5 Ways to Improve Virtualization Security
Security is a top priority among businesses today and no doubt as a virtualization administrator you are tasked with ensuring securing in your environment is what it needs to be. Whether you manage VMware or Hyper-V environments, security is a constant battle that must be implemented in layers and generally, the weakest link can lead to compromise. In this post, we will take a look at 5 Ways to improve virtualization security in general concepts to help bolster the overall security stance for your virtual environments.
5 Ways to Improve Virtualization Security
Let’s take a look at the following 5 ways to improve virtualization security:
- Upgrade host firmware and BIOS to latest version
- Limit access to hypervisor hosts
- Use Virtualization-Based security
- Encrypt virtual hard disks
- Patch your guest operating systems running inside virtual machines
Let’s look at each of these virtualization security areas and see how why they are extremely important in your virtualization security strategy.
Upgrade Host Firmware and BIOS to Latest Version
We have certainly been in for a wild ride since the beginning of 2018 with events that unfolded with CPU security flaws that were discovered with speculative execution. Ever since then there have be continuous flaws and security vulnerabilities released in regards to speculative execution.
With the potential for attackers to be able to side step security mechanisms and even snoop in on otherwise protected spaces in the CPU architecture, it is extremely important with a virtualization host to follow the recommended patching and microcode updates that have been released to mitigate these speculative execution vulnerabilities.
VMware released a whole series of patches and mitigations in relation to speculative execution before the hardware manufacturers and Intel released their official patches.
If you haven’t already:
- Check with your hardware vendor for your virtualization host and make sure you have the latest BIOS and firmware updates for the hardware
- Check with your virtualization software vendor and make sure you have implemented the recommended patches for the hypervisor that coincides with the mitigations at the hardware level.
Limit Access to Hypervisor Hosts
This may seem like a no-brainer, however, limiting access to the hypervisor host itself can certainly improve your security stance. With hypervisor hosts, any access to the host itself and management of the host, is essentially access to all the workloads residing on the host.
Limiting access to the host itself with well established role based permissions configured for managing the environment can greatly limit exposure to someone having too much access and the security implications that may pose.
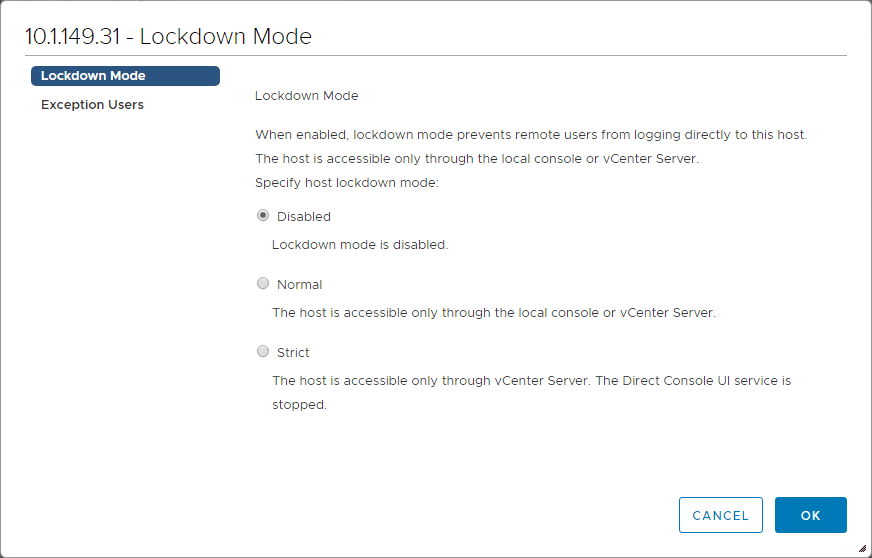
With VMware vSphere ESXi, you can enforce lockdown mode. When lockdown mode is enabled, no users other than vpxuser have authentication permissions, nor can they perform operations against the host directly. Lockdown mode forces all operations to be performed through vCenter Server. The root user is still authorized to log in to the direct console user interface when lockdown mode is enabled.
With Hyper-V you can secure access to the Hyper-V host with Windows permissions. Additonally using secure networks to access the virtualization hosts can help to secure access to the hypervisor host.
