Five Ways to Improve Network Security
Network security is at the heart of designing a good security posture in an enterprise data center. Often, when threat actors are able to move easily in a lateral way across a network, it is due to poorly designed network architecture from a security standpoint. In this post, we will take a look at five ways to improve network security and see how these can increase security across your network in the enterprise data center.
1. Network Segmentation
While network segmentation is not enough in its own right to create a secure network, it is a good start. Having a “flat” monolithic network is not desirable from many fronts, including security. Segmenting your network by using VLANs and different subnets creates a boundary of sorts for broadcast domains as well as lateral movement in the same broadcast domain.
If an attacker compromises a particular network subnet, they at least only see the nodes on a particular subnet and it will take more work on their part to understand the network layout of the additional subnets that may exist. While these are discoverable, segmenting helps to make this more difficult.
When networks are segmented, you also have a logical boundary for applying network firewall rules, policies, etc. This is much more difficult or not possible to do with a flat, single network subnet containing all devices.
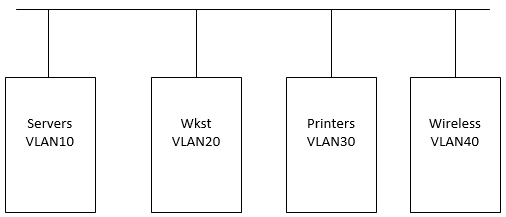
What segments make sense? While this is not an all inclusive list, you most likely will want to create a VLAN for servers, workstations, printers, wireless, and other subnets as needed to align with devices on your network.
It a lot of cases, it makes sense to group similar device types on a subnet, and perform the segmenting of the network based on the device type. However, this is only one method of segmenting and will depend on your business and security needs.
2. Micro-segmentation
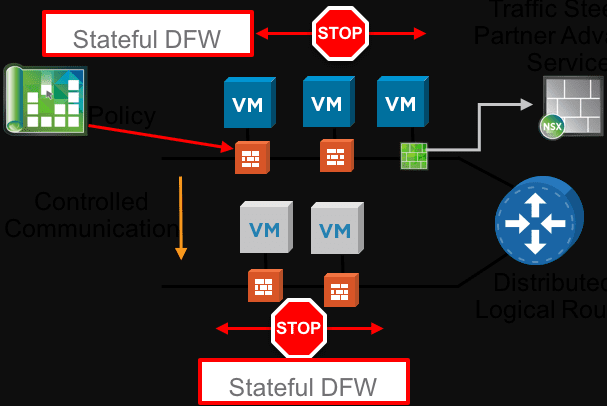
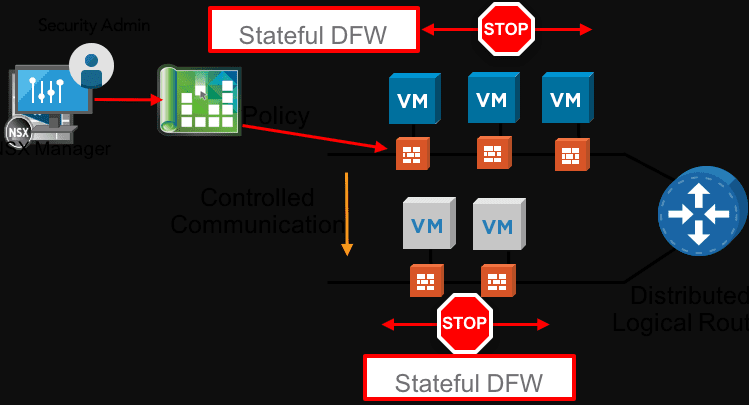
Taking network segmentation much further, micro-segmentation allows you to create a “zero-trust” model of network policy. Back in the old days, everything that was internal to your network was simply “trusted”. Attackers have been able to exploit this mindset.
The new mindset is the zero-trust model where the stance is taken that no device is trusted, even if it is internal to your network. Micro-segmentation restricts network communication, even if on the same Layer 2 VLAN so that devices can only communicate with other network endpoints they are explicitly allowed to communicate with.
