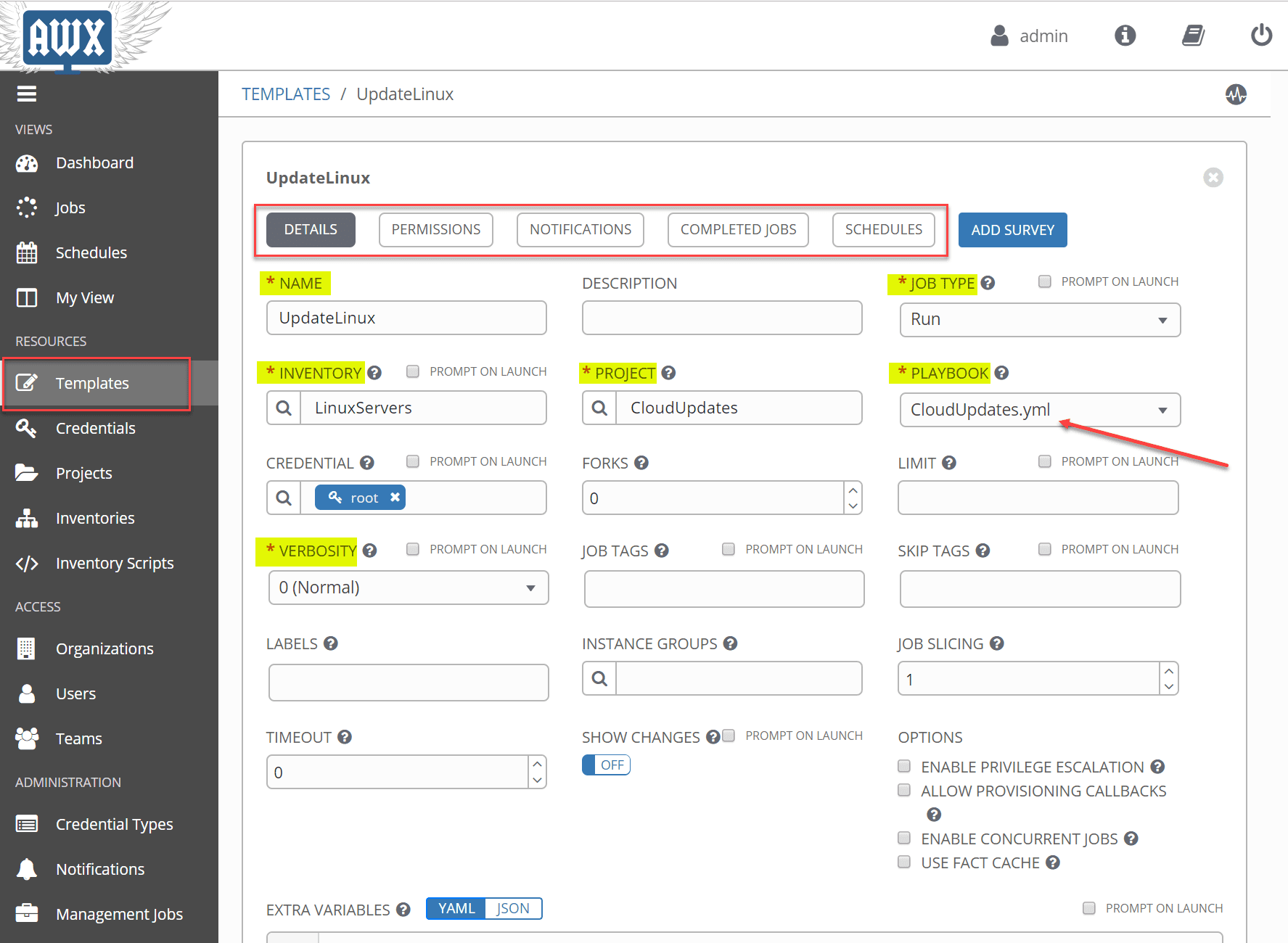
A job template is a definition and set of parameters for running an Ansible job. Job templates are useful to execute the same job many times. While the REST API allows executing jobs directly, Tower requires first creating a job template.
I have highlighted the required fields on the job template screen. After you choose the Project, you should have the Playbook available which is the YAML file underneath your project folder you created.