Use Virtualization-based Security
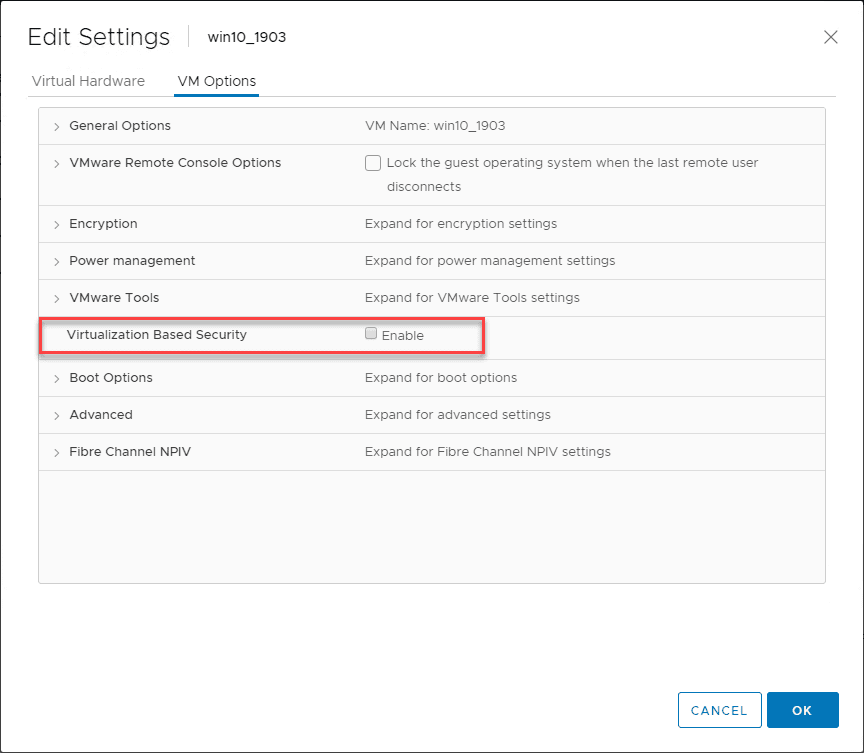
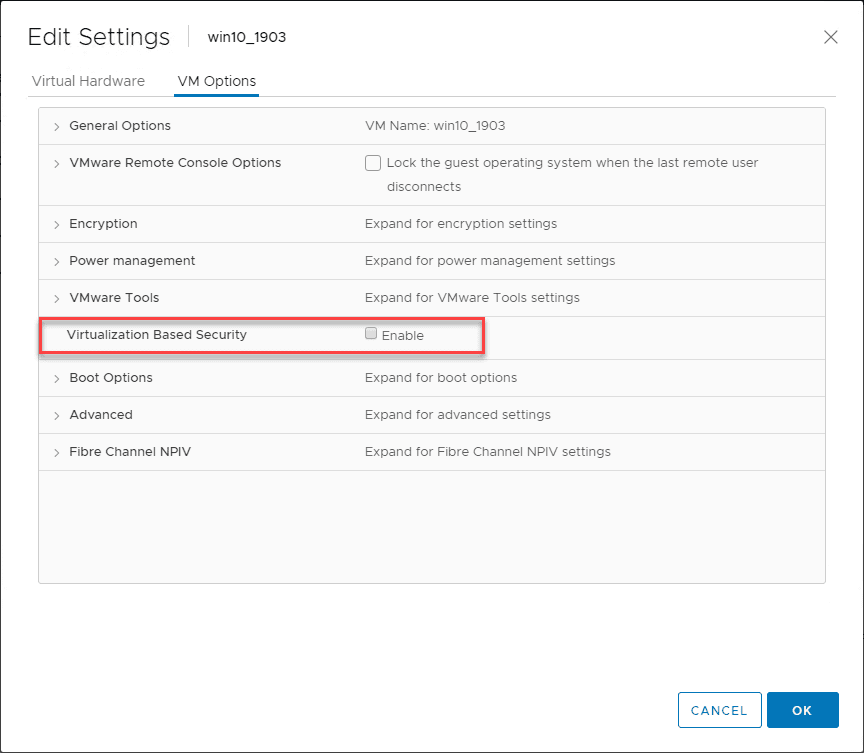
What is Virtualization-based security? It uses hardware virtualization features to create and isolate a secure region of memory from the normal operating system. This virtual secure mode can host security solutions and provides increased protection from vulnerabilities in the operating system and preventing malicious exploits that attempt to defeat security protections you may have in place.
To do this it uses the Windows hypervisor to create a virtual secure mode that protects security asses like authenticated user credentials. Even if malware can gain acces to the OS kernel the possible exploits can be limited and contained. This is due to the hypervisor preventing malware from eecuting code or accessing platform secrets.
With the latest versions of VMware vSphere and Hyper-V, virtualization-based security can be implemented in guest operating systems running in a virtual machine. This allows the protections that VBS brings to the table to be extended to VMs.
I have covered setting up VBS in VMware vSphere. Take a look at that post here.
Encrypt Virtual Hard Disks
Encryption is one of the basic ways to protect data. Entire hard disk encryption is a great way to protect all the data on a hard disk. This is a common practice for businesses that have laptops that travel out with mobile sales reps and such. However, this is equally important in your virtualized environment.
An attacker or a rogue administrator can steal the entire hard disk of a virtual machine and then take the VMDK or VHDX to another location and mount it to steal data or crack files as needed. However, with virtual hard disk encryption, you can implement entire hard disk encryption of the virtual disk.
VMware has VM Encryption and Hyper-V has Guarded Fabric with BitLocker encryption that can be implemented for this purpose. In this way, if an attacker or rogue administrator takes a copy of the disk with them and mounts the disk, it will be unreadable.
Patch Guest Operating Systems Running in VMs
As painful as patching guest operating systems can be, patching guest operating systems is an essential part of keeping your environment secure. All it takes is a vulnerable guest operating system for an attacker to have a backdoor into an operating system. Known vulnerabilities are generally some of the first points of attack for an attacker.
Virtualization-based security can help to mitigate an contain sensitive areas on the guest operating system. However, patching helps to add an additional layer of plugging any security holes that may exist and present an opportunity for an attacker.
Having a regular patch schedule is essential. Many business tend to perform patches on clients, but neglect servers. This is a dangerous stance to take since often servers are externally facing or may process some type of Internet traffic. Patching servers is a critical part of your overall security strategy.
Wrapping Up
There are certainly more than the 5 Ways to Improve Virtualization Security. However, the five ways mentioned are a great way to get started with securing your virtual environments, no matter what hypervisor you are running. The issue of security is certainly not going away any time soon.
Treating security as “layers of an onion” will help form many layers of risk mitigation so that if an attacker makes their way through one layer, there are other layers available to stop them.