Great products that enable this type of network micro-segmentation are VMware’s NSX software-defined networking solution. From a physical device standpoint, there are many vendors out there that can apply network policy at a switch port level, such as Extreme Networks and their policy-based network solution.
With these types of solutions, you can effectively limit a device to see only the handful of network resources they may actually need to see.
3. Identity-based Network Policy
One of the huge pushes with network security has been identity-based networking. In other words, you want to grant rights to network resources based on “who” the user actually is of the network device.
In days gone by, network access was simply based on the device itself – what it was connected to, the VLAN it was on, its IP Address, etc. Today’s security challenges and concerns demand more scrutiny of who is using the network endpoint.
This is where identity-based networking comes into play. Using various means, you can identify who the user is that is on a particular network device, and based on that information, apply network policy that dictates which resources they can connect to.
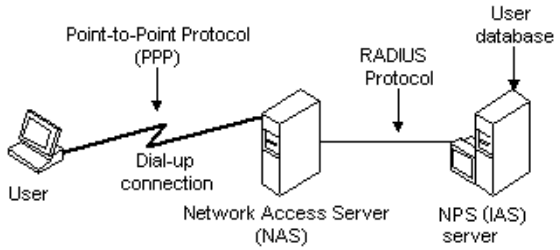
This is something that VMware NSX can do easily. Also, more traditional 802.1X network authentication can be used to apply network policy with RADIUS based on their identity.
4. Monitor for New Devices Connected to your Network
It sounds simple, but monitoring when and if new or unexpected devices are connected to your network can go a long way in knowing if you may have a rogue device, or unauthorized user/device connected to your network.
Using a tool like Arpwatch is a powerful way to detect when new devices are connected to your network, or if you have an odd change in MAC addresses connected. If the MAC address “flip/flops” there could be a security issue underway.
5. Perform Network Monitoring and Analysis
Keeping an eye on where packets are going both laterally, across your internal subnets, and north/south traffic or egress traffic out to the Internet. Monitoring egress traffic is perhaps one of the more inciteful ways to pinpoint traffic that is malicious or maybe “Shadow IT”.
If the bad guys get into your network, they have to get traffic out to somewhere or some domain. Monitoring types of traffic, protocol mismatches like DNS going to port 18000 or something strange like that for example can clue you into something that isn’t normal.
Monitoring top level domains or TLD is a good indicator of potentially malicious traffic. Monitoring for unusual protocols or other protocol anomalies.
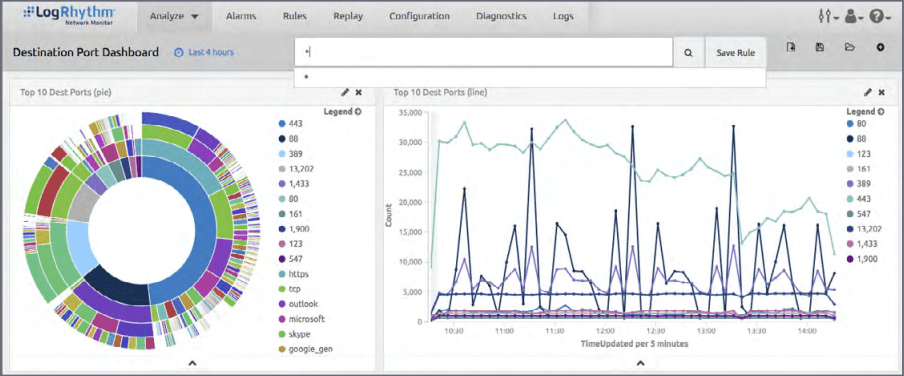
There are many good tools for network monitoring, however, one I have written about before is LogRhythm’s NetMon tool that gives you tremendous network visibility, even with the “freemium” version.
Wrapping Up – Five Ways to Improve Network Security
Network security is a crucially important part of your overall security. After all, the network is what ties endpoints together and allows packets to flow. With these five ways to improve network security and others, you can help to close potential security holes in your network infrastructure.