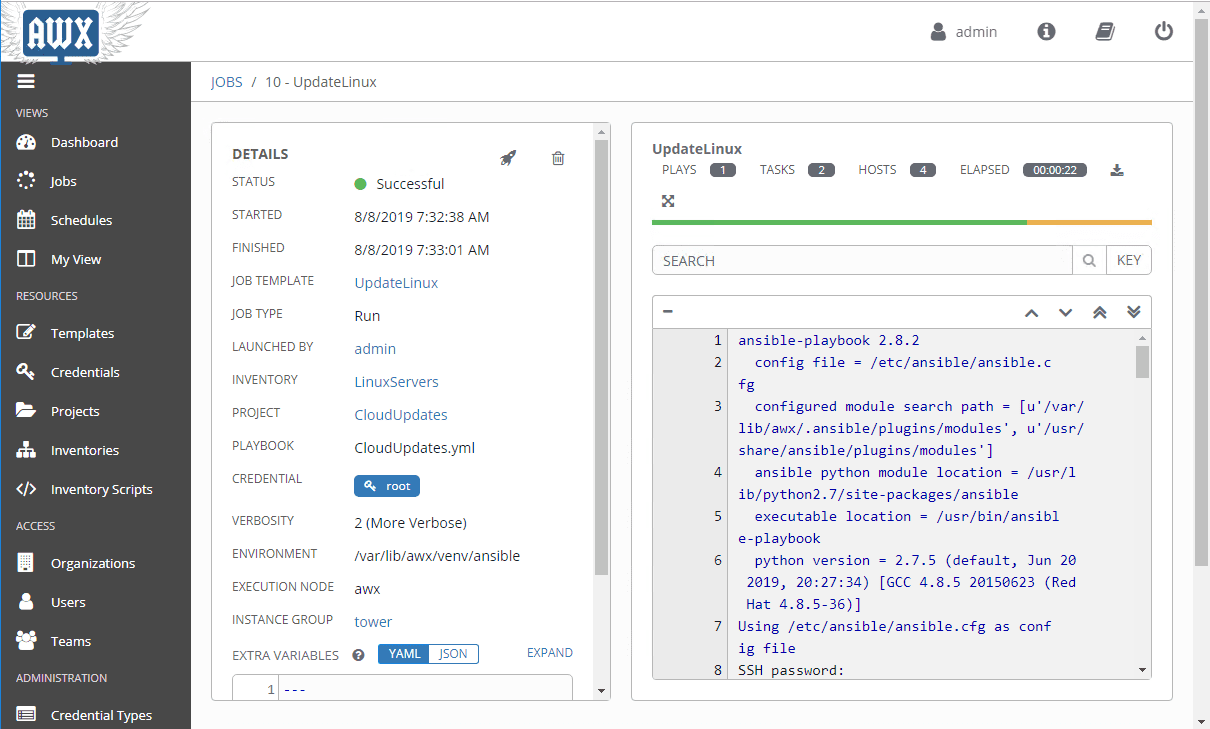
After saving out the new job to update and patch Linux servers with Ansible, we are ready to run the job. For the purposes of this post, we are simply running the job ad-hoc, manually. However, you can also schedule them as you would most likely want to do.
Below, you see the output of running the job along with the status bar above the output screen. The output is normal Ansible output as you would see if running this from the command line.
Wrapping Up
The ability to Use Ansible AWX to Automate Linux Updates and Patches is an easy demonstration of the power of automation. By creating a simple script and using Ansible, you can keep your Linux servers patched on a schedule without the administrative burden of doing this manually. More Ansible AWX topics to come.
Download Ansible AWX:
Google is updating how articles are shown. Don’t miss our leading home lab and tech content, written by humans, by setting Virtualization Howto as a preferred source.


Nice article! Can you add and example of you CloudUpdate.yml file? It’s also interesting thing 🙂
Hi @L K , I might be a tad late to the party but here are some templates for patch management you can use together with a full AWX set up on Debian after dynamically fetching all Proxmox-based hosts from your cluster – https://bachelor-tech.com/detailed-guides/deploy-ansible-awx-to-automate-os-patching/7-useful-patch-management-ansible-awx-templates-for-your-hosts/ .