Three Free SSL Certificates and Tools
There are various means that can be used to create free self-signed certificates that can be used for various means. This can include lab environments or POCs of products, testing, or other means. All of us know the headache at times trying to work through SSL certificate errors with various products. Over the past few years, we have gotten better tools to create free SSL certificates that are actually valid. What are those tools or SSL certificates that can be used for this purpose? In this post we will take a look at three Free SSL Certificates and Tools that can be used for adding SSL functionality for various reasons.
Three Free SSL Certificates and Tools Overview
There are many advantages to using SSL aside from testing and POC environents:
- Performance – it can actually improve page load times
- SEO benefits – Google and others actually give precedence to websites that are secured with SSL
- Security – Perhaps the biggest reason, security of your website is critical with today’s security threats
- Trust – More and more, end users are learning to only trust websites that are secured with SSL
- Regulatory Compliance – SSL is a key component in compliance regulations such as PCI compliance
The benefits of SSL are obvious. This post is not meant to be an all inclusive list of SSL certificates and tools to create free SSL certificates, however, these are three tools that I have used that have worked well in lab, POC, test, and other environments to enable SSL functionality. We will look at the following:
- LetsEncrypt
- CloudFlare Origin Certificates
- PowerShell Generated Self-Signed Certificates with Trust
Let’s take a brief look at each type of free SSL certificate and tool and see how it can be used to enable SSL functionality freely and simply on lab, test, or even production servers where you have the need to enable SSL functionality without any cost associated besides the configuration of the SSL certificate itself.
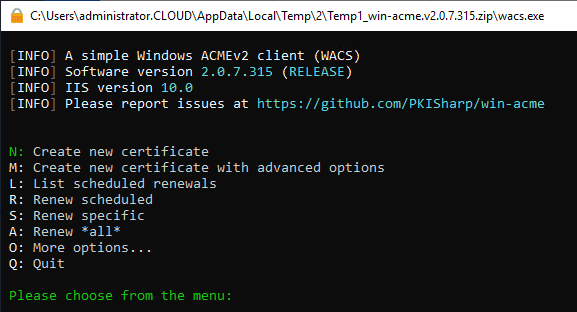
LetsEncrypt Free SSL Certificates
I have heard in various circles people say that they are afraid to use free certificates and have heard this related to LetsEncrypt. However, there are a ton of posts out on the net regarding LetsEncrypt. However, in my thinking if there was a huge flaw residing in LetsEncrypt, most likely we would have seen something discovered.
I have used the LetsEncrypt SSL certificates in various use cases that I have had in lab environments and other environments and they have worked great. There are a couple of issues with LetsEncrypt, not really related to security, but a couple of other aspects of the service to be aware of.
- For the automated configuration of LetsEncrypt, strangely, LetsEncrypt wants to see port 80 open. There is a workaround to this that I will note using DNS proving of your domain.
- LetsEncrypt certificates are only valid for 3 months at a time, so you will need some type of automation in place to update your certificates or know you will need to replace them every 3 months
Below is a screenshot I took creating a free LetsEncrypt SSL certificate in the home lab for a SharePoint server.
Cloudflare Origin Certificates
Origin CA offered by Cloudflare uses a Cloudflare-issues SSL certificate. This means you do not have to have one issued by a Certificate Authority. This reduces a great deal of complexity regarding SSL configuration. Once the certificate is provisioned, you install the certificate at your origin server. The SSL certificate can be provisioned directly from the Cloudflare dashboard.
Cloudflare offers different modes of operation that configure the Cloudflare origin certificate a bit differently depending on how strictly you want to enforce the SSL traffic coming from Cloudflare to your origin server. With either mode, traffic to your end user will always be encrypted. The different modes of operation will affect only the traffic coming from Cloudflare to your origin server.
Flexible SSL – Flexible SSL is the easiest configuration that can be provisioned. The Flexible mode does not require you installing an SSL certificate on your origin server. This is not quite as secure as the Full Method, but it allows at least getting traffic to your end users secured.
Full SSL – Full mode provides end-to-end encryption of your traffic, both to Cloudflare and from Cloudflare to your origin server. This method requires installing an SSL certificate on your origin server.
There is a third more strict variant of Full mode, called Full (Strict) mode. This mode checks for SSL certificate validity at the origin web server. A self-signed certificate cannot be used. A Cloudflare CA cert or valid certificate purchased from a Certificate Authority is required to avoid errors in this configuration.
PowerShell Generated Self-Signed Certificates with Trust
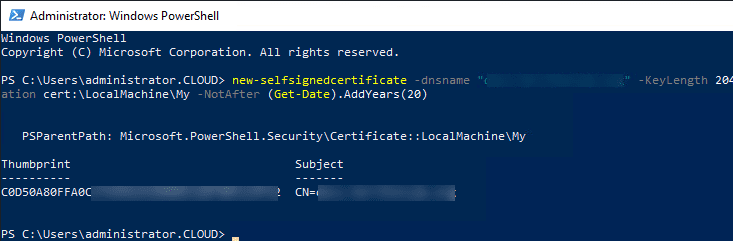
The third option falls back to a self-signed certificate that we all know and love/hate, whichever is the case. However, for various testing and proof of concept environments, they actually work well. I am an even bigger fan of self-signed certificates now with the PowerShell commandlet to easily create one with Windows Server 2012 R2 and higher. The new-selfsignedcertificate cmdlet makes this process easy. The below certificate quickly spins up a self-signed certificate in the Personal store on your server. As you can see, you can add the logic to set the period the SSL cert is valid. For labbing you can make these extremely long as the one below is valid for 20 years.
new-selfsignedcertificate -dnsname "myserver.mydomain.local" -KeyLength 2048 -CertStoreLocation cert:LocalMachineMy -NotAfter (Get-Date).AddYears(20)
Once you have a certificate, you can export the public key and place this on a workstation in the Trusted Root Certificate Authorities node and have a perfectly working SSL connection as if you had a valid certificate from a legitimate Certificate Authority.
Wrapping Up
Hopefully these Three Free SSL Certificates and Tools will help any who may be struggling to find a good solution for testing with SSL or even a free SSL certificate in production. Using solutions like LetsEncrypt, Cloudflare, and even self-signed certificates easily provisioned in PowerShell provide great ways to encrypt traffic to your web or other server.